- Cisco Community
- Technology and Support
- Security
- VPN
- Nat isse with Gre over Ipsec
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-01-2013 06:33 AM - edited 02-21-2020 06:35 PM
Hi guys!
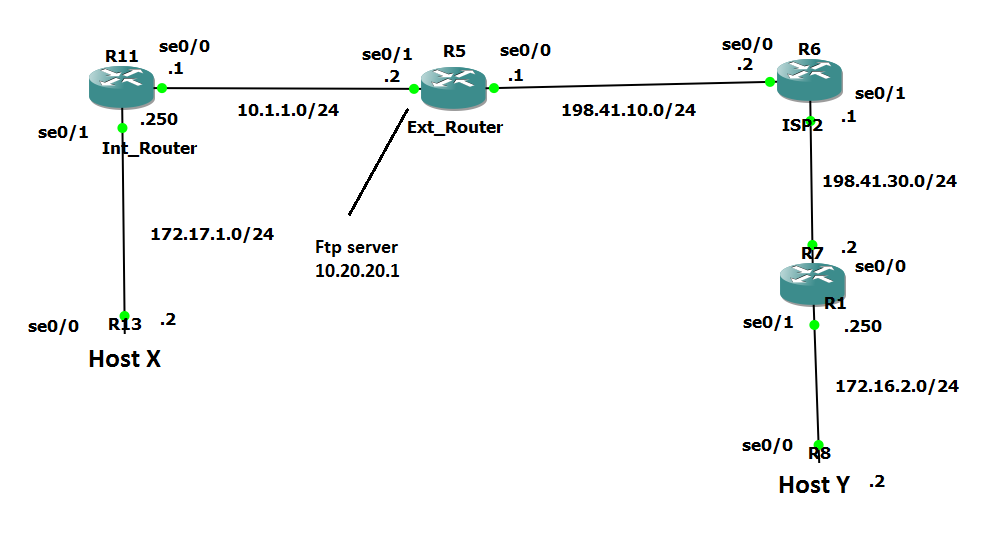
I have a little problem with my configuration.
I would like to reach the host Y from X through a VPN tunnel.
My configuration is working fine, until i add this static nat entry:
-ip nat inside source static 10.20.20.1 198.41.10.1
In that case the endpoints of the tunnel can't reach each other (172.16.13.1 <-> 172.16.13.2).
The Ext_Router does the Nat translation and the tunnel is between Ext_Router and R7.
What will be the problem?
The configuration files are attached.
Solved! Go to Solution.
- Labels:
-
IPSEC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-01-2013 08:14 AM
Hi,
Let me first say that my dealings with GRE + IPsec have been pretty slim.
But what it looks to me from looking at the configurations and NAT is that you have following configurations with regards to NAT on R5/Ext_Router
- PAT translation configuration for 2 LAN networks that use the Serial 0/0 IP address as a PAT address
- A Static NAT for one LAN host that ALSO uses the Serial0/0 IP address for translation.
If the NAT operation on router is anything like the Cisco PIX or ASA. The Static NAT will override the PAT configuration (overload) completely and therefore no user belonging to the source networks of ACL 1 wont be able to use the NAT and therefore traffic wont work for them but should probably work for the Static NAT host 10.20.20.1?
Could this be the problem? Could another 198.41.10.x IP Be used for the Static NAT?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-01-2013 10:02 AM
Dear Attila Javor
you have to create two access list one for NAT and second for VPN.
then
inte s0/0
ip nat outside
int s0/1
ip nat inside
match address 101
VPN access list apply in int s0/0 suppose access list 101 for VPN
access-list 101 permit ip 192.168.1.0 0.0.0.255 11.11.11.11 (Remote user) 255.255.255.255
access-list 101 permit ip 192.168.1.0 0.0.0.255 22.22.22.22(Remote user) 255.255.255.255
In NAT access list you have deny your remote ip. if u deny your remote ip then only data will travel via tunnel otherwise it will travel over Internet.
hope this is help you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-01-2013 08:14 AM
Hi,
Let me first say that my dealings with GRE + IPsec have been pretty slim.
But what it looks to me from looking at the configurations and NAT is that you have following configurations with regards to NAT on R5/Ext_Router
- PAT translation configuration for 2 LAN networks that use the Serial 0/0 IP address as a PAT address
- A Static NAT for one LAN host that ALSO uses the Serial0/0 IP address for translation.
If the NAT operation on router is anything like the Cisco PIX or ASA. The Static NAT will override the PAT configuration (overload) completely and therefore no user belonging to the source networks of ACL 1 wont be able to use the NAT and therefore traffic wont work for them but should probably work for the Static NAT host 10.20.20.1?
Could this be the problem? Could another 198.41.10.x IP Be used for the Static NAT?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 11:45 PM - edited 02-14-2018 11:46 PM
Can we use IPSEC over GRE With PAT on Cisco 4451 Router?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-01-2013 10:02 AM
Dear Attila Javor
you have to create two access list one for NAT and second for VPN.
then
inte s0/0
ip nat outside
int s0/1
ip nat inside
match address 101
VPN access list apply in int s0/0 suppose access list 101 for VPN
access-list 101 permit ip 192.168.1.0 0.0.0.255 11.11.11.11 (Remote user) 255.255.255.255
access-list 101 permit ip 192.168.1.0 0.0.0.255 22.22.22.22(Remote user) 255.255.255.255
In NAT access list you have deny your remote ip. if u deny your remote ip then only data will travel via tunnel otherwise it will travel over Internet.
hope this is help you
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

