- Cisco Community
- Technology and Support
- Security
- VPN
- IPSEC and Tunnel Protection
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2013 04:43 AM - edited 02-21-2020 07:18 PM
Network Diagram
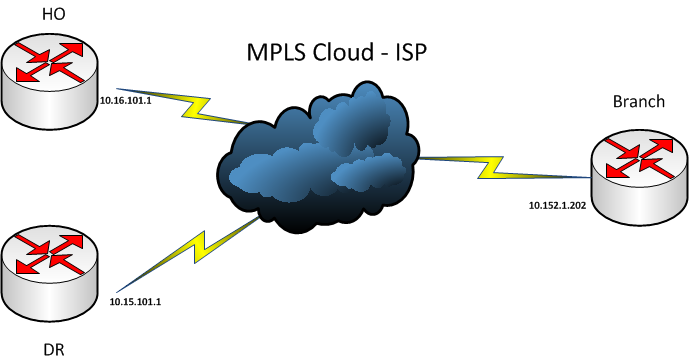
Config of Branch
IOS Version
(C2801-ADVIPSERVICESK9-M), Version 12.4(15)T7,
Physical Interface
interface Vlan220
ip address 10.152.1.202 255.255.255.252
no ip redirects
no ip unreachables
no ip proxy-arp
no ip route-cache cef
no ip route-cache
Tunnel connecting to **
interface Tunnel220
ip address 192.168.220.5 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip mtu 1430
ip nhrp authentication dmvpn243
ip nhrp map multicast 10.16.101.1
ip nhrp map 192.168.220.1 10.16.101.1
ip nhrp network-id 243
ip nhrp holdtime 3600
ip nhrp nhs 192.168.220.1
no ip route-cache cef
no ip route-cache
ip tcp adjust-mss 1330
ip ospf network point-to-multipoint
ip ospf cost 10
ip ospf hello-interval 10
ip ospf priority 0
ip ospf mtu-ignore
tunnel source Vlan220
tunnel mode gre multipoint
tunnel key 243
tunnel protection ipsec profile dmvpn-profile
end
Tunnel Connecting to DR
interface Tunnel230
ip address 192.168.230.1 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication dmvpn230
ip nhrp map 192.168.230.254 10.15.101.1
ip nhrp map multicast 10.15.101.1
ip nhrp network-id 230
ip nhrp holdtime 3600
ip nhrp nhs 192.168.230.254
tunnel source Vlan220
tunnel mode gre multipoint
tunnel key 230
tunnel protection ipsec profile dr
Problem
Show crypto ipsec output ( ommited )
Crypto map tag: Tunnel220-head-0, local addr 10.152.1.202
protected vrf: (none)
local ident (addr/mask/prot/port): (10.152.1.202/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (10.15.101.1/255.255.255.255/47/0)
local ident (addr/mask/prot/port): (10.152.1.202/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (10.16.101.1/255.255.255.255/47/0)
Crypto map tag: Tunnel230-head-0, local addr 10.152.1.202
protected vrf: (none)
local ident (addr/mask/prot/port): (10.152.1.202/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (10.15.101.1/255.255.255.255/47/0)
I am making secure connection to DR ( 10.15.101.1 ) and tunnel comes up however there are some issues with IPSEC . When i remove tunnel protection things start working properly and I can receive ping replies from both ends which means NHRP / DMVPN config is perfect . The issue with IPSEC ( phase 2 ) is that I want to connect 10.15.101.1 ( DR ) and Branch ( 10.152.1.202 ) .
When I check show crypto ipsec sa I can see duplicate proxy identies i.e. 10.152.1.202 - 10.15.101.1 from tunnel 220 ( posted above in quote ) and again in tunnel 230 . To make things work fine it should only appear in Tunnel 230 config . When I shutdown tunnel 220 the proxy identity goes away from 220 and the only one left is being learned from Tunnel 230 ( the right one ) after that it starts working properly but when both tunnels are up again duplicate entries would come up and i cant ping the other end ( tunnel ) i.e. 192.168.230.x being learned through 10.15.101.1 .
Could this be due to IOS bug ? Note that in above config ( tunnel 220 which points to ** ) I have put ip nhrp map 192.168.220.1 10.16.101.1 which means that in crypto ipsec ( for tunnel 220 ) I should only receive connection to 10.16.101.1 and not 10.15.101.1 .
Solved! Go to Solution.
- Labels:
-
IPSEC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2013 08:52 AM
Hmmmm, phase 1 DMVPN (which is using point to point on spoke side) doesn't require shared ;-)
It's only multipoint interface problem.
Wll anyway, glad it worked out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2013 07:56 AM
Since you're sourcing two DMVPN tunnels from same source interface, you should use same IPsec profile and "shared" keyword for this conf to be correct.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2013 08:28 AM
Thanks Marcin
If I am having the encryption policies correct then it shoulndt be a problem but considering this a IOS level programing limitation I thought of giving it a try , i used same policy and the result was same .
interface Tunnel220
ip address 192.168.220.5 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip mtu 1430
ip nhrp authentication dmvpn243
ip nhrp map multicast 10.16.101.1
ip nhrp map 192.168.220.1 10.16.101.1
ip nhrp network-id 243
ip nhrp holdtime 3600
ip nhrp nhs 192.168.220.1
no ip route-cache cef
no ip route-cache
ip tcp adjust-mss 1330
ip ospf network point-to-multipoint
ip ospf cost 10
ip ospf hello-interval 10
ip ospf priority 0
ip ospf mtu-ignore
tunnel source Vlan220
tunnel mode gre multipoint
tunnel key 243
tunnel protection ipsec profile dmvpn-profile
end
Current configuration : 452 bytes
!
interface Tunnel230
ip address 192.168.230.1 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication dmvpn230
ip nhrp map 192.168.230.254 10.15.101.1
ip nhrp map multicast 10.15.101.1
ip nhrp network-id 230
ip nhrp holdtime 3600
ip nhrp nhs 192.168.230.254
tunnel source Vlan220
tunnel mode gre multipoint
tunnel key 230
tunnel protection ipsec profile dmvpn-profile
Then I thought it might be reasonable to use that shared keyword rather than dmvpn-profile or else so I even tried that and results were same . I have done the same setup with another customer using 1700 routers ( shared profiles ) and it worked like a charm , dont know why is it showing tunnel 230 proxy identity in tunnel 220 details .
Glad if anyone can provide help .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2013 08:43 AM
You are still missing the shared keyword.
What happens later we'll see:
show crypto map
show crypto ipsec sa
show crypto rule
are minimum needed.
Just open a TAC case and have the guys help you out figuring the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2013 08:50 AM
Thanks Marcin , works like a charm
The other customer never had this problem , they were running 1700 , IOS 12.3 running DMVPN Phase 1 with shared ipsec profiles but I never used shared keyword after profile name , maybe something new because of newer code .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2013 08:52 AM
Hmmmm, phase 1 DMVPN (which is using point to point on spoke side) doesn't require shared ;-)
It's only multipoint interface problem.
Wll anyway, glad it worked out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2013 09:21 AM
Thanks , with phase 1 I was still using one single physical interface to source 2 tunnels but with that the ipsec algo must be running different way
Thanks a lot
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide