- Cisco Community
- Technology and Support
- Security
- VPN
- FlexVPN: There was no IPSEC policy found for received TS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2022 11:47 AM - edited 01-11-2022 02:13 PM
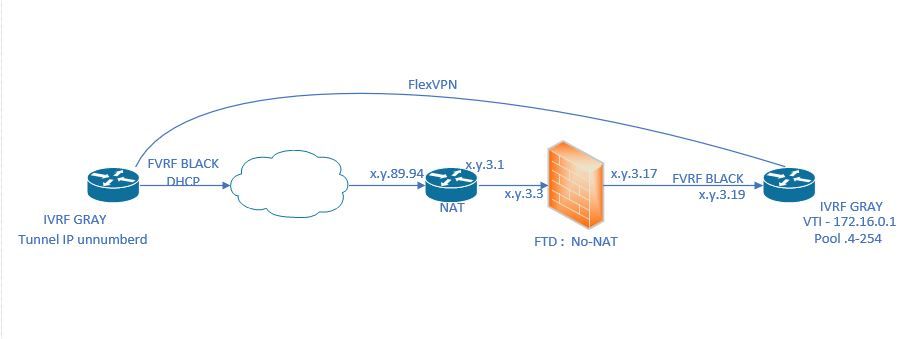
Hey folks, I am running across a problem I just cannot solve. I hope you guys can assist with this FlexVPN ERROR: "There was no IPSEC policy found for received TS"
HUB Config:
vrf definition BLACK ! address-family ipv4 exit-address-family ! vrf definition GRAY ! address-family ipv4 exit-address-family ! vrf definition mgmt description MGMT ! address-family ipv4 exit-address-family ! aaa authentication login default local aaa authorization console aaa authorization exec default local if-authenticated aaa authorization network default local ! ip domain name myDomain.com ! no crypto ikev2 authorization policy default ! crypto ikev2 authorization policy TMA00-AUTH-POLICY pool LOCAL_IP_POOL netmask 255.255.255.0 route set access-list LOCAL_SUBNETS route accept any tag 100 distance 2 ! crypto ikev2 proposal TMA00-IKEV2-PROP encryption aes-gcm-256 prf sha512 group 21 ! crypto ikev2 policy TMA00-IKEV2-POLICY match fvrf BLACK proposal TMA00-IKEV2-PROP ! crypto ikev2 keyring TMA00-IKEV2-KEYRING peer TMA00 description FLEXPVN-SPOKES address 0.0.0.0 0.0.0.0 identity fqdn domain myDomain.com pre-shared-key local <REMOVED> pre-shared-key remote <REMOVED> ! ! crypto ikev2 profile TMA00-IKEV2-PROFILE match fvrf BLACK match identity remote fqdn domain myDomain.com identity local fqdn myrtr.myDomain.com authentication remote pre-share authentication local pre-share keyring local TMA00-IKEV2-KEYRING aaa authorization group psk list default TMA00-AUTH-POLICY virtual-template 101 ! ! crypto ipsec transform-set TMA00-IPSEC-TSET esp-gcm 256 mode tunnel ! crypto ipsec profile TMA00-IPSEC-PROFILE set transform-set TMA00-IPSEC-TSET set ikev2-profile TMA00-IKEV2-PROFILE ! no crypto ipsec profile default ! interface Loopback172 description LOOPBACK FOR FLEXVPN vrf forwarding GRAY ip address 172.16.0.1 255.255.255.0 ! interface GigabitEthernet1/0.4 encapsulation dot1Q 4 vrf forwarding BLACK ip address x.y.3.19 255.255.255.248 ip virtual-reassembly in ! interface Virtual-Template101 type tunnel vrf forwarding GRAY ip unnumbered Loopback172 ip nhrp network-id 1 ip nhrp redirect tunnel vrf BLACK tunnel protection ipsec profile TMA00-IPSEC-PROFILE ! ip local pool LOCAL_IP_POOL 172.16.0.4 172.16.0.254 ! ip route vrf BLACK 0.0.0.0 0.0.0.0 x.y.3.17 ! ip access-list standard LOCAL_SUBNETS permit x.y.3.132 0.0.0.3
Remote Config:
vrf definition BLACK ! address-family ipv4 exit-address-family ! vrf definition GRAY ! address-family ipv4 exit-address-family ! vrf definition mgmt description MGMT ! address-family ipv4 exit-address-family ! aaa authentication login default local aaa authorization exec default local if-authenticated aaa authorization network default local aaa accounting update newinfo ! ip domain name myDomain.com ! no crypto ikev2 authorization policy default ! crypto ikev2 authorization policy TMA01-AUTH-POLICY netmask 255.255.255.0 route set access-list LOCAL_SUBNETS route accept any tag 102 distance 2 ! crypto ikev2 proposal TMA00-IKEV2-PROP encryption aes-gcm-256 prf sha512 group 21 ! crypto ikev2 policy TMA00-IKEV2-POLICY match fvrf BLACK proposal TMA00-IKEV2-PROP ! crypto ikev2 keyring TMA00-IKEV2-KEYRING peer TMA00 description TMA FLEXVPN HUB address 0.0.0.0 0.0.0.0 identity fqdn domain myDomain.com pre-shared-key local <REMOVED> pre-shared-key remote <REMOVED> ! ! ! crypto ikev2 profile TMA00-IKEV2-PROFILE match fvrf BLACK match identity remote fqdn domain myDomain.com identity local fqdn MyR1.myDomain.com authentication remote pre-share authentication local pre-share keyring local TMA00-IKEV2-KEYRING aaa authorization group psk list default TMA01-AUTH-POLICY virtual-template 101 ! crypto logging session ! crypto ipsec transform-set TMA00-IPSEC-TSET esp-gcm 256 mode tunnel ! crypto ipsec profile TMA00-IPSEC-PROFILE set transform-set TMA00-IPSEC-TSET set ikev2-profile TMA00-IKEV2-PROFILE ! no crypto ipsec profile default ! interface Loopback101 vrf forwarding GRAY ip address x.x.1.3 255.255.255.255 ! interface Tunnel172 vrf forwarding GRAY ip address negotiated ip nhrp network-id 1 ip nhrp shortcut virtual-template 101 tunnel source GigabitEthernet1 tunnel destination x.y.89.94 tunnel vrf BLACK tunnel protection ipsec profile TMA00-IPSEC-PROFILE ! interface GigabitEthernet1 description OUTSIDE vrf forwarding BLACK ip address x.y.89.81 255.255.255.240 negotiation auto ! interface Virtual-Template101 type tunnel description FLEXVPN-VIRTUAL-TEMPLATE-SPOKE-TUNNELS vrf forwarding GRAY no ip address ip unnumbered Loopback172 ip nhrp network-id 1 ip nhrp shortcut virtual-template 101 tunnel vrf BLACK tunnel protection ipsec profile TMA00-IPSEC-PROFILE ! ! ip route vrf BLACK 0.0.0.0 0.0.0.0 x.y.89.84 ! ip access-list standard LOCAL_SUBNETS permit x.x.1.3
Debug from HUB:
*Jan 11 18:55:38: IKEv2-PAK:Next payload: SA, version: 2.0 Exchange type: IKE_SA_INIT, flags: INITIATOR Message id: 0, length: 386
Payload contents:
SA Next payload: KE, reserved: 0x0, length: 40
last proposal: 0x0, reserved: 0x0, length: 36
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 3 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-GCM
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA512
last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_521_ECP/Group 21
KE Next payload: N, reserved: 0x0, length: 140
DH group: 21, Reserved: 0x0
N Next payload: VID, reserved: 0x0, length: 36
VID Next payload: VID, reserved: 0x0, length: 23
VID Next payload: VID, reserved: 0x0, length: 19
VID Next payload: VID, reserved: 0x0, length: 23
VID Next payload: NOTIFY, reserved: 0x0, length: 21
NOTIFY(NAT_DETECTION_SOURCE_IP) Next payload: NOTIFY, reserved: 0x0, length: 28
Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_SOURCE_IP
NOTIFY(NAT_DETECTION_DESTINATION_IP) Next payload: NONE, reserved: 0x0, length: 28
Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
*Jan 11 18:55:38: IKEv2-PAK:(SESSION ID = 304,SA ID = 1):Next payload: SA, version: 2.0 Exchange type: IKE_SA_INIT, flags: RESPONDER MSG-RESPONSE Message id: 0, length: 386
Payload contents:
SA Next payload: KE, reserved: 0x0, length: 40
last proposal: 0x0, reserved: 0x0, length: 36
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 3 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-GCM
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA512
last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_521_ECP/Group 21
KE Next payload: N, reserved: 0x0, length: 140
DH group: 21, Reserved: 0x0
N Next payload: VID, reserved: 0x0, length: 36
VID Next payload: VID, reserved: 0x0, length: 23
VID Next payload: VID, reserved: 0x0, length: 19
VID Next payload: VID, reserved: 0x0, length: 23
VID Next payload: NOTIFY, reserved: 0x0, length: 21
NOTIFY(NAT_DETECTION_SOURCE_IP) Next payload: NOTIFY, reserved: 0x0, length: 28
Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_SOURCE_IP
NOTIFY(NAT_DETECTION_DESTINATION_IP) Next payload: NONE, reserved: 0x0, length: 28
Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
*Jan 11 18:55:38: IKEv2-PAK:(SESSION ID = 304,SA ID = 1):Next payload: ENCR, version: 2.0 Exchange type: IKE_AUTH, flags: INITIATOR Message id: 1, length: 637
Payload contents:
VID Next payload: IDi, reserved: 0x0, length: 20
IDi Next payload: AUTH, reserved: 0x0, length: 43
Id type: FQDN, Reserved: 0x0 0x0
AUTH Next payload: CFG, reserved: 0x0, length: 72
Auth method PSK, reserved: 0x0, reserved 0x0
CFG Next payload: SA, reserved: 0x0, length: 325
cfg type: CFG_REQUEST, reserved: 0x0, reserved: 0x0
*Jan 11 18:55:38: attrib type: internal IP4 address, length: 0
*Jan 11 18:55:38: attrib type: internal IP4 netmask, length: 0
*Jan 11 18:55:38: attrib type: internal IP4 DNS, length: 0
*Jan 11 18:55:38: attrib type: internal IP4 DNS, length: 0
*Jan 11 18:55:38: attrib type: internal IP4 NBNS, length: 0
*Jan 11 18:55:38: attrib type: internal IP4 NBNS, length: 0
*Jan 11 18:55:38: attrib type: internal IP4 subnet, length: 0
*Jan 11 18:55:38: attrib type: internal IP6 DNS, length: 0
*Jan 11 18:55:38: attrib type: internal IP6 subnet, length: 0
*Jan 11 18:55:38: attrib type: application version, length: 257
attrib type: Unknown - 28675, length: 0
*Jan 11 18:55:38: attrib type: Unknown - 28672, length: 0
*Jan 11 18:55:38: attrib type: Unknown - 28692, length: 0
*Jan 11 18:55:38: attrib type: Unknown - 28681, length: 0
*Jan 11 18:55:38: attrib type: Unknown - 28674, length: 0
*Jan 11 18:55:38: SA Next payload: TSi, reserved: 0x0, length: 36
last proposal: 0x0, reserved: 0x0, length: 32
Proposal: 1, Protocol id: ESP, SPI size: 4, #trans: 2 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-GCM
last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
TSi Next payload: TSr, reserved: 0x0, length: 24
Num of TSs: 1, reserved 0x0, reserved 0x0
TS type: TS_IPV4_ADDR_RANGE, proto id: 47, length: 16
start port: 0, end port: 65535
start addr: x.y.89.81, end addr: x.y.89.81
TSr Next payload: NOTIFY, reserved: 0x0, length: 24
Num of TSs: 1, reserved 0x0, reserved 0x0
TS type: TS_IPV4_ADDR_RANGE, proto id: 47, length: 16
start port: 0, end port: 65535
start addr: x.y.89.94, end addr: x.y.89.94
NOTIFY(INITIAL_CONTACT) Next payload: NOTIFY, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: INITIAL_CONTACT
NOTIFY(SET_WINDOW_SIZE) Next payload: NOTIFY, reserved: 0x0, length: 12
Security protocol id: Unknown - 0, spi size: 0, type: SET_WINDOW_SIZE
NOTIFY(ESP_TFC_NO_SUPPORT) Next payload: NOTIFY, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: ESP_TFC_NO_SUPPORT
NOTIFY(NON_FIRST_FRAGS) Next payload: NONE, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: NON_FIRST_FRAGS
*Jan 11 18:55:38: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to down
*Jan 11 18:55:38: IKEv2-ERROR:(SESSION ID = 304,SA ID = 1):: There was no IPSEC policy found for received TS
Payload contents:
VID Next payload: IDr, reserved: 0x0, length: 20
IDr Next payload: AUTH, reserved: 0x0, length: 43
Id type: FQDN, Reserved: 0x0 0x0
AUTH Next payload: NOTIFY, reserved: 0x0, length: 72
Auth method PSK, reserved: 0x0, reserved 0x0
NOTIFY(TS_UNACCEPTABLE) Next payload: NONE, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: TS_UNACCEPTABLE
*Jan 11 18:55:38: IKEv2-PAK:(SESSION ID = 304,SA ID = 1):Next payload: ENCR, version: 2.0 Exchange type: IKE_AUTH, flags: RESPONDER MSG-RESPONSE Message id: 1, length: 200
Payload contents:
ENCR Next payload: VID, reserved: 0x0, length: 172
*Jan 11 18:55:38: %CRYPTO-5-IKEV2_SESSION_STATUS: Crypto tunnel v2 is UP. Peer x.y.89.81:4500 f_vrf: BLACK i_vrf: BLACK Id: MyR1.MyDomain.com
*Jan 11 18:55:38: IKEv2-PAK:(SESSION ID = 304,SA ID = 1):Next payload: ENCR, version: 2.0 Exchange type: INFORMATIONAL, flags: INITIATOR Message id: 2, length: 69
Payload contents:
DELETE Next payload: NONE, reserved: 0x0, length: 12
Security protocol id: ESP, spi size: 4, num of spi: 1
*Jan 11 18:55:38: IKEv2-PAK:(SESSION ID = 304,SA ID = 1):Next payload: ENCR, version: 2.0 Exchange type: INFORMATIONAL, flags: RESPONDER MSG-RESPONSE Message id: 2, length: 57
Payload contents:
ENCR Next payload: NONE, reserved: 0x0, length: 29
*Jan 11 18:55:38: IKEv2-PAK:(SESSION ID = 304,SA ID = 1):Next payload: ENCR, version: 2.0 Exchange type: INFORMATIONAL, flags: INITIATOR Message id: 3, length: 65
Payload contents:
DELETE Next payload: NONE, reserved: 0x0, length: 8
Security protocol id: IKE, spi size: 0, num of spi: 0
*Jan 11 18:55:38: IKEv2-PAK:(SESSION ID = 304,SA ID = 1):Next payload: ENCR, version: 2.0 Exchange type: INFORMATIONAL, flags: RESPONDER MSG-RESPONSE Message id: 3, length: 57
Payload contents:
ENCR Next payload: NONE, reserved: 0x0, length: 29
*Jan 11 18:55:38: %CRYPTO-5-IKEV2_SESSION_STATUS: Crypto tunnel v2 is DOWN. Peer x.y.89.81:4500 f_vrf: BLACK i_vrf: BLACK Id: MyR1.MyDomain.com
OUTSIDE Router NAT STATMENTS:
ip nat inside source static esp x.y.3.19 interface GigabitEthernet0/0 ip nat inside source static udp x.y.3.19 500 interface GigabitEthernet0/0 500 ip nat inside source static udp x.y.3.19 4500 interface GigabitEthernet0/0 4500
Solved! Go to Solution.
- Labels:
-
FlexVPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2023 08:56 AM
Example: Remote Config that also had a local subnet that did not transverse the VPN
aaa group server radius ISE
server name ISE1
ip radius source-interface Loopback1
deadtime 5
retransmit 3
timeout 20
!
aaa authentication login default local
aaa authorization exec default local if-authenticated
aaa authorization network default local
aaa accounting update newinfo
!
!
vrf definition BLACK
!
address-family ipv4
exit-address-family
!
vrf definition GRAY
!
address-family ipv4
exit-address-family
!
vrf definition mgmt
description MGMT
!
address-family ipv4
exit-address-family
!
no crypto ikev2 authorization policy default
!
crypto ikev2 authorization policy AUTH-POLICY
netmask 255.255.255.0
route set access-list LOCAL_SUBNETS
route accept any tag 102 distance 2
!
crypto ikev2 proposal <SITE>-IKEV2-PROP
encryption aes-gcm-256
prf sha384
group 20
!
crypto ikev2 policy <SITE>-IKEV2-POLICY
match fvrf BLACK
proposal <SITE>-IKEV2-PROP
!
crypto ikev2 keyring <SITE>-IKEV2-KEYRING
peer <SITE>
description TMA FLEXVPN HUB
address <HUB_IP>
identity address <HUB_IP>
pre-shared-key local <PRE-SHARED-KEY>
pre-shared-key remote <PRE-SHARED-KEY>
!
!
!
crypto ikev2 profile <SITE>-IKEV2-PROFILE
match fvrf BLACK
match identity remote fqdn domain <REMOTE_FQDN>
identity local fqdn <LOCAL_FQDN>
authentication remote pre-share
authentication local pre-share
keyring local <SITE>-IKEV2-KEYRING
aaa authorization group psk list default AUTH-POLICY
virtual-template 101
!
crypto ikev2 nat keepalive 900
crypto ikev2 dpd 10 2 periodic
no crypto ikev2 http-url cert
!
!
no crypto ipsec transform-set default
crypto ipsec transform-set <SITE>-IPSEC-TSET esp-gcm 256
mode tunnel
!
crypto ipsec profile <SITE>-IPSEC-PROFILE
set transform-set <SITE>-IPSEC-TSET
set pfs group20
set ikev2-profile <SITE>-IKEV2-PROFILE
!
no crypto ipsec profile default
!
interface Loopback1
no ip address
!
interface Loopback101
vrf forwarding GRAY
ip address 10.0.1.3 255.255.255.255
!
interface Loopback172
description LOOPBACK-VIRTUAL-TEMPLATE
vrf forwarding GRAY
no ip address
!
interface Tunnel172
vrf forwarding GRAY
ip address negotiated
ip nhrp network-id 1
ip nhrp shortcut virtual-template 101
tunnel source GigabitEthernet1
tunnel mode ipsec ipv4
tunnel destination <HUB_IP>
tunnel vrf BLACK
tunnel protection ipsec profile <SITE>-IPSEC-PROFILE
!
interface GigabitEthernet1
description OUTSIDE
vrf forwarding BLACK
ip address <OUTSIDE_IP> <OUTSIDE_MASK>
ip tcp adjust-mss 1360
negotiation auto
!
interface GigabitEthernet2
description INSIDE
ip address <INSIDE_IP> <INSIDE_MASK>
negotiation auto
!
interface GigabitEthernet3
description Client_Routable_1
ip address 10.64.2.1 255.255.255.128
negotiation auto
!
interface GigabitEthernet4
description Client_NonRoutable_1
ip address 172.31.64.1 255.255.255.0
negotiation auto
!
interface GigabitEthernet5
description GREEN3
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet6
description GREEN4
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet7
description GREEN5
no ip address
negotiation auto
!
interface GigabitEthernet8
description Managment Interface
vrf forwarding mgmt
ip address <MGMT_IP> <MGMT_MASK
negotiation auto
!
interface Virtual-Template101 type tunnel
description FLEXVPN-VIRTUAL-TEMPLATE-SPOKE-TUNNELS
vrf forwarding GRAY
ip unnumbered Loopback172
ip nhrp network-id 1
ip nhrp shortcut virtual-template 101
tunnel vrf BLACK
tunnel protection ipsec profile <SITE>-IPSEC-PROFILE
!
ip route 0.0.0.0 0.0.0.0 <HUB_IP>
ip route vrf BLACK 0.0.0.0 0.0.0.0 <HUB_IP>
ip route vrf mgmt 0.0.0.0 0.0.0.0 10.0.0.1
!
!
ip access-list standard LOCAL_SUBNETS
permit 10.0.1.3
!
ip access-list extended OUTSIDE_HUB_IN_v0.1
permit esp any any
permit udp any any eq isakmp
permit udp any any eq non500-isakmp
permit icmp any any echo
permit icmp any any echo-reply
permit udp any any eq bootps
permit udp any any eq bootpc
deny ip any any log
ip access-list extended VTY_LINE_v0.1
remark *****For Testing Only*******
permit tcp any any eq 22 log
deny ip any any log
remark *****For Testing Only*******
!
!
logging origin-id hostname
logging facility local2
!
!
snmp-server trap-source GigabitEthernet8
!
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 6 support-multiple
radius-server attribute 8 include-in-access-req
radius-server dead-criteria time 20 tries 2
radius-server deadtime 1
!
radius server ISE1
address ipv4 <RADIUS_SERVER_IP> auth-port 1645 acct-port 1646
key <RADIUS_KEY>
!
!
ntp logging
ntp source GigabitEthernet8
!
!
!
!
Example Hub:
vrf definition BLACK
!
address-family ipv4
exit-address-family
!
vrf definition GRAY
!
address-family ipv4
exit-address-family
!
vrf definition mgmt
description MGMT
!
address-family ipv4
exit-address-family
!
aaa new-model
!
!
aaa group server tacacs+ ise_group
server name ise
ip vrf forwarding mgmt
!
aaa authentication login default group ise_group local
aaa authentication enable default group ise_group enable
aaa authorization console
aaa authorization config-commands
aaa authorization exec default group ise_group local if-authenticated
aaa authorization commands 1 default group ise_group local if-authenticated
aaa authorization commands 15 default group ise_group local if-authenticated
aaa accounting exec default start-stop group ise_group
aaa accounting commands 1 default start-stop group ise_group
aaa accounting commands 15 default start-stop group ise_group
!
no ip domain lookup
ip domain name <DOMAIN_NAME>
!
!
multilink bundle-name authenticated
!
no crypto ikev2 authorization policy default
!
crypto ikev2 authorization policy <SITE>-AUTH-POLICY
pool LOCAL_IP_POOL
ne<SITE>sk 255.255.255.0
route set access-list LOCAL_SUBNETS
route accept any tag 100 distance 2
!
crypto ikev2 proposal <SITE>-IKEV2-PROP
encryption aes-gcm-256
prf sha384
group 20
!
crypto ikev2 policy <SITE>-IKEV2-POLICY
match fvrf BLACK
proposal <SITE>-IKEV2-PROP
!
crypto ikev2 keyring <SITE>-IKEV2-KEYRING
peer <SITE>
description FLEXPVN-SPOKES
address 0.0.0.0 0.0.0.0
identity fqdn domain <LOCAL_FQDN>
pre-shared-key local <PRESHARED_KEY>
pre-shared-key remote <PRESHARED_KEY>
!
!
!
crypto ikev2 profile <SITE>-IKEV2-PROFILE
match fvrf BLACK
match identity remote fqdn domain <REMOTE_FQDN>
identity local fqdn <LOCAL_FQDN>
authentication remote pre-share
authentication local pre-share
keyring local <SITE>-IKEV2-KEYRING
aaa authorization group psk list default <SITE>-AUTH-POLICY
virtual-template 101
!
!
!
!
crypto logging session
crypto logging ikev2
crypto isakmp aggressive-mode disable
!
!
no crypto ipsec transform-set default
crypto ipsec transform-set <SITE>-IPSEC-TSET esp-gcm 256
mode tunnel
!
crypto ipsec profile <SITE>-IPSEC-PROFILE
set transform-set <SITE>-IPSEC-TSET
set pfs group20
set ikev2-profile <SITE>-IKEV2-PROFILE
!
no crypto ipsec profile default
!
!
!
!
!
!
interface Loopback172
description LOOPBACK FOR FLEXVPN
vrf forwarding GRAY
ip address 172.16.0.1 255.255.255.0
!
interface Loopback10100
ip address 10.1.0.0 255.255.255.255
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
description FIREWALL connection
vrf forwarding GRAY
ip address <IP_TO_FW> <MASK_TO_FW>
duplex auto
speed auto
!
interface GigabitEthernet0/1
description OOBMGMT Uplink
vrf forwarding mgmt
ip address <OOB_IP> 255.255.255.224
duplex auto
speed auto
!
interface GigabitEthernet0/2
no ip address
shutdown
duplex auto
speed auto
!
interface GigabitEthernet1/0.4
encapsulation dot1Q 4
vrf forwarding BLACK
ip address <BLACK_VRF_IP> 255.255.255.248
ip virtual-reassembly in
!
interface GigabitEthernet1/0.5
description GRAY_MGMT
encapsulation dot1Q 5
vrf forwarding BLACK
ip address <GRAY_VRF_IP> 255.255.255.192
ip virtual-reassembly in
!
interface GigabitEthernet1/1
no ip address
!
interface Virtual-Template101 type tunnel
vrf forwarding GRAY
ip unnumbered Loopback172
ip nhrp network-id 1
ip nhrp redirect
tunnel mode ipsec ipv4
tunnel vrf BLACK
tunnel protection ipsec profile <SITE>-IPSEC-PROFILE
!
interface Vlan1
no ip address
!
ip local pool LOCAL_IP_POOL 172.16.0.4 172.16.0.254
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip tftp source-interface GigabitEthernet0/1
ip route <ROUTE_TO_OUTSIDE> 192.168.3.17
ip route vrf BLACK 0.0.0.0 0.0.0.0 192.168.3.17
ip route vrf mgmt 0.0.0.0 0.0.0.0 <OOB_GW>
ip ssh time-out 30
ip ssh authentication-retries 2
ip ssh version 2
ip scp server enable
!
ip access-list standard LOCAL_SUBNETS
permit 192.168.3.132 0.0.0.3
!
ip access-list extended ICMP_T3C1C13
permit icmp any any host-unreachable
permit icmp any any administratively-prohibited
ip access-list extended TEST1
permit ip any any log
permit esp any any log
!
nls resp-timeout 1
cpd cr-id 1
route-map ICMP_POLICY permit 10
match ip address ICMP_T3C1C13
set interface Null0
!
!
tacacs server ise
address ipv4 <ISE_IP>
key <ISE_KEY>
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2023 12:33 PM
Hello, have you solved the issue, it seems i have a similar one??
Have you tried out the "share" keyword at the end when attaching the ipsec profile to the virtualtemplate interface?
br, Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2023 01:50 PM - edited 10-24-2023 01:51 PM
Oh wow. It has been a while since I had this issue. But if my memory serves me right it ended up being something trivial like a command missing off the physical or tunnel interface. So double check your configuration on both ends to ensure that is properly configured. I remember that TAC was also at a loss and every indication I received did not point to the config problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2023 08:56 AM
Example: Remote Config that also had a local subnet that did not transverse the VPN
aaa group server radius ISE
server name ISE1
ip radius source-interface Loopback1
deadtime 5
retransmit 3
timeout 20
!
aaa authentication login default local
aaa authorization exec default local if-authenticated
aaa authorization network default local
aaa accounting update newinfo
!
!
vrf definition BLACK
!
address-family ipv4
exit-address-family
!
vrf definition GRAY
!
address-family ipv4
exit-address-family
!
vrf definition mgmt
description MGMT
!
address-family ipv4
exit-address-family
!
no crypto ikev2 authorization policy default
!
crypto ikev2 authorization policy AUTH-POLICY
netmask 255.255.255.0
route set access-list LOCAL_SUBNETS
route accept any tag 102 distance 2
!
crypto ikev2 proposal <SITE>-IKEV2-PROP
encryption aes-gcm-256
prf sha384
group 20
!
crypto ikev2 policy <SITE>-IKEV2-POLICY
match fvrf BLACK
proposal <SITE>-IKEV2-PROP
!
crypto ikev2 keyring <SITE>-IKEV2-KEYRING
peer <SITE>
description TMA FLEXVPN HUB
address <HUB_IP>
identity address <HUB_IP>
pre-shared-key local <PRE-SHARED-KEY>
pre-shared-key remote <PRE-SHARED-KEY>
!
!
!
crypto ikev2 profile <SITE>-IKEV2-PROFILE
match fvrf BLACK
match identity remote fqdn domain <REMOTE_FQDN>
identity local fqdn <LOCAL_FQDN>
authentication remote pre-share
authentication local pre-share
keyring local <SITE>-IKEV2-KEYRING
aaa authorization group psk list default AUTH-POLICY
virtual-template 101
!
crypto ikev2 nat keepalive 900
crypto ikev2 dpd 10 2 periodic
no crypto ikev2 http-url cert
!
!
no crypto ipsec transform-set default
crypto ipsec transform-set <SITE>-IPSEC-TSET esp-gcm 256
mode tunnel
!
crypto ipsec profile <SITE>-IPSEC-PROFILE
set transform-set <SITE>-IPSEC-TSET
set pfs group20
set ikev2-profile <SITE>-IKEV2-PROFILE
!
no crypto ipsec profile default
!
interface Loopback1
no ip address
!
interface Loopback101
vrf forwarding GRAY
ip address 10.0.1.3 255.255.255.255
!
interface Loopback172
description LOOPBACK-VIRTUAL-TEMPLATE
vrf forwarding GRAY
no ip address
!
interface Tunnel172
vrf forwarding GRAY
ip address negotiated
ip nhrp network-id 1
ip nhrp shortcut virtual-template 101
tunnel source GigabitEthernet1
tunnel mode ipsec ipv4
tunnel destination <HUB_IP>
tunnel vrf BLACK
tunnel protection ipsec profile <SITE>-IPSEC-PROFILE
!
interface GigabitEthernet1
description OUTSIDE
vrf forwarding BLACK
ip address <OUTSIDE_IP> <OUTSIDE_MASK>
ip tcp adjust-mss 1360
negotiation auto
!
interface GigabitEthernet2
description INSIDE
ip address <INSIDE_IP> <INSIDE_MASK>
negotiation auto
!
interface GigabitEthernet3
description Client_Routable_1
ip address 10.64.2.1 255.255.255.128
negotiation auto
!
interface GigabitEthernet4
description Client_NonRoutable_1
ip address 172.31.64.1 255.255.255.0
negotiation auto
!
interface GigabitEthernet5
description GREEN3
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet6
description GREEN4
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet7
description GREEN5
no ip address
negotiation auto
!
interface GigabitEthernet8
description Managment Interface
vrf forwarding mgmt
ip address <MGMT_IP> <MGMT_MASK
negotiation auto
!
interface Virtual-Template101 type tunnel
description FLEXVPN-VIRTUAL-TEMPLATE-SPOKE-TUNNELS
vrf forwarding GRAY
ip unnumbered Loopback172
ip nhrp network-id 1
ip nhrp shortcut virtual-template 101
tunnel vrf BLACK
tunnel protection ipsec profile <SITE>-IPSEC-PROFILE
!
ip route 0.0.0.0 0.0.0.0 <HUB_IP>
ip route vrf BLACK 0.0.0.0 0.0.0.0 <HUB_IP>
ip route vrf mgmt 0.0.0.0 0.0.0.0 10.0.0.1
!
!
ip access-list standard LOCAL_SUBNETS
permit 10.0.1.3
!
ip access-list extended OUTSIDE_HUB_IN_v0.1
permit esp any any
permit udp any any eq isakmp
permit udp any any eq non500-isakmp
permit icmp any any echo
permit icmp any any echo-reply
permit udp any any eq bootps
permit udp any any eq bootpc
deny ip any any log
ip access-list extended VTY_LINE_v0.1
remark *****For Testing Only*******
permit tcp any any eq 22 log
deny ip any any log
remark *****For Testing Only*******
!
!
logging origin-id hostname
logging facility local2
!
!
snmp-server trap-source GigabitEthernet8
!
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 6 support-multiple
radius-server attribute 8 include-in-access-req
radius-server dead-criteria time 20 tries 2
radius-server deadtime 1
!
radius server ISE1
address ipv4 <RADIUS_SERVER_IP> auth-port 1645 acct-port 1646
key <RADIUS_KEY>
!
!
ntp logging
ntp source GigabitEthernet8
!
!
!
!
Example Hub:
vrf definition BLACK
!
address-family ipv4
exit-address-family
!
vrf definition GRAY
!
address-family ipv4
exit-address-family
!
vrf definition mgmt
description MGMT
!
address-family ipv4
exit-address-family
!
aaa new-model
!
!
aaa group server tacacs+ ise_group
server name ise
ip vrf forwarding mgmt
!
aaa authentication login default group ise_group local
aaa authentication enable default group ise_group enable
aaa authorization console
aaa authorization config-commands
aaa authorization exec default group ise_group local if-authenticated
aaa authorization commands 1 default group ise_group local if-authenticated
aaa authorization commands 15 default group ise_group local if-authenticated
aaa accounting exec default start-stop group ise_group
aaa accounting commands 1 default start-stop group ise_group
aaa accounting commands 15 default start-stop group ise_group
!
no ip domain lookup
ip domain name <DOMAIN_NAME>
!
!
multilink bundle-name authenticated
!
no crypto ikev2 authorization policy default
!
crypto ikev2 authorization policy <SITE>-AUTH-POLICY
pool LOCAL_IP_POOL
ne<SITE>sk 255.255.255.0
route set access-list LOCAL_SUBNETS
route accept any tag 100 distance 2
!
crypto ikev2 proposal <SITE>-IKEV2-PROP
encryption aes-gcm-256
prf sha384
group 20
!
crypto ikev2 policy <SITE>-IKEV2-POLICY
match fvrf BLACK
proposal <SITE>-IKEV2-PROP
!
crypto ikev2 keyring <SITE>-IKEV2-KEYRING
peer <SITE>
description FLEXPVN-SPOKES
address 0.0.0.0 0.0.0.0
identity fqdn domain <LOCAL_FQDN>
pre-shared-key local <PRESHARED_KEY>
pre-shared-key remote <PRESHARED_KEY>
!
!
!
crypto ikev2 profile <SITE>-IKEV2-PROFILE
match fvrf BLACK
match identity remote fqdn domain <REMOTE_FQDN>
identity local fqdn <LOCAL_FQDN>
authentication remote pre-share
authentication local pre-share
keyring local <SITE>-IKEV2-KEYRING
aaa authorization group psk list default <SITE>-AUTH-POLICY
virtual-template 101
!
!
!
!
crypto logging session
crypto logging ikev2
crypto isakmp aggressive-mode disable
!
!
no crypto ipsec transform-set default
crypto ipsec transform-set <SITE>-IPSEC-TSET esp-gcm 256
mode tunnel
!
crypto ipsec profile <SITE>-IPSEC-PROFILE
set transform-set <SITE>-IPSEC-TSET
set pfs group20
set ikev2-profile <SITE>-IKEV2-PROFILE
!
no crypto ipsec profile default
!
!
!
!
!
!
interface Loopback172
description LOOPBACK FOR FLEXVPN
vrf forwarding GRAY
ip address 172.16.0.1 255.255.255.0
!
interface Loopback10100
ip address 10.1.0.0 255.255.255.255
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
description FIREWALL connection
vrf forwarding GRAY
ip address <IP_TO_FW> <MASK_TO_FW>
duplex auto
speed auto
!
interface GigabitEthernet0/1
description OOBMGMT Uplink
vrf forwarding mgmt
ip address <OOB_IP> 255.255.255.224
duplex auto
speed auto
!
interface GigabitEthernet0/2
no ip address
shutdown
duplex auto
speed auto
!
interface GigabitEthernet1/0.4
encapsulation dot1Q 4
vrf forwarding BLACK
ip address <BLACK_VRF_IP> 255.255.255.248
ip virtual-reassembly in
!
interface GigabitEthernet1/0.5
description GRAY_MGMT
encapsulation dot1Q 5
vrf forwarding BLACK
ip address <GRAY_VRF_IP> 255.255.255.192
ip virtual-reassembly in
!
interface GigabitEthernet1/1
no ip address
!
interface Virtual-Template101 type tunnel
vrf forwarding GRAY
ip unnumbered Loopback172
ip nhrp network-id 1
ip nhrp redirect
tunnel mode ipsec ipv4
tunnel vrf BLACK
tunnel protection ipsec profile <SITE>-IPSEC-PROFILE
!
interface Vlan1
no ip address
!
ip local pool LOCAL_IP_POOL 172.16.0.4 172.16.0.254
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip tftp source-interface GigabitEthernet0/1
ip route <ROUTE_TO_OUTSIDE> 192.168.3.17
ip route vrf BLACK 0.0.0.0 0.0.0.0 192.168.3.17
ip route vrf mgmt 0.0.0.0 0.0.0.0 <OOB_GW>
ip ssh time-out 30
ip ssh authentication-retries 2
ip ssh version 2
ip scp server enable
!
ip access-list standard LOCAL_SUBNETS
permit 192.168.3.132 0.0.0.3
!
ip access-list extended ICMP_T3C1C13
permit icmp any any host-unreachable
permit icmp any any administratively-prohibited
ip access-list extended TEST1
permit ip any any log
permit esp any any log
!
nls resp-timeout 1
cpd cr-id 1
route-map ICMP_POLICY permit 10
match ip address ICMP_T3C1C13
set interface Null0
!
!
tacacs server ise
address ipv4 <ISE_IP>
key <ISE_KEY>
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2023 01:15 AM
Hello Keibler, thx for your reply.
So, the last config example is still the one which was faulty?
br, Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2023 04:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2023 11:19 PM
Hello Keibler, i solved my problem in the meantime, it was a typo in the tunnel config. but i am interested about the flex vpn config with NAT. Thx so far. kind regards, Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2023 06:45 AM
So if you need additional assistance please let me know. It may also be better to open another thread.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide