- Cisco Community
- Technology and Support
- Security
- VPN
- Re: B2B VPN BGP over IPSC cant ping/ssh across tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2022 09:17 PM
Hi
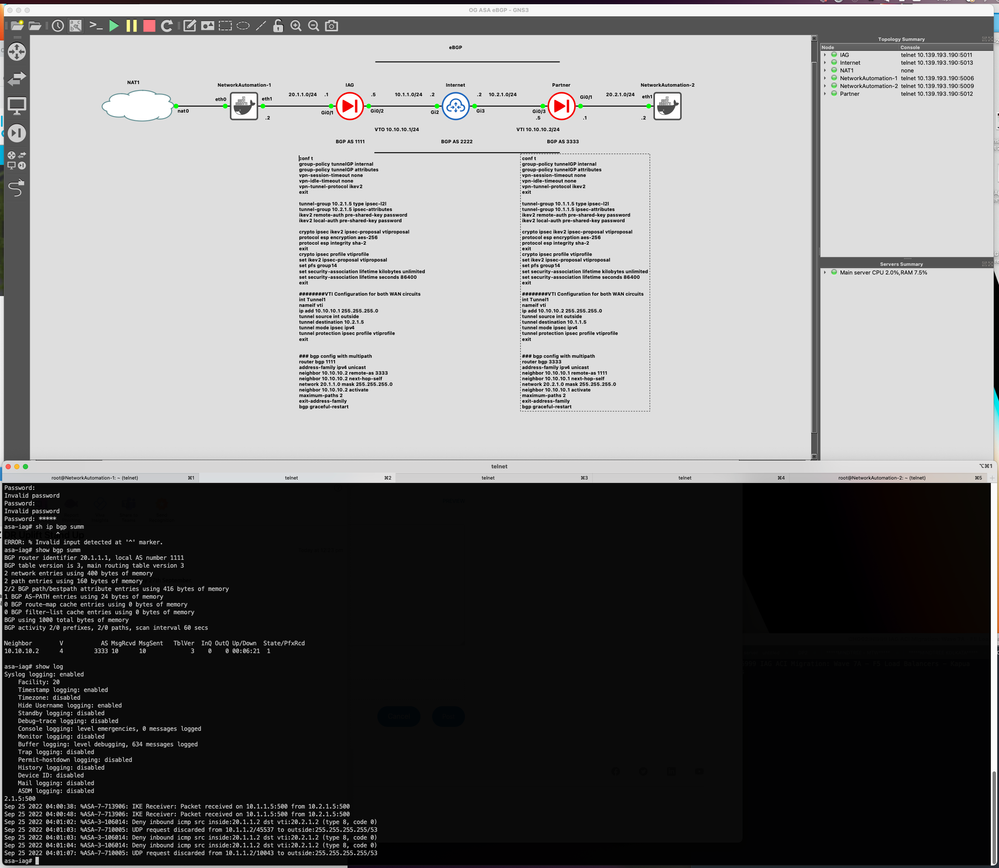
I am hoping that i can get some guidance on getting this lab up and running. I am trying to run bgp over IPSeC between two asa in routed mode and pass traffic over it. I have successfully got BPG up and running over the IPSeC from what i can tell using a VTI on the ASAs. However i am unable to ping from a client on each side across the VPN Tunnel. I have enabled ICMP inspection on the ASAs. The debug output on the ASA when i do try to ping from a src at 20.1.1.2 to dst 20.2.1.2 shows:
Sep 25 2022 04:00:38: %ASA-7-713906: IKE Receiver: Packet received on 10.1.1.5:500 from 10.2.1.5:500
Sep 25 2022 04:00:48: %ASA-7-713906: IKE Receiver: Packet received on 10.1.1.5:500 from 10.2.1.5:500
Sep 25 2022 04:01:02: %ASA-3-106014: Deny inbound icmp src inside:20.1.1.2 dst vti:20.2.1.2 (type 8, code 0)
Sep 25 2022 04:01:03: %ASA-7-710005: UDP request discarded from 10.1.1.2/45537 to outside:255.255.255.255/53
Sep 25 2022 04:01:03: %ASA-3-106014: Deny inbound icmp src inside:20.1.1.2 dst vti:20.2.1.2 (type 8, code 0)
Sep 25 2022 04:01:04: %ASA-3-106014: Deny inbound icmp src inside:20.1.1.2 dst vti:20.2.1.2 (type 8, code 0)
Sep 25 2022 04:01:07: %ASA-7-710005: UDP request discarded from 10.1.1.2/10043 to outside:255.255.255.255/53
Any suggestions would be great.
Thank You.
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2022 03:35 AM
Hazahhh...Awesome
That did the trick thank you for taking the time to respond. So obvious now
Thank You
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2022 11:56 PM - edited 09-25-2022 12:01 AM
@oriongruca your security levels are incorrect on the inside and outside interfaces, the outside interface should have a security level of 0 and the inside interface should have 100. Traffic will be denied source from an interface with a lower security level to an interface with a higher security level, unless there is an ACL explictly permitting the traffic.
Change the security level on both ASAs as below.
interface GigabitEthernet0/1
nameif inside
security-level 100
!
interface GigabitEthernet0/2
nameif outside
security-level 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2022 03:35 AM
Hazahhh...Awesome
That did the trick thank you for taking the time to respond. So obvious now
Thank You
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide