- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Delete Certificate that does not have an Associates Trustpoint
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Delete Certificate that does not have an Associates Trustpoint
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 07:18 PM
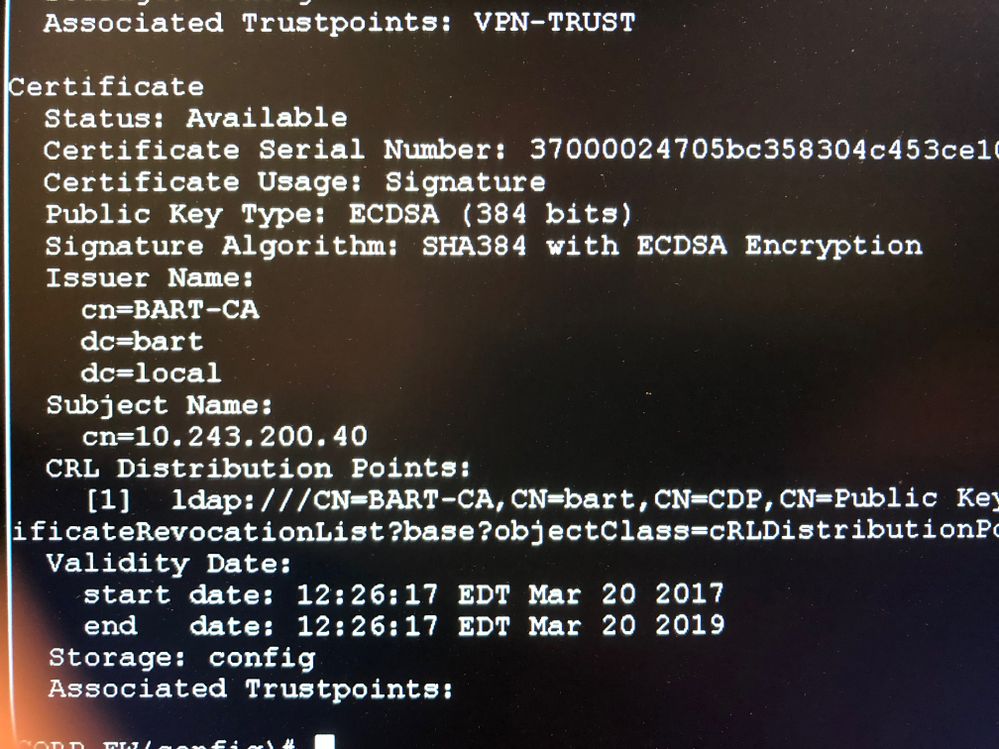
I have been having some trouble getting a site to site tunnel working using IKEV2 certificates. I have one working tunnel and another that is not. Get the "self signed not acceptable". Only that isn't really the case. Certs on both devices signed by the same CA and generated in the exact same fashion. However, one ASA I see an errant certificate that I can figure out how to delete. I am thinking that this certificate is causing the issue. See below. Thanks
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2018 12:47 AM
you see that certificate with "sh run crypto ca"? If yes try deleting it with "no crypto ca cert chain ...".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2018 03:03 AM
Thanks for the response. I did try that, however it still wants a trustpoint. This is what I get:
FW(config)# no crypto ca certificate chain
ERROR: % Incomplete command
FW(config)#
FW(config)# no crypto ca certificate chain ?
configure mode commands/options:
WORD < 65 char Trustpoint Name
I slept on it last night. The certificate shows up, I can't blow away the config since it is in production. I have to get the remote office up this morning so loose all trust that I am the one that knows.
I know that the remote end is the one that is having issues with the certificate. The local side loves the certificate that it receives and actually brings the tunnel up. The other side not so much. I am going to run a debug crypto ca on the other side to see if I can match the serials as to what is happening with the certificate. Otherwise the behavior I see is not what I expect.
Second step is that I am going to zero the device. Delete the existing trustpoint, and keys. Then rekey. Shouldn't take too long.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2018 04:07 AM
Rekeyed the ASA. Did this by removing references then deleting the trustpoint and then clearing the key. Then I reversed the process. Same problem with the tunnel but the extra certificate is now gone.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2018 05:26 AM
Updated the code on the remote side from 9.8.20 to 9.8.3. Now the certs are passing authentication on both sides. Could be a code issue. Still failing, but I do have the resolution for why the post was created. Will examine the configurations. Especially since I have two tunnels configured to two different ASA's. One works and one does not.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: