- Cisco Community
- Technology and Support
- Security
- VPN
- Site-to-Site between ASA 5505 VPN problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2022 06:27 AM
Hello,
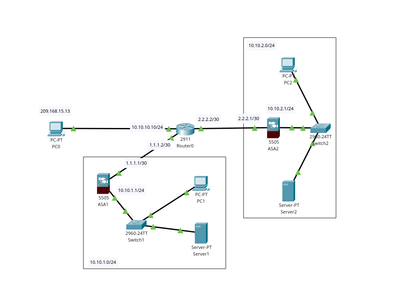
I am a student and I have a project to create an all-to-all VPN connection between two ASA devices.
I'm not very familiar with network configurations, but I followed a few steps and managed to get here. Where am I going wrong and why don't I have - There are no IKEv1 SAs
These are the configurations of both devices:
ASA1#show running-config
ASA Version 8.4(2)
!
hostname ASA1
names
!
interface Ethernet0/0
!
interface Ethernet0/1
switchport access vlan 2
!
interface Vlan1
nameif inside
security-level 100
ip address 10.10.1.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 1.1.1.1 255.255.255.252
!
object network local-net
subnet 10.10.1.0 255.255.255.0
object network remote-net
subnet 10.10.2.0 255.255.255.0
!
route outside 0.0.0.0 0.0.0.0 1.1.1.2 1
!
access-list LAN-TRAFFIC extended permit ip 10.10.1.0 255.255.255.0 10.10.2.0 255.255.255.0
!
telnet timeout 5
ssh timeout 5
!
crypto ipsec ikev1 transform-set L2L esp-aes 256 esp-sha-hmac
!
crypto map L2L 1 match address LAN-TRAFFIC
crypto map L2L 1 set peer 2.2.2.1
crypto map L2L 1 set ikev1 transform-set L2L
crypto map L2L interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
encr aes
authentication pre-share
group 2
!
tunnel-group 2.2.2.1 type ipsec-l2l
tunnel-group 2.2.2.1 ipsec-attributes
ikev1 pre-shared-key pass123
!
ASA2#show running-config
interface Vlan1
nameif inside
security-level 100
ip address 10.10.2.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 2.2.2.1 255.255.255.0
!
object network local-net
subnet 10.10.2.0 255.255.255.0
object network remote-net
subnet 10.10.1.0 255.255.255.0
!
route outside 0.0.0.0 0.0.0.0 2.2.2.2 1
!
access-list LAN-TRAFFIC extended permit ip 10.10.2.0 255.255.255.0 10.10.1.0 255.255.255.0
!
telnet timeout 5
ssh timeout 5
!
!
crypto ipsec ikev1 transform-set L2L esp-aes 256 esp-sha-hmac
!
crypto map L2L 1 match address LAN-TRAFFIC
crypto map L2L 1 set peer 1.1.1.1
crypto map L2L 1 set ikev1 transform-set L2L
crypto map L2L interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
encr aes
authentication pre-share
group 2
!
tunnel-group 1.1.1.1 type ipsec-l2l
tunnel-group 1.1.1.1 ipsec-attributes
ikev1 pre-shared-key pass123
!
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2022 09:02 AM
ping 10.10.2.1 source 10.10.1.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2022 07:08 AM
initiate traffic and then check IPSec tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2022 07:31 AM
i'm sorry for the stupid question but how to do it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2022 09:02 AM
ping 10.10.2.1 source 10.10.1.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2022 11:53 AM
When I tried it gave a result, but why is there no ipsec sa?
ASA1#show crypto isakmp sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 2.2.2.1
Type : L2L Role : Initiator
Rekey : no State : MM_NO_STATE
There are no IKEv2 SAs
ASA1#show crypto ipsec sa
There are no ipsec sas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2022 10:39 PM
Firstly, the two most important commands when troubleshooting any vpn tunnel on a cisco device:
1. "show crypto isakmp sa" or "sh cry isa sa"
2. "show crypto ipsec sa" or "sh cry ips sa"
The first command will show the state of the tunnel. For an tunnel to be perfectly up and passing traffic like it is supposed to, you should see a status "MM_ACTIVE" on an ASA and "QM_IDLE" on a router. The second command will show you the tunnel stats in detail showing clearly the number of packets encapsulated and decapsulated through the vpn tunnel. These numbers should be more or less equal.
(Henceforth throughout the document, I shall be referring to the above mentioned commands as command 1 and command 2 respectively)
Tips to Remember
1. Upon issuing command 1, if you see the status as "MM_NO_STATE" on an ASA or "MM_WAIT_MSG2" on a router, then you would want to -
a. Check the ISAKMP policies that are configured on both the ends of the tunnel to check if the parameters are matched. By ISAKMP policies, I am referring to the parameters that have been configured after issuing the command "crypto isakmp policy <policy-number>" within the sub-prompt. Out of the multiple policies that may have been configured at both ends, at least one policy must match completely with the peer policy, else you would see this status message. Make sure that you match the parameter "group" as well else you will still see this status message.
b. Check if you are able to ping the peer IP address. Also check with your ISP providers on both ends to see if they have blocked UDP port 500 at their end. Blocking of port 500 can also result in this status message.
2. Upon issuing command 1, if you see the status as "MM_WAIT_MSG4" on a router, you would want to check the value of the "group" parameter set under the "crypto isakmp policy <policy-number>" for the policy that is supposed to match on both ends of the tunnel. This parameter has to match on both ends, just like all the other parameters.
3. Upon issuing command 1, if you see the status as "MM_KEY_EXCH" on an ASA or "MM_WAIT_MSG6" on a router, then you would want to ensure that the pre-shared-key you are using on both ends is exactly matched, character by character.
4. Upon issuing command 1, if you see the status "MM_ACTIVE" on an ASA or "QM_IDLE" on a router, issue command 2. If for some reason the traffic is not passing through the vpn tunnel successfully, then you might want to check the IPSEC transform set that has been set under the crypto map for both ends. Here too, the parameters must match at all times.
5. Upon checking to see if traffic is passing successfully, if you find that traffic is not successfully passing through the tunnel, you would also need to check if the traffic for that vpn tunnel has been either exempted from the NAT process by using the "nat (interface-name) 0" command or if the crypto acl has the natted IP of the subnet and not the real IP.
Must DO's
1. Always enable ISAKMP on the interface that you want to terminate the VPN tunnel on. You can do this by issuing the command "crypto isakmp enable <interface-name>".
2. Always apply the crypto map to the same interface that has the isakmp enabled. The command "crypto map <map-name> interface <interface-name>" should do the trick!
3. Ensure that there is only one crypto map applied to a particular interface.
4. Ensure that the crypto acl's or access-list that are used to match traffic to go through the vpn tunnel do not overlap with other access-lists applied to tunnels going to other peers. This can cause a major traffic passage issue although the status of the tunnel will show as "MM_ACTIVE" or "QM_IDLE".
This may help you,
Rachel Gomez
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: