- Cisco Community
- Technology and Support
- Security
- VPN
- ASA to ASA IPSec VPN. Not an expert but can't understand why it's not working. !!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA to ASA IPSec VPN. Not an expert but can't understand why it's not working. !!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2012 03:20 AM - edited 02-21-2020 06:20 PM
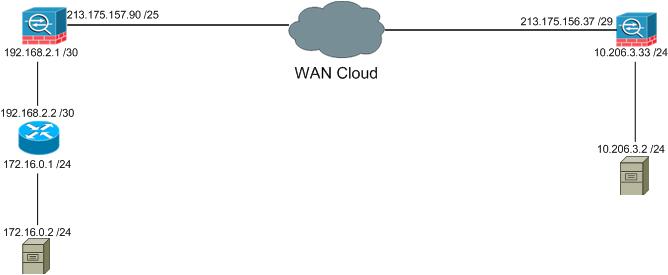
Hello everyone,
This is my first time trying to set up a site to site IPSec VPN between two ASAs. I've done it before between routers with no problems (more or less). I've been googling like a mad man and also checking youtube but maybe I am missing something simple.
My aim here is to have users on the left LAN 172.16.0.0 have access to users on the right LAN, obviously via VPN. I don't intend to NAT either side LAN's traffic, literrally all traffic goes over the VPN.
Currently both ASAs are running 8.4(2).
The security parameters I will like to use are:
IKE Phase 1 - AES - 128, SHA-1, Pre Shared Key, DH2
IKE Phase 2 - ESP-AES 128, ESP-SHA-HMAC
With a router, using CLI, we simply configure exactly what we need. But when using the GUI on the ASA both IKE v1 & IKE v2 are giving mutliple options which I am unsure if I am choosing correctly.
For IKE v1 settings it is asking me for only a pre-shared key, whereas with IKE v2 it is asking me for a local & remote pre-shared key. I thought both sides used the same pre-shared key. Never head of local & remote. Could someone explain this please? As a matter of fact though I used the same key for ALL the options.
For IKE v1 & v2 it is given an option for IKE Policy and IPSec proposal. Could someone please explain me the difference and why are there so MANY options where you can just choose one instead you end up with mulitple Policy and proposals. With the router command line I would just set IKE policy by choosing a number e.g 'crypto isakmp policy 100' and then set the encryption, authentication etc.
I am unsure how to set the transform-set also. Would really appreciate if someone can tell me.
For the record the log kept telling me that Phase 1 is completed. So I am assuming that is IKE phase 1 and I set that up correctly...maybe.
I have lots of other questions but I don't want to bombard you guys with so much.
Thanks everyone in advance for your input and I don't want you to feel like you are doing my job for me. I am just at wits end with trying to set this up for about a week now. Thank you.
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2012 04:22 AM
From version 8.4.2, there are 2 types of IKE that you can configure, ie: IKEv1 and IKEv2.
IKEv1 is the old IKE, which is the one similar to one that you configure on the router. So to configure it, just configure IKEv1, and don't configure anything with IKEv2.
You mention that phase 1 is complete, so the output of "show cry ikev1 sa" is MM_Active?
Here is the configuration guide for your reference:
http://www.cisco.com/en/US/docs/security/asa/asa84/configuration/guide/vpn_site2site.html
and just refer to IKEv1 part.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2012 05:26 AM
Hi,
Jennifer I just out of the office at the moment so when I can get back I will do the show command you suggested and let you know the output.
Also, a question just came to mind. Can more than one IPSec VPN be configured on a single interface? Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2012 06:02 AM
Yes, you can have more than one IPSec VPN tunnel configured on a single interface.
You would use just 1 crypto map name and apply that to an interface, however, you can have multiple sequence number within that crypto map for different IPSec VPN tunnels.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

