- Cisco Community
- Technology and Support
- Security
- VPN
- Site-2-Site redundant VPN Tunnel from remote office to Head Offi
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2012 05:47 AM
I have firewall ASA 5510 in EDN-UK1 main office (internet connection with Virgin) and having 7 remote firewalls in other countries.
EDN_UK1 firewall has VPN connection with each of 7 Remote firewalls.
Now we are going to install one more EDN-UK2 firewall in main office (internet connection with BT) to use as standby for all remote 7 offices VPNs. In case EDN-Uk1 fails the EDN-UK2 start serving the remote VPNs without interruption.
I have studied Active/standby failover and GRE over IPsec tunnel with OSP but I can’t find what would be the correct configurations to implement this task.
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2012 07:02 AM
Hi Mahmood,
Could you please tell me if the firewall that you are going to install will have a different public Ip address or will it be in Active/Standby failover.
If it will have a different IP address, then on all the remote sides you will have to specify the old as well as the new IP address.
On remote firewalls are ASA then you need to specify,
crypto map outside_map 10 set peer 1.1.1.1 2.2.2.2
When this command will be there, the remote firewalls will try to bring tunnel up with 1.1.1.1 and if they fail then they will try with the ip 2.2.2.2
If you are using the device in active failover then you don't have to make any changes. The configuration gets replicated as soon as the device sync with each other and as soon as the active ASA goes down, the standby ASA takes over it and does not allow the tunnel to go down.
Regarding the GRE tunnel, ASA is a firewall and does not support GRE over IPSec feature.
Let me know if this helps.
Thanks,
Vishnu Sharma
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2012 06:38 AM
Hi Mahmood,
Please find answers to your questions:
1. Active failover mean ( in your reply) Active/Active failover
Active/Standby Failover is different from Active/Active failover. In Active/Standby failover, we have two devices in sync with each other out of which, 1 will be in active mode and the other will be in standby mode. If the active ASA goes down for any reason, the standby firewall will become active and will take the ownership. In Active/Active failover, we create contexts on the ASA (each firewall has two contexts) and both firewalls are active at the same time with 1 contect in active mode and another context in standby mode. Active/Active failover will not be of any help to you because VPN does not work with Active/Active failover.
2. Can I configure two different firewalls (single firewalls) in Active/Active
Already answered above. VPN does not work with Active/Active failover.
3) Is there any need to change in VPN configurations of existing Head office Firewalls OLD ASA 1.1.1.1
No change is required on Old firewall. The changes will only be on remote side.
4) Should I have to make same configirations on NEW ASA 2.2.2.2 or when both devices sync NEW ASA will take all the configurations from OLD ASA by itself.
When you configure NEW ASA with a different public Ip address (not active/standby failover), the NEW ASA will have the same configuration what you had on the OLD ASA.
5) Is there any need to run dynamic routing protocols like OSPF on remote ASA's and Head Office Old and New ASA's
You dont have to run any routing protocol on the remote side. On the host end you can use IP SLA monitoring on the switch behind the ASA to change the routes accordingly i.e. it will point to OLD ASA for the return traffic and if OLD ASA goes down, it will change the route to NEW ASA so that the traffic is sent to the remote locations.
Please let me know if this answers your question.
Thanks,
Vishnu Sharma
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2012 07:02 AM
Hi Mahmood,
Could you please tell me if the firewall that you are going to install will have a different public Ip address or will it be in Active/Standby failover.
If it will have a different IP address, then on all the remote sides you will have to specify the old as well as the new IP address.
On remote firewalls are ASA then you need to specify,
crypto map outside_map 10 set peer 1.1.1.1 2.2.2.2
When this command will be there, the remote firewalls will try to bring tunnel up with 1.1.1.1 and if they fail then they will try with the ip 2.2.2.2
If you are using the device in active failover then you don't have to make any changes. The configuration gets replicated as soon as the device sync with each other and as soon as the active ASA goes down, the standby ASA takes over it and does not allow the tunnel to go down.
Regarding the GRE tunnel, ASA is a firewall and does not support GRE over IPSec feature.
Let me know if this helps.
Thanks,
Vishnu Sharma
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2012 01:00 AM
Hi Sharma,
Your Understandings are correct, Both the firewalls would have different public IP addresses because both have internet connection from two different ISPs. I have few questions if you are kind enough to reply them please.
1. Active failover mean ( in your reply) Active/Active failover
2. Can I configure two different firewalls (single firewalls) in Active/Active
3) Is there any need to change in VPN configurations of existing Head office Firewalls OLD ASA 1.1.1.1
4) Should I have to make same configirations on NEW ASA 2.2.2.2 or when both devices sync NEW ASA will take all the configurations from OLD ASA by itself.
5) Is there any need to run dynamic routing protocols like OSPF on remote ASA's and Head Office Old and New ASA's
Thanks
Mahmood
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2012 06:38 AM
Hi Mahmood,
Please find answers to your questions:
1. Active failover mean ( in your reply) Active/Active failover
Active/Standby Failover is different from Active/Active failover. In Active/Standby failover, we have two devices in sync with each other out of which, 1 will be in active mode and the other will be in standby mode. If the active ASA goes down for any reason, the standby firewall will become active and will take the ownership. In Active/Active failover, we create contexts on the ASA (each firewall has two contexts) and both firewalls are active at the same time with 1 contect in active mode and another context in standby mode. Active/Active failover will not be of any help to you because VPN does not work with Active/Active failover.
2. Can I configure two different firewalls (single firewalls) in Active/Active
Already answered above. VPN does not work with Active/Active failover.
3) Is there any need to change in VPN configurations of existing Head office Firewalls OLD ASA 1.1.1.1
No change is required on Old firewall. The changes will only be on remote side.
4) Should I have to make same configirations on NEW ASA 2.2.2.2 or when both devices sync NEW ASA will take all the configurations from OLD ASA by itself.
When you configure NEW ASA with a different public Ip address (not active/standby failover), the NEW ASA will have the same configuration what you had on the OLD ASA.
5) Is there any need to run dynamic routing protocols like OSPF on remote ASA's and Head Office Old and New ASA's
You dont have to run any routing protocol on the remote side. On the host end you can use IP SLA monitoring on the switch behind the ASA to change the routes accordingly i.e. it will point to OLD ASA for the return traffic and if OLD ASA goes down, it will change the route to NEW ASA so that the traffic is sent to the remote locations.
Please let me know if this answers your question.
Thanks,
Vishnu Sharma
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2012 12:59 AM
Hi
I am still working on this project and it required several changes in the our network before implementation.
I am worried about one point.
We have two internet lines from two different ISPs so the Public IP range is different. Would it be possible to run both firewalls in Active/Standby mode while the IP subnet of Outside interfaces at both firewalls will be different
ASA1 ASA2
Outside 202.83.x.x/27 94.x.x.x/27 different subnet
inside 10.x.x.1 10.x.x.2 same subnet (can ping)
DMZ 192.x.x.1 192.x.x.2 same subnet (but they cannot ping each other)
Failover 172.x.x.1 172.x.x.2 same subnet (can ping)
If I configure only statefull failover interface as primary and secondary at both firewalls would it be sufficient to work as Active/standby and pass VPN and other crdentials between active to standby
I mean does the below config are enough and will work or not because for outside interface and DMZ I cant do anything
Primary Unit config
failover
failover lan unit primary
failover lan interface failover Ethernet0/3
failover replication http
failover link failover Ethernet0/3
failover interface ip failover 10.100.0.100 255.255.255.0 standby 10.100.0.101
Secondary Unit config
failover
failover lan unit secondary
failover lan interface failover Ethernet0/3
failover replication http
failover link failover Ethernet0/3
failover interface ip failover 10.100.0.100 255.255.255.0 standby 10.100.0.101
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2012 06:07 AM
No, you can't run the firewall in Active/Standby failover mode when the IP Address of the Outside is different. It doesn't work that way. They need to be in the same subnet, and only 1 ip address works, meaning that the IP Address follows the active ASA.
Example:
ASA1 (primary): 202.83.x.1 (active)
ASA2 (Secondary): 202.83.x.2 (standby)
From the above example, only 202.83.x.1 will be used to pass traffic, and 202.83.x.2 is only used for the firewall to check on the interface status by performing keepalive/polling. When ASA2 becomes the active ASA, it will have 202.83.x.1 as its ip address.
This way will make configuring default gateway easy as you only need to configure 1 ip address as a default gateway or next hop route.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2012 04:50 AM
What he probably means is you can configure the ASA in active/standby failover mode first, then the standby ASA will already have the configuration. You can save it, and then chnage the configuration with the new public IP Address on the outside interface. And yes, you are right, they would not be in Active/Standby mode after you change it accordingly. You would also need to remove all the failover configuration lines.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2013 04:24 AM
Hi
I have tried that scenario.
I have configured SLA on cisco layer three switch which is changing the default gateway for all LAN traffic to firewall A to B and then when A is backup then B-A
I configured the remote office VPN with the following settings
crypto map outside_map0 1 set peer 34.x.x.x.x 202.y.y.y.y
tunnel-group 34.x.x.x.x type ipsec-l2l
tunnel-group 34.x.x.x.x general-attributes
default-group-policy GroupPolicy1
tunnel-group 34.x.x.x.x ipsec-attributes
pre-shared-key * ******
tunnel-group 202.y.y.y.y type ipsec-l2l
tunnel-group 202.y.y.y.y general-attributes
default-group-policy GroupPolicy1
tunnel-group 202.y.y.y.y ipsec-attributes
pre-shared-key ******
My SLA configuration is working fine.
ip sla 1
icmp-echo 194.168.4.100
timeout 500
frequency 3
ip sla schedule 1 start-time now life forever
track 1 ip sla 1 reachability
ip route 0.0.0.0 0.0.0.0 10.0.0.252 track 1
ip route 0.0.0.0 0.0.0.0 10.0.0.251 10 <
ip route 194.168.4.100 255.255.255.255 10.0.0.252
I have created VPN on firewall A and B. both firewalls have same configurations apart from their public and private IP addresses.
THE PROBLEM IS THAT THE REMOTE OFFICE CRETAES VPN SESSION WITH BOTH asa A AND B
AND BOTH VPN SATYS UP EITHER LAN TRIFFIC IS PASSING THROUGH ASA A OR BACKUP ASA B
When both VPNs are up from my side all traffic is going through firewall A and only going through firewall B when firewall A is down.
.
But remote office ASA is confused for the selection of ASA A or B
When ASA A is active and traffic is passing through ASA A the remote office LAN should send their all VPN traffic to main office towards the ASA A but its not happening.
From remote office they can’t access file server, DNS and any other application while from core switch the LAN traffic has default route via ASA A.
Please help me to find out the way for this problem
Thanks
Mahmood
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2013 02:30 AM
Your topology is not so clear to me, but i think the problem is somehow related to assymmetric routing, where traffic to the central site goes through the ASA B and return traffic goes throug the ASA A wich drops it due to inspection policies. Have tried to disable tunnel to site B and see what will happen if only tunnel to ASA A is active?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2013 03:23 AM
Hi Andrew
Please see the 1st two posts to better understand the topology
When the tunnel between remote office and site B is disabled and only up between remote office and site A then there is no problem and traffic passes through without any problem.
The problem is that when tunnel at remote office is up for both site A and site B then remote office has to enabled tunnels with different public IP addresses but same Local Area parameters. If am routing all my traffic from head office to remote office via site A via SLA monitor but still the communication fails because of two enabled tunnels. Specially from remote to head office all applications like outlook, dns, file servers failed
Thanks
Mahmood
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2013 09:18 AM
I think you should enable dynamic routing between sites, so channel selection will depend on it. In that case you can avoid asymmectic routing and the issues that come with that, plus it'll be more scalable.
Try to run OSPF with unicast neighbors over IPSEC tunnel and properly adjust metric.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2013 12:52 AM
Hi Andrew
Thanks a lot for your reply. Actually I have ASA firewall on both sides and they dont support GRE tuneels over IPSEC.
I think I cant run OSPF with unicast neighbors over IPSEC tunnel.
Is there any solution to define the preferred route for VPN at remote side when both the tunnels are up?
Thanks again
Mahmood
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2013 06:16 AM
Hi All
I have completed and finished this task successfully.
I have configured IP SLA on backup firewall as well.
Backup firewall tracks the external interface of primary firewall by ICMP and keeps firewall down when primary is up and if primary is down the backup firewall comes up with right routing table and same time my layer three switch forwards all the default traffic to backup ASA.
Everything on VPN is working fine.
Now I am looking redundancy for TMG server. I have added one more network card in TMG server and have attached that network card to backup firewall. The DMZ zone at backup firewall is different than primary firewall.
I am looking for similar solution like IP SLA for windows server if there is any.
Anyway I am thankfull to Vishnu, Jennifer and andrew who helped me to complete this task, specially to Vishnu.
Thanks
Mahmood
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2019 10:00 AM
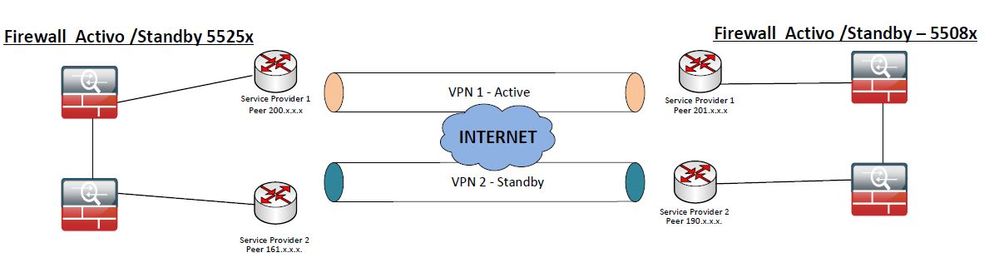
Hi Experts
I have this scenario, we currently have a VPN Site to Site with some ASA 5508x already active with my Service Provider 1 and I want to configure the contingency with another Peer (New Public IP) with my Service Provider 2,
There is some additional configuration that you have to put in the ASA.
I have only declared the following statement adding the 2nd public ip from the other end of the ASA, here the configuration:
crypto map outside_map 1 match address outside_cryptomap_3
crypto map outside_map 1 set pfs group5
crypto map outside_map 1 set peer 201.x.x.x 190.x.x.x
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA
crypto map outside_map 1 set ikev2 pre-shared-key *****
crypto map outside_map 1 set security-association lifetime seconds 28800
crypto map outside_map 1 set df-bit set-df
Our test will be to disconnect the internet from 1 end and see if it commutes with the other internet 2 link or is there something that I need to configure in the ASA?
Thank you in advance for your help if you have faced a simulated scenario
Regards.
Carlos P.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2020 02:27 AM
Hi Carlos,
I am having exactly the same scenario to implement. Did you get your configurations sorted and your setup is working fine?
Regards,
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: