- Cisco Community
- Technology and Support
- Security
- VPN
- Re: IKEv1 CVE-2002-1623 with Site-to-Site VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IKEv1 CVE-2002-1623 with Site-to-Site VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 10:35 PM
Hi there,
After we upgraded our clients ASAs (5525) to the latest recommended release by Cisco 9.12(2), the client has conducted a security scan check from a third party vendor. Two of the vulnerabilities mentioned in the report are as follows:
| Port | Plugin Name | CVE Information |
| 500 | Internet Key Exchange (IKE) Aggressive Mode with Pre-Shared Key | CVE-2002-1623 |
| 443 | SSL/TLS Diffie-Hellman Modulus <= 1024 Bits (Logjam) | CVE-2015-4000 |
I couldn't find any patches or fixes for those vulnerabilities in Cisco website nor any other security forums or even workaround for them.
CVE-2002-1623 states that "Internet Key Exchange (IKE) Aggressive Mode with Pre-Shared Key", however, when I checked show crypto ikev1 sa, it shows Main Mode is used.
There's Site-to-Site VPN between two ASAs and both IKEv1 & IKEv2 are used with PSK, so is it safe to remove IKEv1 from the connection profile (via ASDM)? Will it affect the VPN connection? and eventually fix CVE-2002-1623?
Any suggestions for remedial work will be highly appreciated .
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2020 01:14 AM
If both IKEv1 and IKEv2 are specified, then it would attempt to use IKEv2 first, by the sounds of it you are using IKEv1. So removing IKEv1 now would cause issues. Confirm the peer device has the correct IKEv2 configuration, then re-attempt to establish the tunnel - if/when the VPN tunnel establishes an IKEv2 SA then you can remove IKEv1.
Run "show ssl" to determine your current DH group, and "ssl dh-group ..." to specify a new DH group.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2020 03:21 AM - edited 03-03-2020 03:58 AM
Thanks so much for reply!
I run both commands (show crypto ikev1 sa & show crypto ikev2 sa) on both ASA:
SiteA# show crypto ikev1 sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: b.b.b.b
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
SiteA# show crypto ikev2 sa
IKEv2 SAs:
Session-id:990, Status:UP-ACTIVE, IKE count:1, CHILD count:2
Tunnel-id Local Remote Status Role
134976655 a.a.a./500 b.b.b.b/500 READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA96, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/39371 sec
Child sa: local selector 172.30.x.0/0 - 172.30.x.255/65535
remote selector 172.20.x.0/0 - 172.20.x.255/65535
ESP spi in/out: 0x9a3a93eb/0xd6b8c47e
Child sa: local selector 172.30.x.0/0 - 172.30.x.255/65535
remote selector 172.21.x.0/0 - 172.21.x.255/65535
ESP spi in/out: 0x5ef04788/0x34e26a5e
SiteA# show ssl
Accept connections using SSLv3 or greater and negotiate to TLSv1 or greater
Start connections using TLSv1 and negotiate to TLSv1 or greater
SSL DH Group: group2 (1024-bit modulus)
SSL ECDH Group: group19 (256-bit EC)
SSL trust-points:
Self-signed (RSA 2048 bits RSA-SHA256) certificate available
Self-signed (EC 256 bits ecdsa-with-SHA256) certificate available
Interface Internet: ASDM_TrustPoint0 (RSA 2048 bits RSA-SHA256)
Interface Internal: ASDM_TrustPoint0 (RSA 2048 bits RSA-SHA256)
Interface BackupInternet: ASDM_TrustPoint0 (RSA 2048 bits RSA-SHA256)
Certificate authentication is not enabled
SiteA# show vpn-sessiondb detail
---------------------------------------------------------------------------
VPN Session Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concur : Inactive
----------------------------------------------
Site-to-Site VPN : 2 : 27 : 3
IKEv2 IPsec : 1 : 6 : 2
IKEv1 IPsec : 1 : 21 : 1
---------------------------------------------------------------------------
Total Active and Inactive : 2 Total Cumulative : 27
Device Total VPN Capacity : 250
Device Load : 1%
---------------------------------------------------------------------------
---------------------------------------------------------------------------
Tunnels Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concurrent
----------------------------------------------
IKEv1 : 1 : 21 : 1
IKEv2 : 1 : 6 : 2
IPsec : 6 : 77 : 7
---------------------------------------------------------------------------
Totals : 8 : 104
---------------------------------------------------------------------------
##############################################################
SiteB# show crypto ikev1 sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: a.a.a.a
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
SiteB# show crypto ikev2 sa
IKEv2 SAs:
Session-id:4, Status:UP-ACTIVE, IKE count:1, CHILD count:2
Tunnel-id Local Remote Status Role
15312525 b.b.b.b/500 a.a.a.a/500 READY RESPONDER
Encr: AES-CBC, keysize: 256, Hash: SHA96, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/39670 sec
Child sa: local selector 172.20.x.0/0 - 172.20.x.255/65535
remote selector 172.30.x.0/0 - 172.30.x.255/65535
ESP spi in/out: 0xd6b8c47e/0x9a3a93eb
Child sa: local selector 172.21.x.0/0 - 172.21.x.255/65535
remote selector 172.30.x.0/0 - 172.30.x.255/65535
ESP spi in/out: 0x34e26a5e/0x5ef04788
SiteB# show ssl
Accept connections using SSLv3 or greater and negotiate to TLSv1 or greater
Start connections using TLSv1 and negotiate to TLSv1 or greater
SSL DH Group: group2 (1024-bit modulus)
SSL ECDH Group: group19 (256-bit EC)
SSL trust-points:
Self-signed (RSA 1024 bits RSA-SHA1) certificate available
Self-signed (EC 256 bits ecdsa-with-SHA256) certificate available
Interface OUTSIDE: ASDM_TrustPoint3 (RSA 2048 bits RSA-SHA256)
VPNLB interface OUTSIDE: ASDM_TrustPoint3 (RSA 2048 bits RSA-SHA256)
Certificate authentication is not enabled
So, my question is if I remove ikev1, will it mitigate CVE-2002-1623 venerability?
Can I remove ikev1 via ASDM? (What's the best/safest way)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2020 04:11 AM - edited 03-03-2020 04:38 AM
You've got IKEv1 and an IKEv2 SA....are these tunnels between SiteA and SiteB? Or are they to other peer devices? You need to make sure they are both IKEv2.
...but to disable IKEv1.
Firstly backup your configuration before you make any changes.
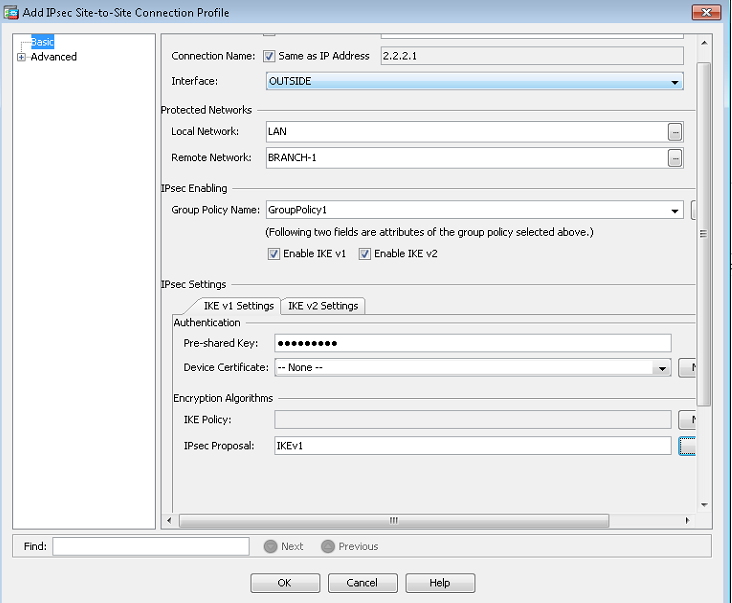
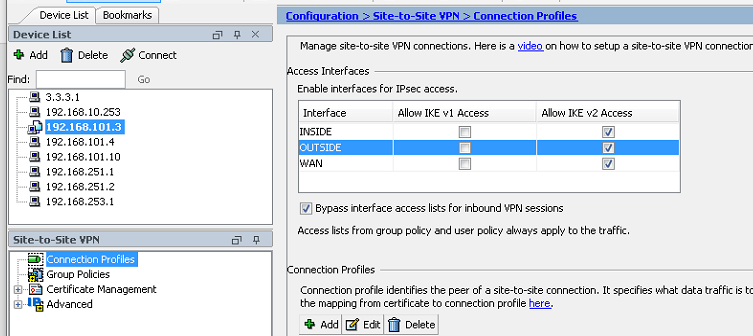
Then in ASDM untick "enable IKE v1"
You can also untick IKEv1 on the OUTSIDE interface, e.g:-
Test and only once you establish all tunnels using IKEV2, then you can also remove the IPSec IKEv1 Proposal and IKEv1 Policies.
Modify DH group using the command ssl dh-group <group>
ASA-DC-1/pri/act(config)# ssl dh-group ?
configure mode commands/options:
group2 Configure DH group 2 - 1024-bit modulus
group5 Configure DH group 5 - 1536-bit modulus
group14 Configure DH group 14 - 2048-bit modulus, 224-bit prime order
subgroup (FIPS)
group24 Configure DH group 24 - 2048-bit modulus, 256-bit prime order
subgroup (FIPS)
I'd probably use group14 as a minimum.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2020 04:59 AM
Yes, that's right! these tunnels are between SiteA and SiteB only
So, after disabling IKEv1 , I should clear the crypto, right? and how do I make sure that only IKEv2 is used?
Will disabling IKEv1 mitigate CVE-2002-1623 vulnerability?
Finally, will modify DH group (on both ASA) has an impact on the VPN connection (will the connection be lost)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2020 05:14 AM
Changing the DH group applies to SSL not IPSec, so the IPSec VPNs would not be impacted, but potentially if you are using Remote Access SSL-VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2020 05:37 AM
Thanks so much!
I will try to disable IKEv1, then let you know the result.
Sorry, you're right we using SSL VPN for remote Access VPN., so after changing DH group, the VPN user needs to reconnect (is there any further setting from his side, e.g Anyconnect)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2020 04:54 AM
Hi,
For the first vulnerability, as ling as you don't use IKEv1 remote-access VPN with pre-shared-key (via the old VPN Client client or EzVPN hardware clients), you don't care. As it seems, you run S2S IKEv1 IPsec VPN, so it does not apply.
For the second vulnerability, just use a more secure DH group, though the ASA has not been affected by this vulnerability
Regards,
Cristian Matei
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2020 05:44 AM - edited 03-03-2020 12:45 PM
Thanks for your reply, but for remote access VPN, SSL VPN is used NOT IPsec.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide