- Cisco Community
- Technology and Support
- Security
- VPN
- Re: SSL Certificate *renewal* instructions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2017 03:52 PM - edited 03-12-2019 04:30 AM
I can't seem to find clear instructions for installing a RENEWED ssl certificate on an ASA. All of the instructions I see talk about generating the CSR from the ASA but what about when a customer renews their SSL cert through a popular vendor such as GoDaddy or DigiCert? They are not using a CSR generated by the ASA so how in the heck do I get the new cert installed??
Also, nobody (and I mean nobody) has been able to demonstrate how to install a wildcard cert to an ASA. The ASA will not allow an asterisk (*) as part of the FQDN or CN.
Please don't just post some link to a cisco doc, *explain* it to me because I guarantee I've already read any cisco doc you are about to link.
As you can imagine, I'm very frustrated at this point.
Thanks,
John
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2017 09:13 PM - edited 08-31-2017 09:31 AM
You can install a wildcard certificate on an ASA. You just cannot create a CSR for a wildcard using the ASA.
When installing the wildcard certificate (or renewed certificate) you must have the private key used to request the wildcard (or the original wildcard in case of a renewal). Often we do this with OpenSSL making the key easy to save.
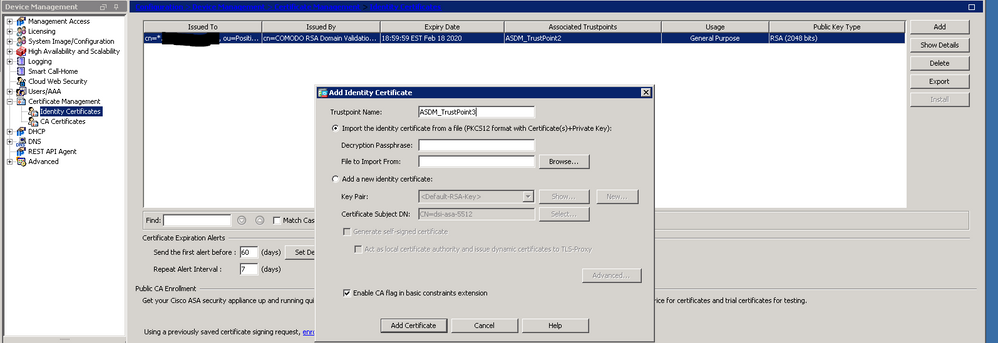
When you have the wildcard certificate and key in a PKCS12 file, just add them as a new identity certificate as shown below and then choose that new certificate instead of the old one under your remote access VPN configuration. As you can see in the screenshot, my ASA currently has a wildcard certificate installed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2017 08:49 PM - edited 08-28-2017 08:50 PM
Hi
First of all I'm not very comfortable with asdm and maybe it could be easier if someone else can help you on that topic.
There's no kind of renewal certificate procedure.
Let me explain:
- need to create a new trustpoint
- get your provider root and intermediate
- having your cert and your private key
- using openssl to make a pkcs12 certificate
- authenticate your trustpoint with your provider cert
- import your pkcs12 cert into your trustpoint
- use the command ssl trust-point to change from your old to your new certificate.
Create trustpoint:
crypto ca trustpoint mywildcardcert.com
fqdn xxx.company.com
enrollment terminal
revocation-check none
Authenticate your trustpoint:
crypto ca authenticate mywildcardcert.com
then copy/paste your CA authority cert
-----BEGIN CERTIFICATE-----
Your CA authority certificate (usually you receive a bundle containing the root and subca)
-----END CERTIFICATE-----
quit
Then you need to accept the certificate and you should get the message that trustpoint ca is accepted and certificate has been imported.
Openssl stuff: i recommend you to do it on a Linux or mac machine (like Ubuntu vm if you don't have any mac or Linux machine)
cat RootCA.pem Intermediate.pem > root.crt
openssl pkcs12 -export -in wildcardcert.pem -inkey wildcardKEY.pem -certfile root.crt -out mycertwildcardexport.p12
It'll prompt you for a password. Choose something complexe for security purpose but don't lose it as you'll need it on the next step.
cat mycertwildcardexport.p12 | base64
Import on ASA
crypto ca import mywildcardcert.com pkcs12 secret-defined-before
Paste all content of your p12 file created before then type quit on the next empty line.
You'll get prompted if you want to import all cert hierarchy. Answer yes.
Last, assign it to your outside interface:
ssl trust-point mywildcardcert.com outside
If you want to validate it, you can use openssl:
openssl s_client -connect your-fqdn-vpn:443
Let me know how it went.
Thanks
PS: Please don't forget to rate and select as validated answer if this answered your question
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2017 09:28 AM
I appreciate you taking the time to lay out all the steps. There is some helpful information in your post but not exactly what I was looking for.
Thank you for your effort.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2017 01:53 PM
Sorry I was thinking that you were searching for "how to import wildcard certificate" on ASA. Sure it was through CLI and not ASDM.
thanks
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2017 09:13 PM - edited 08-31-2017 09:31 AM
You can install a wildcard certificate on an ASA. You just cannot create a CSR for a wildcard using the ASA.
When installing the wildcard certificate (or renewed certificate) you must have the private key used to request the wildcard (or the original wildcard in case of a renewal). Often we do this with OpenSSL making the key easy to save.
When you have the wildcard certificate and key in a PKCS12 file, just add them as a new identity certificate as shown below and then choose that new certificate instead of the old one under your remote access VPN configuration. As you can see in the screenshot, my ASA currently has a wildcard certificate installed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2017 09:24 AM
This was exactly what I needed to know. Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2017 09:33 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2018 07:06 AM
Do I have to delete the old cert? I added my new wildcard cert and saved it but I am getting the cert expiration warning when VPN'ing into my environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2018 08:45 AM
although you imported the new cert, it’s sitting idle and the VPN config is
still using the old cert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2018 09:18 AM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2018 08:50 AM - edited 05-07-2018 08:51 AM
You just need to assign the enrolled SSL trustpoint to the interface you're using for Anyconnect termination.
CLI:
ASA (config)# ssl trust-point <trustpoint name> <interface>
ASDM:
Configuration/device mgmt/advanced/SSL settings: select the interface and click on "edit" then select the "primary enrolled certificate" dropdown, select your new cert and then click OK. Don't forget to apply and save the new config.
You're done.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 08:50 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 09:26 PM
If i understand correctly you already renewed the certificate on your F5, Right?
If so, you should have the cert and the private key, right? Then take a look on my post at the beginning of this thread, I explain how to combine a cert pem file and private key into p12 file. On asa, i also explained how to import that file and set this new trustpoint for anyconnect.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2018 04:10 AM
Steps to create pkcs12 using openssl given here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2020 09:16 AM
Hi Marvin, I thought I would just add this here as it may be helpful.
You talk of importing the keys and new cert from a pkcs12 file. In my case I did not have a pkcs12 file or a private key file.
I thought I would add if you just have .crt file from the renewed certificate the same as previously requested. Just change the radio button to add new, choose the same key-pair used in the existing trustpoint.
eg:
crypto ca trustpoint ASDM_TrustPoint0
enrollment terminal
subject-name CN=vpn.yourcompany.com
keypair SSL-Keypair
no validation-usage
crl configure
The following command will tell you which trustpoint your currently using.
show run | inc ssl trust-point
eg: ssl trust-point ASDM_TrustPoint0
There may be an interface name as the 4th parameter.
Once you have the certificate imported and any newer CA certs imported.
Change the above command to the new trustpoint name.
GoDaddy has the following helpful link.
Regards.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide