- Cisco Community
- Technology and Support
- Security
- VPN
- Re: NAM & Cisco ISE EAP-Chaining
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NAM & Cisco ISE EAP-Chaining
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2019 08:04 AM
Hello,
I was wondering if someone may be able to help me with something.
As it stands we have Windows 10 machines connecting to ISE 2.3. The idea is to have EAP-Chaining with NAM Module to check Machine Certificate (TLS) and user credentials via MSCHAP.
I've ran into a problem where the machine account does not authenticate but the user account does. (I have a Authz policy that allows partial access to the network for this)
11001 Received RADIUS Access-Request
11017 RADIUS created a new session
15049 Evaluating Policy Group
15008 Evaluating Service Selection Policy
15048 Queried PIP - Normalised Radius.RadiusFlowT
11507 Extracted EAP-Response/Identity
12100 Prepared EAP-Request proposing EAP-FAST w
12625 Valid EAP-Key-Name attribute received
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12102 Extracted EAP-Response containing EAP-FAS
accepting EAP-FAST as negotiated
12800 Extracted first TLS record; TLS handshake star
12175 Received Tunnel PAC
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12801 Prepared TLS ChangeCipherSpec message
12802 Prepared TLS Finished message
12105 Prepared EAP-Request with another EAP-FAS
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAS
12804 Extracted TLS Finished message
12816 TLS handshake succeeded
12132 EAP-FAST built PAC-based tunnel for purpose
12209 Starting EAP chaining
12218 Selected identity type 'User'
12125 EAP-FAST inner method started
11521 Prepared EAP-Request/Identity for inner EAP m
12105 Prepared EAP-Request with another EAP-FAS
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAS
12212 Identity type provided by client is equal to reque
11522 Extracted EAP-Response/Identity for inner EAP
11806 Prepared EAP-Request for inner method propo
challenge
12105 Prepared EAP-Request with another EAP-FAS
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAS
11808 Extracted EAP-Response containing EAP-MSC
inner method and accepting EAP-MSCHAP as
15041 Evaluating Identity Policy
15048 Queried PIP - CERTIFICATE.Issuer - Common
15048 Queried PIP - Network Access.EapAuthenticati
15013 Selected Identity Source - ISE_AD
24430 Authenticating user against Active Directory - IS
24325 Resolving identity - *MASKED*
24313 Search for matching accounts at join point - *MASKED*
24319 Single matching account found in forest - *MASKED*
24323 Identity resolution detected single matching acc
24343 RPC Logon request succeeded - *MASKED*
24402 User authentication against Active Directory su
22037 Authentication Passed
11824 EAP-MSCHAP authentication attempt passed
12105 Prepared EAP-Request with another EAP-FAS
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAS
11810 Extracted EAP-Response for inner method con
response
11814 Inner EAP-MSCHAP authentication succeeded
11519 Prepared EAP-Success for inner EAP method
12128 EAP-FAST inner method finished successfully
12966 Sent EAP Intermediate Result TLV indicating s
12105 Prepared EAP-Request with another EAP-FAS
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAS
12126 EAP-FAST cryptobinding verification passed
12202 Approved EAP-FAST client Authorization PAC
12219 Selected identity type 'Machine'
12125 EAP-FAST inner method started
11521 Prepared EAP-Request/Identity for inner EAP m
12105 Prepared EAP-Request with another EAP-FAS
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAS
12213 Identity type provided by client is not equal to re
12216 Identity type provided by client was already use
12967 Sent EAP Intermediate Result TLV indicating fa
12105 Prepared EAP-Request with another EAP-FAS
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAS
24715 ISE has not confirmed locally previous success
user in Active Directory
15036 Evaluating Authorization Policy
15048 Queried PIP - Radius.User-Name
15016 Selected Authorization Profile - Monitor-Mode
12964 Sent EAP Result TLV indicating success
12171 Successfully finished EAP-FAST user authoriza
12105 Prepared EAP-Request with another EAP-FAS
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAS
12106 EAP-FAST authentication phase finished succe
11503 Prepared EAP-Success
24432 Looking up user in Active Directory - ISE_AD
24355 LDAP fetch succeeded - *MASKED*
24416 User's Groups retrieval from Active Directory su
11002 Returned RADIUS Access-Accept
Upon further investigation, it would appear that NAM cannot find my certificate. I have double checked and the certificate is imported to the Trusted Root Certificate Authorities on the PC.
I have checked the DART logs from the NAM agent and it would appear that The issue is that AnyConnect is not parsing the correct certificate stores on the PC.
Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3600]: Auth[*-Wired:machine-auth]: Client certificate list has been cleared
2036: : Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3600]: Auth[*-Wired:machine-auth]: Select certificate and set identity, cred_source: 6
2037: : Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3600]: Auth[*-Wired:machine-auth]: Create list of all certs in machine store for selection
2038: Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3600]: Enumerating certificate store 'machine personal'.
2039: : Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3600]: Found 0 certificates available in the store 'machine personal'.
2040: : Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3600]: Auth[*-Wired:machine-auth]: Filter certs in machine store to select best cert(s) for authentication
2041: : Mar 04 2019 14:44:59.764 +0000: %NAM-3-ERROR_MSG: %[tid=3600]: There are no client certificates available
2042:: Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3600]: Auth[*-Wired:user-auth]: Received Identity Type TLV: old type User; proposed Machine; new type User
2043: Mar 04 2019 14:44:59.764 +0000: %NAM-6-INFO_MSG: %[tid=3600]: EAP: Identity Type sent as User
2044: Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3600]: EAP: Identity type sent: sync=107
2045: Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3600]: EAP: credential request 107: state transition: PENDING -> RESPONDED
2046: Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3600]: EAP: credential request completed, response sent: sync=107
2047: Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3600]: EAP: credential request 107: state transition: RESPONDED -> COMPLETED
2048: Mar 04 2019 14:44:59.764 +0000: %NAM-7-DEBUG_MSG: %[tid=3652]: EAP-CB: credential requested: sync=108, session-id=1, handle=00A2CA9C, type=AC_CRED_IDENTITY
I have double checked a few things with this. The NAM Module configuration file is configured to trust any certificate within the OS Store.
Has anyone seen this issue before where Anyconnect only looks within the personal store. I don't have any other AC modules installed Just core and NAM.
Any advice would be much appreciated.
Thanks,
Ry
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2019 08:24 AM
Upon further investigation, it would appear that NAM cannot find my certificate. I have double checked and the certificate is imported to the Trusted Root Certificate Authorities on the PC.
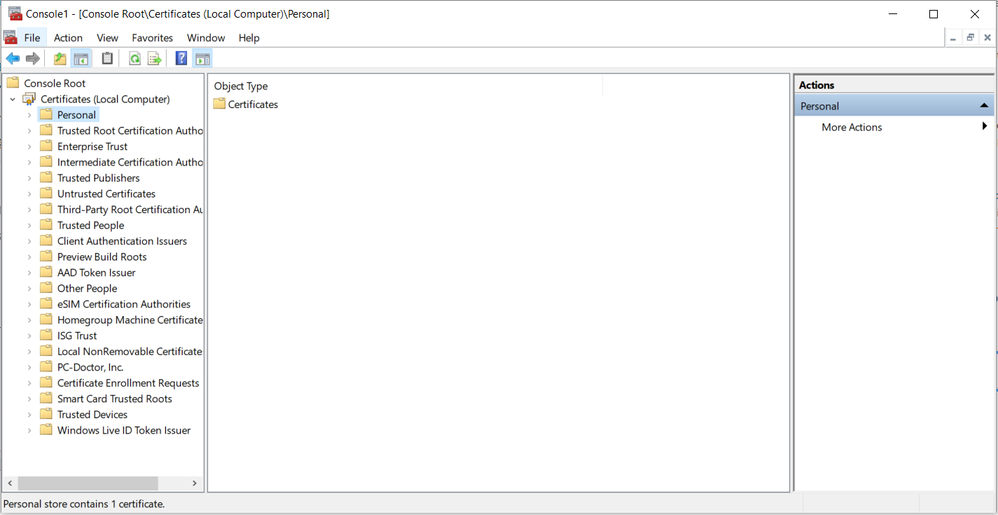
The machine certificate should NOT be in the Trusted cert store of the machine. It should be under the Personal store under Machine account:
Trusted cert stores are meant for only CA certs, no private keys are associated with those certs. This must by why AC does not see them. Did you manually install the machine certs under the Trusted Root store?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2019 08:32 AM
Hi Rahul,
Thanks for the quick response, I'm not using individual machine certificates.
I'm matching my policy based on a certificate with the issuer common name. Therefore, I want to match this to my domain root cert that is held within the trusted root certificate authority.
Thanks,
Ryan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2019 09:17 AM
Ryan,
The Machine Auth bit still needs some kind of credentials to send back to complete authentication. This can be either machine password or a machine certificate. When you send the machine cert (issued to machine by CA) and CA cert chain, the ISE should be able to validate that it has indeed been issued by a CA that it trusts - hence completing the authentication. If you only send the CA cert, it breaks the chain of trust. ISE no longer knows who has send the client auth data back. The assumption here is that only the client (machine) has the private keys and that since a known CA has issued the cert, ISE can trust this TLS transaction.
In short, client has to send the machine cert and CA cert (which the OS chains together automatically) to complete authentication. AC NAM only needs to search for your machine cert in the Personal store.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: