- Cisco Community
- Technology and Support
- Security
- VPN
- Re: IR809 redundant VPN failover to cellular issues
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IR809 redundant VPN failover to cellular issues
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2017 09:06 AM - edited 03-12-2019 04:30 AM
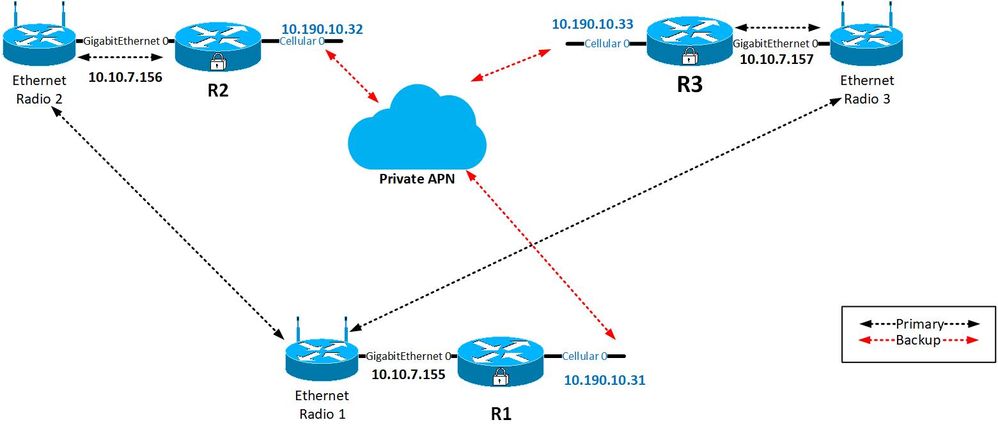
I have 3 IR809 routers that will use directly connected ethernet radios with cellular interface as backup. R1 is the primary (CTU) with R2 & R3 each needing to independantly tunnel back to R1. I have tried ip sla, and while that in itself works, the tunnels themselves are not functioning how I need them.
For example, if R2's ethernet radio goes down and R2 switches to cellular, I can only get a functioning tunnel if R1's ethernet interface is shut. What I would need is for R1 to accept connections on its cellular from R2 while also connecting via ethernet for R1. Below is the config for R1 abbreviated some;
crypto isakmp policy 1 encr aes authentication pre-share group 14 crypto isakmp key TestKey address 10.10.7.156 crypto isakmp key TestKey address 10.10.7.157 crypto isakmp key TestKey address 10.190.190.32 crypto isakmp key TestKey address 10.190.190.33 ! crypto ipsec transform-set T1 esp-aes esp-sha-hmac mode tunnel ! crypto ipsec profile IPSEC set transform-set T1 ! interface Tunnel0 ip address 172.10.1.1 255.255.255.248 tunnel source 10.10.7.155 tunnel destination 10.10.7.156 ! interface Tunnel1 ip address 172.20.1.1 255.255.255.248 tunnel source 10.190.10.31 tunnel destination 10.170.190.32 ! interface Tunnel2 ip address 172.30.1.1 255.255.255.248 tunnel source 10.10.7.155 tunnel destination 10.10.7.157 ! interface Tunnel3 ip address 172.40.1.1 255.255.255.248 tunnel source 10.190.10.31 tunnel destination 10.190.10.33 ! interface GigabitEthernet0 ip address 10.10.7.155 255.255.255.0 ! interface Cellular0 no ip address ! interface Dialer1 ip address negotiated ip nat outside ! router eigrp 1 network 10.10.7.0 0.0.0.255 network 10.20.1.0 0.0.0.7 network 10.170.190.0 0.0.0.255 ! ip route 10.20.2.0 255.255.255.248 Tunnel0 track 10 ip route 10.20.3.0 255.255.255.248 Tunnel2 track 11 ip route 10.20.2.0 255.255.255.248 Tunnel1 20 ip route 10.20.3.0 255.255.255.248 Tunnel3 20 ip route 192.168.101.0 255.255.255.224 10.10.7.254 ! ip sla 1 icmp-echo 10.10.7.156 source-ip 10.10.7.155 ip sla schedule 1 life forever start-time now ip sla 2 icmp-echo 10.10.7.157 source-ip 10.10.7.155 ip sla schedule 2 life forever start-time now dialer-list 1 protocol ip permit ! access-list 1 permit any
Basically I can get tunnel functioning if I disconnect or shut down BOTH R1 & R2's eth interfaces, then both will communicate via cellular. The above config is my last attempt thinkign to use 2nd ip sla which did not work as expected.
- Labels:
-
Other VPN Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2017 12:07 AM
If you are using crypto map to encrypt the GRE traffic then please migrate to DVTI that will accept the connection from any interface. Here is an example:
HTH
Moh,
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: