- Cisco Community
- Technology and Support
- Security
- VPN
- Re: FlexVPN name-mangler won't match on email or DN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FlexVPN name-mangler won't match on email or DN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2022 04:17 AM - edited 07-26-2022 04:42 AM
Dear community,
Have a small problem where I am trying to connect a strongswan client via x509 certificates to a Catalyst 8000v (Version 17.08.01a) in the cloud. The connection is working without problems except for when I am using the name-mangler to match on DN or email.
This is the IKEv2 profile where the client connectes:
crypto ikev2 profile FlexLink_OS
description *** VT_FlexLink FlexLink OS Certificates ***
match certificate FlexLink_OS
identity local fqdn tt-flexgw4.awsgw.xxxxx.org
authentication remote ecdsa-sig
authentication local ecdsa-sig
pki trustpoint EC-PKI_VPN
dpd 10 3 periodic
aaa authorization group cert list FlexVPN_AAA FlexLink_OS
aaa authorization user cert list FlexVPN_AAA name-mangler email-USR
virtual-template 5 mode auto
!
crypto ikev2 name-mangler email-USR
email username
* If I use the fqdn all, the client is connecting! The username looks like that: name1.name-idc-phone.xxxxx.org
With the "email" or "dn" matching, I get the error:
*Jul 26 10:57:16.357: IKEv2-ERROR:AAA user author request failed
*Jul 26 10:57:16.357: IKEv2-ERROR:Address type 0 not supported
I think that the problem can be in one of the 3 places:
1. IOS BUG (tested with 17.07.01a and 17.08.01a)
2. Certificate format. Certificates are release with Linux strongswan-pki
3. faulty configuration.
If I open the certificates on my computer, I can see the DN and email fields. They are there, but I think that the router can't read them for some reason.
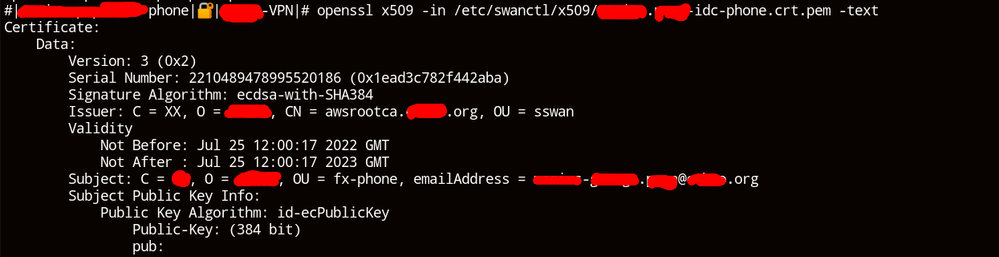
This is the cert:
Thank you for taking the time!
- Labels:
-
FlexVPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2022 04:28 AM
I will try first see the Cert. in strongswan
check the dn
and e-mail
are it appear or not ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2022 04:36 AM - edited 07-26-2022 04:43 AM
cert screenshot added in original post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2022 04:54 AM
crypto pki certificate map ......
issuer-name .......can you check if you enter certification map with issuer-name OR email
is connect success
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2022 05:34 AM
I think that the problem is with the name-mangler rather.
When I modify the name mangler and use FQDN, it work.
When I match based on DN or e-mail it doesn't.
I modified the certificate map and I can match based on issuer name.
The problem is with the user authorization:
*Jul 26 12:33:17.502: IKEv2:(SA ID = 1):[IKEv2 -> AAA] Authorisation request sent
*Jul 26 12:33:17.503: IKEv2:(SA ID = 1):[AAA -> IKEv2] Received AAA authorisation response
*Jul 26 12:33:17.503: IKEv2-ERROR:AAA user author request failed
*Jul 26 12:33:17.503: IKEv2-ERROR:Address type 0 not supported
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 04:03 PM
email username <-
here the issue
for example
name......org
the SW will take only the name not full email from the certificate and send it to AAA.
in AAA you must add User name not add User full email.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2022 12:14 AM
Will make a test now.
I have local AAA for now. Tried matching other fields and I still get the error:
Address type 0 not supported
What's the best practice of generating certificates for FlexVPN authentication?
I'm seeing examples where Windows Server CA was used.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2022 03:21 PM - edited 07-29-2022 04:59 PM
crypto ikev2 profile FlexLink_OS
description *** VT_FlexLink FlexLink OS Certificates ***
match certificate FlexLink_OS/CERT-MAP
identity local fqdn tt-flexgw4.awsgw.xxxxx.org
authentication remote ecdsa-sig
authentication local ecdsa-sig
pki trustpoint EC-PKI_VPN
dpd 10 3 periodic
aaa authorization group cert list FlexVPN_AAA/AAA-Author
aaa authorization user cert list FlexVPN_AAA/AAA-Author name-mangler email-USR
virtual-template 5 mode auto
!
crypto ikev2 name-mangler email-USR
email username
I make some change please check it,
The IKEv2 Author Policy attr. from the AAA
the Cert-MAP need to config
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide