- Cisco Community
- Technology and Support
- Security
- VPN
- Remote client can't access LAN server via VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2013 12:05 AM
Hi friends,
I am a new palyer in ASA.
My company is small. We need remote client access server in LAN via VPN.
I have an ASA5510 with version 7.0 . I have configured remote access VPN and it can establish tunnel successfully. But I can't access server.
VPN client is version 5.0.07.0290 . Encrypted packets have increasing but Decrypted packets is 0 in statistics of VPN client, after I connected successfully.
In ASA side, I show crypto ipsec sa, just have decrypted packets increase.
Who can help me?
Thanks a lot.
The configuration in follow:
ASA Version 7.0(7)
!
hostname VPNhost
names
dns-guard
!
interface Ethernet0/0
nameif outside
security-level 10
ip address 221.122.96.51 255.255.255.240
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.42.199 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
shutdown
no nameif
no security-level
no ip address
management-only
!
ftp mode passive
dns domain-lookup inside
access-list PAT_acl extended permit ip 192.168.42.0 255.255.255.0 any
access-list allow_PING extended permit icmp any any inactive
access-list Internet extended permit ip host 221.122.96.51 any inactive
access-list VPN extended permit ip 192.168.42.0 255.255.255.0 192.168.43.0 255.255.255.0
access-list VPN extended permit ip 192.168.43.0 255.255.255.0 192.168.42.0 255.255.255.0
access-list CAPTURE extended permit ip host 192.168.43.10 host 192.168.42.251
access-list CAPTURE extended permit ip host 192.168.42.251 host 192.168.43.10
pager lines 24
mtu outside 1500
mtu inside 1500
ip local pool testpool 192.168.43.10-192.168.43.20arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list VPN
nat (inside) 1 access-list PAT_acl
route outside 0.0.0.0 0.0.0.0 221.122.96.49 10
username testuser password 123
aaa authentication ssh console LOCAL
aaa local authentication attempts max-fail 3no sysopt connection permit-ipsec
crypto ipsec transform-set FirstSet esp-des esp-md5-hmac
crypto dynamic-map dyn1 1 set transform-set FirstSet
crypto dynamic-map dyn1 1 set reverse-route
crypto map mymap 1 ipsec-isakmp dynamic dyn1
crypto map mymap interface outside
isakmp enable outside
isakmp policy 1 authentication pre-share
isakmp policy 1 encryption des
isakmp policy 1 hash md5
isakmp policy 1 group 2
isakmp policy 1 lifetime 86400
isakmp nat-traversal 3600
tunnel-group testgroup type ipsec-ra
tunnel-group testgroup general-attributes
address-pool testpool
tunnel-group testgroup ipsec-attributes
pre-shared-key *
telnet timeout 5ssh timeout 10
console timeout 0: end
Topology as follow:
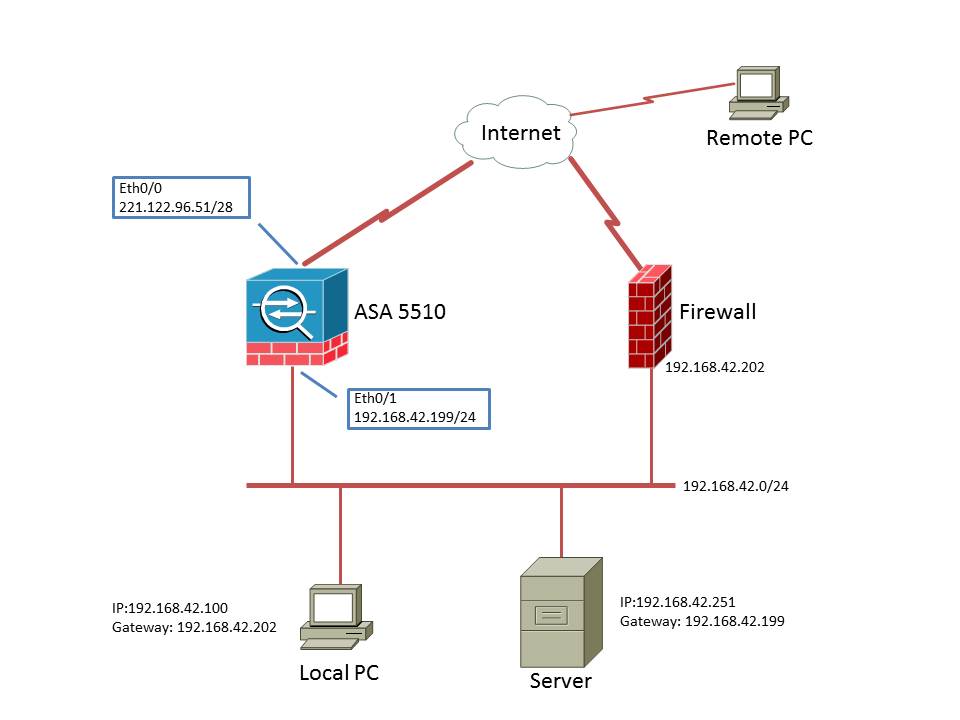
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2013 08:42 AM
Hi,
Configure split tunneling for the VPN.
Create the access list that defines the network behind the ASA.
ciscoasa(config)#access-list Split_Tunnel_List remark The corporate network behind the ASA. ciscoasa(config)#access-list Split_Tunnel_List standard permit 10.0.1.0 255.255.255.0
Enter Group Policy configuration mode for the policy that you wish to modify.
ciscoasa(config)#group-policy hillvalleyvpn attributes ciscoasa(config-group-policy)#
Specify the split tunnel policy. In this case the policy is tunnelspecified.
ciscoasa(config-group-policy)#split-tunnel-policy tunnelspecified
Specify the split tunnel access list. In this case, the list is Split_Tunnel_List.
ciscoasa(config-group-policy)#split-tunnel-network-list value Split_Tunnel_List
Issue this command:
ciscoasa(config)#tunnel-group hillvalleyvpn general-attributes
Associate the group policy with the tunnel group
ciscoasa(config-tunnel-ipsec)# default-group-policy hillvalleyvpn
Exit the two configuration modes.
ciscoasa(config-group-policy)#exit ciscoasa(config)#exit ciscoasa#
Save the configuration to non-volatile RAM (NVRAM) and press Enter when prompted to specify the source filename.
Regards,
Abhishek Purohit
CCIE-S- 35269
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2013 09:15 AM
ASA configuration update:
ASA Version 7.0(7)
!
hostname VPNhost
interface Ethernet0/0
nameif outside
security-level 10
ip address 221.122.96.51 255.255.255.240
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.42.199 255.255.255.0
ftp mode passive
dns domain-lookup
inside access-list PAT_acl extended permit ip 192.168.42.0 255.255.255.0 any
access-list VPN extended permit ip 192.168.42.0 255.255.255.0 192.168.43.0 255.255.255.0
access-list VPN extended permit ip 192.168.43.0 255.255.255.0 192.168.42.0 255.255.255.0
access-list CAPTURE extended permit ip host 192.168.43.10 host 192.168.42.251
access-list CAPTURE extended permit ip host 192.168.42.251 host 192.168.43.10
pager lines 24
mtu outside 1500
mtu inside 1500
ip local pool testpool 192.168.43.10-192.168.43.20
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list VPN
nat (inside) 1 access-list PAT_acl
route outside 0.0.0.0 0.0.0.0 221.122.96.49 10
username testuser password 123
aaa authentication ssh console LOCAL
aaa local authentication attempts max-fail 3
no sysopt connection permit-ipsec
crypto ipsec transform-set FirstSet esp-des esp-md5-hmac
crypto dynamic-map dyn1 1 set transform-set FirstSet
crypto dynamic-map dyn1 1 set reverse-route
crypto map mymap 1 ipsec-isakmp dynamic dyn1
crypto map mymap interface outside isakmp
enable outside isakmp policy 1 authentication pre-share
isakmp policy 1 encryption des isakmp policy 1 hash md5
isakmp policy 1 group 2 isakmp policy 1 lifetime 86400
isakmp nat-traversal 3600
tunnel-group testgroup type ipsec-ra
tunnel-group testgroup general-attributes
address-pool testpool
tunnel-group testgroup ipsec-attributes
pre-shared-key *
telnet timeout 5
ssh timeout 10
console timeout 0
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2013 10:05 AM
Hi Wind,
I see couple of extra configs which doesn't help.
You can remove them.
1) no access-list VPN extended permit ip 192.168.43.0 255.255.255.0 192.168.42.0 255.255.255.0
2) Enable sysopt VPN: sysopt connection permit-ipsec
3) RRI shouold be used when you have Dynamic routing :
no crypto dynamic-map dyn1 1 set reverse-route
Now coming to the issue:
Is this happening only with the Server or you are unable to reach anything in the LAN?
If, this is happening only with the LAN server, then check the LAN server's settings (firewall settings) that it should allow the all networks and not only 192.168.42.0.
On the ASA, check the encaps.
Client Encaps are Decaps on ASA, and vice versa.
If, you are not able to reach anything, then take captures on the inside interface.
ACL would be something like this.
Assigned IP from the POOL to the 192.168.42.0/24 network and vice-versa.
Apply the capture on the inside interface. and check if you are able to see traffic leaving the ASA to the internal network as well as traffic entering from internal n/w to the assigned IP.
Also, you can do a test of packet-tracer.
connect the client. check the ip assigned from the pool.
then run the command.
packet-tracer in in icmp 192.168.42.199 8 0
Share the output os the same.
I hope this helps.
Regards,
Abhishek Purohit
CCIE-S- 35269
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2013 04:25 AM
Hi Abhishek,
Thanks for your reply.
I remove PAT and set address pool in 192.168.42.0/24, then the VPN was working.
Now, I have a question:
My client can't access Internet when the VPN is established. I want to access Internet through VPN. How do I configure it?
If I want to access Internet not through VPN, how do I configure it?
Could you give me some direction and some documents?
By the way, the packet-tracer is appear in ASA 7.2 or above. Mine is 7.0 .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2013 08:42 AM
Hi,
Configure split tunneling for the VPN.
Create the access list that defines the network behind the ASA.
ciscoasa(config)#access-list Split_Tunnel_List remark The corporate network behind the ASA. ciscoasa(config)#access-list Split_Tunnel_List standard permit 10.0.1.0 255.255.255.0
Enter Group Policy configuration mode for the policy that you wish to modify.
ciscoasa(config)#group-policy hillvalleyvpn attributes ciscoasa(config-group-policy)#
Specify the split tunnel policy. In this case the policy is tunnelspecified.
ciscoasa(config-group-policy)#split-tunnel-policy tunnelspecified
Specify the split tunnel access list. In this case, the list is Split_Tunnel_List.
ciscoasa(config-group-policy)#split-tunnel-network-list value Split_Tunnel_List
Issue this command:
ciscoasa(config)#tunnel-group hillvalleyvpn general-attributes
Associate the group policy with the tunnel group
ciscoasa(config-tunnel-ipsec)# default-group-policy hillvalleyvpn
Exit the two configuration modes.
ciscoasa(config-group-policy)#exit ciscoasa(config)#exit ciscoasa#
Save the configuration to non-volatile RAM (NVRAM) and press Enter when prompted to specify the source filename.
Regards,
Abhishek Purohit
CCIE-S- 35269
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2013 06:30 PM
Hi Abhishek,
Thank you for your help!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide