- Cisco Community
- Technology and Support
- Security
- VPN
- Re: DMVPN through Static PAT
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2010 04:56 PM - edited 02-21-2020 05:01 PM
Hi, everyone.
The main site having DMVPN-Hub-router is provided only one public IP by ISP with PPPoE.
I am running dmvpn between three points with no problem.
Now I am trying to insert ASA5510 between internet and dmvpn-hub-router.
■Then what should I do on ASA5510?
・Configure static PAT for udp500 and udp4500 such as bellow ?
access-list 100 extended permit ip any any
access-list DMVPN_nat_static extended permit udp host DMVPN-Global-int eq isakmp any
access-list DMVPN_nat_static_1 remark IPSec NAT-Traversal
access-list DMVPN_nat_static_1 extended permit udp host DMVPN-Global-int eq 4500 any
access-list pppoe_access_in extended permit udp any any
global (pppoe) 1 interface
static (DMVPN,pppoe) udp interface isakmp access-list DMVPN_nat_static
static (DMVPN,pppoe) udp interface 4500 access-list DMVPN_nat_static_1
access-group pppoe_access_in in interface pppoe
■What should I do on DMVPN-HUB
・Change default route Dialer1 to ASA5510 ?
ip route 0.0.0.0 0.0.0.0 172.16.0.1
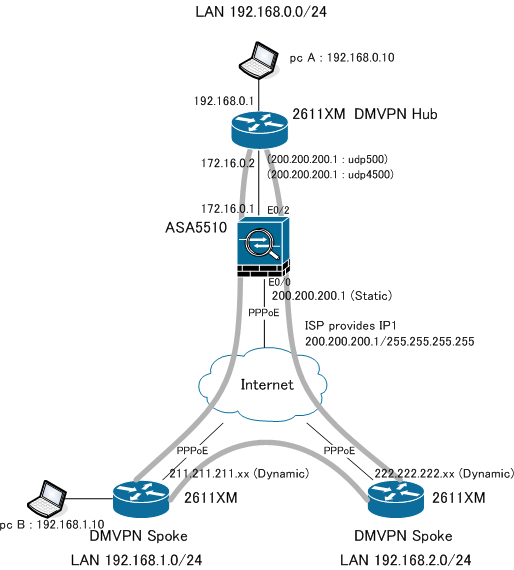
I could not connect pcB to pcA with following configuration (Ping command faild).
What should I do else ?
Regards,
okumura
<cf.> Full configuration ***********************************
■ASA5510
ciscoasa# show run
: Saved
:
ASA Version 8.2(2)
!
hostname ciscoasa
domain-name default.domain.invalid
enable password ****** encrypted
passwd ****** encrypted
names
name 172.16.0.2 DMVPN-Global-int
!
interface Ethernet0/0
nameif pppoe
security-level 0
pppoe client vpdn group pppoe
ip address pppoe setroute
!
interface Ethernet0/1
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/2
nameif DMVPN
security-level 100
ip address 172.16.0.1 255.255.255.0
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.226.5 255.255.255.0
management-only
!
ftp mode passive
dns server-group DefaultDNS
domain-name default.domain.invalid
access-list 100 extended permit ip any any
access-list DMVPN_nat_static extended permit udp host DMVPN-Global-int eq isakmp any
access-list DMVPN_nat_static_1 remark IPSec NAT-Traversal
access-list DMVPN_nat_static_1 extended permit udp host DMVPN-Global-int eq 4500 any
access-list pppoe_access_in extended permit udp any any
pager lines 24
logging asdm informational
mtu management 1500
mtu pppoe 1454
mtu DMVPN 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-631.bin
no asdm history enable
arp timeout 14400
global (pppoe) 1 interface
static (DMVPN,pppoe) udp interface isakmp access-list DMVPN_nat_static
static (DMVPN,pppoe) udp interface 4500 access-list DMVPN_nat_static_1
access-group pppoe_access_in in interface pppoe
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.226.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
telnet timeout 5
ssh timeout 5
console timeout 0
vpdn group pppoe request dialout pppoe
vpdn group pppoe localname ******
vpdn group pppoe ppp authentication pap
vpdn username ****** password ***** store-local
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
call-home
profile CiscoTAC-1
no active
destination address http ******
destination address email ******
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:******
: end
■DMVPN HUB router
DMVPN_HUB#show running-config
Building configuration...
Current configuration : 2370 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname DMVPN_HUB
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
no network-clock-participate slot 1
no network-clock-participate wic 0
ip cef
!
!
no ip dhcp use vrf connected
ip dhcp excluded-address 192.168.0.1 192.168.0.10
!
ip dhcp pool CL0
network 192.168.0.0 255.255.255.0
default-router 192.168.0.1
!
!
!
username cisco password 0 cisco
!
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 0.0.0.0 0.0.0.0
crypto isakmp keepalive 30
!
!
crypto ipsec transform-set DMVPNSET esp-3des esp-sha-hmac
!
crypto ipsec profile DMPROFILE
set transform-set DMVPNSET
!
!
!
interface Loopback0
shutdown
!
interface Tunnel0
ip address 10.0.0.1 255.255.255.0
no ip redirects
ip mtu 1368
ip nhrp authentication DMCISCO
ip nhrp map multicast dynamic
ip nhrp network-id 99
ip nhrp holdtime 300
ip ospf network broadcast
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 10
tunnel protection ipsec profile DMPROFILE
!
interface FastEthernet0/0
description Internet
ip address 172.16.0.2 255.255.255.0
ip virtual-reassembly
ip tcp adjust-mss 1414
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 192.168.0.1 255.255.255.0
ip nat inside
ip virtual-reassembly
ip tcp adjust-mss 1414
duplex auto
speed auto
!
interface Dialer1
shutdown
!
router ospf 1
log-adjacency-changes
network 10.0.0.0 0.0.0.255 area 0
network 192.168.0.0 0.0.0.255 area 0
!
ip route 0.0.0.0 0.0.0.0 172.16.0.1
!
!
ip http server
no ip http secure-server
ip nat inside source list 1 interface FastEthernet0/0 overload
!
access-list 1 permit 192.168.0.0 0.0.0.255
dialer-list 1 protocol ip permit
!
!
!
control-plane
!
!
!
dial-peer cor custom
!
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
exec-timeout 0 0
logging synchronous
login local
!
!
end
■DMVPN Spoke router
DMVPN_SPOKE#show running-config
Building configuration...
Current configuration : 2272 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname DMVPN_SPOKE
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
no network-clock-participate slot 1
no network-clock-participate wic 0
ip cef
!
!
no ip dhcp use vrf connected
ip dhcp excluded-address 192.168.1.1 192.168.1.10
!
ip dhcp pool CL1
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 0.0.0.0 0.0.0.0
crypto isakmp keepalive 30
!
!
crypto ipsec transform-set DMVPNSET esp-3des esp-sha-hmac
!
crypto ipsec profile DMPROFILE
set transform-set DMVPNSET
!
!
!
interface Tunnel0
ip address 10.0.0.2 255.255.255.0
no ip redirects
ip mtu 1368
ip nhrp authentication DMCISCO
ip nhrp map 10.0.0.1 200.200.200.1
ip nhrp map multicast 200.200.200.1
ip nhrp network-id 99
ip nhrp holdtime 300
ip nhrp nhs 10.0.0.1
ip ospf network broadcast
ip ospf priority 0
tunnel source Dialer1
tunnel mode gre multipoint
tunnel key 10
tunnel protection ipsec profile DMPROFILE
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
pppoe enable group global
pppoe-client dial-pool-number 1
!
interface Serial0/0
no ip address
shutdown
!
interface FastEthernet0/1
ip address 192.168.1.1 255.255.255.0
ip nat inside
ip virtual-reassembly
ip tcp adjust-mss 1414
duplex auto
speed auto
!
interface Serial0/1
no ip address
shutdown
!
interface Dialer1
mtu 1454
ip address negotiated
ip nat outside
ip virtual-reassembly
encapsulation ppp
dialer pool 1
dialer-group 1
ppp authentication chap callin
ppp chap hostname ***********
ppp chap password 0 ******
!
router ospf 1
log-adjacency-changes
network 10.0.0.0 0.0.0.255 area 0
network 192.168.1.0 0.0.0.255 area 0
!
ip route 0.0.0.0 0.0.0.0 Dialer1 permanent
!
!
ip http server
no ip http secure-server
ip nat inside source list 1 interface Dialer1 overload
!
access-list 1 permit 192.168.1.0 0.0.0.255
dialer-list 1 protocol ip permit
!
!
!
control-plane
!
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
login
!
!
end
Solved! Go to Solution.
- Labels:
-
DMVPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2010 06:56 AM
Hi Tomoyuki,
Please change the IPSec Transform set to transport mode as below (On both Hub and Spoke)
crypto ipsec transform-set DMVPNSET esp-3des esp-sha-hmac
mode transport
Thanks,
Naman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2010 11:07 AM
Hi Omkura,
Yes. Transport mode must be used when any device is behind NAT.
Thanks,
Naman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2010 06:33 AM
You are Welcome.
Please do not forget to mark your thread as answered when you get the answer you are looking for.
Thanks,
Naman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2010 10:46 AM
Hi Tomoyuki,
Do you see Phase 1\ Phase 2 come up ?
Is NAT-T being negotiated ? (Else traffic will be ESP and not UDP\4500 and you will have to permit ESP also in Firewall)
What does the packet capture show on ASA in both Ingress and Egress Direction ?
Thanks,
Naman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2010 09:07 PM
Hi, Naman.
Thank you for your reply.
> Do you see Phase 1\ Phase 2 come up ?
■DMVPN_HUB_ROUTER
#show crypto isakmp sa
dst src state conn-id slot status
172.16.0.2 211.211.211.xx QM_IDLE 51 0 ACTIVE
172.16.0.2 211.211.211.xx MM_NO_STATE 50 0 ACTIVE (deleted)
172.16.0.2 211.211.211.xx MM_NO_STATE 49 0 ACTIVE (deleted)
#
*Mar 1 00:27:47.489: %CRYPTO-6-IKMP_MODE_FAILURE: Processing of Quick mode failed with peer at 211.211.211.xx
#show crypto ipsec sa
(No entry)
#show ip int br
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 172.16.0.2 YES NVRAM up up
FastEthernet0/1 192.168.0.1 YES NVRAM up up
NVI0 unassigned NO unset up up
Tunnel0 10.0.0.1 YES NVRAM up up
■DMVPN_SPOKE_ROUTER
#show crypto isakmp sa
dst src state conn-id slot status
200.200.200.1 211.211.211.xx QM_IDLE 54 0 ACTIVE
200.200.200.1 211.211.211.xx MM_NO_STATE 53 0 ACTIVE (deleted)
200.200.200.1 211.211.211.xx MM_NO_STATE 52 0 ACTIVE (deleted)
#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 211.211.211.xx
protected vrf: (none)
local ident (addr/mask/prot/port): (211.211.211.xx/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (200.200.200.1/255.255.255.255/47/0)
current_peer 200.200.200.1 port 500
PERMIT, flags={origin_is_acl,ipsec_sa_request_sent}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 395, #recv errors 0
local crypto endpt.: 211.211.211.xx, remote crypto endpt.: 200.200.200.1
path mtu 1454, ip mtu 1454, ip mtu idb Dialer1
current outbound spi: 0x0(0)
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
#show ip int br
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 unassigned YES manual up up
FastEthernet0/1 192.168.1.1 YES manual up up
NVI0 unassigned NO unset up up
Virtual-Access1 unassigned YES unset up up
Virtual-Access2 unassigned YES unset up up
Dialer1 211.211.211.xx YES IPCP up up
Tunnel0 10.0.0.2 YES manual up up
Does this mean that only one of the SA of phase2 has established?
Regards,
okumura
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2010 09:43 AM
Hi,
You are having a Phase 2 failure. See below
"Mar 1 00:27:47.489: %CRYPTO-6-IKMP_MODE_FAILURE: Processing of Quick mode failed with peer at 211.211.211.xx"
Please enable "debug crypto isakmp \ debug crypto ipsec" on both routers and go through the debugs, you should be able to see the problem.
If not then please post the debugs and I can take a look.
1. Shutdown the Tunnel on Spoke
2, Enable Debugs on both
3. Re-Enable the Tunnel on Spoke
Thanks,
Naman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2010 06:15 PM
Hi, Naman.
Thank you for your advise.
I have done following step,
1. Shutdown the Tunnel interface on Spoke
2. Enable Debugs on both (debug crypto isakmp \ debug crypto ipsec)
3. Re-Enable the Tunnel interface on Spoke
and I attached debugs by dmvpn_debug.txt.
In the debug output,
*Mar 2 19:42:57.505: IPSEC(validate_transform_proposal): no IPSEC cryptomap exists for local address 172.16.0.2 .
If this is cause of ipsec failure, could you tell me the lack of configuration?
Regards,
okumura
↓(dmvpn_debug.txt)
【DMVPN_HUB】**************************************************************************************
DMVPN_HUB#
*Mar 2 19:42:57.421: IPSEC(key_engine): got a queue event with 1 kei messages
*Mar 2 19:42:57.501: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 172.16.0.2, remote= 211.211.211.xx,
local_proxy= 200.200.200.1/255.255.255.255/47/0 (type=1),
remote_proxy= 211.211.211.xx/255.255.255.255/47/0 (type=1),
protocol= ESP, transform= esp-3des esp-sha-hmac (Tunnel-UDP),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x400
*Mar 2 19:42:57.505: map_db_find_best did not find matching map
*Mar 2 19:42:57.505: IPSEC(validate_transform_proposal): no IPSEC cryptomap exists for local address 172.16.0.2
DMVPN_HUB#
【DMVPN_SPOKE】**************************************************************************************
DMVPN_SPOKE(config-if)#
*Mar 10 19:22:41.825: insert of map into mapdb AVL failed, map + ace pair already exists on the mapdb
*Mar 10 19:22:41.833: ISAKMP: callback: no SA found for 0.0.0.0/0.0.0.0 [vrf 0]
*Mar 10 19:22:41.833: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
*Mar 10 19:22:41.837: IPSEC(recalculate_mtu): reset sadb_root 854B86A0 mtu to 1454
*Mar 10 19:22:41.841: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 211.211.211.xx, remote= 200.200.200.1,
local_proxy= 211.211.211.xx/255.255.255.255/47/0 (type=1),
remote_proxy= 200.200.200.1/255.255.255.255/47/0 (type=1),
protocol= ESP, transform= esp-3des esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x6A009DB2(1778425266), conn_id= 0, keysize= 0, flags= 0x400A
*Mar 10 19:22:41.845: ISAKMP: received ke message (1/1)
*Mar 10 19:22:41.845: ISAKMP:(0:0:N/A:0): SA request profile is (NULL)
*Mar 10 19:22:41.845: ISAKMP: Created a peer struct for 200.200.200.1, peer port 500
*Mar 10 19:22:41.845: ISAKMP:
DMVPN_SPOKE(coNew peer created peer = 0x85A200FC peer_handle = 0x80000106
*Mar 10 19:22:41.845: ISAKMP: Locking peer struct 0x85A200FC, IKE refcount 1 for isakmp_initiator
*Mar 10 19:22:41.845: ISAKMP: local port 500, remote port 500
*Mar 10 19:22:41.849: ISAKMP: set new node 0 to QM_IDLE
*Mar 10 19:22:41.849: insert sa successfully sa = 84F95674
*Mar 10 19:22:41.849: ISAKMP:(0:0:N/A:0):Can not start Aggressive mode, trying Main mode.
*Mar 10 19:22:41.849: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 200.200.200.1
*Mar 10 19:22:41.849: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-07 ID
*Mar 10 19:22:41.849: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-03 ID
*Mar 10 19:22:41.853: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-02 ID
*Mar 10 19:22:41.853: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
*Mar 10 19:22:41.853: ISAKMP:(0:0:N/A:0):Old State = IKE_READY New State = IKE_I_MM1
*Mar 10 19:22:41.853: ISAKMP:(0:0:N/A:0): beginning Main Mode exchange
*Mar 10 19:22:41.853: ISAKMP:(0:0:N/A:0): sending packet to 200.200.200.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Mar 10 19:22:42.101: ISAKMP (0:0): received packet from 200.200.200.1 dport 500 sport 500 Global (I) MM_NO_STATE
*Mar 10 19:22:42.105: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 10 19:22:42.105: ISAKMP:(0:0:N/A:0):Old State = IKE_I_MM1 New State = IKE_I_MM2
*Mar 10 19:22:42.105: ISAKMP:(0:0:N/A:0): processing SA payload. message ID = 0
*Mar 10 19:22:42.105: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 10 19:22:42.109: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 10 19:22:42.109: ISAKMP (0:0): vendor ID is NAT-T v7
*Mar 10 19:22:42.109: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 200.200.200.1
*Mar 10 19:22:42.109: ISAKMP:(0:0:N/A:0): local preshared key found
*Mar 10 19:22:42.109: ISAKMP : Scanning profiles for xauth ...
*Mar 10 19:22:42.109: ISAKMP:(0:0:N/A:0):Checking ISAKMP transform 1 against priority 1 policy
*Mar 10 19:22:42.109: ISAKMP: encryption 3DES-CBC
*Mar 10 19:22:42.109: ISAKMP: hash SHA
*Mar 10 19:22:42.113: ISAKMP: default group 2
*Mar 10 19:22:42.113: ISAKMP: auth pre-share
*Mar 10 19:22:42.113: ISAKMP: life type in seconds
*Mar 10 19:22:42.113: ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x80
*Mar 10 19:22:42.113: ISAKMP:(0:0:N/A:0):atts are acceptable. Next payload is 0
*Mar 10 19:22:42.342: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 10 19:22:42.342: ISAKMP:(0:1:SW:1): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 10 19:22:42.342: ISAKMP (0:134217729): vendor ID is NAT-T v7
*Mar 10 19:22:42.342: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 10 19:22:42.346: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM2 New State = IKE_I_MM2
*Mar 10 19:22:42.350: ISAKMP:(0:1:SW:1): sending packet to 200.200.200.1 my_port 500 peer_port 500 (I) MM_SA_SETUP
*Mar 10 19:22:42.350: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 10 19:22:42.350: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM2 New State = IKE_I_MM3
*Mar 10 19:22:42.654: ISAKMP (0:134217729): received packet from 200.200.200.1 dport 500 sport 500 Global (I) MM_SA_SETUP
*Mar 10 19:22:42.654: ISAKMP:(0:1:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 10 19:22:42.654: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM3 New State = IKE_I_MM4
*Mar 10 19:22:42.658: ISAKMP:(0:1:SW:1): processing KE payload. message ID = 0
*Mar 10 19:22:42.943: ISAKMP:(0:1:SW:1): processing NONCE payload. message ID = 0
*Mar 10 19:22:42.943: ISAKMP:(0:1:SW:1):found peer pre-shared key matching 200.200.200.1
*Mar 10 19:22:42.947: ISAKMP:(0:1:SW:1):SKEYID state generated
*Mar 10 19:22:42.951: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 10 19:22:42.951: ISAKMP:(0:1:SW:1): vendor ID is Unity
*Mar 10 19:22:42.951: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 10 19:22:42.951: ISAKMP:(0:1:SW:1): vendor ID is DPD
*Mar 10 19:22:42.951: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 10 19:22:42.955: ISAKMP:(0:1:SW:1): speaking to another IOS box!
*Mar 10 19:22:42.955: ISAKMP (0:134217729): NAT found, the node outside NAT
*Mar 10 19:22:42.955: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 10 19:22:42.955: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM4 New State = IKE_I_MM4
*Mar 10 19:22:42.959: ISAKMP:(0:1:SW:1):Send initial contact
*Mar 10 19:22:42.959: ISAKMP:(0:1:SW:1):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
*Mar 10 19:22:42.959: ISAKMP (0:134217729): ID payload
next-payload : 8
type : 1
address : 211.211.211.xx
protocol : 17
port : 0
length : 12
*Mar 10 19:22:42.963: ISAKMP:(0:1:SW:1):Total payload length: 12
*Mar 10 19:22:42.963: ISAKMP:(0:1:SW:1): sending packet to 200.200.200.1 my_port 4500 peer_port 4500 (I) MM_KEY_EXCH
*Mar 10 19:22:42.967: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 10 19:22:42.967: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM4 New State = IKE_I_MM5
*Mar 10 19:22:42.987: ISAKMP (0:134217729): received packet from 200.200.200.1 dport 4500 sport 4500 Global (I) MM_KEY_EXCH
*Mar 10 19:22:42.991: ISAKMP:(0:1:SW:1): processing ID payload. message ID = 0
*Mar 10 19:22:42.991: ISAKMP (0:134217729): ID payload
next-payload : 8
type : 1
address : 172.16.0.2
protocol : 17
port : 0
length : 12
*Mar 10 19:22:42.991: ISAKMP:(0:1:SW:1):: peer matches *none* of the profiles
*Mar 10 19:22:42.995: ISAKMP:(0:1:SW:1): processing HASH payload. message ID = 0
*Mar 10 19:22:42.995: ISAKMP:(0:1:SW:1):SA authentication status:
authenticated
*Mar 10 19:22:42.995: ISAKMP:(0:1:SW:1):SA has been authenticated with 200.200.200.1
*Mar 10 19:22:42.995: ISAKMP:(0:1:SW:1):IKE_DPD is enabled, initializing timers
*Mar 10 19:22:42.999: ISAKMP: Trying to insert a peer 211.211.211.xx/200.200.200.1/4500/, and inserted successfully 85A200FC.
*Mar 10 19:22:42.999: ISAKMP:(0:1:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 10 19:22:42.999: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM5 New State = IKE_I_MM6
*Mar 10 19:22:43.003: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 10 19:22:43.003: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM6 New State = IKE_I_MM6
*Mar 10 19:22:43.007: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 10 19:22:43.007: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE
*Mar 10 19:22:43.011: ISAKMP:(0:1:SW:1):beginning Quick Mode exchange, M-ID of 913328703
*Mar 10 19:22:43.015: ISAKMP:(0:1:SW:1): sending packet to 200.200.200.1 my_port 4500 peer_port 4500 (I) QM_IDLE
*Mar 10 19:22:43.015: ISAKMP:(0:1:SW:1):Node 913328703, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
*Mar 10 19:22:43.019: ISAKMP:(0:1:SW:1):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
*Mar 10 19:22:43.019: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
*Mar 10 19:22:43.019: ISAKMP:(0:1:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Mar 10 19:22:43.039: ISAKMP (0:134217729): received packet from 200.200.200.1 dport 4500 sport 4500 Global (I) QM_IDLE
*Mar 10 19:22:43.039: ISAKMP: set new node -116990988 to QM_IDLE
*Mar 10 19:22:43.043: ISAKMP:(0:1:SW:1): processing HASH payload. message ID = -116990988
*Mar 10 19:22:43.043: ISAKMP:(0:1:SW:1): processing NOTIFY PROPOSAL_NOT_CHOSEN protocol 3
spi 1778425266, message ID = -116990988, sa = 84F95674
*Mar 10 19:22:43.047: ISAKMP:(0:1:SW:1): deleting spi 1778425266 message ID = 913328703
*Mar 10 19:22:43.047: ISAKMP:(0:1:SW:1):deleting node 913328703 error TRUE reason "Delete Larval"
*Mar 10 19:22:43.047: ISAKMP:(0:1:SW:1):deleting node -116990988 error FALSE reason "Informational (in) state 1"
*Mar 10 19:22:43.047: ISAKMP:(0:1:SW:1):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY
*Mar 10 19:22:43.047: ISAKMP:(0:1:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Mar 10 19:22:43.812: %LINK-3-UPDOWN: Interface Tunnel0, changed state to up
*Mar 10 19:22:44.814: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to upnfig-if)#
DMVPN_SPOKE(config-if)#
*Mar 10 19:23:07.002: IPSEC(crypto_map_check_encrypt_core): CRYPTO: Packet dropped because cryptomap is currently being created
DMVPN_SPOKE(config-if)#
*Mar 10 19:23:11.842: IPSEC(key_engine): request timer fired: count = 1,
(identity) local= 211.211.211.xx, remote= 200.200.200.1,
local_proxy= 211.211.211.xx/255.255.255.255/47/0 (type=1),
remote_proxy= 200.200.200.1/255.255.255.255/47/0 (type=1)
*Mar 10 19:23:11.842: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 211.211.211.xx, remote= 200.200.200.1,
local_proxy= 211.211.211.xx/255.255.255.255/47/0 (type=1),
remote_proxy= 200.200.200.1/255.255.255.255/47/0 (type=1),
protocol= ESP, transform= esp-3des esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0xECDAEEE2(3973770978), conn_id= 0, keysize= 0, flags= 0x400A
*Mar 10 19:23:11.846: ISAKMP: received ke message (1/1)
*Mar 10 19:23:11.846: ISAKMP:(0:0:N/A:0): SA request profile is (NULL)
*Mar 10 19:23:11.846: ISAKMP: Created a peer struct for 200.200.200.1, peer port 500
*Mar 10 19:23:11.850: ISAKMP: New peer created peer = 0x8557B900 peer_handle = 0x80000107
*Mar
DMVPN_SPOKE(co10 19:23:11.850: ISAKMP: Locking peer struct 0x8557B900, IKE refcount 1 for isakmp_initiator
*Mar 10 19:23:11.850: ISAKMP: local port 500, remote port 500
*Mar 10 19:23:11.850: ISAKMP: set new node 0 to QM_IDLE
*Mar 10 19:23:11.850: ISAKMP: Find a dup sa in the avl tree during calling isadb_insert sa = 84496E14
*Mar 10 19:23:11.850: ISAKMP:(0:0:N/A:0):Can not start Aggressive mode, trying Main mode.
*Mar 10 19:23:11.854: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 200.200.200.1
*Mar 10 19:23:11.854: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-07 ID
*Mar 10 19:23:11.854: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-03 ID
*Mar 10 19:23:11.854: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-02 ID
*Mar 10 19:23:11.854: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
*Mar 10 19:23:11.854: ISAKMP:(0:0:N/A:0):Old State = IKE_READY New State = IKE_I_MM1
*Mar 10 19:23:11.858: ISAKMP:(0:0:N/A:0): beginning Main Mode exchange
*Mar 10 19:23:11.858: ISAKMP:(0:0:N/A:0): sending packet to 200.200.200.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Mar 10 19:23:12.106: ISAKMP (0:0): received packet from 200.200.200.1 dport 500 sport 500 Global (I) MM_NO_STATE
*Mar 10 19:23:12.106: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 10 19:23:12.110: ISAKMP:(0:0:N/A:0):Old State = IKE_I_MM1 New State = IKE_I_MM2
*Mar 10 19:23:12.110: ISAKMP:(0:0:N/A:0): processing SA payload. message ID = 0
*Mar 10 19:23:12.110: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 10 19:23:12.114: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 10 19:23:12.114: ISAKMP (0:0): vendor ID is NAT-T v7
*Mar 10 19:23:12.114: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 200.200.200.1
*Mar 10 19:23:12.114: ISAKMP:(0:0:N/A:0): local preshared key found
*Mar 10 19:23:12.114: ISAKMP : Scanning profiles for xauth ...
*Mar 10 19:23:12.114: ISAKMP:(0:0:N/A:0):Checking ISAKMP transform 1 against priority 1 policy
*Mar 10 19:23:12.114: ISAKMP: encryption 3DES-CBC
*Mar 10 19:23:12.118: ISAKMP: hash SHA
*Mar 10 19:23:12.118: ISAKMP: default group 2
*Mar 10 19:23:12.118: ISAKMP: auth pre-share
*Mar 10 19:23:12.118: ISAKMP: life type in seconds
*Mar 10 19:23:12.118: ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x80
*Mar 10 19:23:12.118: ISAKMP:(0:0:N/A:0):atts are acceptable. Next payload is 0
*Mar 10 19:23:12.351: ISAKMP:(0:2:SW:1): processing vendor id payload
*Mar 10 19:23:12.351: ISAKMP:(0:2:SW:1): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 10 19:23:12.351: ISAKMP (0:134217730): vendor ID is NAT-T v7
*Mar 10 19:23:12.351: ISAKMP:(0:2:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 10 19:23:12.355: ISAKMP:(0:2:SW:1):Old State = IKE_I_MM2 New State = IKE_I_MM2
*Mar 10 19:23:12.359: ISAKMP:(0:2:SW:1): sending packet to 200.200.200.1 my_port 500 peer_port 500 (I) MM_SA_SETUP
*Mar 10 19:23:12.359: ISAKMP:(0:2:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 10 19:23:12.359: ISAKMP:(0:2:SW:1):Old State = IKE_I_MM2 New State = IKE_I_MM3
*Mar 10 19:23:12.663: ISAKMP (0:134217730): received packet from 200.200.200.1 dport 500 sport 500 Global (I) MM_SA_SETUP
*Mar 10 19:23:12.667: ISAKMP:(0:2:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 10 19:23:12.667: ISAKMP:(0:2:SW:1):Old State = IKE_I_MM3 New State = IKE_I_MM4
*Mar 10 19:23:12.671: ISAKMP:(0:2:SW:1): processing KE payload. message ID = 0
*Mar 10 19:23:12.956: ISAKMP:(0:2:SW:1): processing NONCE payload. message ID = 0
*Mar 10 19:23:12.960: ISAKMP:(0:2:SW:1):found peer pre-shared key matching 200.200.200.1
*Mar 10 19:23:12.964: ISAKMP:(0:2:SW:1):SKEYID state generated
*Mar 10 19:23:12.964: ISAKMP:(0:2:SW:1): processing vendor id payload
*Mar 10 19:23:12.964: ISAKMP:(0:2:SW:1): vendor ID is Unity
*Mar 10 19:23:12.964: ISAKMP:(0:2:SW:1): processing vendor id payload
*Mar 10 19:23:12.964: ISAKMP:(0:2:SW:1): vendor ID is DPD
*Mar 10 19:23:12.968: ISAKMP:(0:2:SW:1): processing vendor id payload
*Mar 10 19:23:12.968: ISAKMP:(0:2:SW:1): speaking to another IOS box!
*Mar 10 19:23:12.968: ISAKMP (0:134217730): NAT found, the node outside NAT
*Mar 10 19:23:12.968: ISAKMP:(0:2:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 10 19:23:12.968: ISAKMP:(0:2:SW:1):Old State = IKE_I_MM4 New State = IKE_I_MM4
*Mar 10 19:23:12.972: ISAKMP:(0:2:SW:1):Send initial contact
*Mar 10 19:23:12.972: ISAKMP:(0:2:SW:1):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
*Mar 10 19:23:12.976: ISAKMP (0:134217730): ID payload
next-payload : 8
type : 1
address : 211.211.211.xx
protocol : 17
port : 0
length : 12
*Mar 10 19:23:12.976: ISAKMP:(0:2:SW:1):Total payload length: 12
*Mar 10 19:23:12.980: ISAKMP:(0:2:SW:1): sending packet to 200.200.200.1 my_port 4500 peer_port 4500 (I) MM_KEY_EXCH
*Mar 10 19:23:12.980: ISAKMP:(0:2:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 10 19:23:12.980: ISAKMP:(0:2:SW:1):Old State = IKE_I_MM4 New State = IKE_I_MM5
*Mar 10 19:23:13.004: ISAKMP (0:134217729): received packet from 200.200.200.1 dport 4500 sport 4500 Global (I) QM_IDLE
*Mar 10 19:23:13.004: ISAKMP: set new node -1556145704 to QM_IDLE
*Mar 10 19:23:13.008: ISAKMP:(0:1:SW:1): processing HASH payload. message ID = -1556145704
*Mar 10 19:23:13.008: ISAKMP:(0:1:SW:1): processing DELETE payload. message ID = -1556145704
*Mar 10 19:23:13.008: ISAKMP:(0:1:SW:1):peer does not do paranoid keepalives.
*Mar 10 19:23:13.012: ISAKMP:(0:1:SW:1):deleting SA reason "No reason" state (I) QM_IDLE (peer 200.200.200.1)
*Mar 10 19:23:13.012: ISAKMP:(0:1:SW:1):deleting node -1556145704 error FALSE reason "Informational (in) state 1"
*Mar 10 19:23:13.016: ISAKMP: set new node 1526681295 to QM_IDLE
*Mar 10 19:23:13.020: ISAKMP:(0:1:SW:1): sending packet to 200.200.200.1 my_port 4500 peer_port 4500 (I) QM_IDLE
*Mar 10 19:23:13.020: ISAKMP:(0:1:SW:1):purging node 1526681295
*Mar 10 19:23:13.024: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Mar 10 19:23:13.024: ISAKMP:(0:1:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_DEST_SA
*Mar 10 19:23:13.024: ISAKMP (0:134217730): received packet from 200.200.200.1 dport 4500 sport 4500 Global (I) MM_KEY_EXCH
*Mar 10 19:23:13.028: ISAKMP:(0:2:SW:1): processing ID payload. message ID = 0
*Mar 10 19:23:13.028: ISAKMP (0:134217730): ID payload
next-payload : 8
type : 1
address : 172.16.0.2
protocol : 17
port : 0
length : 12
*Mar 10 19:23:13.028: ISAKMP:(0:2:SW:1):: peer matches *none* of the profiles
*Mar 10 19:23:13.028: ISAKMP:(0:2:SW:1): processing HASH payload. message ID = 0
*Mar 10 19:23:13.032: ISAKMP:(0:2:SW:1):SA authentication status:
authenticated
*Mar 10 19:23:13.032: ISAKMP:(0:2:SW:1):SA has been authenticated with 200.200.200.1
*Mar 10 19:23:13.032: ISAKMP:(0:2:SW:1):IKE_DPD is enabled, initializing timers
*Mar 10 19:23:13.032: ISAKMP: Trying to insert a peer 211.211.211.xx/200.200.200.1/4500/, and found existing one 85A200FC to reuse, free 8557B900
*Mar 10 19:23:13.036: ISAKMP:(0:2:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 10 19:23:13.036: ISAKMP:(0:2:SW:1):Old State = IKE_I_MM5 New State = IKE_I_MM6
*Mar 10 19:23:13.040: ISAKMP:(0:1:SW:1):deleting SA reason "No reason" state (I) QM_IDLE (peer 200.200.200.1)
*Mar 10 19:23:13.040: ISAKMP: Unlocking IKE struct 0x85A200FC for isadb_mark_sa_deleted(), count 1
*Mar 10 19:23:13.040: ISAKMP:(0:1:SW:1):deleting node 913328703 error FALSE reason "IKE deleted"
*Mar 10 19:23:13.040: ISAKMP:(0:1:SW:1):deleting node -116990988 error FALSE reason "IKE deleted"
*Mar 10 19:23:13.040: ISAKMP:(0:1:SW:1):deleting node -1556145704 error FALSE reason "IKE deleted"
*Mar 10 19:23:13.044: ISAKMP:(0:1:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 10 19:23:13.044: ISAKMP:(0:1:SW:1):Old State = IKE_DEST_SA New State = IKE_DEST_SA
*Mar 10 19:23:13.048: ISAKMP:(0:2:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 10 19:23:13.048: ISAKMP:(0:2:SW:1):Old State = IKE_I_MM6 New State = IKE_I_MM6
*Mar 10 19:23:13.048: ISAKMP:(0:2:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 10 19:23:13.052: ISAKMP:(0:2:SW:1):Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE
*Mar 10 19:23:13.052: ISAKMP:(0:2:SW:1):beginning Quick Mode exchange, M-ID of 512460017
*Mar 10 19:23:13.060: ISAKMP:(0:2:SW:1): sending packet to 200.200.200.1 my_port 4500 peer_port 4500 (I) QM_IDLE
*Mar 10 19:23:13.060: ISAKMP:(0:2:SW:1):Node 512460017, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
*Mar 10 19:23:13.060: ISAKMP:(0:2:SW:1):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
*Mar 10 19:23:13.064: ISAKMP:(0:2:SW:1):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
*Mar 10 19:23:13.064: ISAKMP:(0:2:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Mar 10 19:23:13.088: ISAKMP (0:134217730): received packet from 200.200.200.1 dport 4500 sport 4500 Global (I) QM_IDLE
*Mar 10 19:23:13.088: ISAKMP: set new node 1095942895 to QM_IDLE
*Mar 10 19:23:13.092: ISAKMP:(0:2:SW:1): processing HASH payload. message ID = 1095942895
*Mar 10 19:23:13.092: ISAKMP:(0:2:SW:1): processing NOTIFY PROPOSAL_NOT_CHOSEN protocol 3
spi 3973770978, message ID = 1095942895, sa = 84496E14
*Mar 10 19:23:13.092: ISAKMP:(0:2:SW:1): deleting spi 3973770978 message ID = 512460017
*Mar 10 19:23:13.092: ISAKMP:(0:2:SW:1):deleting node 512460017 error TRUE reason "Delete Larval"
*Mar 10 19:23:13.096: ISAKMP:(0:2:SW:1):deleting node 1095942895 error FALSE reason "Informational (in) state 1"
*Mar 10 19:23:13.096: ISAKMP:(0:2:SW:1):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY
*Mar 10 19:23:13.096: ISAKMP:(0:2:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
nfig-if)#
DMVPN_SPOKE(config-if)#
*Mar 10 19:23:41.843: IPSEC(key_engine): request timer fired: count = 2,
(identity) local= 211.211.211.xx, remote= 200.200.200.1,
local_proxy= 211.211.211.xx/255.255.255.255/47/0 (type=1),
remote_proxy= 200.200.200.1/255.255.255.255/47/0 (type=1)
*Mar 10 19:23:41.843: ISAKMP: received ke message (3/1)
*Mar 10 19:23:41.843: ISAKMP:(0:2:SW:1):peer does not do paranoid keepalives.
*Mar 10 19:23:41.847: ISAKMP:(0:2:SW:1):deleting SA reason "P1 delete notify (in)" state (I) QM_IDLE (peer 200.200.200.1)
*Mar 10 19:23:41.847: ISAKMP:(0:1:SW:1):peer does not do paranoid keepalives.
*Mar 10 19:23:41.851: ISAKMP: set new node 1864681754 to QM_IDLE
*Mar 10 19:23:41.851: ISAKMP:(0:2:SW:1): sending packet to 200.200.200.1 my_port 4500 peer_port 4500 (I) QM_IDLE
*Mar 10 19:23:41.855: ISAKMP:(0:2:SW:1):purging node 1864681754
*Mar 10 19:23:41.855: ISAKMP:(0:2:SW:1):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Mar 10 19:23:41.855: ISAKMP:(0:2:SW:1):Ol
DMVPN_SPOKE(cod State = IKE_P1_COMPLETE New State = IKE_DEST_SA
*Mar 10 19:23:41.859: ISAKMP:(0:2:SW:1):deleting SA reason "No reason" state (I) QM_IDLE (peer 200.200.200.1)
*Mar 10 19:23:41.859: ISAKMP: Unlocking IKE struct 0x85A200FC for isadb_mark_sa_deleted(), count 0
*Mar 10 19:23:41.859: ISAKMP: Deleting peer node by peer_reap for 200.200.200.1: 85A200FC
*Mar 10 19:23:41.863: ISAKMP:(0:2:SW:1):deleting node 512460017 error FALSE reason "IKE deleted"
*Mar 10 19:23:41.863: ISAKMP:(0:2:SW:1):deleting node 1095942895 error FALSE reason "IKE deleted"
*Mar 10 19:23:41.863: ISAKMP:(0:2:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 10 19:23:41.863: ISAKMP:(0:2:SW:1):Old State = IKE_DEST_SA New State = IKE_DEST_SA
*Mar 10 19:23:41.867: IPSEC(key_engine): got a queue event with 1 kei messages
*Mar 10 19:23:41.871: ISAKMP (0:134217730): received packet from 200.200.200.1 dport 4500 sport 4500 Global (I) MM_NO_STATEnfig-if)#
DMVPN_SPOKE(config-if)#
*Mar 10 19:23:51.831: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 211.211.211.xx, remote= 200.200.200.1,
local_proxy= 211.211.211.xx/255.255.255.255/47/0 (type=1),
remote_proxy= 200.200.200.1/255.255.255.255/47/0 (type=1),
protocol= ESP, transform= esp-3des esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0xE10316A7(3775076007), conn_id= 0, keysize= 0, flags= 0x400A
*Mar 10 19:23:51.835: ISAKMP: received ke message (1/1)
*Mar 10 19:23:51.835: ISAKMP:(0:0:N/A:0): SA request profile is (NULL)
*Mar 10 19:23:51.835: ISAKMP: Created a peer struct for 200.200.200.1, peer port 500
*Mar 10 19:23:51.835: ISAKMP: New peer created peer = 0x85A200FC peer_handle = 0x80000109
*Mar 10 19:23:51.839: ISAKMP: Locking peer struct 0x85A200FC, IKE refcount 1 for isakmp_initiator
*Mar 10 19:23:51.839: ISAKMP: local port 500, remote port 500
*Mar 10 19:23:51.839: ISAKMP: set new node 0 to QM_IDLE
*Mar 10 19:23:51.839: ISAKMP: Find a dup sa
DMVPN_SPOKE(co in the avl tree during calling isadb_insert sa = 84497D68
*Mar 10 19:23:51.839: ISAKMP:(0:0:N/A:0):Can not start Aggressive mode, trying Main mode.
*Mar 10 19:23:51.839: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 200.200.200.1
*Mar 10 19:23:51.843: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-07 ID
*Mar 10 19:23:51.843: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-03 ID
*Mar 10 19:23:51.843: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-02 ID
*Mar 10 19:23:51.843: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
*Mar 10 19:23:51.843: ISAKMP:(0:0:N/A:0):Old State = IKE_READY New State = IKE_I_MM1
*Mar 10 19:23:51.843: ISAKMP:(0:0:N/A:0): beginning Main Mode exchange
*Mar 10 19:23:51.848: ISAKMP:(0:0:N/A:0): sending packet to 200.200.200.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Mar 10 19:23:52.092: ISAKMP (0:0): received packet from 200.200.200.1 dport 500 sport 500 Global (I) MM_NO_STATE
*Mar 10 19:23:52.092: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 10 19:23:52.092: ISAKMP:(0:0:N/A:0):Old State = IKE_I_MM1 New State = IKE_I_MM2
*Mar 10 19:23:52.096: ISAKMP:(0:0:N/A:0): processing SA payload. message ID = 0
*Mar 10 19:23:52.096: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 10 19:23:52.096: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 10 19:23:52.096: ISAKMP (0:0): vendor ID is NAT-T v7
*Mar 10 19:23:52.100: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 200.200.200.1
*Mar 10 19:23:52.100: ISAKMP:(0:0:N/A:0): local preshared key found
*Mar 10 19:23:52.100: ISAKMP : Scanning profiles for xauth ...
*Mar 10 19:23:52.100: ISAKMP:(0:0:N/A:0):Checking ISAKMP transform 1 against priority 1 policy
*Mar 10 19:23:52.100: ISAKMP: encryption 3DES-CBC
*Mar 10 19:23:52.100: ISAKMP: hash SHA
*Mar 10 19:23:52.100: ISAKMP: default group 2
*Mar 10 19:23:52.100: ISAKMP: auth pre-share
*Mar 10 19:23:52.104: ISAKMP: life type in seconds
*Mar 10 19:23:52.104: ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x80
*Mar 10 19:23:52.104: ISAKMP:(0:0:N/A:0):atts are acceptable. Next payload is 0
*Mar 10 19:23:52.332: ISAKMP:(0:3:SW:1): processing vendor id payload
*Mar 10 19:23:52.332: ISAKMP:(0:3:SW:1): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 10 19:23:52.332: ISAKMP (0:134217731): vendor ID is NAT-T v7
*Mar 10 19:23:52.336: ISAKMP:(0:3:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 10 19:23:52.336: ISAKMP:(0:3:SW:1):Old State = IKE_I_MM2 New State = IKE_I_MM2
*Mar 10 19:23:52.340: ISAKMP:(0:3:SW:1): sending packet to 200.200.200.1 my_port 500 peer_port 500 (I) MM_SA_SETUP
*Mar 10 19:23:52.340: ISAKMP:(0:3:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 10 19:23:52.340: ISAKMP:(0:3:SW:1):Old State = IKE_I_MM2 New State = IKE_I_MM3
*Mar 10 19:23:52.645: ISAKMP (0:134217731): received packet from 200.200.200.1 dport 500 sport 500 Global (I) MM_SA_SETUP
*Mar 10 19:23:52.645: ISAKMP:(0:3:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 10 19:23:52.645: ISAKMP:(0:3:SW:1):Old State = IKE_I_MM3 New State = IKE_I_MM4
*Mar 10 19:23:52.649: ISAKMP:(0:3:SW:1): processing KE payload. message ID = 0
*Mar 10 19:23:52.945: ISAKMP:(0:3:SW:1): processing NONCE payload. message ID = 0
*Mar 10 19:23:52.945: ISAKMP:(0:3:SW:1):found peer pre-shared key matching 200.200.200.1
*Mar 10 19:23:52.949: ISAKMP:(0:3:SW:1):SKEYID state generated
*Mar 10 19:23:52.949: ISAKMP:(0:3:SW:1): processing vendor id payload
*Mar 10 19:23:52.949: ISAKMP:(0:3:SW:1): vendor ID is Unity
*Mar 10 19:23:52.953: ISAKMP:(0:3:SW:1): processing vendor id payload
*Mar 10 19:23:52.953: ISAKMP:(0:3:SW:1): vendor ID is DPD
*Mar 10 19:23:52.953: ISAKMP:(0:3:SW:1): processing vendor id payload
*Mar 10 19:23:52.953: ISAKMP:(0:3:SW:1): speaking to another IOS box!
*Mar 10 19:23:52.953: ISAKMP (0:134217731): NAT found, the node outside NAT
*Mar 10 19:23:52.957: ISAKMP:(0:3:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 10 19:23:52.957: ISAKMP:(0:3:SW:1):Old State = IKE_I_MM4 New State = IKE_I_MM4
*Mar 10 19:23:52.961: ISAKMP:(0:3:SW:1):Send initial contact
*Mar 10 19:23:52.961: ISAKMP:(0:3:SW:1):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
*Mar 10 19:23:52.961: ISAKMP (0:134217731): ID payload
next-payload : 8
type : 1
address : 211.211.211.xx
protocol : 17
port : 0
length : 12
*Mar 10 19:23:52.965: ISAKMP:(0:3:SW:1):Total payload length: 12
*Mar 10 19:23:52.969: ISAKMP:(0:3:SW:1): sending packet to 200.200.200.1 my_port 4500 peer_port 4500 (I) MM_KEY_EXCH
*Mar 10 19:23:52.969: ISAKMP:(0:3:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 10 19:23:52.969: ISAKMP:(0:3:SW:1):Old State = IKE_I_MM4 New State = IKE_I_MM5
*Mar 10 19:23:52.989: ISAKMP (0:134217731): received packet from 200.200.200.1 dport 4500 sport 4500 Global (I) MM_KEY_EXCH
*Mar 10 19:23:52.993: ISAKMP:(0:3:SW:1): processing ID payload. message ID = 0
*Mar 10 19:23:52.993: ISAKMP (0:134217731): ID payload
next-payload : 8
type : 1
address : 172.16.0.2
protocol : 17
port : 0
length : 12
*Mar 10 19:23:52.997: ISAKMP:(0:3:SW:1):: peer matches *none* of the profiles
*Mar 10 19:23:52.997: ISAKMP:(0:3:SW:1): processing HASH payload. message ID = 0
*Mar 10 19:23:52.997: ISAKMP:(0:3:SW:1):SA authentication status:
authenticated
*Mar 10 19:23:52.997: ISAKMP:(0:3:SW:1):SA has been authenticated with 200.200.200.1
*Mar 10 19:23:52.997: ISAKMP:(0:3:SW:1):IKE_DPD is enabled, initializing timers
*Mar 10 19:23:53.001: ISAKMP: Trying to insert a peer 211.211.211.xx/200.200.200.1/4500/, and inserted successfully 85A200FC.
*Mar 10 19:23:53.001: ISAKMP:(0:3:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 10 19:23:53.001: ISAKMP:(0:3:SW:1):Old State = IKE_I_MM5 New State = IKE_I_MM6
*Mar 10 19:23:53.005: ISAKMP:(0:3:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 10 19:23:53.005: ISAKMP:(0:3:SW:1):Old State = IKE_I_MM6 New State = IKE_I_MM6
*Mar 10 19:23:53.009: ISAKMP:(0:3:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 10 19:23:53.009: ISAKMP:(0:3:SW:1):Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE
*Mar 10 19:23:53.013: ISAKMP:(0:3:SW:1):beginning Quick Mode exchange, M-ID of 1856229624
*Mar 10 19:23:53.017: ISAKMP:(0:3:SW:1): sending packet to 200.200.200.1 my_port 4500 peer_port 4500 (I) QM_IDLE
*Mar 10 19:23:53.021: ISAKMP:(0:3:SW:1):Node 1856229624, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
*Mar 10 19:23:53.021: ISAKMP:(0:3:SW:1):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
*Mar 10 19:23:53.021: ISAKMP:(0:3:SW:1):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
*Mar 10 19:23:53.021: ISAKMP:(0:3:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Mar 10 19:23:53.041: ISAKMP (0:134217731): received packet from 200.200.200.1 dport 4500 sport 4500 Global (I) QM_IDLE
*Mar 10 19:23:53.041: ISAKMP: set new node -1096124930 to QM_IDLE
*Mar 10 19:23:53.045: ISAKMP:(0:3:SW:1): processing HASH payload. message ID = -1096124930
*Mar 10 19:23:53.045: ISAKMP:(0:3:SW:1): processing NOTIFY PROPOSAL_NOT_CHOSEN protocol 3
spi 3775076007, message ID = -1096124930, sa = 84497D68
*Mar 10 19:23:53.049: ISAKMP:(0:3:SW:1): deleting spi 3775076007 message ID = 1856229624
*Mar 10 19:23:53.049: ISAKMP:(0:3:SW:1):deleting node 1856229624 error TRUE reason "Delete Larval"
*Mar 10 19:23:53.049: ISAKMP:(0:3:SW:1):deleting node -1096124930 error FALSE reason "Informational (in) state 1"
*Mar 10 19:23:53.049: ISAKMP:(0:3:SW:1):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY
*Mar 10 19:23:53.049: ISAKMP:(0:3:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
nfig-if)#
DMVPN_SPOKE(config-if)#
*Mar 10 19:24:03.042: ISAKMP:(0:1:SW:1):purging node 913328703
*Mar 10 19:24:03.042: ISAKMP:(0:1:SW:1):purging node -116990988
*Mar 10 19:24:03.046: ISAKMP:(0:1:SW:1):purging node -1556145704
DMVPN_SPOKE(config-if)#
*Mar 10 19:24:13.046: ISAKMP:(0:1:SW:1):purging SA., sa=84F95674, delme=84F95674
DMVPN_SPOKE(config-if)#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2010 06:56 AM
Hi Tomoyuki,
Please change the IPSec Transform set to transport mode as below (On both Hub and Spoke)
crypto ipsec transform-set DMVPNSET esp-3des esp-sha-hmac
mode transport
Thanks,
Naman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2010 06:57 PM
Hi, Naman.
Thank you for your reply!
IPSEC phase2 has established!
Is the reason that crypt mode must be "transport" written in the following document?
"Note If encryption is used, then IPsec transport mode must be used to enable NHRP. "
Is this proper reason?
Best Regards,
okumura
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2010 11:07 AM
Hi Omkura,
Yes. Transport mode must be used when any device is behind NAT.
Thanks,
Naman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2010 10:06 PM
Hi, Naman.
Thank you for your nice Advise!
Best Regards,
okumura
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2010 06:33 AM
You are Welcome.
Please do not forget to mark your thread as answered when you get the answer you are looking for.
Thanks,
Naman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-23-2010 04:11 PM
Hi,
A trouble has occured.
I posted another thread.
https://supportforums.cisco.com/message/3255959#3255959
thanks.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: