- Cisco Community
- Technology and Support
- Security
- VPN
- FTD 6.2.2 Remote Access VPN certificate issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2018 11:57 PM - edited 03-12-2019 05:26 AM
Hi.
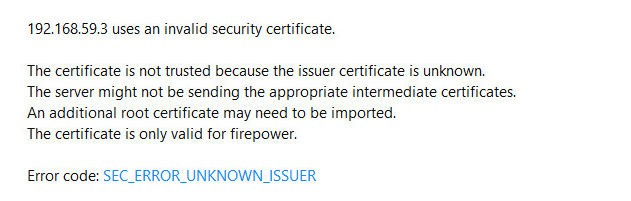
I'm working on Cisco ASA FTD 6.2.2 Remote Access VPN. I have an internal test domain (xinmix.local) and a test MS Certificate Authority server. Based on the docs on Internet I've created specific certificate template on CA server to use it with SCEP cert enrollment. I finished cert enrollment process with SCEP and it is displayed as Available. But the problem is when I want to use HTTPS on the external client toward the FTD external-facing interface, browsers don't let me to open the page saying the certificate is invalid and issued to the "Firepower" (which is hostname of my ASA FTD device). Please notice that it's not the same error normally we see while using non-public certificates (like custom and self-generated certificates), which we can proceed to the page despite the certificate. Instead they say an intermediate root CA is missing and then prevents me to proceed to the web page. I tested it with 4 different browsers and none of them allowed me in.
This is what I got on the browser. Any idea?
I'm looking for a good document about managing the certificates on FTD, cause the Cisco documents don't have details and explanation of what they intended to do and are just like "click on this, paste your cert, finish the process,..." which is not good and enough for learners.
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2018 02:19 AM - edited 07-10-2018 07:55 PM
You need to follow the remote access SSL VPN wizard in FMC to initially assign the available certificate to your outside interface.
If you already have it created and want to change the certificate, edit the VPN (Devices > VPN > Remote Access and click the pencil icon to the right of the relevant VPN listing) and go under the Access Interfaces tab. Edit the interface(s) and select the new Trustpoint (e.g. certificate). Save and deploy and you should see the proper certificate now presented to your clients.
If no interface identity certificate is configured then the "SSL Global Identity Certificate" will be used. that's most likely what you have in place currently.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2018 02:19 AM - edited 07-10-2018 07:55 PM
You need to follow the remote access SSL VPN wizard in FMC to initially assign the available certificate to your outside interface.
If you already have it created and want to change the certificate, edit the VPN (Devices > VPN > Remote Access and click the pencil icon to the right of the relevant VPN listing) and go under the Access Interfaces tab. Edit the interface(s) and select the new Trustpoint (e.g. certificate). Save and deploy and you should see the proper certificate now presented to your clients.
If no interface identity certificate is configured then the "SSL Global Identity Certificate" will be used. that's most likely what you have in place currently.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2018 08:30 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide