- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Point Remote VPN users to different internal ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2021 01:09 PM
Hello there,
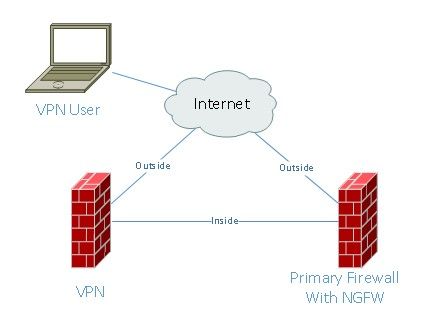
I have the below basic network diagram. We have two ASA firewalls, both newer 5500 models. One has Firepower Module and is used for our internet browsing for the company. The other is simply used as an AnyConnect VPN Concentrator without Firepower.
We have a few sites that connect via a site-to-site vpn as well to that VPN firewall using a simple router. The vpn acl on the remote devices said to point all traffic (including internet) over the VPN to our head-end for filtering, so no local internet browsing occurs at the vpn user\device level. This is for those remote router sites only, not AnyConnect (they leverage split-tunnel).
Currently those users' internet access is going back out our VPN firewall because that's the default gateway. How can we make remote VPN users that are tunneling all traffic over the VPN send their internet traffic over to the Primary Firewall that has the NGFW capabilities without landing them on the primary firewall for VPN?
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Remote Access
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2021 01:15 PM
You can define a separate default route for tunneled traffic along with the standard default route.
route <if_name> 0.0.0.0 0.0.0.0 <gateway_ip> tunneled
So essentially the VPN users traffic would be sent to another next hop, which would then route that traffic out the other firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2021 01:11 PM
After I posted this the light bulb went off of a route map with the remote router internal LAN as the source, to change the default gateway to the LAN address..but I'll see if anyone else has any other ideas.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2021 01:15 PM
You can define a separate default route for tunneled traffic along with the standard default route.
route <if_name> 0.0.0.0 0.0.0.0 <gateway_ip> tunneled
So essentially the VPN users traffic would be sent to another next hop, which would then route that traffic out the other firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2021 01:16 PM
Thanks Rob, I knew the answer would be simplistic!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2021 01:31 PM
Well I guess we have that setup already, but I'm not seeing traffic in our Primary firewall for the same destination IP as I'm seeing on the VPN firewall.
I see there are no NAT rules on the VPN ASA, but in theory we wouldn't need to NAT them as we have static routes on our core switches for the remote VPN sites.
Thoughts?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2021 12:16 AM
@Travis-Fleming can you run packet-tracer from the VPN firewall to confirm the traffic takes the correct path?
Does the Primary FW know to reach the RAVPN IP pool via it's inside interface connected to the core switch?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2021 06:22 AM
Thanks Rob this lead me to the right answer. The primary FW did not have a route to this particular subnet out it's inside interface. After making that route I started to see their internet traffic on the primary FW like I think I should.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide