- Cisco Community
- Technology and Support
- Security
- VPN
- Site to Site VPN from Site C to Site B. In between there is Site A.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Site to Site VPN from Site C to Site B. In between there is Site A.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2013 03:02 AM
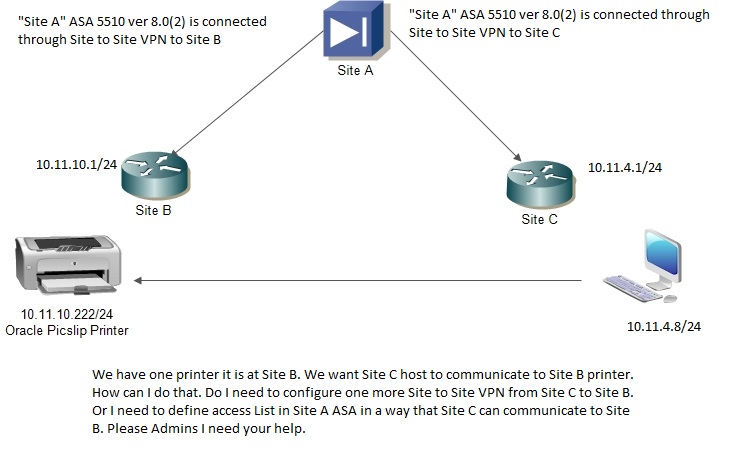
We have a requirement we have one printer which is at "Site C" and it has to print from site B. However, VPN is not configured from "Site B to Site C". These two sites are configured Site to Site VPN from SITE A "ASA 5510 version 8.0(2). Is there a way I can get communicate "Site B to Site C" by defining access list or anything. Please let me know. Please also have a look at the topology two routers at the remote site are 2800 Series. Thank you.
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2013 03:12 AM
Hi,
Well the I guess you got 2 options
- Configure a L2L VPN directly between Site B and Site C (traffic wouldnt have to go through Site A)
- Add the traffic between Site B and Site C on both of the existing L2L VPN connections
If you want to tunnel the traffic between Site B and Site C through Site A then you will have to
- Make sure that the ASA has "same-security-traffic permit intra-interface" configured. This will enable traffic entering on the "outside" to leave on the "outside". This is essentially the traffic between Site B and Site C taking an U-turn at Site A ASA. The mentioned configuration is needed for this to be possible.
- Define in the Site A to Site B L2L VPN connection ACLs that traffic from Site B to Site C should go through this L2L VPN
- Define in the Site A to Site C L2L VPN connection ACLs that traffic from SIte B to Site C should go through this L2L VPN
- Define a NAT0 configuration on the Site A ASA "outside" interface which does NAT0 between the Site B and Site C networks
- Also configure the appropriate NAT0 configurations on the Site B and Site C routers
Hope this helps
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2013 04:03 AM
Looks like Site C to Site B will be easy. Please have a look at Site B and Site C running configuration. Now please let me know how to configure 2 VPN on single 2800 Series router. Without Disturbing Site A configuration
Site C#show run
Building configuration...
Current configuration : 2672 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname SITCO-DIA1
!
boot-start-marker
boot system flash flash:c2800nm-advsecurityk9-mz.124-15.T9.bin
boot system flash flash:c2800nm-ipbase-mz.124-15.T10.bin
boot-end-marker
!
logging buffered 51200 warnings
enable secret 5 $1$UC784zH75YQO..fhY6S.ar0
enable password asdf
!
no aaa new-model
dot11 syslog
!
!
ip cef
no ip dhcp use vrf connected
!
ip dhcp pool DSL
network 10.11.4.0 255.255.255.0
default-router 10.11.4.1
dns-server 208.67.222.222
!
!
ip domain name yourdomain.com
!
multilink bundle-name authenticated
!
!
!
!
!
username admin privilege 15 secret 5 $ghjikhggfffd
archive
log config
hidekeys
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key ijklmnopq address 87.101.158.218 no-xauth
!
!
crypto ipsec transform-set VPN_ITC_TS esp-aes esp-sha-hmac
!
crypto map VPN_ITC 10 ipsec-isakmp
set peer 87.101.158.218
set transform-set VPN_ITC_TS
match address 135
!
!
!
!
class-map match-any Servers-List
match access-group 190
!
!
policy-map Servers
class Servers-List
bandwidth percent 50
!
!
!
!
interface FastEthernet0/0
description WAN ITC
bandwidth 2048
ip address 87.101.54.74 255.255.255.252
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map VPN_ITC
service-policy output Servers
!
interface FastEthernet0/1
description LAN ITC
ip address 10.11.4.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 87.101.54.73
ip route 87.101.158.216 255.255.255.252 87.101.54.73
ip route 192.168.0.0 255.255.0.0 87.101.54.73
!
!
ip http server
ip http access-class 23
ip http authentication local
no ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
ip nat inside source list 138 interface FastEthernet0/0 overload
!
access-list 135 permit ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 deny ip 10.11.4.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 permit ip 10.11.4.0 0.0.0.255 any
access-list 190 remark List of Servers to be assigned QOS
access-list 190 permit ip any host 192.168.50.1
access-list 190 permit ip any host 192.168.50.13
access-list 190 permit ip any host 192.168.50.15
access-list 190 permit ip any host 192.168.50.21
access-list 190 permit ip any host 192.168.50.22
access-list 190 permit ip any host 192.168.50.24
!
!
!
!
control-plane
!
!
line con 0
login local
line aux 0
line vty 0 4
login local
transport input telnet
!
scheduler allocate 20000 1000
!
end
Here is Site B router
Site B#show run
Building configuration...
Current configuration : 2859 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname SITCO-warehouse
!
boot-start-marker
boot system flash flash:c2800nm-advsecurityk9-mz.124-15.T9.bin
boot system flash flash:c2800nm-ipbase-mz.124-15.T10.bin
boot-end-marker
!
logging buffered 51200 warnings
enable password 7 010156544F2B424E154F1E2837253221
!
no aaa new-model
dot11 syslog
!
!
ip cef
no ip dhcp use vrf connected
!
ip dhcp pool DSL
network 10.11.10.0 255.255.255.0
default-router 10.11.10.1
dns-server 208.67.222.222
!
!
ip domain name yourdomain.com
!
multilink bundle-name authenticated
!
!
!
!
!
username abcd privilege 15 secret 5 efghijjk
archive
log config
hidekeys
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key abcdefg address 87.101.158.218 no-xauth
!
!
crypto ipsec transform-set VPN_ITC_TS esp-aes esp-sha-hmac
!
crypto map VPN_ITC 10 ipsec-isakmp
set peer 87.101.158.218
set transform-set VPN_ITC_TS
match address 135
!
!
!
!
class-map match-any Servers-List
match access-group 190
!
!
policy-map Servers
class Servers-List
bandwidth percent 50
!
!
!
!
interface FastEthernet0/0
description WAN Link to ITC
bandwidth 2048
ip address 87.105.144.2 255.255.255.252
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map VPN_ITC
service-policy output Servers
!
interface FastEthernet0/1
description LAN
ip address 10.11.10.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex full
speed 100
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 87.105.144.1
ip route 87.101.158.216 255.255.255.252 87.105.144.1
ip route 192.168.0.0 255.255.0.0 87.105.144.1
!
!
ip http server
ip http access-class 23
ip http authentication local
no ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
ip nat inside source list 138 interface FastEthernet0/0 overload
!
access-list 20 permit 212.93.196.0 0.0.0.255
access-list 23 permit 10.10.10.0 0.0.0.7
access-list 135 permit ip 10.11.10.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 deny ip 10.11.10.0 0.0.0.255 192.168.0.0 0.0.255.255
access-list 138 permit ip 10.11.10.0 0.0.0.255 any
access-list 190 remark List of Servers to be assigned QOS
access-list 190 permit ip any host 192.168.50.1
access-list 190 permit ip any host 192.168.50.13
access-list 190 permit ip any host 192.168.50.15
access-list 190 permit ip any host 192.168.50.21
access-list 190 permit ip any host 192.168.50.22
access-list 190 permit ip any host 192.168.50.24
!
!
!
!
control-plane
!
!
line con 0
login local
line aux 0
line vty 0 4
privilege level 15
login local
transport input telnet
line vty 5 15
access-class 23 in
privilege level 15
login local
transport input telnet
!
scheduler allocate 20000 1000
!
end
Note: IPs and password are edited.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

