- Cisco Community
- Technology and Support
- Security
- VPN
- Site to Site VPN Failover
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Site to Site VPN Failover
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2020 07:10 AM
We have remote site Cisco ASA 5506 firewalls that run IoT devices. We tunnel this traffic across our WAN on an ipsec site to site vpn to a Sophos Appliance which then routes the traffic to the internet.
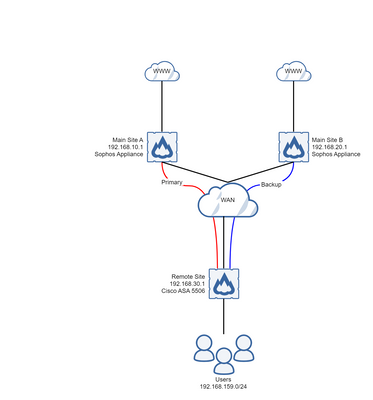
Up until now all these remote site firewalls have terminated on a single remote appliance, which is a bit of a single point of failure! What I would like to do is have the VPN failover to an identical device at a different site. Like the topology below.
To make sure the VPN is configured correctly, if I have either Main Site peer address configured, the VPN correctly forms. The problems then start when I try adding Site B as the backup peer to the connection profile of Site A..
I've added two default tracked routes with different metrics, the primary to Site A, and the backup to Site B. When Site A becomes unreachable the IP SLA drops the route to Site A correctly and fails over to B. The VPN however does not, and it just sits there as if the VPN is up. If I logout the VPN and then try to fire up some traffic from the user side, the VPN comes back up to Site A. The only way round this at the moment has been to reload the Remote Site firewall, and the VPN correctly forms to Site B.
When Site A becomes available, the tracked route comes back online, however then the VPN doesn't fail back to the primary.
I'm using the following config on my Remote site firewall, with the Sophos appliances only responding to VPN requests.
sla monitor 1
type echo protocol ipIcmpEcho 192.168.10.1 interface inside
sla monitor schedule 1 life forever start-time now
sla monitor 2
type echo protocol ipIcmpEcho 192.168.20.1 interface inside
sla monitor schedule 2 life forever start-time now
service sw-reset-button
crypto ipsec ikev1 transform-set IPSEC esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map inside_map1 1 match address inside_cryptomap
crypto map inside_map1 1 set pfs group5
crypto map inside_map1 1 set peer 192.168.10.1 192.168.20.1
crypto map inside_map1 1 set ikev1 transform-set IPSEC
crypto map inside_map1 1 set nat-t-disable
crypto map inside_map1 interface inside
crypto ca trustpool policy
crypto ikev1 enable inside
crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
route inside 0.0.0.0 0.0.0.0 192.168.10.1 1 track 1
route inside 0.0.0.0 0.0.0.0 192.168.20.1 5 track 2
track 1 rtr 1 reachability
!
track 2 rtr 2 reachability
tunnel-group 192.168.10.1 type ipsec-l2l
tunnel-group 192.168.10.1 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group 192.168.20.1 type ipsec-l2l
tunnel-group 192.168.20.1 ipsec-attributes
ikev1 pre-shared-key *****
I'm obviously doing something wrong, but have exhausted my knowledge as to what it is. Any help would be appreciated.
Kind
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2020 07:17 AM
Hi @RobjBrown
Dead Peer Detection (DPD) would be required for the firewalls to determine whether the tunnel is down and clear the IPSec SAs. Check it's enabled on both the Sophos and ASA firewalls.
HTH
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide