- Cisco Community
- Technology and Support
- Security
- VPN
- Re: IKEv2 AAA user authorization failed with AnyConnect and Freeradius
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2018 08:16 AM - edited 03-12-2019 05:18 AM
Hello,
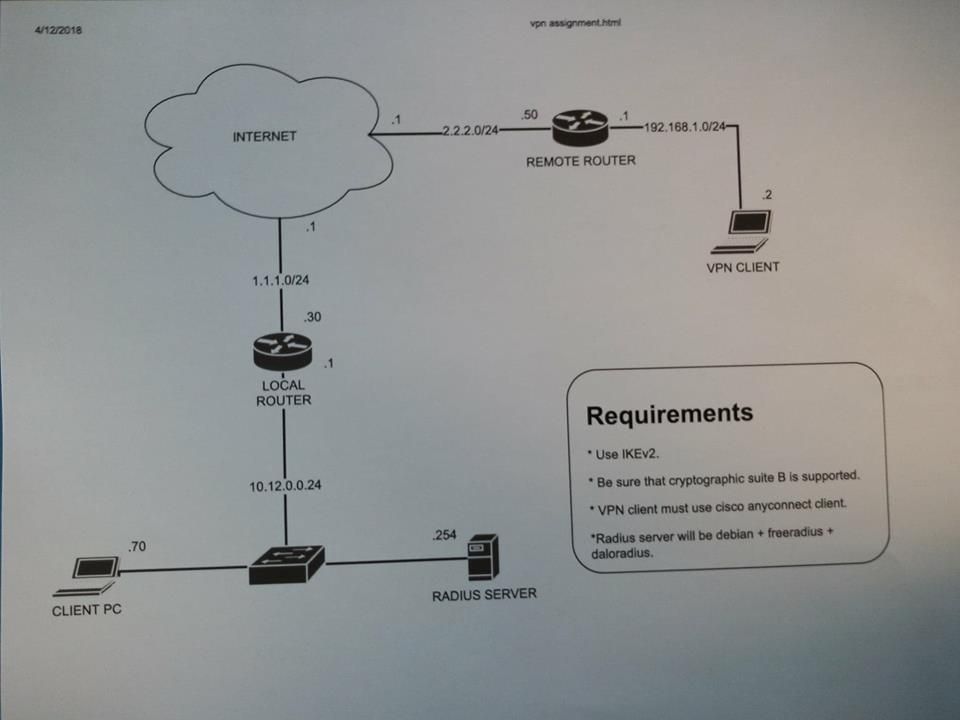
I come to ask you for help for a project in company during my internship. I have to deploy a remote VPN with AnyConnect. I give you the schema of the projet :
I generated a certificate on the router that I then exported to the Anyconnect client.
For the IKEv2 configuration I used this tutorial: https://www.cisco.com/c/en/us/support/docs/security/flexvpn/200555-FlexVPN-AnyConnect-IKEv2-Remote-Access.html
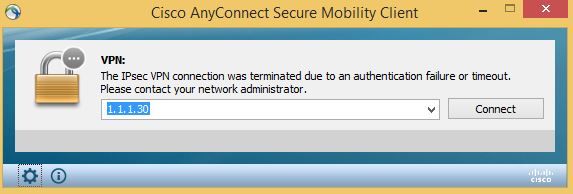
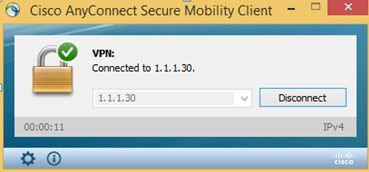
But when I try to connect with Anyconnect, I get the following error:
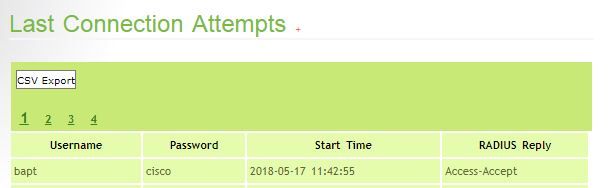
However as you can see on the picture the connection is successful on the Radius server so it doesn't make sense...
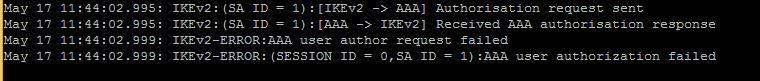
I give you IKEv2 logs on the router during the connection.
Thanks in advance for your help !
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2018 02:06 AM - edited 05-28-2018 02:08 AM
In the end I used the configuration of this article that I adapted to my project and it's working !
Thanks for helps guys !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2018 08:28 AM - edited 05-18-2018 08:43 AM
Hi,
In the screenshot that is probably a successful authentication, but authorization has still failed.
Can you post a screenshot of your authorization rules?
Could you enable debug "debug radius" repeat authentication, post the output here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2018 11:57 AM
Hi, thanks for your help !
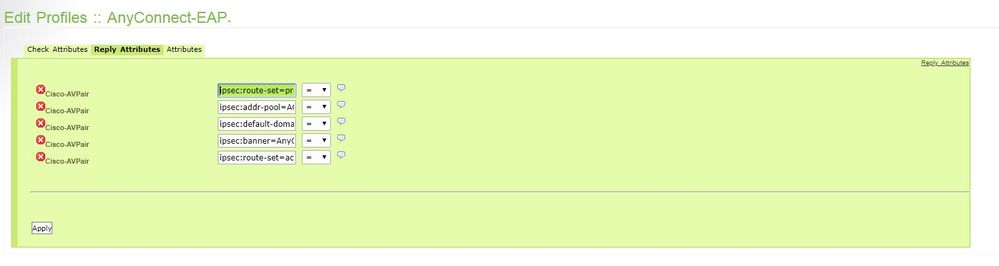
This is my rules as you can see they are the same as the tutorial.
My rules :
Tutorial :
I'm only going back to work on Tuesday so I can enable debug radius only in few days. Thanks :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2018 12:20 AM
Hi, I'm back at work so I enabled the "debug radius" and this is what I can see :
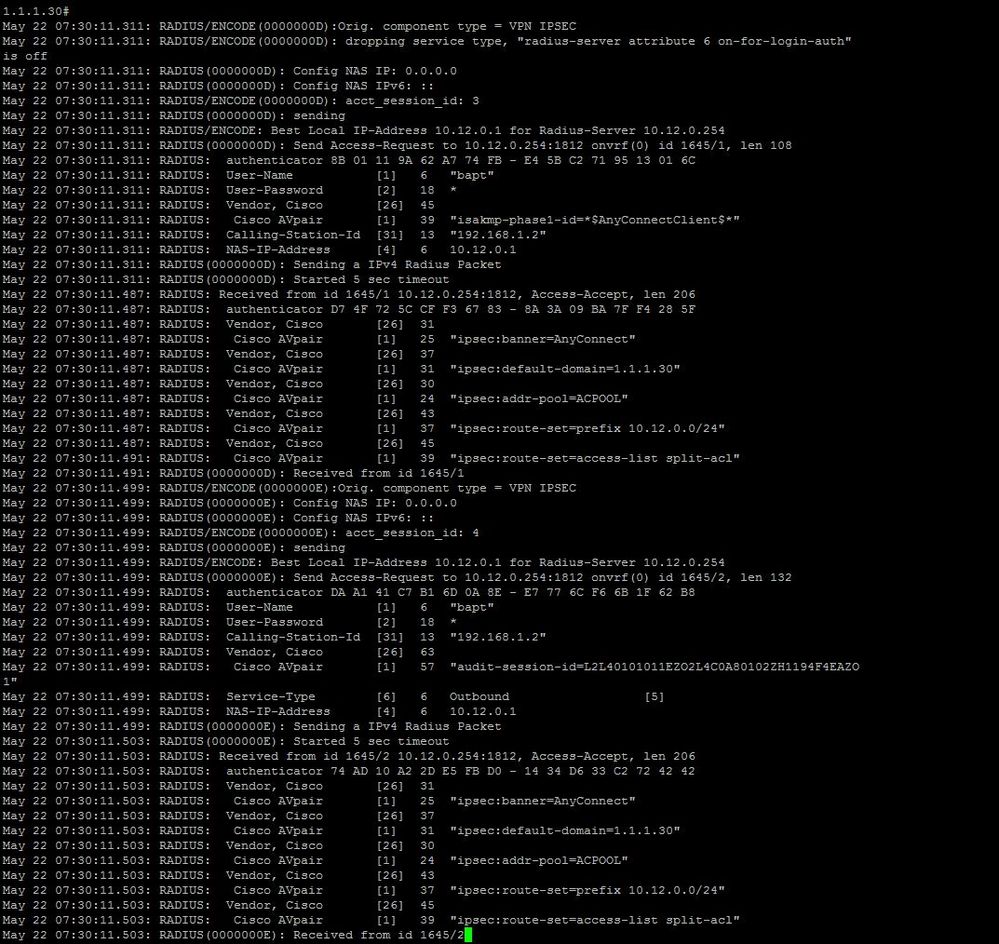
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2018 08:14 AM
Hi,
Did it generate any more logs than that? Could you also run "debug aaa authorization" and post the full output.
What errors are seen on the radius server when it fails authorization?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2018 08:36 AM
Hi when I run "debug crypto ikev2" I have all this logs :
1.1.1.30#debug crypto ikev2
IKEv2 default debugging is on
1.1.1.30#
May 22 15:41:57.239: IKEv2:Received Packet [From 192.168.1.2:54236/To 1.1.1.30:500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 0000000000000000 Message id: 0
IKEv2 IKE_SA_INIT Exchange REQUEST
Payload contents:
SA KE N VID VID VID VID VID NOTIFY(NAT_DETECTION_SOURCE_IP) NOTIFY(NAT_DETECTION_DESTINATION_IP) VID CFG NOTIFY(REDIRECT_SUPPORTED)
May 22 15:41:57.239: IKEv2:(SESSION ID = 2,SA ID = 1):Verify SA init message
May 22 15:41:57.239: IKEv2:(SESSION ID = 2,SA ID = 1):Insert SA
May 22 15:41:57.239: IKEv2:Searching Policy with fvrf 0, local address 1.1.1.30
May 22 15:41:57.239: IKEv2:Found Policy 'IKEv2-pol'
May 22 15:41:57.239: IKEv2:(SESSION ID = 2,SA ID = 1):Processing IKE_SA_INIT message
May 22 15:41:57.239: IKEv2:(SESSION ID = 2,SA ID = 1):Received valid config mode data
May 22 15:41:57.239: IKEv2:Config data recieved:
May 22 15:41:57.243: IKEv2:(SESSION ID = 2,SA ID = 1):Config-type: Config-request
May 22 15:41:57.243: IKEv2:(SESSION ID = 2,SA ID = 1):Attrib type: unknown, length: 2, data: 0x2 0x40
May 22 15:41:57.243: IKEv2:IKEv2 responder - ignoring config data received in IKE_SA_INIT exch
May 22 15:41:57.243: IKEv2:(SESSION ID = 2,SA ID = 1):Set received config mode data
May 22 15:41:57.243: IKEv2:(SA ID = 1):[IKEv2 -> PKI] Retrieve configured trustpoint(s)
May 22 15:41:57.243: IKEv2:(SA ID = 1):[PKI -> IKEv2] Retrieved trustpoint(s): 'cisco' 'root-ca'
May 22 15:41:57.243: IKEv2:(SA ID = 1):[IKEv2 -> PKI] Get Public Key Hashes of trustpoints
May 22 15:41:57.243: IKEv2:(SA ID = 1):[PKI -> IKEv2] Getting of Public Key Hashes of trustpoints PASSED
May 22 15:41:57.243: IKEv2:(SA ID = 1):[IKEv2 -> PKI] Start PKI Session
May 22 15:41:57.243: IKEv2:(SA ID = 1):[PKI -> IKEv2] Starting of PKI Session PASSED
May 22 15:41:57.243: IKEv2:(SESSION ID = 2,SA ID = 1):[IKEv2 -> Crypto Engine] Computing DH public key, DH Group 1
May 22 15:41:57.251: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] DH key Computation PASSED
May 22 15:41:57.251: IKEv2:(SESSION ID = 2,SA ID = 1):Request queued for computation of DH key
May 22 15:41:57.251: IKEv2:(SESSION ID = 2,SA ID = 1):[IKEv2 -> Crypto Engine] Computing DH secret key, DH Group 1
May 22 15:41:57.267: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] DH key Computation PASSED
May 22 15:41:57.267: IKEv2:(SESSION ID = 2,SA ID = 1):Request queued for computation of DH secret
May 22 15:41:57.267: IKEv2:(SA ID = 1):[IKEv2 -> Crypto Engine] Calculate SKEYSEED and create rekeyed IKEv2 SA
May 22 15:41:57.267: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] SKEYSEED calculation and creation of rekeyed IKEv2 SA PASSED
May 22 15:41:57.267: IKEv2:IKEv2 responder - no config data to send in IKE_SA_INIT exch
May 22 15:41:57.267: IKEv2:(SESSION ID = 2,SA ID = 1):Generating IKE_SA_INIT message
May 22 15:41:57.267: IKEv2:(SESSION ID = 2,SA ID = 1):IKE Proposal: 2, SPI size: 0 (initial negotiation),
Num. transforms: 4
AES-CBC SHA256 SHA256 DH_GROUP_768_MODP/Group 1
May 22 15:41:57.267: IKEv2:(SA ID = 1):[IKEv2 -> PKI] Retrieve configured trustpoint(s)
May 22 15:41:57.267: IKEv2:(SA ID = 1):[PKI -> IKEv2] Retrieved trustpoint(s): 'cisco' 'root-ca'
May 22 15:41:57.267: IKEv2:(SA ID = 1):[IKEv2 -> PKI] Get Public Key Hashes of trustpoints
May 22 15:41:57.267: IKEv2:(SA ID = 1):[PKI -> IKEv2] Getting of Public Key Hashes of trustpoints PASSED
May 22 15:41:57.267: IKEv2:(SESSION ID = 2,SA ID = 1):Sending Packet [To 192.168.1.2:54236/From 1.1.1.30:500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 1A9CE8C3101AD48F Message id: 0
IKEv2 IKE_SA_INIT Exchange RESPONSE
Payload contents:
SA KE N VID VID VID VID VID VID NOTIFY(NAT_DETECTION_SOURCE_IP) NOTIFY(NAT_DETECTION_DESTINATION_IP) CERTREQ
May 22 15:41:57.267: IKEv2:(SESSION ID = 2,SA ID = 1):Completed SA init exchange
May 22 15:41:57.267: IKEv2:(SESSION ID = 2,SA ID = 1):Starting timer (30 sec) to wait for auth message
May 22 15:41:57.287: IKEv2:(SESSION ID = 2,SA ID = 1):Received Packet [From 192.168.1.2:54237/To 1.1.1.30:500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 1A9CE8C3101AD48F Message id: 1
IKEv2 IKE_AUTH Exchange REQUEST
Payload contents:
VID IDi CERTREQ CFG SA NOTIFY(IPCOMP_SUPPORTED) TSi TSr NOTIFY(INITIAL_CONTACT) NOTIFY(ESP_TFC_NO_SUPPORT) NOTIFY(NON_FIRST_FRAGS)
May 22 15:41:57.287: IKEv2:(SESSION ID = 2,SA ID = 1):Stopping timer to wait for auth message
May 22 15:41:57.287: IKEv2:(SESSION ID = 2,SA ID = 1):Checking NAT discovery
May 22 15:41:57.287: IKEv2:(SESSION ID = 2,SA ID = 1):NAT OUTSIDE found
May 22 15:41:57.287: IKEv2:(SESSION ID = 2,SA ID = 1):NAT detected float to init port 54237, resp port 4500
May 22 15:41:57.287: IKEv2:(SESSION ID = 2,SA ID = 1):Searching policy based on peer's identity '*$AnyConnectClient$*' of type 'key ID'
May 22 15:41:57.287: IKEv2:found matching IKEv2 profile 'AnyConnect-EAP'
May 22 15:41:57.287: IKEv2:Searching Policy with fvrf 0, local address 1.1.1.30
May 22 15:41:57.287: IKEv2:Found Policy 'IKEv2-pol'
May 22 15:41:57.287: IKEv2:(SESSION ID = 2,SA ID = 1):Verify peer's policy
May 22 15:41:57.287: IKEv2:(SESSION ID = 2,SA ID = 1):Peer's policy verified
May 22 15:41:57.287: IKEv2:(SA ID = 1):[IKEv2 -> PKI] Retrieving trustpoint(s) from received certificate hash(es)
May 22 15:41:57.287: IKEv2:(SA ID = 1):[PKI -> IKEv2] Retrieved trustpoint(s): NONE
May 22 15:41:57.291: IKEv2:% Received cert hash is invalid, using configured trustpoints from profile for signing
May 22 15:41:57.291: IKEv2:(SA ID = 1):[IKEv2 -> PKI] Getting cert chain for the trustpoint cisco
May 22 15:41:57.291: IKEv2:(SA ID = 1):[PKI -> IKEv2] Getting of cert chain for the trustpoint PASSED
May 22 15:41:57.291: IKEv2:(SESSION ID = 2,SA ID = 1):Check for EAP exchange
May 22 15:41:57.291: IKEv2:(SESSION ID = 2,SA ID = 1):Check for EAP exchange
May 22 15:41:57.291: IKEv2:(SESSION ID = 2,SA ID = 1):Generate my authentication data
May 22 15:41:57.291: IKEv2:[IKEv2 -> Crypto Engine] Generate IKEv2 authentication data
May 22 15:41:57.291: IKEv2:[Crypto Engine -> IKEv2] IKEv2 authentication data generation PASSED
May 22 15:41:57.291: IKEv2:(SESSION ID = 2,SA ID = 1):Get my authentication method
May 22 15:41:57.291: IKEv2:(SESSION ID = 2,SA ID = 1):My authentication method is 'RSA'
May 22 15:41:57.291: IKEv2:(SESSION ID = 2,SA ID = 1):Sign authentication data
May 22 15:41:57.291: IKEv2:(SA ID = 1):[IKEv2 -> PKI] Getting private key
May 22 15:41:57.291: IKEv2:(SA ID = 1):[PKI -> IKEv2] Getting of private key PASSED
May 22 15:41:57.291: IKEv2:(SA ID = 1):[IKEv2 -> Crypto Engine] Sign authentication data
May 22 15:41:57.507: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] Signing of authenticaiton data PASSED
May 22 15:41:57.511: IKEv2:(SESSION ID = 2,SA ID = 1):Authentication material has been sucessfully signed
May 22 15:41:57.511: IKEv2:(SESSION ID = 2,SA ID = 1):Generating AnyConnect EAP request
May 22 15:41:57.511: IKEv2:(SESSION ID = 2,SA ID = 1):Sending AnyConnect EAP 'hello' request
May 22 15:41:57.511: IKEv2:(SESSION ID = 2,SA ID = 1):Constructing IDr payload: '1.1.1.30' of type 'IPv4 address'
May 22 15:41:57.511: IKEv2:(SESSION ID = 2,SA ID = 1):Building packet for encryption.
Payload contents:
VID IDr CERT CERT AUTH EAP
May 22 15:41:57.511: IKEv2:(SESSION ID = 2,SA ID = 1):Sending Packet [To 192.168.1.2:54237/From 1.1.1.30:4500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 1A9CE8C3101AD48F Message id: 1
IKEv2 IKE_AUTH Exchange RESPONSE
Payload contents:
ENCR
May 22 15:41:57.511: IKEv2:(SESSION ID = 2,SA ID = 1):Starting timer (90 sec) to wait for auth message
May 22 15:41:58.591: IKEv2:(SESSION ID = 2,SA ID = 1):Received Packet [From 192.168.1.2:54237/To 1.1.1.30:4500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 1A9CE8C3101AD48F Message id: 2
IKEv2 IKE_AUTH Exchange REQUEST
Payload contents:
EAP
May 22 15:41:58.591: IKEv2:(SESSION ID = 2,SA ID = 1):Stopping timer to wait for auth message
May 22 15:41:58.591: IKEv2:(SESSION ID = 2,SA ID = 1):Processing AnyConnect EAP response
May 22 15:41:58.591: IKEv2:(SESSION ID = 2,SA ID = 1):Generating AnyConnect EAP AUTH request
May 22 15:41:58.591: IKEv2:(SESSION ID = 2,SA ID = 1):Sending AnyConnect EAP 'auth-request'
May 22 15:41:58.591: IKEv2:(SESSION ID = 2,SA ID = 1):Building packet for encryption.
Payload contents:
EAP
May 22 15:41:58.591: IKEv2:(SESSION ID = 2,SA ID = 1):Sending Packet [To 192.168.1.2:54237/From 1.1.1.30:4500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 1A9CE8C3101AD48F Message id: 2
IKEv2 IKE_AUTH Exchange RESPONSE
Payload contents:
ENCR
May 22 15:41:58.591: IKEv2:(SESSION ID = 2,SA ID = 1):Starting timer (90 sec) to wait for auth message
May 22 15:42:04.487: IKEv2:(SESSION ID = 2,SA ID = 1):Received Packet [From 192.168.1.2:54237/To 1.1.1.30:4500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 1A9CE8C3101AD48F Message id: 3
IKEv2 IKE_AUTH Exchange REQUEST
Payload contents:
EAP
May 22 15:42:04.487: IKEv2:(SESSION ID = 2,SA ID = 1):Stopping timer to wait for auth message
May 22 15:42:04.487: IKEv2:(SESSION ID = 2,SA ID = 1):Processing AnyConnect EAP response
May 22 15:42:04.491: IKEv2:Using authentication method list a-eap-authen
May 22 15:42:04.491: IKEv2:(SA ID = 1):[IKEv2 -> AAA] Authentication request sent
May 22 15:42:04.495: IKEv2:Received response from aaa for AnyConnect EAP
May 22 15:42:04.495: IKEv2:(SESSION ID = 2,SA ID = 1):Generating AnyConnect EAP VERIFY request
May 22 15:42:04.495: IKEv2:(SESSION ID = 2,SA ID = 1):Sending AnyConnect EAP 'VERIFY' request
May 22 15:42:04.495: IKEv2:(SESSION ID = 2,SA ID = 1):Building packet for encryption.
Payload contents:
EAP
May 22 15:42:04.495: IKEv2:(SESSION ID = 2,SA ID = 1):Sending Packet [To 192.168.1.2:54237/From 1.1.1.30:4500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 1A9CE8C3101AD48F Message id: 3
IKEv2 IKE_AUTH Exchange RESPONSE
Payload contents:
ENCR
May 22 15:42:04.495: IKEv2:(SESSION ID = 2,SA ID = 1):Starting timer (90 sec) to wait for auth message
May 22 15:42:04.499: IKEv2:(SESSION ID = 2,SA ID = 1):Received Packet [From 192.168.1.2:54237/To 1.1.1.30:4500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 1A9CE8C3101AD48F Message id: 4
IKEv2 IKE_AUTH Exchange REQUEST
Payload contents:
EAP
May 22 15:42:04.499: IKEv2:(SESSION ID = 2,SA ID = 1):Stopping timer to wait for auth message
May 22 15:42:04.499: IKEv2:(SESSION ID = 2,SA ID = 1):Processing AnyConnect EAP ack response
May 22 15:42:04.499: IKEv2:(SESSION ID = 2,SA ID = 1):Generating AnyConnect EAP success request
May 22 15:42:04.499: IKEv2:(SESSION ID = 2,SA ID = 1):Sending AnyConnect EAP success status message
May 22 15:42:04.499: IKEv2:(SESSION ID = 2,SA ID = 1):Building packet for encryption.
Payload contents:
EAP
May 22 15:42:04.499: IKEv2:(SESSION ID = 2,SA ID = 1):Sending Packet [To 192.168.1.2:54237/From 1.1.1.30:4500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 1A9CE8C3101AD48F Message id: 4
IKEv2 IKE_AUTH Exchange RESPONSE
Payload contents:
ENCR
May 22 15:42:04.499: IKEv2:(SESSION ID = 2,SA ID = 1):Starting timer (90 sec) to wait for auth message
May 22 15:42:04.503: IKEv2:(SESSION ID = 2,SA ID = 1):Received Packet [From 192.168.1.2:54237/To 1.1.1.30:4500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 1A9CE8C3101AD48F Message id: 5
IKEv2 IKE_AUTH Exchange REQUEST
Payload contents:
AUTH
May 22 15:42:04.503: IKEv2:(SESSION ID = 2,SA ID = 1):Stopping timer to wait for auth message
May 22 15:42:04.503: IKEv2:(SESSION ID = 2,SA ID = 1):Send AUTH, to verify peer after EAP exchange
May 22 15:42:04.503: IKEv2:(SESSION ID = 2,SA ID = 1):Verify peer's authentication data
May 22 15:42:04.503: IKEv2:(SESSION ID = 2,SA ID = 1):Use preshared key for id *$AnyConnectClient$*, key len 32
May 22 15:42:04.503: IKEv2:[IKEv2 -> Crypto Engine] Generate IKEv2 authentication data
May 22 15:42:04.503: IKEv2:[Crypto Engine -> IKEv2] IKEv2 authentication data generation PASSED
May 22 15:42:04.503: IKEv2:(SESSION ID = 2,SA ID = 1):Verification of peer's authenctication data PASSED
May 22 15:42:04.503: IKEv2:(SESSION ID = 2,SA ID = 1):Processing INITIAL_CONTACT
May 22 15:42:04.503: IKEv2:Using mlist a-eap-author and username bapt for group author request
May 22 15:42:04.503: IKEv2:(SA ID = 1):[IKEv2 -> AAA] Authorisation request sent
May 22 15:42:04.507: IKEv2:(SA ID = 1):[AAA -> IKEv2] Received AAA authorisation response
May 22 15:42:04.507: IKEv2-ERROR:AAA user author request failed
May 22 15:42:04.507: IKEv2-ERROR:(SESSION ID = 0,SA ID = 1):AAA user authorization failed
May 22 15:42:04.507: IKEv2-ERROR:(SESSION ID = 0,SA ID = 1):
May 22 15:42:04.507: IKEv2:(SESSION ID = 2,SA ID = 1):Verification of peer's authentication data FAILED
May 22 15:42:04.507: IKEv2:(SESSION ID = 2,SA ID = 1):Sending authentication failure notify
May 22 15:42:04.507: IKEv2:(SESSION ID = 2,SA ID = 1):Building packet for encryption.
Payload contents:
NOTIFY(AUTHENTICATION_FAILED)
May 22 15:42:04.507: IKEv2:(SESSION ID = 2,SA ID = 1):Sending Packet [To 192.168.1.2:54237/From 1.1.1.30:4500/VRF i0:f0]
Initiator SPI : C824BA07A776E9FE - Responder SPI : 1A9CE8C3101AD48F Message id: 5
IKEv2 IKE_AUTH Exchange RESPONSE
Payload contents:
ENCR
May 22 15:42:04.507: IKEv2:(SESSION ID = 2,SA ID = 1):Auth exchange failed
May 22 15:42:04.507: IKEv2-ERROR:(SESSION ID = 2,SA ID = 1):: Auth exchange failed
May 22 15:42:04.511: IKEv2:(SESSION ID = 2,SA ID = 1):Abort exchange
May 22 15:42:04.511: IKEv2:(SESSION ID = 2,SA ID = 1):Deleting SA
May 22 15:42:04.511: IKEv2:(SA ID = 1):[IKEv2 -> PKI] Close PKI Session
May 22 15:42:04.511: IKEv2:(SA ID = 1):[PKI -> IKEv2] Closing of PKI Session PASSED
Then the "debug aaa authorization" :
1.1.1.30#debug aaa authorization
AAA Authorization debugging is on
1.1.1.30#
May 22 15:43:49.623: AAA/BIND(00000011): Bind i/f
May 22 15:43:49.635: AAA/BIND(00000012): Bind i/f
May 22 15:43:49.635: AAA/AUTHOR (0x12): Pick method list 'a-eap-author'
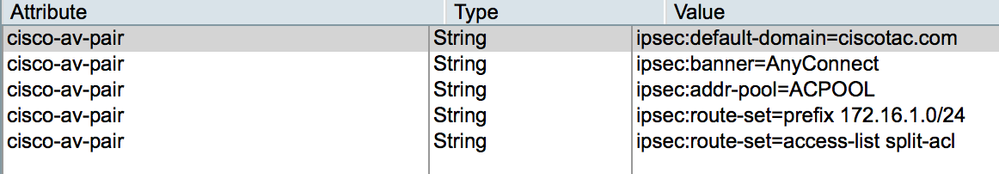
And for finish logs of the radius server looks good :
Thanks for taking the time to read this :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2018 08:47 AM
I can see in the router logs authorization fails, but no indication why.
May 22 15:42:04.507: IKEv2-ERROR:(SESSION ID = 0,SA ID = 1):AAA user authorization failed.
I have a suspicion it's related to the name-mangler configured, but want some logs to look at.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2018 12:39 AM
I can't have more details with authorization logs. If I run the "debug aaa authorization" "debug aaa authentication" and "debug radius authentication", I have the following logs but that's it :
May 23 07:46:35.219: AAA/BIND(00000017): Bind i/f
May 23 07:46:35.219: AAA/AUTHEN/LOGIN (00000017): Pick method list 'a-eap-authen'
May 23 07:46:35.219: RADIUS/ENCODE(00000017):Orig. component type = VPN IPSEC
May 23 07:46:35.219: RADIUS/ENCODE(00000017): dropping service type, "radius-server attribute 6 on-for-login-autis off
May 23 07:46:35.219: RADIUS(00000017): Config NAS IP: 0.0.0.0
May 23 07:46:35.219: RADIUS(00000017): Config NAS IPv6: ::
May 23 07:46:35.219: RADIUS/ENCODE(00000017): acct_session_id: 13
May 23 07:46:35.219: RADIUS(00000017): sending
May 23 07:46:35.219: RADIUS/ENCODE: Best Local IP-Address 10.12.0.1 for Radius-Server 10.12.0.254
May 23 07:46:35.219: RADIUS(00000017): Send Access-Request to 10.12.0.254:1812 onvrf(0) id 1645/10, len 108
May 23 07:46:35.219: RADIUS: authenticator BE E3 1C FB 16 BF 40 6C - A3 4E 7D 35 BA 49 2D 55
May 23 07:46:35.219: RADIUS: User-Name [1] 6 "bapt"
May 23 07:46:35.219: RADIUS: User-Password [2] 18 *
May 23 07:46:35.219: RADIUS: Vendor, Cisco [26] 45
May 23 07:46:35.219: RADIUS: Cisco AVpair [1] 39 "isakmp-phase1-id=*$AnyConnectClient$*"
May 23 07:46:35.219: RADIUS: Calling-Station-Id [31] 13 "192.168.1.2"
May 23 07:46:35.219: RADIUS: NAS-IP-Address [4] 6 10.12.0.1
May 23 07:46:35.219: RADIUS(00000017): Sending a IPv4 Radius Packet
May 23 07:46:35.219: RADIUS(00000017): Started 5 sec timeout
May 23 07:46:35.227: RADIUS: Received from id 1645/10 10.12.0.254:1812, Access-Accept, len 206
May 23 07:46:35.227: RADIUS: authenticator 9F CF 2A 99 9E B1 CA 0B - 9C 3D 8E 24 89 C5 15 3A
May 23 07:46:35.227: RADIUS: Vendor, Cisco [26] 31
May 23 07:46:35.227: RADIUS: Cisco AVpair [1] 25 "ipsec:banner=AnyConnect"
May 23 07:46:35.227: RADIUS: Vendor, Cisco [26] 37
May 23 07:46:35.227: RADIUS: Cisco AVpair [1] 31 "ipsec:default-domain=1.1.1.30"
May 23 07:46:35.227: RADIUS: Vendor, Cisco [26] 30
May 23 07:46:35.227: RADIUS: Cisco AVpair [1] 24 "ipsec:addr-pool=ACPOOL"
May 23 07:46:35.227: RADIUS: Vendor, Cisco [26] 43
May 23 07:46:35.227: RADIUS: Cisco AVpair [1] 37 "ipsec:route-set=prefix 10.12.0.0/24"
May 23 07:46:35.227: RADIUS: Vendor, Cisco [26] 45
May 23 07:46:35.227: RADIUS: Cisco AVpair [1] 39 "ipsec:route-set=access-list split-acl"
May 23 07:46:35.227: RADIUS(00000017): Received from id 1645/10
May 23 07:46:35.235: AAA/BIND(00000018): Bind i/f
May 23 07:46:35.235: AAA/AUTHOR (0x18): Pick method list 'a-eap-author'
May 23 07:46:35.235: RADIUS/ENCODE(00000018):Orig. component type = VPN IPSEC
May 23 07:46:35.235: RADIUS(00000018): Config NAS IP: 0.0.0.0
May 23 07:46:35.235: RADIUS(00000018): Config NAS IPv6: ::
May 23 07:46:35.235: RADIUS/ENCODE(00000018): acct_session_id: 14
May 23 07:46:35.235: RADIUS(00000018): sending
May 23 07:46:35.235: RADIUS/ENCODE: Best Local IP-Address 10.12.0.1 for Radius-Server 10.12.0.254
May 23 07:46:35.235: RADIUS(00000018): Send Access-Request to 10.12.0.254:1812 onvrf(0) id 1645/11, len 132
May 23 07:46:35.235: RADIUS: authenticator 6E 84 20 11 48 00 25 86 - 4B C4 50 E2 85 84 EA CA
May 23 07:46:35.235: RADIUS: User-Name [1] 6 "bapt"
May 23 07:46:35.235: RADIUS: User-Password [2] 18 *
May 23 07:46:35.235: RADIUS: Calling-Station-Id [31] 13 "192.168.1.2"
May 23 07:46:35.239: RADIUS: Vendor, Cisco [26] 63
May 23 07:46:35.239: RADIUS: Cisco AVpair [1] 57 "audit-session-id=L2L40101011EZO2L4C0A80102ZH1194C376"
May 23 07:46:35.239: RADIUS: Service-Type [6] 6 Outbound [5]
May 23 07:46:35.239: RADIUS: NAS-IP-Address [4] 6 10.12.0.1
May 23 07:46:35.239: RADIUS(00000018): Sending a IPv4 Radius Packet
May 23 07:46:35.239: RADIUS(00000018): Started 5 sec timeout
May 23 07:46:35.239: RADIUS: Received from id 1645/11 10.12.0.254:1812, Access-Accept, len 206
May 23 07:46:35.239: RADIUS: authenticator 1C 82 62 0F 16 77 DE 28 - 94 CB 94 33 2B BE D1 31
May 23 07:46:35.239: RADIUS: Vendor, Cisco [26] 31
May 23 07:46:35.239: RADIUS: Cisco AVpair [1] 25 "ipsec:banner=AnyConnect"
May 23 07:46:35.239: RADIUS: Vendor, Cisco [26] 37
May 23 07:46:35.239: RADIUS: Cisco AVpair [1] 31 "ipsec:default-domain=1.1.1.30"
May 23 07:46:35.239: RADIUS: Vendor, Cisco [26] 30
May 23 07:46:35.239: RADIUS: Cisco AVpair [1] 24 "ipsec:addr-pool=ACPOOL"
May 23 07:46:35.239: RADIUS: Vendor, Cisco [26] 43
May 23 07:46:35.239: RADIUS: Cisco AVpair [1] 37 "ipsec:route-set=prefix 10.12.0.0/24"
May 23 07:46:35.239: RADIUS: Vendor, Cisco [26] 45
May 23 07:46:35.239: RADIUS: Cisco AVpair [1] 39 "ipsec:route-set=access-list split-acl"
May 23 07:46:35.239: RADIUS(00000018): Received from id 1645/11
This issue really doesn't make sense ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2018 05:26 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2018 08:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2018 02:06 AM - edited 05-28-2018 02:08 AM
In the end I used the configuration of this article that I adapted to my project and it's working !
Thanks for helps guys !
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: