- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Site-to-Site VPN in Cisco ASA 5520 ver 9.1
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2020 11:05 PM
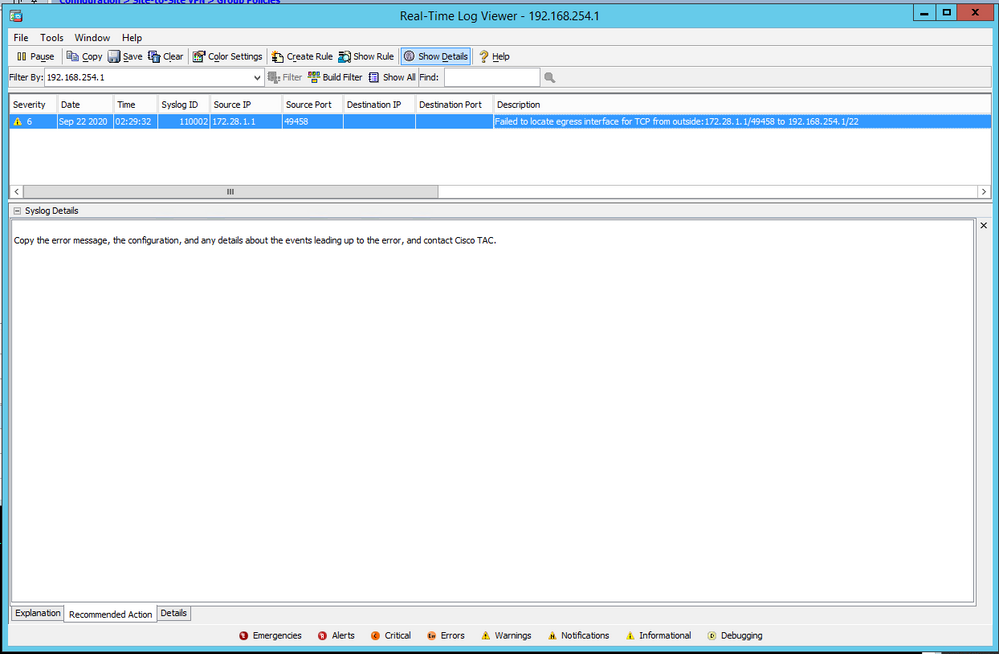
I have created an IPSec tunnel between Cisco ASA 5520 in DC and Aruba Virtual Gateway in AWS. NAT-T is enabled on both sides. The tunnel is up. Cisco local network in 192.168.254.0/28 which is the Gig0/1 interface. Aruba network is 172.28.1.0/24. I cannot ping across the tunnel. It maybe due to ICMP disabled by default. However, when I tried to use ssh, I got the following error:
How do I troubleshoot this? Also how do I enable ICMP across the tunnel?
the following access-list is present on the ASA
access-list outside_cryptomap_2 extended permit ip 192.168.254.0 255.255.255.240 172.28.1.0 255.255.255.0
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2020 10:32 PM
I was able to resolve the issue by allowing interesting traffic through the access-list applied on the outside interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2020 12:38 AM
How do you know the tunnel is up and functioning?
Please provide the following output of "show crypto ipsec sa", "show nat detail", "show route" and your configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2020 05:41 AM
@Rob IngramI had to roll back the changes I made last night due to other reasons. So I cannot share the show results. But during the configuration, "show crypto ikev1 sa" had 1 active tunnel. "show crypto ipsec sa peer x.x.x.x" had correct transform set, proxy-IDs and even some packet encaps and decaps. I did not check "show nat details" but when I ran "show run | i remote-net" I had found "nat (inside,outside) source static local-net local-net destination static remote-net remote-net no-proxy-arp route-lookup".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2020 06:38 AM
I was able to piece together some information from the logs I had.
CM-ASA# show crypto ikev1 sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: x.x.x.x
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
CM-ASA#
CM-ASA(config)# show crypto ipsec sa peer x.x.x.x
peer address: x.x.x.x
Crypto map tag: SYSTEM_DEFAULT_CRYPTO_MAP, seq num: 65535, local addr: y.y.y.y
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (172.20.10.42/255.255.255.255/0/0)
current_peer: x.x.x.x, username: admin
dynamic allocated peer ip: 172.20.10.42
dynamic allocated peer ip(ipv6): 0.0.0.0
#pkts encaps: 1547, #pkts encrypt: 1547, #pkts digest: 1547
#pkts decaps: 1684, #pkts decrypt: 1684, #pkts verify: 1684
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 1547, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: y.y.y.y/4500, remote crypto endpt.: x.x.x.x/10001
path mtu 1472, ipsec overhead 66(52), override mtu 1406, media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 2B2DFE53
current inbound spi : 8E9C60A0
inbound esp sas:
spi: 0x8E9C60A0 (2392613024)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={RA, Tunnel, NAT-T-Encaps, IKEv2, }
slot: 0, conn_id: 1568768, crypto-map: SYSTEM_DEFAULT_CRYPTO_MAP
sa timing: remaining key lifetime (sec): 28372
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x2B2DFE53 (724434515)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={RA, Tunnel, NAT-T-Encaps, IKEv2, }
slot: 0, conn_id: 1568768, crypto-map: SYSTEM_DEFAULT_CRYPTO_MAP
sa timing: remaining key lifetime (sec): 28372
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: BLR2LVR, seq num: 1, local addr: y.y.y.y
access-list outside_cryptomap_2 extended permit ip 192.168.254.0 255.255.255.240 172.28.1.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.254.0/255.255.255.240/0/0)
remote ident (addr/mask/prot/port): (172.28.1.0/255.255.255.0/0/0)
current_peer: x.x.x.x
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: y.y.y.y/4500, remote crypto endpt.: x.x.x.x/4500
path mtu 1500, ipsec overhead 82(52), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 441FC300
current inbound spi : BF1427D1
inbound esp sas:
spi: 0xBF1427D1 (3205769169)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, NAT-T-Encaps, IKEv1, }
slot: 0, conn_id: 1576960, crypto-map: BLR2LVR
sa timing: remaining key lifetime (kB/sec): (4374000/1699)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0x441FC300 (1142932224)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, NAT-T-Encaps, IKEv1, }
slot: 0, conn_id: 1576960, crypto-map: BLR2LVR
sa timing: remaining key lifetime (kB/sec): (4374000/1699)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
CM-ASA(config)# show run
CM-ASA(config)# show access-list | i 172.28
access-list outside_cryptomap_2 line 1 extended permit ip 192.168.254.0 255.255.255.240 172.28.1.0 255.255.255.0 (hitcnt=0) 0x2d0d53cc
CM-ASA(config)# exit
CM-ASA# show run crypto map
crypto map BLR2LVR 1 match address outside_cryptomap_2
crypto map BLR2LVR 1 set peer x.x.x.x
crypto map BLR2LVR 1 set ikev1 transform-set VG_Aruba1
crypto map BLR2LVR 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map BLR2LVR interface outside
CM-ASA#
CM-ASA# show running-config | i P2
access-list P2 extended permit object-group DM_INLINE_SERVICE_1 any host 172.30.1.50
access-list P2 extended permit tcp any host 172.30.1.44
access-list P2 extended permit icmp any object ClearPassDataSVI
access-group P2 in interface outside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2020 12:52 PM
@Rob IngramDo we need access-group on the outside interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2020 02:22 AM - edited 09-22-2020 02:23 AM
Do you have a (correct) route to the remote subnet?
Also, simulate the flow with packet-tracer and share the result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2020 06:05 AM
I hadn't checked the "show route" output. I am going to simulate it in packet-tracer now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2020 10:32 PM
I was able to resolve the issue by allowing interesting traffic through the access-list applied on the outside interface.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: