- Cisco Community
- Technology and Support
- Security
- VPN
- IPSEC L2L Between ASA and Cyberoam
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2016 11:03 PM - edited 02-21-2020 08:59 PM
Hi All,
Im currently facing an issue with l2l ipsec between Cisco ASA (9.X) to Cyberoam Firewall.
We have Phase 1 and Phase 2 with PSK matched, but seems like the ASA stuck in MM_WAIT_MSG6
The Cyberoam Firewall is not behind any NAT device while the ASA is behind a NAT router.
Below is the Configuration in Cyberoam
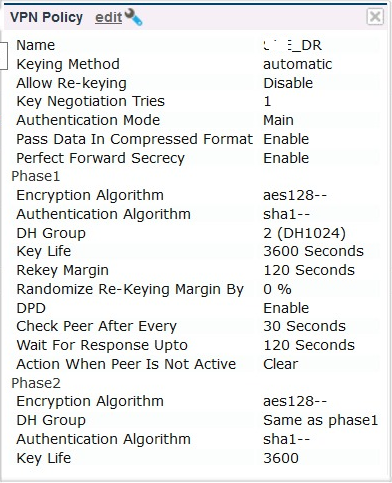
Here is the config in ASA
!
object network TEST_DC
subnet 192.168.100.0 255.255.255.0
!
object network GC_NOC_MAPPED_LAN
subnet 192.168.110.0 255.255.255.0
!
object network GC_NOCPC_MAPPED_LAN
host 192.168.110.110
!
object network GC_NOCPC_LAN
host 192.168.88.110
nat (inside,Internet) static GC_NOCPC_MAPPED_LAN
!
!
access-list TEST_VPN extended permit ip object GC_NOC_MAPPED_LAN object TEST_DC
!
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
!
crypto map outside_map 4 match address TEST_VPN
crypto map outside_map 4 set pfs
crypto map outside_map 4 set peer 1.1.1.1
crypto map outside_map 4 set ikev1 transform-set ESP-AES-128-SHA
crypto map outside_map 4 set security-association lifetime seconds 3600
!
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 3600
!
tunnel-group 1.1.1.1 type ipsec-l2l
tunnel-group 1.1.1.1 ipsec-attributes
ikev1 pre-shared-key *****
Below is the Message from Debug crypto ikev1 127 and ipsec 127:
A5512X-GF-FW01#
A5512X-GF-FW01# debug crypto ikev1 127Sep 20 11:05:52 [IKEv1 DEBUG]Pitcher: received a key acquire message, spi 0x0
Sep 20 11:05:52 [IKEv1]NAT-T disabled in crypto map outside_map 4.
Sep 20 11:05:52 [IKEv1]IP = 1.1.1.1, IKE Initiator: New Phase 1, Intf inside, IKE Peer 1.1.1.1 local Proxy Address 192.168.110.0, remote Proxy Address 192.168.100.0, Crypto map (outside_map)
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, constructing ISAKMP SA payload
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, constructing Fragmentation VID + extended capabilities payload
Sep 20 11:05:52 [IKEv1]IP = 1.1.1.1, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + NONE (0) total length : 148
Sep 20 11:05:52 [IKEv1]IP = 1.1.1.1, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 124
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, processing SA payload
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, Oakley proposal is acceptable
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, processing VID payload
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, Received DPD VID
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, processing VID payload
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, Received Cisco Unity client VID
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, constructing ke payload
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, constructing nonce payload
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, constructing Cisco Unity VID payload
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, constructing xauth V6 VID payload
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, Send IOS VID
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, Constructing ASA spoofing IOS Vendor ID payload (version: 1.0.0, capabilities: 20000001)
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, constructing VID payload
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, Send Altiga/Cisco VPN3000/Cisco ASA GW VID
Sep 20 11:05:52 [IKEv1]IP = 1.1.1.1, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + KE (4) + NONCE (10) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 256
Sep 20 11:05:52 [IKEv1]IP = 1.1.1.1, Header invalid, missing SA payload! (next payload = 4)
Sep 20 11:05:52 [IKEv1]IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 68
Sep 20 11:05:52 [IKEv1]IP = 1.1.1.1, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + KE (4) + NONCE (10) + NONE (0) total length : 180
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, processing ke payload
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, processing ISA_KE payload
Sep 20 11:05:52 [IKEv1 DEBUG]IP = 1.1.1.1, processing nonce payload
Sep 20 11:05:52 [IKEv1]IP = 1.1.1.1, Connection landed on tunnel_group 1.1.1.1
Sep 20 11:05:52 [IKEv1 DEBUG]Group = 1.1.1.1, IP = 1.1.1.1, Generating keys for Initiator...
Sep 20 11:05:52 [IKEv1 DEBUG]Group = 1.1.1.1, IP = 1.1.1.1, constructing ID payload
Sep 20 11:05:52 [IKEv1 DEBUG]Group = 1.1.1.1, IP = 1.1.1.1, constructing hash payload
Sep 20 11:05:52 [IKEv1 DEBUG]Group = 1.1.1.1, IP = 1.1.1.1, Computing hash for ISAKMP
Sep 20 11:05:52 [IKEv1 DEBUG]Group = 1.1.1.1, IP = 1.1.1.1, constructing dpd vid payload
Sep 20 11:05:52 [IKEv1]IP = 1.1.1.1, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + ID (5) + HASH (8) + VENDOR (13) + NONE (0) total length : 84
debug crypto ikev1 127
Sep 20 11:27:20 [IKEv1]IP = 1.1.1.1, Header invalid, missing SA payload! (next payload = 4)
A5512X-GF-FW01#
A5512X-GF-FW01# IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=1, saddr=192.168.110.110, sport=256, daddr=192.168.100.20, dport=256
IPSEC(crypto_map_check)-5: Checking crypto map outside_map 1: skipping because 5-tuple does not match ACL VPN-TRAFFIC.
IPSEC(crypto_map_check)-5: Checking crypto map outside_map 2: skipping because 5-tuple does not match ACL SALCRA-TRAFFIC.
IPSEC(crypto_map_check)-5: Checking crypto map outside_map 3: skipping because 5-tuple does not match ACL SRGASIA-TRAFFIC.
IPSEC(crypto_map_check)-3: Checking crypto map outside_map 4: matched.
Sep 20 11:35:33 [IKEv1 DEBUG]Pitcher: received a key acquire message, spi 0x0
IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=1, saddr=192.168.110.110, sport=256, daddr=192.168.100.20, dport=256
IPSEC(crypto_map_check)-5: Checking crypto map outside_map 1: skipping because 5-tuple does not match ACL VPN-TRAFFIC.
IPSEC(crypto_map_check)-5: Checking crypto map outside_map 2: skipping because 5-tuple does not match ACL SALCRA-TRAFFIC.
IPSEC(crypto_map_check)-5: Checking crypto map outside_map 3: skipping because 5-tuple does not match ACL SRGASIA-TRAFFIC.
IPSEC(crypto_map_check)-3: Checking crypto map outside_map 4: matched.
Sep 20 11:35:33 [IKEv1]IP = 1.1.1.1, IKE Initiator: New Phase 1, Intf inside, IKE Peer 1.1.1.1 local Proxy Address 192.168.110.0, remote Proxy Address 192.168.100.0, Crypto map (outside_map)
Sep 20 11:35:33 [IKEv1 DEBUG]IP = 1.1.1.1, constructing ISAKMP SA payload
Sep 20 11:35:33 [IKEv1 DEBUG]IP = 1.1.1.1, constructing NAT-Traversal VID ver 02 payload
Sep 20 11:35:33 [IKEv1 DEBUG]IP = 1.1.1.1, constructing NAT-Traversal VID ver 03 payload
Sep 20 11:35:33 [IKEv1 DEBUG]IP = 1.1.1.1, constructing NAT-Traversal VID ver RFC payload
Sep 20 11:35:33 [IKEv1 DEBUG]IP = 1.1.1.1, constructing Fragmentation VID + extended capabilities payload
Sep 20 11:35:33 [IKEv1]IP = 1.1.1.1, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 168
IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=1, saddr=192.168.110.110, sport=256, daddr=192.168.100.20, dport=256
IPSEC(crypto_map_check)-5: Checking crypto map outside_map 1: skipping because 5-tuple does not match ACL VPN-TRAFFIC.
IPSEC(crypto_map_check)-5: Checking crypto map outside_map 2: skipping because 5-tuple does not match ACL SALCRA-TRAFFIC.
IPSEC(crypto_map_check)-5: Checking crypto map outside_map 3: skipping because 5-tuple does not match ACL SRGASIA-TRAFFIC.
IPSEC(crypto_map_check)-3: Checking crypto map outside_map 4: matched.
Sep 20 11:35:41 [IKEv1]IP = 1.1.1.1, IKE_DECODE RESENDING Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 168
2, refcnt 0, tuncnt 0
Sep 20 11:50:51 [IKEv1 DEBUG]Group = 1.1.1.1, IP = 1.1.1.1, sending delete/delete with reason message
Sep 20 11:50:51 [IKEv1 DEBUG]Group = 1.1.1.1, IP = 1.1.1.1, constructing blank hash payload
Sep 20 11:50:51 [IKEv1 DEBUG]Group = 1.1.1.1, IP = 1.1.1.1, constructing IKE delete payload
Sep 20 11:50:51 [IKEv1 DEBUG]Group = 1.1.1.1, IP = 1.1.1.1, constructing qm hash payload
Sep 20 11:50:51 [IKEv1]IP = 1.1.1.1, IKE_DECODE SENDING Message (msgid=2fbccf31) with payloads : HDR + HASH (8) + DELETE (12) + NONE (0) total length : 80
A5512X-GF-FW01# Sep 20 12:15:21 [IKEv1]IP = 1.1.1.1, IKE_DECODE RESENDING Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 172
Sep 20 12:15:21 [IKEv1]IP = 1.1.1.1, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 40
Sep 20 12:15:21 [IKEv1]IP = 1.1.1.1, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 40
Sep 20 12:15:21 [IKEv1]IP = 1.1.1.1, Received an un-encrypted NO_PROPOSAL_CHOSEN notify message, dropping
Sep 20 12:15:21 [IKEv1]IP = 1.1.1.1, Information Exchange processing failed
Sep 20 12:15:29 [IKEv1]IP = 1.1.1.1, IKE_DECODE RESENDING Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 172
Sep 20 12:15:29 [IKEv1]IP = 1.1.1.1, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 40
Sep 20 12:15:29 [IKEv1]IP = 1.1.1.1, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + NOTIFY (11) + NONE (0) total length : 40
Sep 20 12:15:29 [IKEv1]IP = 1.1.1.1, Received an un-encrypted NO_PROPOSAL_CHOSEN notify message, dropping
Sep 20 12:15:29 [IKEv1]IP = 1.1.1.1, Information Exchange processing failed
A5512X-GF-FW01# show crypto isakmp sa detail
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 1.1.1.1
Type : L2L Role : initiator
Rekey : no State : MM_WAIT_MSG6
Encrypt : aes Hash : SHA
Auth : preshared Lifetime: 86400
Lifetime Remaining: 2145153861
There are no IKEv2 SAs
A5512X-GF-FW01#
we have tried multiple combination of the policy and key, still fail. any help on this?
Solved! Go to Solution.
- Labels:
-
IPSEC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2016 11:49 PM
Hi Anuar,
Can you share the remote peer config ?
It seems they are sending a wrong ID payload (may be not properly configured on the Cyberoam).
Can you configure peer-id-validate nocheck on the tunnel group and test ?
Regards,
Aditya
Please rate helpful posts and mark correct answers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2016 11:50 PM
Phase 1 (ISAKMP Policy) is not matching. Could you please check NAT-Traversal (NAT-T) enable on both end?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2016 11:57 PM
Can you point out which part does not match? I think its already matched (maybe i overlooked)
I already enable NAT-T on my firewall
!
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 3600
!
tunnel-group 1.1.1.1 type ipsec-l2l
tunnel-group 1.1.1.1 ipsec-attributes
ikev1 pre-shared-key *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2016 11:57 PM
As far as config you show these parameter are matching but phase 1 is stuck in MM_WAIT_MSG6 this is last before Phase 1 established in this state ISKMP verify PSK and NAT-T as you said PSK is same so it must be NAT-T issue. Could you check if NAT-T is enable at both end?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 12:00 AM
Ok, Im checking with the cyberoam vendor, seems like he did not turn on the NAT-T
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 01:20 AM
No luck, it still stuck on the MM_WAIT_MSG6,
we tested with different firewall (Peplink) with NAT-T enable on both end, but no luck.
we kept seeing below log on both site even though we already match the key.
Sep 20 15:37:12 [IKEv1]Group = 2.2.2.2, IP = 2.2.2.2, Received an un-encrypted PAYLOAD_MALFORMED notify message, dropping
Sep 20 15:37:12 [IKEv1]Group = 2.2.2.2, IP = 2.2.2.2, Error, peer has indicated that something is wrong with our message. This could indicate a pre-shared key mismatch.
Code log from peplink
IPsec: office-SKE/1x1 - Malformed payload, please verify the Preshared Key or other settings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 01:27 AM
what is crypto identity IP address or hostname.
crypto identity hostname or crypto identity IP ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 01:29 AM
on my site its auto
A5512X-GF-FW01(config)# show run all crypto isakmp
crypto isakmp identity auto
crypto isakmp nat-traversal 20
A5512X-GF-FW01(config)#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 01:47 AM
have you tried debug crypto isakmp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 01:48 AM
that command is not in the ASA. So i only have debug crypto ikev1 and crypto ipsec
A5512X-GF-FW01# debug crypto ?
ca Set PKI debug levels
condition Set IPSec/ISAKMP debug filters
engine Set crypto engine debug levels
ike-common Set IKE common debug levels
ikev1 Set IKEV1 debug levels
ikev2 Set IKEV2 debug levels
ipsec Set IPSec debug levels
ss-api Set Crypto Secure Socket API debug levels
vpnclient Set EasyVPN client debug levels
A5512X-GF-FW01# debug crypto
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 04:30 AM
ok so you migh use ASA 8.4 or above so you have to do debug crypto ikev1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2016 11:17 PM
Sep 30 03:57:53 [IKEv1]IP = 1.1.1.1, IKE_DECODE RECEIVED Message (msgid=cf47f14a) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 64
Sep 30 03:57:53 [IKEv1 DEBUG]Group = 1.1.1.1, IP = 1.1.1.1, processing hash payload
Sep 30 03:57:53 [IKEv1 DEBUG]Group = 1.1.1.1, IP = 1.1.1.1, processing notify payload
Sep 30 03:57:53 [IKEv1]Group = 1.1.1.1, IP = 1.1.1.1, Received non-routine Notify message: Invalid ID info (18)
As of per more testing, we kept seeing this message.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2016 11:49 PM
Hi Anuar,
Can you share the remote peer config ?
It seems they are sending a wrong ID payload (may be not properly configured on the Cyberoam).
Can you configure peer-id-validate nocheck on the tunnel group and test ?
Regards,
Aditya
Please rate helpful posts and mark correct answers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2016 07:36 PM
This did the trick, the IPSEC able to established but somehow the ASA only sending traffic but no return traffic from cyberoam firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2016 12:37 AM
Update:
We have manage to get it working.
For Cyberoam configruation, you must configure the local and remote ID, unless you will be seeing the Received non-routine Notify message: Invalid ID info (18) error.
Also, the behavior of the cyberoam (im not sure if this is an issue from Cyberoam site or it just how Cyberoam handle IPSEC) is that you need to initiate the traffic from Cyberoam site of LAN as well to ensure the traffic able to pass through the tunnel. Again, Im not sure if this is how cyberoam works or handles IPSEC tunnel or its a bug from their site.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

