- Cisco Community
- Technology and Support
- Security
- VPN
- Configuring VPN Site to Site ASA 5505 with Contivity Nortel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Configuring VPN Site to Site ASA 5505 with Contivity Nortel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2012 10:25 AM
ASA is configured with the VPN site to site using the wizard, created the Public IP of contivity, local and remote LAN . I attached the configuration.
In contivity have the following settings:

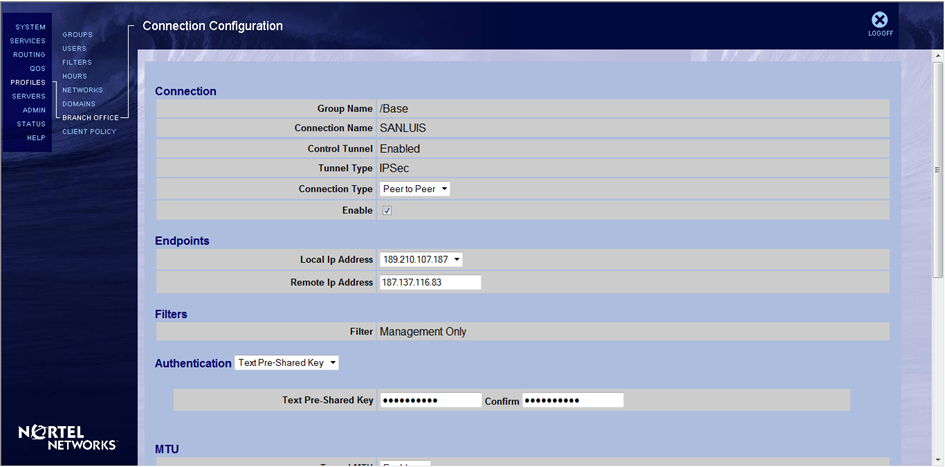
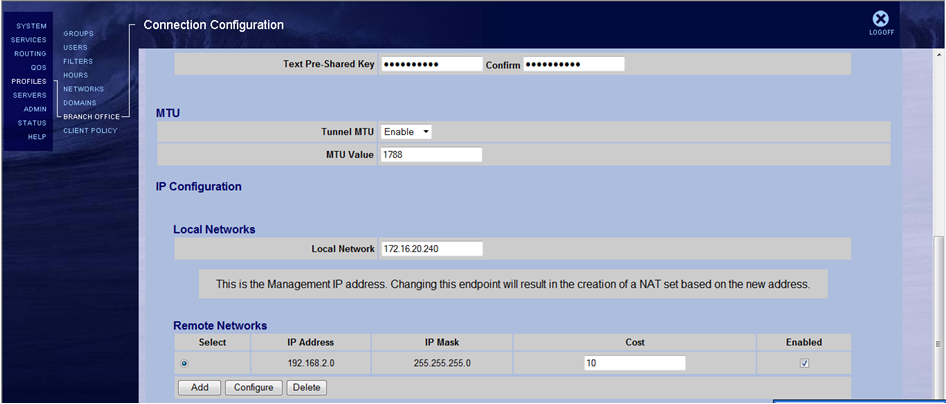
Not able to communicate both subnets.
Do I need to configure IP subnets and published in the contivity as was done in the ASA?
I appreciate your support.
regards
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2012 06:42 PM
I don't see any configuration for the site-to-site VPN on the ASA side that matches the Contivity side.
Here is a sample configuration for ASA that you can reference:
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a0080950890.shtml
Let us know how it goes after the configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2012 07:22 AM
Sorry Jennifer,
I got an error when attaching the ASA config, put the correct settings:
ASA Version 8.3(1)
!
hostname TestASA
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
pppoe client vpdn group client
ip address pppoe
!
interface Vlan10
no nameif
no security-level
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
switchport access vlan 10
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
ftp mode passive
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network Loc_Qro_LAN
subnet 172.16.20.0 255.255.255.0
description LAN_Qro
object network Loc_Qro_Contivity
host 189.210.107.187
object network Loc_SLP_LAN
subnet 192.168.2.0 255.255.255.0
description LAN_SLP
object-group protocol DM_INLINE_PROTOCOL_1
protocol-object ip
protocol-object udp
protocol-object tcp
object-group protocol DM_INLINE_PROTOCOL_2
protocol-object ip
protocol-object udp
protocol-object tcp
access-list outside_access_in extended permit object-group DM_INLINE_PROTOCOL_1 any any
access-list inside_access_in extended permit object-group DM_INLINE_PROTOCOL_2 any any
access-list no_nat extended permit ip 192.168.1.0 255.255.255.0 192.168.25.0 255.255.255.0
access-list outside_1_cryptomap extended permit ip object Loc_SLP_LAN object Loc_Qro_LAN
access-list outside_access_in_1 extended permit ip any any
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
ip local pool SSLClientPool 192.168.25.1-192.168.25.50 mask 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat (inside,outside) source dynamic any interface
nat (inside,outside) source static Loc_SLP_LAN Loc_SLP_LAN destination static Loc_Qro_LAN Loc_Qro_LAN
!
object network obj_any
nat (inside,outside) dynamic interface
access-group inside_access_in in interface inside
access-group outside_access_in_1 in interface outside control-plane
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 187.137.116.83 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.1.0 255.255.255.0 inside
http 0.0.0.0 0.0.0.0 outside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map outside_map 1 match address outside_1_cryptomap
crypto map outside_map 1 set pfs
crypto map outside_map 1 set peer 189.210.107.187
crypto map outside_map 1 set transform-set ESP-3DES-MD5
crypto map outside_map interface outside
crypto ca trustpoint ASDM_TrustPoint0
enrollment self
subject-name CN=TestASA.com
crl configure
crypto ca certificate chain ASDM_TrustPoint0
certificate 9f877850
308201d3 3082013c a0030201 0202049f 87785030 0d06092a 864886f7 0d010105
0500302e 31143012 06035504 03130b54 65737441 53412e63 6f6d3116 30140609
2a864886 f70d0109 02160754 65737441 5341301e 170d3132 31303132 32323333
33375a17 0d323231 30313032 32333333 375a302e 31143012 06035504 03130b54
65737441 53412e63 6f6d3116 30140609 2a864886 f70d0109 02160754 65737441
53413081 9f300d06 092a8648 86f70d01 01010500 03818d00 30818902 818100e4
db65167d 274d047e b561321d 29e7b89b cffe3f8e b485afab 7852d21d 5382cbd1
a856551e 45c9f122 a872dd29 465e9aef c21b0ab7 59858e9b 5855fd16 dc61a8ec
20e6f0ae 780a08d4 f4a7f3b6 4d446c48 c9318476 e8c9aa5d 401ee788 d26673c4
38f2b7d0 bd972210 cd3d42b1 7b650bf8 95a8056c 150b36e5 4715eb48 74065b02
03010001 300d0609 2a864886 f70d0101 05050003 8181002a ae81698b fa94a435
37aaf7d0 c5baab56 5bd66515 b80e784a 0b18a2e0 fcc3bdda 78a00f87 617de66f
5b79f6e9 9586252f 05e14055 aa5d484b a25e9be3 68dfb5ed c60d0afe 2e309c2b
c7c8cae5 d8485e90 b16dc42e c823d9db 6147fd42 bb6953f2 977063a9 8360b80b
65824e4f e290bbcf 142a67e2 2d92ccaa cfb3abac e89162
quit
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption des
hash md5
group 1
lifetime 86400
crypto isakmp policy 30
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
crypto isakmp policy 50
authentication pre-share
encryption des
hash sha
group 1
lifetime 86400
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 outside
ssh timeout 5
console timeout 0
vpdn group client request dialout pppoe
vpdn group client localname cumarsaidchliste1
vpdn group client ppp authentication pap
vpdn username cumarsaidchliste1 password *****
dhcpd auto_config outside
!
dhcpd address 192.168.1.5-192.168.1.36 inside
dhcpd dns 201.116.191.251 201.144.127.251 interface inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl trust-point ASDM_TrustPoint0 outside
ssl trust-point ASDM_TrustPoint0 outside vpnlb-ip
webvpn
svc image disk0:/anyconnect-win-3.0.10055-k9.zip 1
svc profiles AnyConnectWIN3.0 disk0:/anyconnect-win-3.0.10055-k9.zip
tunnel-group-list enable
group-policy SSLCLientPolicy internal
group-policy SSLCLientPolicy attributes
dns-server value 192.168.1.1
vpn-tunnel-protocol svc
default-domain value slp.local
address-pools value SSLClientPool
username cisco password 3USUcOPFUiMCO4Jk encrypted privilege 15
username slpuser password JOg.fnHqzKIK/g5Q encrypted
username slpuser attributes
service-type remote-access
tunnel-group SSLClientProfile type remote-access
tunnel-group SSLClientProfile general-attributes
default-group-policy SSLCLientPolicy
tunnel-group SSLClientProfile webvpn-attributes
group-alias SSLVPNClient enable
tunnel-group 189.210.107.187 type ipsec-l2l
tunnel-group 189.210.107.187 ipsec-attributes
pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:21e036adac660fb04e0106184e4f311d
: end
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2012 12:46 PM
You haven't got the matching crypto isakmp policy (ike).
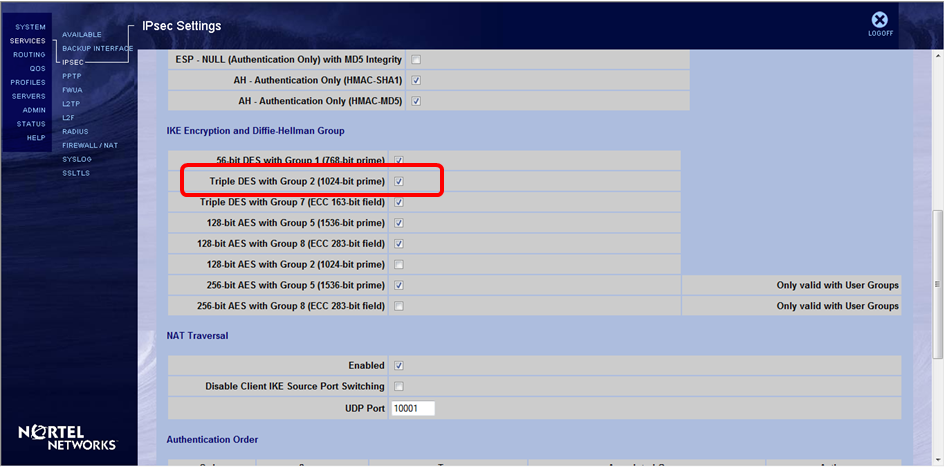
On the contivitiy, you have 3des and group 2 (i can't see the setting for hash, not sure whether it's sha or md5) as the screenshot on the top is cut off.
On the ASA, you should configure the following:
crypto isakmp policy 5
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
For the hash command, check the contivitiy side and match it accordingly.
Then since you are matching VLAN 10 for the crypto ACL, your actual VLAN 10 needs to have the security-level and nameif configured, otherwise it won't work.
Also, the local network on the contivitiy side should be 172.16.20.0/24, instead of 172.16.20.240 as it needs to match the crypto ACL configured on the ASA.
Lastly, I can't see on your first screenshot whether PFS is set or not. If PFS is not set, then you can remove the following line:
crypto map outside_map 1 set pfs
Otherwise, if it is, then just leave it in the configuration.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

