- Cisco Community
- Technology and Support
- Security
- VPN
- Trouble connecting with an IPSEC tunnel in a Hub and Spoke model.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Trouble connecting with an IPSEC tunnel in a Hub and Spoke model.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2021 07:04 PM - edited 01-27-2021 08:44 PM
Hello everyone, I am currently working on a Hub and Spoke model network, connecting the branches with an IPSEC tunnel. ISAKMP turns on when I'm done configuring, but I can't seem to ping any other branch, or generate traffic between them. I've been troubleshooting this for a few days, but I could really use a new set of eyes. I'll attach the output of "show crypto ipsec" from my Hub(LA) and the configuration files for LA and the first branch SF.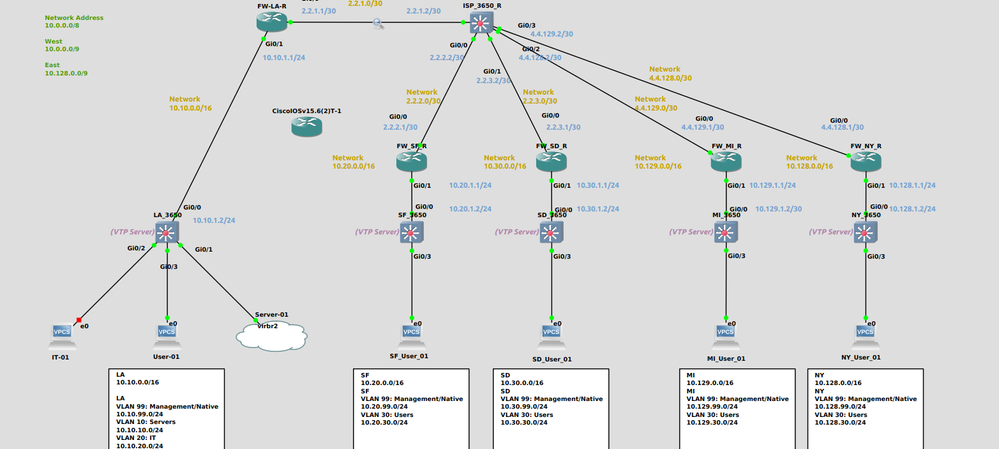
!!FW_LA_R enable configure terminal hostname FW_LA_R ! Int g0/0 Ip add 2.2.1.1 255.255.255.248 Ip nat outside No shut Int g0/1 Ip add 10.10.1.1 255.255.255.0 Ip nat inside No shut ip access-list extended IPSEC_LIST_SF permit ip 10.10.0.0 0.0.255.255 10.20.0.0 0.0.255.255 permit ip 10.30.0.0 0.0.255.255 10.20.0.0 0.0.255.255 permit ip 10.128.0.0 0.0.255.255 10.20.0.0 0.0.255.255 ip access-list extended IPSEC_LIST_SD permit ip 10.10.0.0 0.0.255.255 10.30.0.0 0.0.255.255 permit ip 10.20.0.0 0.0.255.255 10.30.0.0 0.0.255.255 permit ip 10.128.0.0 0.0.255.255 10.30.0.0 0.0.255.255 ip access-list extended IPSEC_LIST_NY permit ip 10.10.0.0 0.0.255.255 10.128.0.0 0.0.255.255 permit ip 10.20.0.0 0.0.255.255 10.128.0.0 0.0.255.255 permit ip 10.129.0.0 0.0.255.255 10.128.0.0 0.0.255.255 ip access-list extended NAT_LIST deny ip 10.10.0.0 0.0.255.255 10.20.0.0 0.0.255.255 deny ip 10.30.0.0 0.0.255.255 10.20.0.0 0.0.255.255 deny ip 10.128.0.0 0.0.255.255 10.20.0.0 0.0.255.255 ! deny ip 10.10.0.0 0.0.255.255 10.30.0.0 0.0.255.255 deny ip 10.20.0.0 0.0.255.255 10.30.0.0 0.0.255.255 deny ip 10.128.0.0 0.0.255.255 10.30.0.0 0.0.255.255 ! deny ip 10.10.0.0 0.0.255.255 10.128.0.0 0.0.255.255 deny ip 10.20.0.0 0.0.255.255 10.128.0.0 0.0.255.255 deny ip 10.129.0.0 0.0.255.255 10.128.0.0 0.0.255.255 ! permit ip 10.10.0.0 0.0.255.255 any ip nat inside source list NAT_LIST int g0/0 overload ! ! ! ! ip route 0.0.0.0 0.0.0.0 2.2.1.2 ip route 10.10.0.0 255.255.0.0 10.10.1.2 ! !! IPSec Phase 1 ! crypto isakmp enable crypto isakmp policy 10 authentication pre-share encryption aes 256 hash sha group 5 crypto isakmp key ABC12345 address 2.2.2.1 crypto isakmp key ABC12345 address 2.2.3.1 crypto isakmp key ABC12345 address 4.4.128.1 ! IPSec Phase 2 ! IPSec Phase 2 crypto ipsec transform-set ABCSET esp-aes 256 esp-sha-hmac crypto map ABCMAP 10 ipsec-isakmp match address IPSEC_LIST_SF set peer 2.2.2.1 set transform-set ABCSET crypto map ABCMAP 20 ipsec-isakmp match address IPSEC_LIST_SD set peer 2.2.3.1 set transform-set ABCSET crypto map ABCMAP 30 ipsec-isakmp match address IPSEC_LIST_NY set peer 4.4.128.1 set transform-set ABCSET interface g0/0 crypto map ABCMAP router ospf 1 default-information originate network 10.0.0.0 0.127.255.255 area 0 network 10.128.0.0 0.127.255.255 area 0 !LA_3650 enable configure terminal hostname LA_3650 ! ip routing vtp mode server vtp domain MAIN Vlan 99 name management Vlan 10 name Server Vlan 20 name IT Vlan 30 name Users interface G0/0 no switchport ip address 10.10.1.2 255.255.255.0 no shutdown interface vlan 99 ip address 10.10.99.1 255.255.255.0 no shutdown interface vlan 10 ip address 10.10.10.1 255.255.255.0 interface vlan 20 ip address 10.10.20.1 255.255.255.0 interface vlan 30 ip address 10.10.30.1 255.255.255.0 no shutdown interface g0/1 switchport mode access switchport access vlan 10 interface g0/2 switchport mode access switchport access vlan 20 interface g0/3 switchport mode access switchport access vlan 30 router ospf 1 network 10.0.0.0 0.127.255.255 area 0 network 10.128.0.0 0.127.255.255 area 0 !FW_SF_R enable configure terminal hostname FW_SF_R ! interface g0/0 ip address 2.2.2.1 255.255.255.252 ip nat outside no shutdown interface g0/1 ip address 10.20.1.1 255.255.255.0 ip nat inside no shutdown ip route 0.0.0.0 0.0.0.0 2.2.2.2 ip nat inside source list NAT_LIST interface g0/0 overload ip access-list extended IPSEC_LIST permit ip 10.20.0.0 0.0.255.255 10.10.0.0 0.0.255.255 permit ip 10.20.0.0 0.0.255.255 10.30.0.0 0.0.255.255 permit ip 10.20.0.0 0.0.255.255 10.129.0.0 0.0.255.255 permit ip 10.20.0.0 0.0.255.255 10.128.0.0 0.0.255.255 ip access-list extended NAT_LIST deny ip 10.20.0.0 0.0.255.255 10.10.0.0 0.0.255.255 deny ip 10.20.0.0 0.0.255.255 10.30.0.0 0.0.255.255 deny ip 10.20.0.0 0.0.255.255 10.129.0.0 0.0.255.255 deny ip 10.20.0.0 0.0.255.255 10.128.0.0 0.0.255.255 permit ip 10.20.0.0 0.0.255.255 any crypto isakmp enable crypto isakmp policy 10 authentication pre-share encryption aes 256 hash sha group 5 crypto isakmp key ABC12345 address 2.2.1.1 crypto ipsec transform-set ABCSET esp-aes 256 esp-sha-hmac crypto map ABCMAP 10 ipsec-isakmp match address IPSEC_LIST set peer 2.2.1.1 set transform-set ABCSET interface g0/0 crypto map ABCMAP router ospf 1 default-information originate network 10.0.0.0 0.127.255.255 area 0 network 10.128.0.0 0.127.255.255 area 0 !SF_3650 enable configure terminal hostname SF_3650 ! ip routing vtp mode server vtp domain SF Vlan 99 name management Vlan 30 name Users interface G0/0 no switchport ip address 10.20.1.2 255.255.255.0 no shutdown interface vlan 99 ip address 10.20.99.1 255.255.255.0 no shutdown interface vlan 30 ip address 10.20.30.1 255.255.255.0 no shutdown interface g0/3 switchport mode access switchport access vlan 30 router ospf 1 network 10.0.0.0 0.127.255.255 area 0 network 10.128.0.0 0.127.255.255 area 0 !FW_SD_R enable configure terminal hostname FW_SD_R ! interface g0/0 ip address 2.2.3.1 255.255.255.252 ip nat outside no shutdown interface g0/1 ip address 10.30.1.1 255.255.255.0 ip nat inside no shutdown ip route 0.0.0.0 0.0.0.0 2.2.3.2 ip nat inside source list NAT_LIST interface G0/0 overload ip access-list extended IPSEC_LIST permit ip any 10.0.0.0 0.127.255.255 permit ip any 10.0.0.0 0.127.255.255 ip access-list extended NAT_LIST permit ip any 10.0.0.0 0.127.255.255 permit ip any 10.0.0.0 0.127.255.255 permit ip any any crypto isakmp enable crypto isakmp policy 10 authentication pre-share encryption aes 256 hash sha group 5 crypto isakmp key ABC12345 address 2.2.1.1 crypto ipsec transform-set ABCSET esp-aes 256 esp-sha-hmac crypto map ABCMAP 10 ipsec-isakmp match address IPSEC_LIST set peer 2.2.1.1 set transform-set ABCSET interface g0/0 crypto map ABCMAP router ospf 1 default-information originate network 10.0.0.0 255.128.0.0 area 0 network 10.128.0.0 255.128.0.0 area 0
FW_LA_R(config-router)#do show crypto ipsec sa
interface: GigabitEthernet0/0
Crypto map tag: ABCMAP, local addr 2.2.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.129.0.0/255.255.0.0/0/0)
remote ident (addr/mask/prot/port): (10.128.0.0/255.255.0.0/0/0)
current_peer 4.4.128.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.1.1, remote crypto endpt.: 4.4.128.1
plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (10.20.0.0/255.255.0.0/0/0)
remote ident (addr/mask/prot/port): (10.30.0.0/255.255.0.0/0/0)
current_peer 2.2.3.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.1.1, remote crypto endpt.: 2.2.3.1
plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (10.30.0.0/255.255.0.0/0/0)
remote ident (addr/mask/prot/port): (10.20.0.0/255.255.0.0/0/0)
current_peer 2.2.2.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.1.1, remote crypto endpt.: 2.2.2.1
plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (10.10.0.0/255.255.0.0/0/0)
remote ident (addr/mask/prot/port): (10.30.0.0/255.255.0.0/0/0)
current_peer 2.2.3.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.1.1, remote crypto endpt.: 2.2.3.1
plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (10.10.0.0/255.255.0.0/0/0)
remote ident (addr/mask/prot/port): (10.20.0.0/255.255.0.0/0/0)
current_peer 2.2.2.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.1.1, remote crypto endpt.: 2.2.2.1
plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (10.10.0.0/255.255.0.0/0/0)
remote ident (addr/mask/prot/port): (10.128.0.0/255.255.0.0/0/0)
current_peer 4.4.128.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.1.1, remote crypto endpt.: 4.4.128.1
plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (10.20.0.0/255.255.0.0/0/0)
remote ident (addr/mask/prot/port): (10.128.0.0/255.255.0.0/0/0)
current_peer 4.4.128.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.1.1, remote crypto endpt.: 4.4.128.1
plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (10.128.0.0/255.255.0.0/0/0)
remote ident (addr/mask/prot/port): (10.20.0.0/255.255.0.0/0/0)
current_peer 2.2.2.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.1.1, remote crypto endpt.: 2.2.2.1
plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (10.128.0.0/255.255.0.0/0/0)
remote ident (addr/mask/prot/port): (10.30.0.0/255.255.0.0/0/0)
current_peer 2.2.3.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.1.1, remote crypto endpt.: 2.2.3.1
plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
- Labels:
-
AnyConnect
-
IPSEC
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2021 12:04 AM
Hi @TL64
If you are pinging from the router itself (FW_LA_R) then the source of the pinging would be the outbound interface, which is not part of the crypto ACL that defines interesting traffic. Ping from an interface in the 10.10.x.x network.
If that doesn't work turn on debugs on both routers (debug crypto isakmp) and provide the output for review.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

