Hi, Has anyone had issues where you are running FTD with AnyConnect (secureclient) with Posture (DAP) enabled and some computers are sending the attribute endpoint.am=xxx and others aren't? I have several devices not sending the anti-malware attrib...
VPN
- Mark all as New
- Mark all as Read
- Float this item to the top
- Subscribe
- Bookmark
- Subscribe to RSS Feed
- Threaded format
- Linear Format
- Sort by Topic Start Date
The content you are looking for has been archived. View related content below.
-
AAA
(3) -
Access Control Server (ACS)
(1) -
AnyConnect
(6,519) -
Appliances
(1) -
ASA
(1) -
ASR 1000 Series
(1) -
ATAs and Gateways and Accessories
(1) -
Buying Recommendation
(34) -
Catalyst Switch
(1) -
Cisco Adaptive Security Appliance (ASA)
(28) -
Cisco Bugs
(1) -
Cisco Cafe
(14) -
Cisco Cloud Services Router
(2) -
Cisco DNA
(2) -
Cisco DNA Automation
(1) -
Cisco Firepower Device Manager (FDM)
(2) -
Cisco Firepower Management Center (FMC)
(4) -
Cisco Firepower Threat Defense (FTD)
(6) -
Cisco Software
(6) -
Cisco Start India
(1) -
Clientless SSL
(266) -
Cloud Security
(1) -
Community Feedback Forum
(15) -
Community Ideas
(9) -
Compliance and Posture
(2) -
Conferencing
(1) -
Connectivity Issues and VPN
(1) -
Device Admin
(1) -
DMVPN
(733) -
Duo
(63) -
Emergency Responder
(1) -
Enterprise Agreement
(1) -
Firewalls
(1) -
FlexVPN
(169) -
General
(1) -
GetVPN
(135) -
Identity Services Engine (ISE)
(5) -
IPSEC
(4,296) -
ISR 1000 Series
(2) -
ISR 4000 Series
(4) -
LAN Switching
(2) -
License
(1) -
Network Management
(21) -
New Document Idea
(1) -
NGFW Firewalls
(3) -
Optical Networking
(1) -
Other Cisco DNA
(1) -
Other Collaboration Topics
(3) -
Other Community Feedback
(1) -
Other IP Telephony
(1) -
Other NAC
(1) -
Other Network
(13) -
Other Network Security Topics
(8) -
Other Networking
(6) -
Other Routers
(8) -
Other Routing
(13) -
Other Security Topics
(2) -
Other Switches
(2) -
Other Switching
(1) -
Other VPN Topics
(13,560) -
Other Wireless and Mobility Subjects
(1) -
Other Wireless Topics
(2) -
Physical Security
(3) -
Remote Access
(5,845) -
Routers
(1) -
Routing
(2) -
Routing Protocols
(12) -
RV340
(1) -
Security Certifications
(1) -
Security Management
(3) -
Small Business Routers
(2) -
Small Business Switches
(1) -
Storage Networking
(1) -
Umbrella
(26) -
VPN
(22,048) -
VPN and AnyConnect
(1) -
VPN y AnyConnect
(4) -
WAN
(2) -
Web Security
(2) -
Wired
(1) -
Wireless Network Management
(3) -
Wireless Security
(5) -
Wireless Security and Network Management
(1)
- « Previous
- Next »
Forum Posts
I have multiple AnyConnect connection profiles for various remote users that provide access to different internal networks. The authentication method needs to be certificate only, but there doesn't seem to be a way to prevent an issued certificate ho...
Hello, Is it possible on Cisco FTD managed by Cisco FMC define multiple DH Group in Phase2 ? From what i see it is just possible one. I tried put , but it doesnt accept. Also looking maybe for option to add thorugh flex config but didnt find any rel...
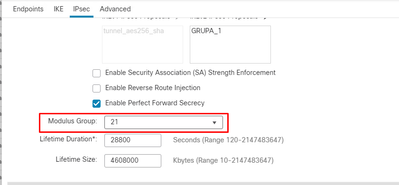
Hi Team,Our Router having many ikev2 proposal, as per TAC suggestion we need to combine in to single policy. Please let me know for this activity any down time needed ?
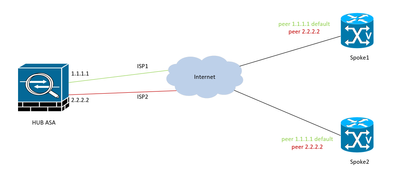
Hi All. I would like to get your thoughts on the following issue i have been facing since implementing Dual ISP and failover for site-to-site vpn tunnels.Hub Site:ASA5515 using 9.6(4)42Spoke sites:Cisco ISRs using 15.1(4)M8, using voip services over ...
Hi! The last weeks it has been a big increase of brute force attempts from all over the world to our Cisco ASAs. We use two factors, so we're not to afraid that they will actually access any of our accounts, but the problem is that they manage to blo...
Following upgrading to upgrading to 5.1.2.42 to fix the vulnerability CVE-2024-20337Within Microsoft Defender this is still flagged as vulnerability for the CVEIt appears to refer to a component of the install:C:\Program Files (x86)\Cisco\Cisco Secur...
As per the CVE, the detailed information is available in the advisory : Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software Remote Access VPN Unauthorized Access Vulnerabilityhttps://sec.cloudapps.cisco.com/security/cente...
Resolved! No SSL trust-points configured
Working on VPN and we are getting errors stating no TP found. Did a sh ssl/ sh run ssl and got weird information back but need help with understanding TP's
Hi, I am currently encountering issue on route-based ipsec vpn. I cannot ping my remote IP also the remote tunnel. I have verified that there is no decap showing on packets. I already configured static route between each site and still unsucessful of...
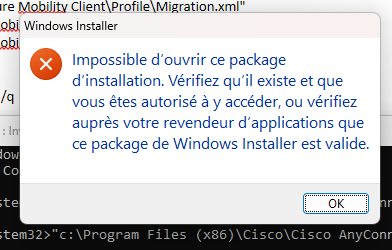
Hello,I try to uninstall silent Cisco AnyConnect Secure Mobility Client v4.9.06037 :"%ProgramFiles(x86)%\Cisco\Cisco AnyConnect Secure Mobility Client\vpnui.exe" -remove -silent >>> Doesn't Work Msiexec /x {id] > not work. Please help me.
Hi, I have one issue with IPSec tunnel Lan-to-Lan between ASA 5525x (v9.8) and ASA FPR 2110 (v9.16). My Tunnel is up but ping between each client was not successful. Both peer status sh cry isakmp sa in "MM_ACTIVE".I ran packet-tracer icmp between pe...
Hi all, I have a bit of an issue where I work in that we have a number of very old series 800 routers with either an advsecurity license or a securityk9 license installed, I don't have the smart accounts for any of these (before my time) and I am now...
The following message is displayed when the connection button is pressed. Please tell me how to solve it. Certificate Validation Failure AnyConnect VPI version 5.0.04232 Secure Client UI version 5.0.00889 Certificate Expiration Date 2025/4/3
Hi, We are trying to implement Azure SAML SSO on our Firepower 1010. We are using ASA 9.19.1 and Secure client 5.0.02075. When we try the login via Azure by clicking the "Test this applicaton" the login works and there are no errors in the logs. The ...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
| Subject | Author | Posted |
|---|---|---|
| 04-24-2024 01:26 AM | ||
| 04-19-2024 08:08 AM | ||
| 04-18-2024 10:47 AM | ||
| 04-03-2024 04:45 AM | ||
| 03-27-2024 07:28 AM |
| User | Count |
|---|---|
| 6 | |
| 4 | |
| 1 | |
| 1 | |
| 1 |





