- Cisco Community
- Technology and Support
- Security
- VPN
- Cisco FTD remote access VPN with ISE posture
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 07:09 PM - edited 12-09-2022 07:11 PM
Hello team,
I'm setting up a remote access VPN on FTD with ISE posture.
The problem I have is that the posture does not work and in AnyConnect I see the message "no policy server detected".
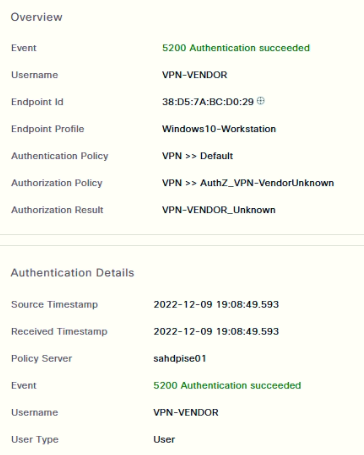
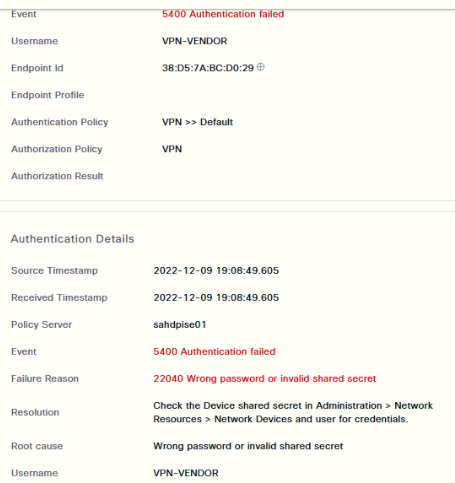
In the ISE logs I see that for each login in the VPN two authentication events are generated in the ISE. The first event has the result "secceeded" (this is fine), and the second event has the result "failed".
I made a capture of the RADIUS packets that the ISE receives and I observed that in the second authentication event the firewall sends the username as if it were the authentication password.
For example:
1st authentication event: username "fernando", password "123456". (This is fine). - result "secceeded"
2nd authentication event: username "fernando", password "fernando". - result "failed".
The temporal action that I applied to solve the problem is to enable the option "If Auth Fail = CONTINUE", in the Authentication Policy of the ISE.
After applying the temporary action, the whole posture procedure works correctly.
Does anyone know why that behavior occurs?
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Remote Access
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2022 06:27 AM - edited 12-12-2022 06:28 AM
I solved the problem.
I was missing a check in the RADIUS configuration of the FTD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2022 01:20 AM
@FernandoDiaz1992 what is RADIUS the configuration on the FTD connection profile? Please provide screenshot
What is the configuration of your ISE authorisation rules and profile (in regard to posture redirect)?
Which cisco guide have you followed for configuration? https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/215236-ise-posture-over-anyconnect-remote-acces.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2022 07:22 AM - edited 12-10-2022 07:26 AM
Hi Rob,
Thanks for answering.
I attach the screenshots of the configuration.
RADIUS in FTD: radius1, radius2, radius3, aclftd.
ISE: ise1, ise2, ise3, ise4, ise5, ise6.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2022 07:27 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2022 07:50 AM
@FernandoDiaz1992 I've seen this before where two authentications are sent to the RADIUS server, but I cannot recall the exact issue. What is the configuration of the connection profile itself?
What version of FMC/FTD are you using?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2022 07:56 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2022 06:27 AM - edited 12-12-2022 06:28 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide