- Cisco Community
- Technology and Support
- Security
- VPN
- Re: how to use the ASA interface to be included into S2S VPN ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2021 11:18 AM
Hi,
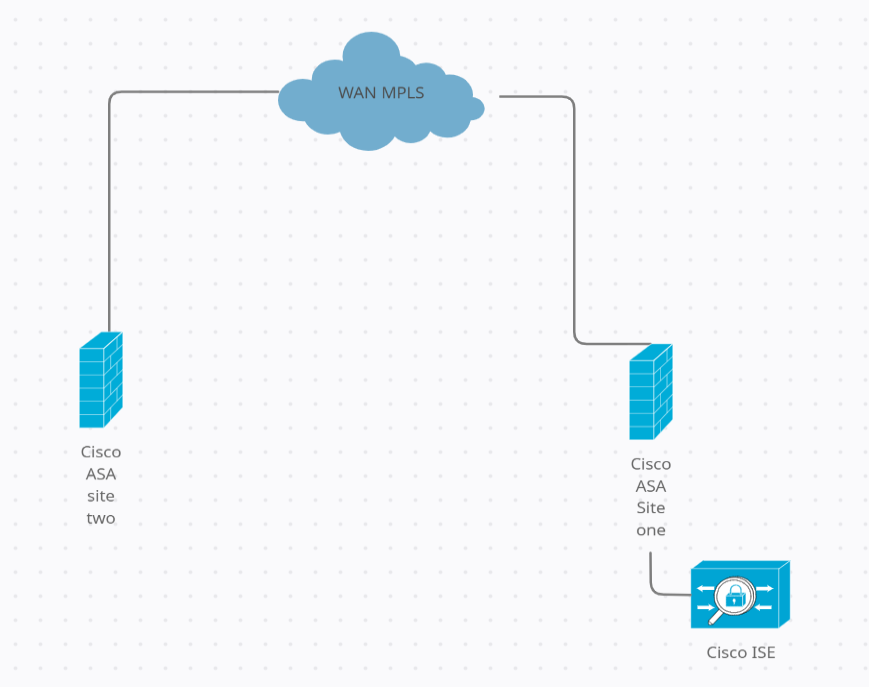
I have two sites that connected using the site to site VPN, in site number one I have ISE
I need the ASA in site number two to connect with ISE in site number one
is there any way to make the ASA WAN interface to be included in the tunnel to connect to the ISE?
Solved! Go to Solution.
- Labels:
-
IPSEC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2021 11:38 AM - edited 06-02-2021 11:43 AM
You need to include the WAN IP address of Site2 in the crypto ACL on both ends. Try this example configuration below, where WAN IP address = 1.1.1.1 and 192.168.10.10 is ISE IP address:
SITE2
access-list VPN_TO_SITE1 permit ip host 1.1.1.1 host 192.168.10.10
SITE1
access-list VPN_TO_SITE2 permit ip host 192.168.10.10 host 1.1.1.1
This will establish a tunnel between those host IP addresses only, if you want the Site 2 ASA to access the rest of the network replace host with a subnet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2021 11:38 AM - edited 06-02-2021 11:43 AM
You need to include the WAN IP address of Site2 in the crypto ACL on both ends. Try this example configuration below, where WAN IP address = 1.1.1.1 and 192.168.10.10 is ISE IP address:
SITE2
access-list VPN_TO_SITE1 permit ip host 1.1.1.1 host 192.168.10.10
SITE1
access-list VPN_TO_SITE2 permit ip host 192.168.10.10 host 1.1.1.1
This will establish a tunnel between those host IP addresses only, if you want the Site 2 ASA to access the rest of the network replace host with a subnet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2021 03:20 PM
Hi
I tried it, it didn't work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2021 01:20 PM - edited 06-03-2021 03:52 PM
The IP address use as NAS in ISE must be allow by ACL of S2S, so what is the IP address you enter in ISE for Other ASA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2021 04:08 PM
I used the other ASA WAN interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2021 04:40 PM
so As understand you use one ISP interface for RA VPN and other ISP interface for S2S to go to ISE?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2021 01:52 AM
Yes as you said the ASA has outside interface connected to the Internet for RA VPN and WAN interface connected to MPLS for S2S VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2021 03:11 PM
Friend I think you need VTI instead of IPSec S2S,
where IPSec S2S is not useful here since the Packet Source is same IPSec IP address and hence the Policy VPN can not use.
Where we can use VTI and change from Policy VPN to Route VPN and all traffic in Route VPN is encrypt by IPSec and protect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2021 12:58 AM
first, thank you for your support.
it does not work for me because I used the wrong interface for no NAT configuration, but it worked for me when I used the correct one.
by inattention, I was using the management interface for NAT and I thought I use the WAN interface
the correct command
nat (WAN, WAN) source static ISE ISE destination static ASA ASA
what I used
nat (MNG, WAN) source static ISE ISE destination static ASA ASA
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2021 07:54 AM
You are so so welcome,
so by change the IP source toward ISE from ISP to Management interface and allow management IP address in S2S ACL then everything is OK.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2021 10:29 AM
In the first I used the management interface it does not work for me
But when I used the WAN interface (lSP) it worked
Thanks
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: