- Cisco Community
- Technology and Support
- Security
- VPN
- Help on establishing Ipsec tunnel btw 1941 and ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Help on establishing Ipsec tunnel btw 1941 and ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2012 12:34 PM - edited 02-21-2020 06:33 PM
We are creating an Ipsec tunnel over the internet to another site but is not working, could someone help me on what could be happening?
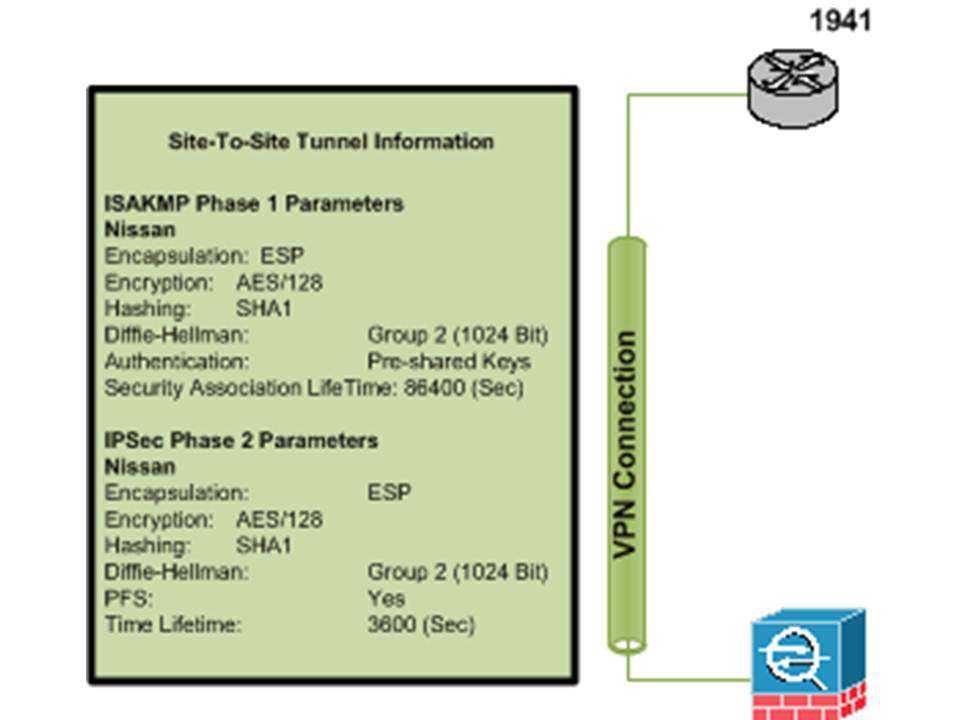
My config:
version 15.1
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname XXXX
!
boot-start-marker
boot-end-marker
!
!
logging buffered 51200 warnings
enable XXXXX
enable password XXXXXX
!
no aaa new-model
!
!
no ipv6 cef
ip source-route
ip cef
!
!
!
!
!
ip domain name yourdomain.com
ip name-server XXX.XXX.XXX.XXX
ip name-server XXX.XXX.XXX.XXX
!
multilink bundle-name authenticated
!
password encryption aes
crypto pki token default removal timeout 0
!
crypto pki trustpoint TP-self-signed-4075439344
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-4075439344
revocation-check none
rsakeypair TP-self-signed-4075439344
!
!
crypto pki certificate chain TP-self-signed-4075439344
certificate self-signed 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 34303735 34333933 3434301E 170D3131 30393139 30323236
34365A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D34 30373534
33393334 3430819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100A35E B6AC0BE0 57A53B45 8CF23671 F91A18AC 09F29E6D AEC70F4D EF3BDCD6
269BFDED 44E26A98 7A1ABCAA DB756AFC 719C3D84 8B605C2A 7E99AF79 B72A84BC
89046B2D 967BB775 978EF14D A0BD8036 523B2AE1 1890EB38 BCA3333B 463D1267
22050A4F EAF4985A 7068024A A0425CE7 D3ADF5F5 C02B2941 67C9B654 6A7EF689
049B0203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 1408B59A 57733D6E 157876B3 72A91F28 F8D95BAB D2301D06
03551D0E 04160414 08B59A57 733D6E15 7876B372 A91F28F8 D95BABD2 300D0609
2A864886 F70D0101 05050003 81810094 ED574BFE 95868A5D B539A70F 228CC08C
E26591C2 16DF19AB 7A177688 D7BB1CCB 5CFE4CB6 25F0DDEB 640E6EFA 58636DC0
238750DD 1ACF8902 96BB39B5 5B2F6DEC CB97CF78 23510943 E09801AF 8EB54020
DF496E25 B787126F D1347022 58900537 844EF865 36CB8DBD 79918E4B 76D00196
DD9950CB A40FC91B 4BCDE0DC 1B217A
quit
license udi pid CISCO1941/K9 sn FTX1539816K
license boot module c1900 technology-package securityk9
!
!
username XXXXXXXXXXXXXX
!
redundancy
!
!
!
!
!
!
crypto isakmp policy 60
encr aes
authentication pre-share
group 2
crypto isakmp key XXXXXXX address XXX.XXX.XXX.XXX
crypto isakmp profile mode
keyring default
self-identity address
match identity host XXX.XXX.XXX.XXX
initiate mode aggressive
!
!
crypto ipsec transform-set VPNbrasil esp-aes esp-sha-hmac
!
crypto map outside 60 ipsec-isakmp
set peer XXX.XXX.XXX.XXX
set transform-set VPNbrasil
set pfs group2
match address vpnbrazil
!
!
!
!
!
interface Tunnel0
ip unnumbered GigabitEthernet0/1
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
description WAN
ip address XXX.XXX.XXX.XXX 255.255.255.248
ip nat outside
no ip virtual-reassembly in
duplex full
speed 100
crypto map outside
!
interface GigabitEthernet0/1
description Intercon_LAN
ip address XXX.XXX.XXX.XXX 255.255.255.252
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
crypto map outside
!
ip forward-protocol nd
!
ip http server
ip http access-class 23
ip http authentication local
ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
!
ip nat inside source list 2 interface GigabitEthernet0/1 overload
ip route 0.0.0.0 0.0.0.0 XXX.XXX.XXX.XXX name Internet
!
ip access-list extended natvpnout
permit ip host XXX.XXX.XXX.XXX any
permit ip any any
ip access-list extended vpnbrazil
permit icmp XXX.XXX.XXX.XXX 0.0.0.255 any
permit icmp any XXX.XXX.XXX.XXX 0.0.0.255
permit ip any any
!
access-list 1 permit any
access-list 2 permit XXX.XXX.XXX.XXX 0.0.0.1 log
access-list 2 permit XXX.XXX.XXX.XXX 0.0.0.7
access-list 3 permit XXX.XXX.XXX.XXX
access-list 23 permit XXX.XXX.XXX.XXX 0.0.0.7
access-list 23 permit any log
!
!
!
!
!
!
control-plane
!
!
b!
line con 0
login local
line aux 0
line 2
no activation-character
no exec
transport preferred none
transport input all
transport output pad telnet rlogin lapb-ta mop udptn v120 ssh
stopbits 1
line vty 0 4
access-class 23 in
privilege level 15
login local
transport input all
telnet transparent
line vty 5
access-class 23 in
privilege level 15
login
transport input all
telnet transparent
line vty 6 15
access-class 23 in
access-class 23 out
privilege level 15
login local
transport input telnet ssh
transport output all
!
Could someone please help me on what could be wrong? and What tests should I do?
Rds,
Luiz
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2012 07:30 AM
try a simple configuration w/o isakmp proflies
have a look at this link:
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00805e8c80.shtml
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: