- Cisco Community
- Technology and Support
- Security
- VPN
- Ezvpn Remote, not allowed to NAT Exempt inside
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2011 11:53 AM
I am a bit baffled as to why I am not allowed to have this NAT exemption rule in place while the EZVPN Remote is enabled.
Here is my topology: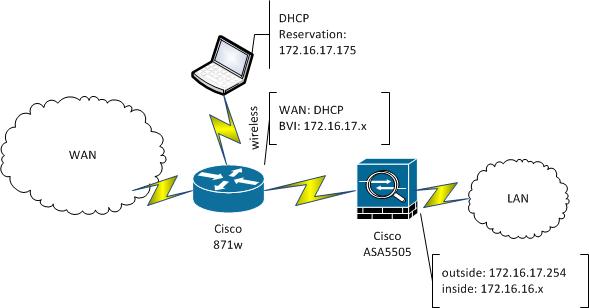
I created a DHCP pool reservation based off of the MAC address of my laptop; this receives the reservation address. I then created a NAT exemption to allow my laptop to communicate with 172.16.16.x network. Below is the config:
access-list inside_nat0_outbound extended permit ip 172.16.16.0 255.255.255.0 host 172.16.17.175
global (inside) 1 interface
global (outside) 1 interface
global (guest) 1 interface
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 0.0.0.0 0.0.0.0
nat (guest) 1 0.0.0.0 0.0.0.0
This works great, but I am unable to enable the EZVPN Remote that I have configured on the ASA. Below is the error:
Result of the command: "vpnclient enable"
* Remove "nat (inside) 0 inside_nat0_outbound"
CONFIG CONFLICT: Configuration that would prevent successful Cisco Easy VPN Remote
operation has been detected, and is listed above. Please resolve the
above configuration conflict(s) and re-enable.
I am looking for two things an explanation as to why this is and why this is not allowed and help configuring a work around so that both can be enabled. Any help would be appreciated.
Thanks,
Steve
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2011 07:00 PM
OK, makes sense now.
So NAT exemption is out of the game as per my post earlier (can't configure NAT exemption and Easy VPN remote on the same ASA).
Second option, i haven't tested this myself, so just my theory that you can test:
no nat-control
Since you don't have nat statement on your outside interface, it should allow you access.
Or third option, also never tested:
access-list static-nonat permit ip 172.16.16.0 255.255.255.0 172.16.17.0 255.255.255.0
static (inside,outside) 172.16.16.0 access-list static-nonat
Unfortunately there is limitation once the ASA is configured as Easy VPN remote as it is meant to be used just to access HQ site.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2011 06:39 PM
You do not have to configure and you can't configuire NAT exemption on Easy VPN remote as it is already automatically allowed when you enable
the ASA as an Easy VPN remote device. So it will exempt 172.16.16.0/24 from being NATed when accessing LAN behind Easy VPN server.
Here is a sample configuration that you can check out for Easy VPN remote on ASA:
Hope that answers your question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2011 06:45 PM
I'm sorry, I should have specified that the EZVPN Remote is connecting to a completely different network. The
Topology map is how the devices are connected in my office. From the LAN to WAN (Switch)-->(ASA)-->(871w)--Internet. The ASA is configured in routed mode, the outside interface is 172.16.17.254, the inside interface is 172.16.16.254, the 871w is 172.16.17.1. My laptop connects to the 871w, receives a DHCP reservation. I modified my "outside" ACL to permit 172.16.17.175 to access 172.16.16.0/24. I then had to create a NAT exemption to allow access from that IP address to the 172.16.16.x network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2011 07:00 PM
OK, makes sense now.
So NAT exemption is out of the game as per my post earlier (can't configure NAT exemption and Easy VPN remote on the same ASA).
Second option, i haven't tested this myself, so just my theory that you can test:
no nat-control
Since you don't have nat statement on your outside interface, it should allow you access.
Or third option, also never tested:
access-list static-nonat permit ip 172.16.16.0 255.255.255.0 172.16.17.0 255.255.255.0
static (inside,outside) 172.16.16.0 access-list static-nonat
Unfortunately there is limitation once the ASA is configured as Easy VPN remote as it is meant to be used just to access HQ site.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2011 09:25 AM
OK I followed your advice and read up on "no nat-control"
I entered the command and seen via the ASDM I was receiving this error:
5 Mar 03 2011 11:11:48 305013 PC 3389 Asymmetric
NAT rules matched for forward and reverse flows; Connection for tcp src outside:PCx/49600
dst inside:Server/3389 denied due to NAT reverse path failure
I then enabled "nat-control" and added your third option. I received the following errors.
Result of the command: "access-list static-nonat permit ip 172.16.16.0 255.255.255.0
172.16.17.0 255.255.255.0"
The command has been sent to the device
Result of the command: "static (inside,outside) 172.16.16.0 access-list static-nonat"
WARNING: real-address conflict with existing static
UDP inside:PC/69 to outside:172.16.17.254/69 netmask 255.255.255.255
WARNING: real-address conflict with existing static
TCP inside:Server/21 to outside:172.16.17.254/21 netmask 255.255.255.255
WARNING: real-address conflict with existing static
TCP inside:Server/20 to outside:172.16.17.254/20 netmask 255.255.255.255
...
This did allow me to access the inside resources from my laptop. Additionally, it allowed me to enable the VPN Client.
I then tested my other static entries, I was able to copy the running-config via tftp from a remote router. The previous static entries don't seem affected by the static command. I also tested a few other services that I have static entries for and everything is working. Whenever I add or remove a static entry I still receive a warning but beyond that it works.
I wonder what future problems if any I will have?
Also, would this issue be resolved if I upgraded to 8.4.1?
Thank you again for your help.
Steve
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2011 02:13 AM
The warning messages are OK, as it just tells you that you have use the same internal ip for other static translation. But since you have configured ACL to have a more specific destination subnet, it will be no issue.
Typically easy vpn remote is not used in how you configure it at the moment, so it's a little bit of a funky setup.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

