- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Site to Site VPN failover problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2018 07:09 PM - edited 03-12-2019 05:12 AM
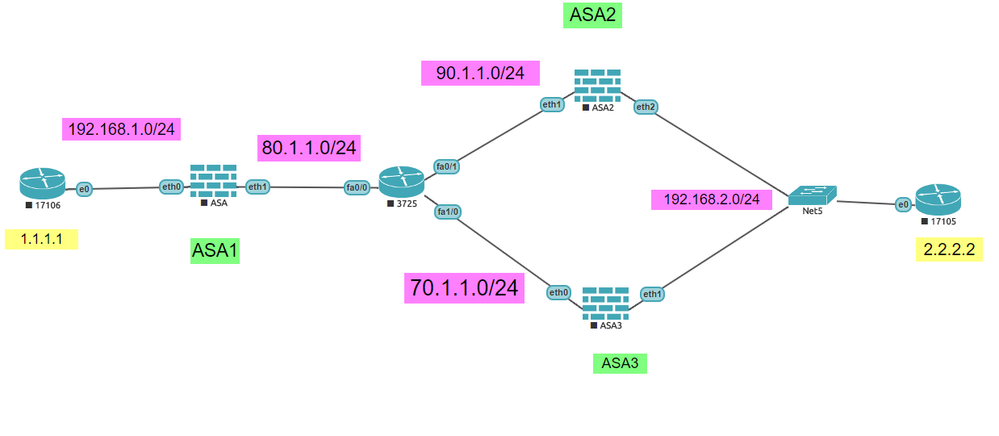
ASA1 is configured in multimode. ASA1 has a single crypto map entry with two peer IPs. IPsec tunnel is working fine with each peer. When we remove primary IP tunnel formed with secondary peer IP.
But the problem is when we put route for primary peer towards inside. Tunnel keeps working. On tunnel we notice encryption but no decryption . In outside capture we can see DPD is being exchanged that is why tunnel is not tear down and tunnel remain up and not switching to secondary tunnel.
ASA software version is 9.7(1)4 <context>
I unable to understand why this is happening and how can we fix it.
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2018 11:32 AM
I able to resolve the issue
Inside route was not working. So, I put a route towards outside with next hop 4.4.4.4
and I got the result
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2018 07:38 PM
Hi
Not sure I get your issue.
When traffic goes on inside zone behind asa1 through tunnel between asa2 and asa1, nothing works, is that right?
Can you share your config or outputs? (Acls, crypto config...)
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2018 08:49 PM
Note: - VPN is configured in context mode
trying to ping 2.2.2.2 from 1.1.1.1
config is working if I use only one peer IP (any out of two)
crypto map CRYMAP 18 match address abc_Crypto
crypto map CRYMAP 18 set pfs
crypto map CRYMAP 18 set peer 90.1.1.1 90.1.1.1
crypto map CRYMAP 18 set ikev1 transform-set ESP_AES256_SHA
crypto map CRYMAP 18 set security-association lifetime seconds 28800
crypto map CRYMAP 18 set security-association lifetime kilobytes 4608000
In order to check the failover from one peer to another. i am changing the route for 90.1.1.1 towards inside
Ping stop . but ipsec keep working. in ipsec i can see #pkts encaps increasing but no #pkts decaps:. Tunnel do not failover to secondary peer
log when I change the route to test the failover
IP = 90.1.1.1, Received Cisco Unity client VID
%ASA-7-715047: IP = 90.1.1.1, processing VID payload
%ASA-7-715049: IP = 90.1.1.1, Received xauth V6 VID
%ASA-7-715047: IP = 90.1.1.1, processing VID payload
%ASA-7-715038: IP = 90.1.1.1, Processing VPN3000/ASA spoofing IOS Vendor ID payload (version: 1.0.0, capabilities: 20000001)
%ASA-7-715047: IP = 90.1.1.1, processing VID payload
%ASA-7-715049: IP = 90.1.1.1, Received Altiga/Cisco VPN3000/Cisco ASA GW VID
%ASA-7-715047: IP = 90.1.1.1, processing NAT-Discovery payload
%ASA-7-713906: IP = 90.1.1.1, computing NAT Discovery hash
%ASA-7-715047: IP = 90.1.1.1, processing NAT-Discovery payload
%ASA-7-713906: IP = 90.1.1.1, computing NAT Discovery hash
%ASA-7-713906: IP = 90.1.1.1, Connection landed on tunnel_group 90.1.1.1
%ASA-7-713906: Group = 90.1.1.1, IP = 90.1.1.1, Generating keys for Initiator...
%ASA-7-715046: Group = 90.1.1.1, IP = 90.1.1.1, constructing ID payload
%ASA-7-715046: Group = 90.1.1.1, IP = 90.1.1.1, constructing hash payload
%ASA-7-715076: Group = 90.1.1.1, IP = 90.1.1.1, Computing hash for ISAKMP
%ASA-7-715034: IP = 90.1.1.1, Constructing IOS keep alive payload: proposal=32767/32767 sec.
%ASA-7-715046: Group = 90.1.1.1, IP = 90.1.1.1, constructing dpd vid payload
%ASA-7-713236: IP = 90.1.1.1, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + ID (5) + HASH (8) + IOS KEEPALIVE (128) + VENDOR (13) + NONE (0) total length : 96
%ASA-6-713172: Group = 90.1.1.1, IP = 90.1.1.1, Automatic NAT Detection Status: Remote end is NOT behind a NAT device This end is NOT behind a NAT device
%ASA-7-713906: IKE Receiver: Packet received on 185.193.35.60:500 from 90.1.1.1:500
%ASA-7-713236: IP = 90.1.1.1, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + ID (5) + HASH (8) + IOS KEEPALIVE (128) + VENDOR (13) + NONE (0) total length : 96
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing ID payload
%ASA-7-714011: Group = 90.1.1.1, IP = 90.1.1.1, ID_IPV4_ADDR ID received
90.1.1.1
%ASA-7-715046: Group = 90.1.1.1, IP = 90.1.1.1, constructing blank hash payload
%ASA-7-715046: Group = 90.1.1.1, IP = 90.1.1.1, constructing IPSec SA payload
%ASA-7-715046: Group = 90.1.1.1, IP = 90.1.1.1, constructing IPSec nonce payload
%ASA-7-715046: Group = 90.1.1.1, IP = 90.1.1.1, constructing pfs ke payload
%ASA-7-715001: Group = 90.1.1.1, IP = 90.1.1.1, constructing proxy ID
%ASA-7-713906: Group = 90.1.1.1, IP = 90.1.1.1, Transmitting Proxy Id:
%ASA-7-714007: Group = 90.1.1.1, IP = 90.1.1.1, IKE Initiator sending Initial Contact
%ASA-7-715046: Group = 90.1.1.1, IP = 90.1.1.1, constructing qm hash payload
%ASA-7-714004: Group = 90.1.1.1, IP = 90.1.1.1, IKE Initiator sending 1st QM pkt: msg id = 9d3d0283
%ASA-7-713236: IP = 90.1.1.1, IKE_DECODE SENDING Message (msgid=9d3d0283) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + KE (4) + ID (5) + ID (5) + NOTIFY (11) + NONE (0) total length : 328
%ASA-7-713906: IKE Receiver: Packet received on 185.193.35.60:500 from 90.1.1.1:500
%ASA-7-713236: IP = 90.1.1.1, IKE_DECODE RECEIVED Message (msgid=9d3d0283) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + KE (4) + ID (5) + ID (5) + NONE (0) total length : 300
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing hash payload
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing SA payload
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing nonce payload
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing ke payload
%ASA-7-713906: Group = 90.1.1.1, IP = 90.1.1.1, processing ISA_KE for PFS in phase 2
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing ID payload
%ASA-7-714011: Group = 90.1.1.1, IP = 90.1.1.1, ID_IPV4_ADDR ID received
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing ID payload
%ASA-7-714011: Group = 90.1.1.1, IP = 90.1.1.1, ID_IPV4_ADDR ID received
%ASA-7-713906: Group = 90.1.1.1, IP = 90.1.1.1, loading all IPSEC SAs
%ASA-7-715001: Group = 90.1.1.1, IP = 90.1.1.1, Generating Quick Mode Key!
%ASA-7-715001: Group = 90.1.1.1, IP = 90.1.1.1, Generating Quick Mode Key!
%ASA-6-602303: IPSEC: An outbound LAN-to-LAN SA (SPI= 0xF26BC494) between 185.193.35.60 and 90.1.1.1 (user= 90.1.1.1) has been created.
%ASA-5-713049: Group = 90.1.1.1, IP = 90.1.1.1, Security negotiation complete for LAN-to-LAN Group (90.1.1.1) Initiator, Inbound SPI = 0xc3b4a664, Outbound SPI = 0xf26bc494
%ASA-7-713906: Group = 90.1.1.1, IP = 90.1.1.1, oakley constructing final quick mode
%ASA-6-602303: IPSEC: An inbound LAN-to-LAN SA (SPI= 0xC3B4A664) between 185.193.35.60 and 90.1.1.1 (user= 90.1.1.1) has been created.
%ASA-7-714006: Group = 90.1.1.1, IP = 90.1.1.1, IKE Initiator sending 3rd QM pkt: msg id = 9d3d0283
%ASA-7-713236: IP = 90.1.1.1, IKE_DECODE SENDING Message (msgid=9d3d0283) with payloads : HDR + HASH (8) + NONE (0) total length : 76
%ASA-7-715007: Group = 90.1.1.1, IP = 90.1.1.1, IKE got a KEY_ADD msg for SA: SPI = 0xf26bc494
%ASA-7-715077: Group = 90.1.1.1, IP = 90.1.1.1, Pitcher: received KEY_UPDATE, spi 0xc3b4a664
%ASA-7-715080: Group = 90.1.1.1, IP = 90.1.1.1, Starting P2 rekey timer: 27360 seconds.
%ASA-5-713120: Group = 90.1.1.1, IP = 90.1.1.1, PHASE 2 COMPLETED (msgid=9d3d0283)
SLP2PVPN01//pri/act(config)# sh log | i 90.1.1.1
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing hash payload
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing SA payload
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing nonce payload
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing ke payload
%ASA-7-713906: Group = 90.1.1.1, IP = 90.1.1.1, processing ISA_KE for PFS in phase 2
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing ID payload
%ASA-7-714011: Group = 90.1.1.1, IP = 90.1.1.1, ID_IPV4_ADDR ID received
%ASA-7-715047: Group = 90.1.1.1, IP = 90.1.1.1, processing ID payload
%ASA-7-714011: Group = 90.1.1.1, IP = 90.1.1.1, ID_IPV4_ADDR ID received
%ASA-7-713906: Group = 90.1.1.1, IP = 90.1.1.1, loading all IPSEC SAs
%ASA-7-715001: Group = 90.1.1.1, IP = 90.1.1.1, Generating Quick Mode Key!
%ASA-7-715001: Group = 90.1.1.1, IP = 90.1.1.1, Generating Quick Mode Key!
%ASA-6-602303: IPSEC: An outbound LAN-to-LAN SA (SPI= 0xF26BC494) between 185.193.35.60 and 90.1.1.1 (user= 90.1.1.1) has been created.
%ASA-5-713049: Group = 90.1.1.1, IP = 90.1.1.1, Security negotiation complete for LAN-to-LAN Group (90.1.1.1) Initiator, Inbound SPI = 0xc3b4a664, Outbound SPI = 0xf26bc494
%ASA-7-713906: Group = 90.1.1.1, IP = 90.1.1.1, oakley constructing final quick mode
%ASA-6-602303: IPSEC: An inbound LAN-to-LAN SA (SPI= 0xC3B4A664) between 185.193.35.60 and 90.1.1.1 (user= 90.1.1.1) has been created.
%ASA-7-714006: Group = 90.1.1.1, IP = 90.1.1.1, IKE Initiator sending 3rd QM pkt: msg id = 9d3d0283
%ASA-7-713236: IP = 90.1.1.1, IKE_DECODE SENDING Message (msgid=9d3d0283) with payloads : HDR + HASH (8) + NONE (0) total length : 76
%ASA-7-715007: Group = 90.1.1.1, IP = 90.1.1.1, IKE got a KEY_ADD msg for SA: SPI = 0xf26bc494
%ASA-7-715077: Group = 90.1.1.1, IP = 90.1.1.1, Pitcher: received KEY_UPDATE, spi 0xc3b4a664
%ASA-7-715080: Group = 90.1.1.1, IP = 90.1.1.1, Starting P2 rekey timer: 27360 seconds.
%ASA-5-713120: Group = 90.1.1.1, IP = 90.1.1.1, PHASE 2 COMPLETED (msgid=9d3d0283)
Note the error - %ASA-7-715038
capture
1: 03:30:25.958583 90.1.1.1.500 > 80.1.1.1.500: udp 92
2: 03:30:25.959178 80.1.1.1.500 > 90.1.1.1.500: udp 92
3: 03:30:35.958705 90.1.1.1.500 > 80.1.1.1.500: udp 92
4: 03:30:35.959270 80.1.1.1.500 > 90.1.1.1.500: udp 92
5: 03:30:45.958171 90.1.1.1.500 > 80.1.1.1.500: udp 92
6: 03:30:45.958705 80.1.1.1.500 > 90.1.1.1.500: udp 92
7: 03:30:55.958217 90.1.1.1.500 > 80.1.1.1.500: udp 92
8: 03:30:55.958751 80.1.1.1.500 > 90.1.1.1.500: udp 92
9: 03:31:05.958354 90.1.1.1.500 > 80.1.1.1.500: udp 92
10: 03:31:05.958904 80.1.1.1.500 > 90.1.1.1.500: udp 92
11: 03:31:15.957790 90.1.1.1.500 > 80.1.1.1.500: udp 92
12: 03:31:15.958339 80.1.1.1.500 > 90.1.1.1.500: udp 92
13: 03:31:25.957637 90.1.1.1.500 > 80.1.1.1.500: udp 92
14: 03:31:25.958248 80.1.1.1.500 > 90.1.1.1.500: udp 92
15: 03:31:35.957973 90.1.1.1.500 > 80.1.1.1.500: udp 92
16: 03:31:35.958507 80.1.1.1.500 > 90.1.1.1.500: udp 92
17: 03:31:45.957363 90.1.1.1.500 > 80.1.1.1.500: udp 92
18: 03:31:45.957943 80.1.1.1.500 > 90.1.1.1.500: udp 92
19: 03:31:55.957439 90.1.1.1.500 > 80.1.1.1.500: udp 92
20: 03:31:55.958034 80.1.1.1.500 > 90.1.1.1.500: udp 92
21: 03:32:05.957500 90.1.1.1.500 > 80.1.1.1.500: udp 92
22: 03:32:05.958049 80.1.1.1.500 > 90.1.1.1.500: udp 92
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2018 08:29 AM
You're trying to configure a L2L vpn with multiple peers but on your example, you have the same IP:
90.1.1.1 90.1.1.1
When you use any of the IPs separately, everything works right? But when you use both of them it's not working?
You said that tunnel is UP but traffic not passing through (encaps yes but not decaps). What's the configuration on the other side? Same crypto acl?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2018 01:02 AM
- on the crypto map I would just add both peers
- I would make sure I have two static routes for the two peers in this way:
route outside 90.1.1.1 255.255.255.255 80.1.1.1
route outside 70.1.1.1 255.255.255.255 80.1.1.1
On this scenario does it work for you?
If not we can easily add track object to each static route. This way we will surely make it work ;)
P.S. don't change the route to 90.1.1.1 to inside, it'll only give you headaches and it will not be relevant to your tests; FYI the behavior you're seeing is NORMAL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2018 10:06 PM
Default route is already there. So, we don't need to configure specific route towards outside. Actually in single mode when we divert the route towards inside. VPN switchover to seconday. But in case of context that is not happening. When I enabled the debug. DPD packet were exchanged between the peers. That is why it was not working. But in case of single mode It stop sending message to peer when we put static route towards inside.
I don't have lab to test context senerios.
Does anyone have eve-ng fully loaded for lab purpose?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2018 11:32 AM
I able to resolve the issue
Inside route was not working. So, I put a route towards outside with next hop 4.4.4.4
and I got the result
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide