- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Firepower 1010 Dynamic S2S
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Firepower 1010 Dynamic S2S
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2022 03:15 AM
Dear Community Members,
We have a Firepower 1010 which we use for multiple S2S VPN Tunnels (13 Tunnels).
The endpoints are cradlepoint IBR-900's.
Due to the fact that these endpoints are mobile routers the IP-address changes quiete frequently (once a week)
Which results in a drop of the tunnel untill we manually update the tunnels with the new WAN-IP.
We tried to fix this issue by using a dynamic S2S profile.
When we add a few mobile routers to this dynamic profile the tunnels come up just as intended.
But when we add more than 4 routers all the dynamic tunnels drop and aren't able to reconnect.
I'm not able to see anything in the log files as to why this is happening.
Has anyone ever experienced something similar?
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2022 03:49 AM
Does it happen with *more* than four peers or with the *forth* peer? It could be related to the applied group-policy:
group-policy DfltGrpPolicy attributes
vpn-simultaneous-logins 3- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2022 03:59 AM
It happens with more than four peers.
After the fourth peer connects all the synamic connections are dropped
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2022 04:16 AM - edited 11-21-2022 04:18 AM
If there is nothing in the logs (did you check the log-levels?) you should activate the crypto ikev1/ikev2 debugs. Can you post the relevant config:
- tunnel-group
- group-policy
- crypto-map entry
- dynamic crypto-map entry
- and all referenced elements (all without PSK)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2022 01:50 AM - edited 11-23-2022 02:06 AM
Hi Karsten,
Sorry for the late reply.
Here's the config you asked for.
Tunnel group
tunnel-group DefaultL2LGroup general-attributes
default-group-policy |s2sGP|dynamic
tunnel-group DefaultL2LGroup ipsec-attributes
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
Group policy
group-policy |s2sGP|dynamic internal
group-policy |s2sGP|dynamic attributes
vpn-tunnel-protocol ikev2
Crypto Map
crypto ipsec ikev2 ipsec-proposal VCS
protocol esp encryption aes-256
protocol esp integrity sha-256
crypto dynamic-map s2sDynamicCryptoMap 46 match address |s2sAcl|831acd42-6b0a-11ed-96a8-61c52c7995b9
crypto dynamic-map s2sDynamicCryptoMap 46 set pfs
crypto dynamic-map s2sDynamicCryptoMap 46 set ikev2 ipsec-proposal VCS
crypto dynamic-map s2sDynamicCryptoMap 46 set security-association lifetime seconds 28800
crypto dynamic-map s2sDynamicCryptoMap 46 set security-association lifetime kilobytes unlimited
crypto map s2sCryptoMap 30000 ipsec-isakmp dynamic s2sDynamicCryptoMap
crypto map s2sCryptoMap interface outside
crypto ikev2 policy 2
encryption aes-256
integrity sha512
group 21 20 14
prf sha512
lifetime seconds 28800
object network ALM-LAN
subnet 10.3.x.x 255.255.x.x
object network MSP001_LAN
subnet 192.168.x.x 255.255.255.248
object network MSP002_LAN
subnet 192.168.x.x 255.255.255.248
object network MSP003_LAN
subnet 192.168.x.x 255.255.255.248
object network MSP004_LAN
subnet 192.168.x.x 255.255.255.248
object network MSP005_LAN
subnet 192.168.x.x 255.255.255.248
object network MSP012_LAN
subnet 192.168.x.x 255.255.255.248
object network MSP006_LAN
subnet 192.168.x.x 255.255.255.248
object network MSP008_LAN
subnet 192.168.x.x 255.255.255.248
object network MSP007_LAN
subnet 192.168.x.x 255.255.255.248
object network MSP009_LAN
subnet 192.168.x.x 255.255.255.248
object network MSP010_LAN
subnet 192.168.x.x 255.255.255.248
object-group network |s2sAclSrcNwgV4|831acd42-6b0a-11ed-96a8-61c52c7995b9
network-object object ALM-LAN
object-group network |s2sAclDestNwgV4|831acd42-6b0a-11ed-96a8-61c52c7995b9
network-object object MSP001_LAN
network-object object MSP003_LAN
network-object object MSP004_LAN
network-object object MSP005_LAN
network-object object MSP006_LAN
network-object object MSP007_LAN
network-object object MSP008_LAN
network-object object MSP009_LAN
network-object object MSP010_LAN
network-object object MSP011_LAN
network-object object MSP012_LAN
Edit:
I found some debug messages after i increaed the logging level
PSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=17, saddr=10.3.x.x, sport=21912, daddr=192.168.x.x, dport=41216
IPSEC(crypto_map_check)-5: Checking crypto map s2sCryptoMap 3: skipping because 5-tuple does not match ACL |s2sAcl|a1cb2b8d-2873-11ed-b3b5-0b1a67c60fb7.
IPSEC(crypto_map_check)-5: Checking crypto map s2sCryptoMap 12: skipping because 5-tuple does not match ACL |s2sAcl|cdeb2242-2d17-11ed-a3df-5f979c793791.
IPSEC(crypto_map_check)-5: Checking crypto map s2sCryptoMap 30000: skipping dynamic_link.
IPSEC(crypto_map_check)-1: Error: No crypto map matched.
IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=17, saddr=10.3.x.x, sport=2055, daddr=192.168.x.x, dport=2055
IPSEC(crypto_map_check)-5: Checking crypto map s2sCryptoMap 3: skipping because 5-tuple does not match ACL |s2sAcl|a1cb2b8d-2873-11ed-b3b5-0b1a67c60fb7.
IPSEC(crypto_map_check)-5: Checking crypto map s2sCryptoMap 12: skipping because 5-tuple does not match ACL |s2sAcl|cdeb2242-2d17-11ed-a3df-5f979c793791.
IPSEC(crypto_map_check)-5: Checking crypto map s2sCryptoMap 30000: skipping dynamic_link.
IPSEC(crypto_map_check)-1: Error: No crypto map matched.
IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=17, saddr=10.3.x.x, sport=2055, daddr=192.168.x.x, dport=2055
IPSEC(crypto_map_check)-5: Checking crypto map s2sCryptoMap 3: skipping because 5-tuple does not match ACL |s2sAcl|a1cb2b8d-2873-11ed-b3b5-0b1a67c60fb7.
IPSEC(crypto_map_check)-5: Checking crypto map s2sCryptoMap 12: skipping because 5-tuple does not match ACL |s2sAcl|cdeb2242-2d17-11ed-a3df-5f979c793791.
IPSEC(crypto_map_check)-5: Checking crypto map s2sCryptoMap 30000: skipping dynamic_link.
IPSEC(crypto_map_check)-1: Error: No crypto map matched.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2022 02:33 AM
show vpn-sessiondb
can you share this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2022 02:42 AM
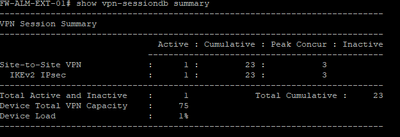
This is the output with 4 connections set to the dynamic profile
FW-ALM-EXT-01# show vpn-sessiondb
---------------------------------------------------------------------------
VPN Session Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concur : Inactive
----------------------------------------------
Site-to-Site VPN : 1 : 23 : 3
IKEv2 IPsec : 1 : 23 : 3
---------------------------------------------------------------------------
Total Active and Inactive : 1 Total Cumulative : 23
Device Total VPN Capacity : 75
Device Load : 1%
---------------------------------------------------------------------------
---------------------------------------------------------------------------
Tunnels Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concurrent
----------------------------------------------
IKEv2 : 1 : 23 : 3
IPsec : 1 : 23 : 2
---------------------------------------------------------------------------
Totals : 2 : 46
---------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2022 03:00 AM
show vpn-sessiondb summary <<- same command but add summary keyword to it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2022 03:03 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 10:50 AM - edited 11-25-2022 11:00 AM
are this issue solve ??
if not
you have multi tunnel share same match ACL ???
I think your way to config is wrong,
what you need is
crypto dynamic-map s2sDynamicCryptoMap 1 match address <Local LAN to Remote LAN Site 1 >
crypto dynamic-map s2sDynamicCryptoMap 1 set pfs
crypto dynamic-map s2sDynamicCryptoMap 1 set ikev2 ipsec-proposal VCS
crypto dynamic-map s2sDynamicCryptoMap 1 set security-association lifetime seconds 28800
crypto dynamic-map s2sDynamicCryptoMap 1 set security-association lifetime kilobytes unlimited
!
crypto dynamic-map s2sDynamicCryptoMap 2 match address <Local LAN to Remote LAN Site 2>
crypto dynamic-map s2sDynamicCryptoMap 2 set pfs
crypto dynamic-map s2sDynamicCryptoMap 2 set ikev2 ipsec-proposal VCS
crypto dynamic-map s2sDynamicCryptoMap 2 set security-association lifetime seconds 28800
crypto dynamic-map s2sDynamicCryptoMap 2 set security-association lifetime kilobytes unlimited
...etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2022 11:48 PM
i,
This is issue has not been resolved yet.
i will try your suggestion somewhere in the coming days.
Thanks for the reply!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2022 07:39 AM
Im having some trouble configuring the mentioned lines.
I cant seem to be able to enter the CLI to configure the VPN.
I can only configure them through the FTD GUI.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: