- Cisco Community
- Technology and Support
- Security
- VPN
- L2TP over IPsec
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
L2TP over IPsec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2019 03:42 AM - edited 02-21-2020 09:41 PM
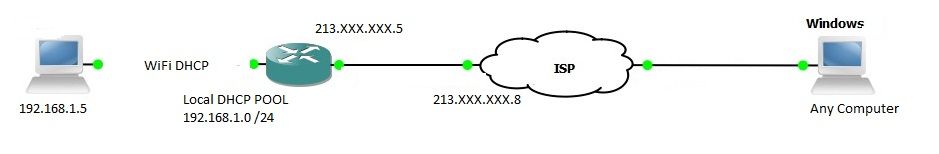
So I was configuring VPN L2TP over IPsec on my cisco router (1111-8p) but I have few problems. First I connect to tunnel. Get for example IP like 10.1.1.3 - but still cant ping anything. I cant even ping10.1.1.3 from router.
My goal is to be able to ping (how access for NAS server) every device from 192.168.1.0 /24 network. I have static ip on my router from ISP. How can i fix this? I realy need this VPN. Here is my ip route table and config:
Gateway of last resort is 213.X.X.8 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 213.X.X.X
10.0.0.0/32 is subnetted, 3 subnets
C 10.1.1.1 is directly connected, Virtual-Access2.1
C 10.1.1.30 is directly connected, Loopback1
S 10.1.101.32 [254/0] via 213.X.X.X, GigabitEthernet0/0/1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Vlan1
L 192.168.1.1/32 is directly connected, Vlan1
192.168.2.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.2.0/24 is directly connected, Loopback0
L 192.168.2.1/32 is directly connected, Loopback0
C 213.X.X.0/23 is directly connected, GigabitEthernet0/0/1
213.X.X.0/32 is subnetted, 1 subnets
L 213.X.X.8 is directly connected, GigabitEthernet0/0/1
Building configuration...
Current configuration : 6547 bytes
!
! Last configuration change at 10:12:52 UTC Mon Jul 15 2019 by me
!
version 16.8
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
no platform punt-keepalive disable-kernel-core
!
hostname Cielimowo
!
boot-start-marker
boot-end-marker
!
!
!
aaa new-model
!
!
aaa authentication ppp VPDN_AUTH local
!
!
!
!
!
!
aaa session-id common
!
ip name-server XXX
ip domain name cielimowo.com
!
ip dhcp pool network
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
domain-name network.com
dns-server 213.X.x.x 213.X.x.x
!
!
!
!
!
!
!
!
!
!
subscriber templating
!
!
!
!
!
!
!
multilink bundle-name authenticated
vpdn enable
!
vpdn-group L2TP
! Default L2TP VPDN group
accept-dialin
protocol l2tp
virtual-template 1
no l2tp tunnel authentication
!
!
flow record defaultApplicationTraffic
match ipv4 protocol
match ipv4 source address
match ipv4 destination address
match transport source-port
match transport destination-port
collect transport tcp flags
collect counter packets long
collect timestamp sys-uptime first
collect timestamp sys-uptime last
!
!
flow exporter export_Gi0_0_1_213.X.x.x_192.168.1.7
destination 192.168.1.7
source GigabitEthernet0/0/1
transport udp 2055
!
!
flow monitor datXGi0_0_1_d55ce208_c0XX0107
exporter export_Gi0_0_1_213.X.X.X_192.168.1.7
record defaultApplicationTraffic
!
!
!
!
crypto pki trustpoint TP-self-signed-2XXXXX784358
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-2XXXX4358
revocation-check none
rsakeypair TP-self-signed-2236784358
!
!
crypto pki certificate chain TP-self-signed-2XXXX4358
certificate self-signed 01
30820330
quit
!
crypto pki certificate pool
cabundle nvram:ios_core.p7b
!
license udi pid C1111-8PLTEEA sn FCZ231XX2TP
no license smart enable
!
diagnostic bootup level minimal
!
spanning-tree extend system-id
!
!
username admin privilege 15 password 0 XXX
username XXX privilege 15 secret 5 $1$TcK8$EiG4bZ6gFw9o82vsYuEaN1
username XXXVPN privilege 15 password 0 XXX
!
redundancy
mode none
!
!
!
!
controller Cellular 0/2/0
lte modem link-recovery disable
!
!
vlan internal allocation policy ascending
!
!
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key Flatron address 0.0.0.0
!
!
crypto ipsec transform-set L2TP-Set2 esp-3des esp-sha-hmac
mode transport
!
!
!
crypto dynamic-map dyn-map 10
set nat demux
set transform-set L2TP-Set2
!
!
crypto map outside_map 65535 ipsec-isakmp dynamic dyn-map
!
!
!
!
!
!
!
!
interface Loopback0
ip address 192.168.2.1 255.255.255.0
ip nat inside
ip virtual-reassembly
!
interface Loopback1
ip address 10.1.1.30 255.255.255.255
!
interface GigabitEthernet0/0/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/0/1
ip flow monitor datXGi0_0_1_d55ce208_c0a80107 input
ip flow monitor datXGi0_0_1_d55ce208_c0a80107 output
ip dhcp relay information option server-id-override
ip dhcp server use subscriber-id client-id
ip address dhcp
ip nat outside
negotiation auto
crypto map outside_map
ip virtual-reassembly
!
interface GigabitEthernet0/1/0
!
interface GigabitEthernet0/1/1
!
interface GigabitEthernet0/1/2
!
interface GigabitEthernet0/1/3
!
interface GigabitEthernet0/1/4
!
interface GigabitEthernet0/1/5
!
interface GigabitEthernet0/1/6
!
interface GigabitEthernet0/1/7
!
interface Cellular0/2/0
ip address negotiated
ipv6 enable
!
interface Cellular0/2/1
no ip address
shutdown
!
interface Virtual-Template1
ip unnumbered Loopback1
peer default ip address pool l2tp-pool
ppp authentication ms-chap-v2 VPDN_AUTH
!
interface Vlan1
ip address pool network
ip nat inside
!
ip local pool l2tp-pool 10.1.1.1 10.1.1.29
ip nat inside source list 1 interface GigabitEthernet0/0/1 overload
ip nat inside source list NAT interface GigabitEthernet0/0/1 overload
ip forward-protocol nd
ip http server
ip http authentication local
ip http secure-server
ip http secure-port 6514
ip http timeout-policy idle 60 life 86400 requests 10000
ip route 0.0.0.0 0.0.0.0 213.X.X.X
!
!
ip access-list extended NAT
permit ip 192.168.1.0 0.0.0.255 any
deny ip 192.168.2.0 0.0.0.255 10.1.1.0 0.0.0.255
permit ip 192.168.2.0 0.0.0.255 any
!
access-list 1 permit 192.168.1.0 0.0.0.255
!
!
!
!
!
!
control-plane
!
!
line con 0
transport input none
stopbits 1
line vty 0 4
exec-timeout 5 0
transport input ssh
line vty 5 97
exec-timeout 5 0
transport input ssh
!
wsma agent exec
!
wsma agent config
!
wsma agent filesys
!
wsma agent notify
!
!
end
- Labels:
-
AnyConnect
-
IPSEC
-
Other VPN Topics
-
Remote Access
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide