- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Possibilities for VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Possibilities for VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2010 02:14 AM
Ok as a continuation of the previous topic.
Im looking for a VPN solution to handle remote support, our current solutions are not good enough anymore and need a lot of management.
Ill start with the requirements of the solution and then 2 network drawings that outline possible solutions
Requirements:
- NO VPN server or VPN device at customer side.
- Engineers need direct access to our network and devices at the customer side.
The VPN tunnel between the client-server or hub-spoke can be permanent. The ideas are based on CISCO software/hardware.
The drawings:
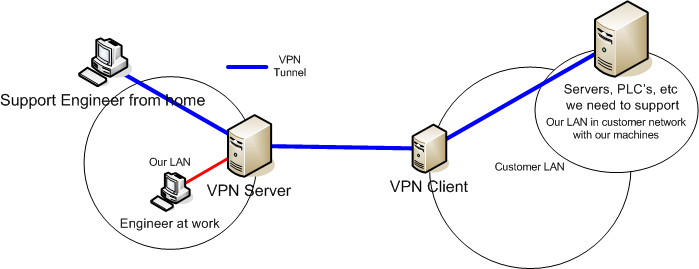
This is one possibility. As said most important is that the engineer can connect to the VPN and then directly access our network at the customer site. I dont know if that is possible with routing etc.We should not have access to the rest of the LAN.
Another possibility would be using DMVPN in the following setup:
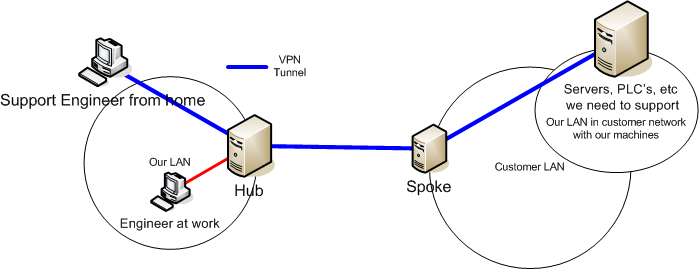
Is this possible? and can the spoke somehow route the addresses correctly so we can access the machines there?
The engineer should be able to for example type in address 192.168.14.13 and reach the server with that address at the customer site.
I know this is all very sketchy but I hope it clarifies the ideas a bit more, if not ill hear it im sure...
Thanks for your time!
- Labels:
-
Remote Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2010 04:02 PM
There are two problems
1) DMVPN requires NHRP to work and the only version available is Cisco NHRP and OpenNHRP for Linux
2) What happen if client block ESP, and AH? You will not able to establish an VPN connection from your server to your Hub site
I think the solution you are want is something similar to Webex Remote Access. Please check out the following link for more info.
http://www.webex.com/product-overview/support-center/remote-access.html
HTH,
jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2010 11:09 PM
Im not sure i understand the problems you listed.
If with 1 you mean that devices etc need to be Cisco, thats not a problem. If need we can place a small router in the clients network to serve as the spoke. As long as it is not a server or anything with a separate internet line it is a viable solution.
As for point 2. Besides the obvious "why would they block it", what connection are you talking about: The spoke to the hub?
The idea is that the VPN is from the hub to the spoke, the engineer sets up a connection to the hub (comparable to a second spoke perhaps?) and then makes a spoke-spoke connection. The spoke, which in this case would be a router at the customers network would route the traffic over the VPN to the right server/client/plc behind it in the network place with our devices.
Im not sure if Webex is a viable solution, but id prefer to stick with DMVPN or similar if at all possible before moving to a software solution.
Thanks for the help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2010 06:38 AM
I've worked for many organizations that don't allow IPSec VPN going out from their production network. If you want to put a server that needs IPSec, it will be in the DMZ. So my statement is still valid. It is depends on your client's security policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2010 02:56 AM
Requirements:
- NO VPN server or VPN device at customer side.
Jerry is correct. This is not the cisco approach. Look at logmein or similar software solutions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2010 03:01 AM
I think that there is a misunderstanding there. With no server or vpn device i mean they dont want a device there that acts like a VPN server as in accepting VPN connections from clients. Outgoing is fine, ie. the client is at the customer making outbound connection to server.
That make sense?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2010 03:36 AM
What you describe is not the Cisco VPN approach, rather the MS approach or many other software producers.
The advantage is evident, you do not depend on any PC for networking.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2010 03:45 AM
Hmmm im probably a bit of a pain, but would u mind explaining that statement?
The cisco solution doesnt depend on a PC? cause aint that what im trying to do?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2010 06:35 AM
The Cisco approach for DMVPN is all configurations are done on a router. There isn't any PC/Server involved.
However, if you want a PC/Server approach, you can you Webex Remote Access.
Regards,
jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2010 11:58 AM
Many customers that I have worked with have used DMVPN as the VPN for remote control of devices at remote sites. In your diagram DMVPN would
be used between the Hub and Spoke routers as you have shown. The Support engineer could connect into your main site again using DMVPN, though I would use a separate DMVPN cloud for this, if you place a small router at the support engineers home. The support engineer could also connect to the main site using EzVPN directly from his PC (say he is not at home). Routing would be used to route between the support engineer (EzVPN or DMVPN) to the Customer site (DMVPN). In your drawing you show that there is a VPN between your servers and the DMVPN spoke router. Usually when I have had customers set this up the LAN that they need to access is directly connected to the DMVPN spoke router so we just use routing to route packets between the servers to the spokes router and then through DMVPN to the hub router, etc. If you need traffic separation at the spoke router (your traffic, versus your customers traffic) then we can probably use VRFs (VRF-lite) to accomplish this.
The advantage of using DMVPN for the VPN connection between your main site and your customer sites is that the network you build looks like an extension of your own network (again could be separated off using VRFs). So you can run any IP application over the links and access multiple devices, without having multiple VPN tunnels per customer site.
Hope this helps,
Mike.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: