- Cisco Community
- Technology and Support
- Security
- VPN
- Heed help. FMC/FTD RA-VPN certificate only
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 11:20 AM
Hello team. i want to configure certificate only ra-vpn based on FMC+FTDv+MS AD+MS CA. It is important that client certificates can be revoked. Can you share the best practices.
I set up a test lab and I'm having a problem. anyconnect client could connect with a revoked certificate. I did something wrong.
help please.
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Remote Access
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 11:24 AM - edited 12-09-2022 11:31 AM
@Dmitry O did you setup CRL or OCSP to check for certificate revocation?
Certificate Enrollment Object Revocation Options
Specify whether to check the revocation status of a certificate by choosing and configuring the method. Revocation checking is off by default, neither method (CRL or OCSP) is checked.
Secure Firewall Management Center Navigation Path
Objects > Object Management, then from the navigation pane choose PKI > PKI Enrollment. Press (+) Add PKI Enrollment to open the Add PKI Enrollment dialog, and select the Revocation tab.
Fields
-
Enable Certificate Revocation Lists—Check to enable CRL checking.
-
Use CRL distribution point from the certificate—Check to obtain the revocation lists ditribution URL from the certificate.
-
Use static URL configured—Check this to add a static, pre-defined distribution URL for revocation lists. Then add the URLs.
CRL Server URLs—The URL of the LDAP server from which the CRL can be downloaded. This URL must start with ldap://, and include a port number in the URL.
-
-
Enable Online Certificate Status Protocol (OCSP)—Check to enable OCSP checking.
OCSP Server URL—The URL of the OCSP server checking for revocation if you require OCSP checks. This URL must start with http://.
-
Consider the certificate valid if revocation information can not be reached—Checked by default. Uncheck if you do not want to allow this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2022 12:55 AM
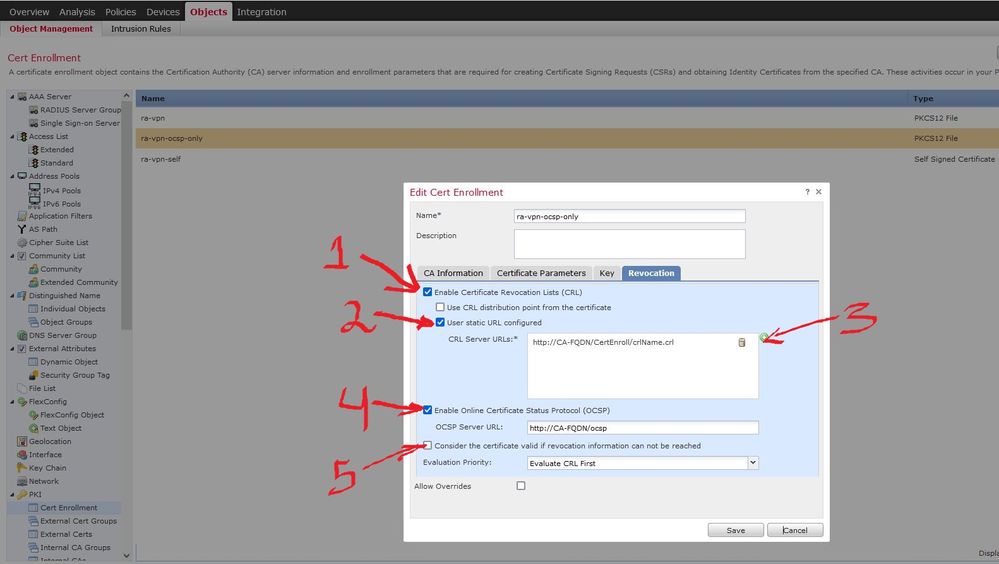
Rob, you were right. I checked Objects > Object Management > PKI > Certificate Enrollment. And there were default settings. I did everything as in the screenshot and it worked.
I am using *.PKCS12(pfx).
1. check "Enable Certificate Revocation Lists (CRL)"
2. check the box "User static URL configured"
3. Add the URL to the CRL
4. check "Enable Online Certificate Status Protocol (OCSP)" and add if configured OCSP URL to "OCSP Server URL"
5. uncheck "Consider the certificate valid if revocation information can not be reached"
For troubleshoot use Devices>VPN>Troubleshooting
in FTDv use cli command show crypto ca crls for show crl info, clear crypto ca crls for clear crl cache, and curl for check avalability *.crl file
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2022 12:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 11:24 AM - edited 12-09-2022 11:31 AM
@Dmitry O did you setup CRL or OCSP to check for certificate revocation?
Certificate Enrollment Object Revocation Options
Specify whether to check the revocation status of a certificate by choosing and configuring the method. Revocation checking is off by default, neither method (CRL or OCSP) is checked.
Secure Firewall Management Center Navigation Path
Objects > Object Management, then from the navigation pane choose PKI > PKI Enrollment. Press (+) Add PKI Enrollment to open the Add PKI Enrollment dialog, and select the Revocation tab.
Fields
-
Enable Certificate Revocation Lists—Check to enable CRL checking.
-
Use CRL distribution point from the certificate—Check to obtain the revocation lists ditribution URL from the certificate.
-
Use static URL configured—Check this to add a static, pre-defined distribution URL for revocation lists. Then add the URLs.
CRL Server URLs—The URL of the LDAP server from which the CRL can be downloaded. This URL must start with ldap://, and include a port number in the URL.
-
-
Enable Online Certificate Status Protocol (OCSP)—Check to enable OCSP checking.
OCSP Server URL—The URL of the OCSP server checking for revocation if you require OCSP checks. This URL must start with http://.
-
Consider the certificate valid if revocation information can not be reached—Checked by default. Uncheck if you do not want to allow this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2022 07:28 AM
Thanks for your reply. But I can't find Objects > Object Management, then from the navigation pane choose PKI > PKI Enrollment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2022 07:44 AM - edited 12-10-2022 12:13 PM
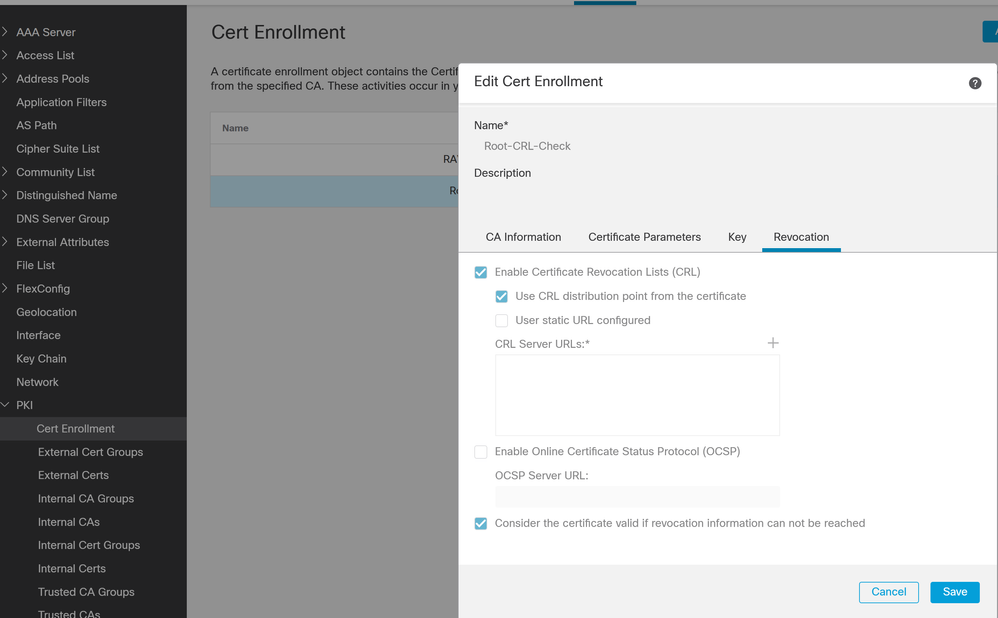
@Dmitry O you are in the correct location:-
Tick the box to enable revocation, either use the CRL distribution point from the certificate or manually configure the CRL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2022 08:16 AM
OK. What certificate should I add? VPN user? Or should it be the root certificate of the CA and his CRL in my AD domain ? I do not fully understand the mechanism of RA-VPN with Certificate only.
Could you share some manuals for configuring RA-VPN wiht certificate-only auth. Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2022 12:20 PM
@Dmitry O the screenshot provided about is where you need to configure CRL check. CRL needs to be enabled on the CA server for your internal CA. The "Enable Certificate Revocation List (CRL)" option is disable as default, so needs to be explictly enabled.
The actual user/machine certificates should be published with the CRL location, this is usually using a DNS name. So you would need to configure DNS servers in the Platform Settings policy (unless you already have done so) - this will allow the FTD to resolve the name of the CRL server.
If the certificates don't reference the CRL location, the certificate template (on the MS CA server) either needs modifying or your can explictly define the location of the CRL server by selecting "Use static URL configured" and manually define the URL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2022 12:55 AM
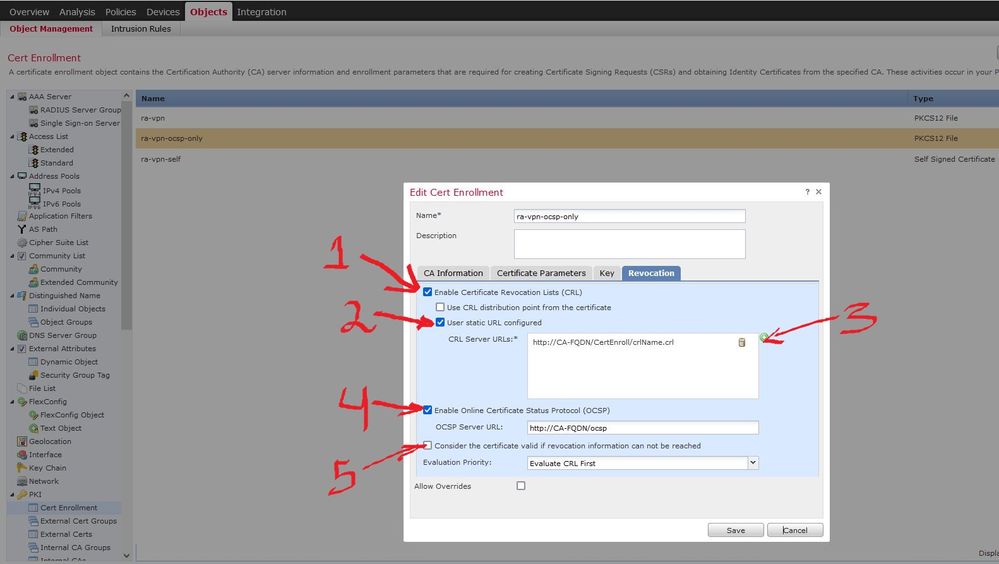
Rob, you were right. I checked Objects > Object Management > PKI > Certificate Enrollment. And there were default settings. I did everything as in the screenshot and it worked.
I am using *.PKCS12(pfx).
1. check "Enable Certificate Revocation Lists (CRL)"
2. check the box "User static URL configured"
3. Add the URL to the CRL
4. check "Enable Online Certificate Status Protocol (OCSP)" and add if configured OCSP URL to "OCSP Server URL"
5. uncheck "Consider the certificate valid if revocation information can not be reached"
For troubleshoot use Devices>VPN>Troubleshooting
in FTDv use cli command show crypto ca crls for show crl info, clear crypto ca crls for clear crl cache, and curl for check avalability *.crl file
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2022 12:55 AM
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: