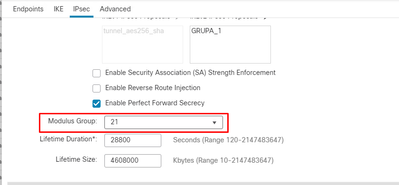
Hello, Is it possible on Cisco FTD managed by Cisco FMC define multiple DH Group in Phase2 ? From what i see it is just possible one. I tried put , but it doesnt accept. Also looking maybe for option to add thorugh flex config but didnt find any rel...