Hi, We are trying to implement Azure SAML SSO on our Firepower 1010. We are using ASA 9.19.1 and Secure client 5.0.02075. When we try the login via Azure by clicking the "Test this applicaton" the login works and there are no errors in the logs. The ...
VPN
- Mark all as New
- Mark all as Read
- Float this item to the top
- Subscribe
- Bookmark
- Subscribe to RSS Feed
- Threaded format
- Linear Format
- Sort by Topic Start Date
The content you are looking for has been archived. View related content below.
-
AAA
(3) -
Access Control Server (ACS)
(1) -
AnyConnect
(6,517) -
Appliances
(1) -
ASA
(1) -
ASR 1000 Series
(1) -
ATAs and Gateways and Accessories
(1) -
Buying Recommendation
(34) -
Catalyst Switch
(1) -
Cisco Adaptive Security Appliance (ASA)
(28) -
Cisco Bugs
(1) -
Cisco Cafe
(14) -
Cisco Cloud Services Router
(2) -
Cisco DNA
(2) -
Cisco DNA Automation
(1) -
Cisco Firepower Device Manager (FDM)
(2) -
Cisco Firepower Management Center (FMC)
(4) -
Cisco Firepower Threat Defense (FTD)
(6) -
Cisco Software
(6) -
Cisco Start India
(1) -
Clientless SSL
(266) -
Cloud Security
(1) -
Community Feedback Forum
(15) -
Community Ideas
(9) -
Compliance and Posture
(2) -
Conferencing
(1) -
Connectivity Issues and VPN
(1) -
Device Admin
(1) -
DMVPN
(733) -
Duo
(63) -
Emergency Responder
(1) -
Enterprise Agreement
(1) -
Firewalls
(1) -
FlexVPN
(169) -
General
(1) -
GetVPN
(135) -
Identity Services Engine (ISE)
(5) -
IPSEC
(4,294) -
ISR 1000 Series
(2) -
ISR 4000 Series
(4) -
LAN Switching
(2) -
License
(1) -
Network Management
(21) -
New Document Idea
(1) -
NGFW Firewalls
(3) -
Optical Networking
(1) -
Other Cisco DNA
(1) -
Other Collaboration Topics
(3) -
Other Community Feedback
(1) -
Other IP Telephony
(1) -
Other NAC
(1) -
Other Network
(13) -
Other Network Security Topics
(8) -
Other Networking
(6) -
Other Routers
(8) -
Other Routing
(13) -
Other Security Topics
(2) -
Other Switches
(2) -
Other Switching
(1) -
Other VPN Topics
(13,560) -
Other Wireless and Mobility Subjects
(1) -
Other Wireless Topics
(2) -
Physical Security
(3) -
Remote Access
(5,845) -
Routers
(1) -
Routing
(2) -
Routing Protocols
(12) -
RV340
(1) -
Security Certifications
(1) -
Security Management
(3) -
Small Business Routers
(2) -
Small Business Switches
(1) -
Storage Networking
(1) -
Umbrella
(26) -
VPN
(22,043) -
VPN and AnyConnect
(1) -
VPN y AnyConnect
(4) -
WAN
(2) -
Web Security
(2) -
Wired
(1) -
Wireless Network Management
(3) -
Wireless Security
(5) -
Wireless Security and Network Management
(1)
- « Previous
- Next »
Forum Posts
I have multiple AnyConnect connection profiles for various remote users that provide access to different internal networks. The authentication method needs to be certificate only, but there doesn't seem to be a way to prevent an issued certificate ho...
The following message is displayed when the connection button is pressed. Please tell me how to solve it. Certificate Validation Failure AnyConnect VPI version 5.0.04232 Secure Client UI version 5.0.00889 Certificate Expiration Date 2025/4/3
Hello, Good Day, Seeking help from you guys, currently I`m configuring Site to Site VPN connection from Cisco Firepower 2130 to AWS. I`m using the download configuration from AWS which is Cisco ASA 5500 9.X file, and I`m using Cisco Firepower 2130 ...
Hi, Has anyone had issues where you are running FTD with AnyConnect (secureclient) with Posture (DAP) enabled and some computers are sending the attribute endpoint.am=xxx and others aren't? I have several devices not sending the anti-malware attrib...
I am using Cisco AnyConnect Secure Mobility Client version Version 4.10.07062 on my Windows 10 system to connect to our office VPN. From past few days I am experiencing a weird issue where my Internet speed is reduced by 96-97% after connecting to VP...
Hello everyone and thanks in advance for your support,one of my clients asked me to reuse an ASA 5506 so as to be able to allow some users to connect remotely via Anyconnect.However, the request requires the use of the tunnellall option for obvious s...
Hi, I have one issue with IPSec tunnel Lan-to-Lan between ASA 5525x (v9.8) and ASA FPR 2110 (v9.16). My Tunnel is up but ping between each client was not successful. Both peer status sh cry isakmp sa in "MM_ACTIVE".I ran packet-tracer icmp between pe...
Hi, there! I want to use two VPNs at once.So initially, I am connected with NordVPN and then I am trying to connect to Anyconnect VPN.But it doesn't work.If I turn off NordVPN and try to connect with Anyconnect, it works well.Is there any way to turn...
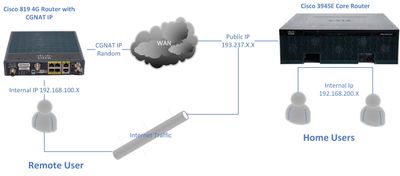
Dear All Members, I am trying to set up the 819 4G Router as a VPN Client (Router) with the purpose of full internet tunnelling.The goal here is the Remote users behind the 4G Router when he travels overseas and connect to any 4g network and when he ...
We have clients receiving a "PKCS12 (PFX) without a supplied password" error while connecting to RAVPN using Cisco Secure Client (5.1.2.42). The headend device is FTD 3130.The full error is "There was an erro during initialization: PKCS12 (PFX) witho...
I'd like to know if it's possible to give a remote client a certificate that they can import to use for SSL VPN authentication instead of having them generate the request and giving it to us to sign and hand back to them. Using an enrollment server i...
I have a weird situation I need to connect to two sepaate VPN (not at the same time).One of these requires Cisco Secure Client 5.x the second works with Any Connect 4.x.I have Cisco Secure Client 5.x installed, if i try connecting to the VPN that use...
Hello,I have an IKEv2 Site-to-Site IPSec tunnel (VTI with static routing) between ASA firewall and 2 stateless HA routers configured with HSRP (IPSec end point is HSRP VIP hosted on the HSRP active router).Despite the fact it is not stateful (not sup...
I have this issue on both a Windows 10 computer and a MACbook Pro running Sonoma 14.4.1. The problem initially appeared on teh Windows box, my secondary device, but just appeared on my Macbook. WE run ISE 3.1 and FTD 7.0.6 I tried to connect Sec...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
| Subject | Author | Posted |
|---|---|---|
| 04-23-2024 01:22 AM | ||
| 04-22-2024 03:28 PM | ||
| 04-19-2024 08:08 AM | ||
| 04-18-2024 10:47 AM | ||
| 04-17-2024 06:49 AM |
| User | Count |
|---|---|
| 6 | |
| 4 | |
| 1 | |
| 1 | |
| 1 |





