- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Unable to initiate VPN from remote site
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2019 08:53 PM
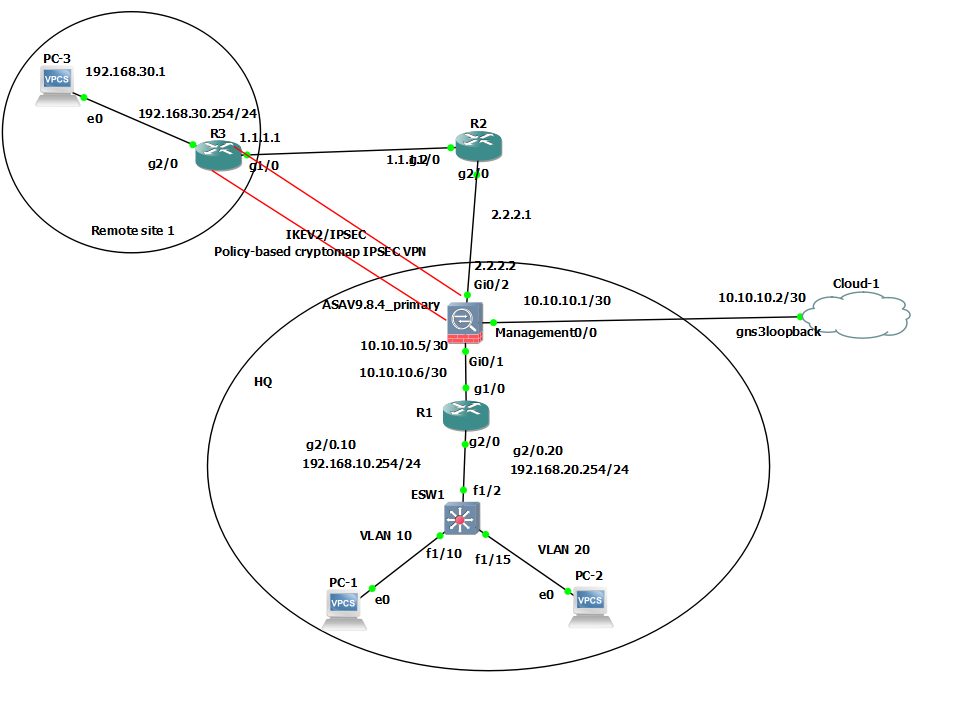
I'm facing a problem where negotiation of second child SA from remote site to second subnet in HQ is failed.
VLAN 10 - 192.168.10.0/24
VLAN 20 - 192.168.20.0/24
VLAN 30 - 192.168.30.0/24
Remote site Vlan 30 initiate first VPN connection to HQ (either Vlan 10 / 20) will success, but then the next Vlan will fail.
Meanwhile if the VPN is initialize from HQ let say from Vlan 10 to Vlan 30 , and then vlan 20 to vlan 30 , both will success.
This is the VPN configuration part for R3.
!
crypto ikev2 proposal TEST1
encryption 3des
integrity sha256
group 2
!
crypto ikev2 policy VPN
proposal TEST1
!
crypto ikev2 keyring KR-R3
peer HQFW
address 2.2.2.2
pre-shared-key VPNPSK
!
!
!
crypto ikev2 profile SITE-PROFILE
match identity remote address 2.2.2.2 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local KR-R3
!
!
!
crypto ipsec transform-set SITE-TS esp-3des esp-sha512-hmac
mode tunnel
!
!
!
crypto map CMAP-SITE 10 ipsec-isakmp
set peer 2.2.2.2
set transform-set SITE-TS
set pfs group2
set ikev2-profile SITE-PROFILE
match address SITE-SITE-CACL
crypto map CMAP-SITE 20 ipsec-isakmp
set peer 2.2.2.2
set transform-set SITE-TS
set pfs group2
set ikev2-profile SITE-PROFILE
match address SITE-SITE-CACL_VLAN2
!
!
interface GigabitEthernet1/0
ip address 1.1.1.1 255.255.255.252
ip nat outside
negotiation auto
crypto map CMAP-SITE
ip access-list extended SITE-SITE-CACL
permit ip 192.168.30.0 0.0.0.255 192.168.10.0 0.0.0.255
ip access-list extended SITE-SITE-CACL_VLAN2
permit ip 192.168.30.0 0.0.0.255 192.168.20.0 0.0.0.255
This is the VPN configuration part for ASAV.
access-list TESTOUT extended permit ip 192.168.10.0 255.255.255.0 192.168.30.0 255.255.255.0
access-list TESTOUT extended permit ip 192.168.20.0 255.255.255.0 192.168.30.0 255.255.255.0
crypto ipsec ikev2 ipsec-proposal TEST1
protocol esp encryption 3des
protocol esp integrity sha-512
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 1 match address TESTOUT
crypto map CMAP 1 set peer 1.1.1.1
crypto map CMAP 1 set ikev2 ipsec-proposal TEST1
crypto map CMAP interface HQ_OUTBOUND
crypto ikev2 policy 1
encryption 3des
integrity sha256
group 2
prf sha256
lifetime seconds 86400
crypto ikev2 enable HQ_OUTBOUND
tunnel-group 1.1.1.1 type ipsec-l2l
tunnel-group 1.1.1.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
This is the debug crypto ikev2 from R3 when the negotiation failed.
*Oct 31 03:49:10.611: IKEv2:% Getting preshared key from profile keyring KR-R3
*Oct 31 03:49:10.615: IKEv2:% Matched peer block 'HQFW'
*Oct 31 03:49:10.619: IKEv2:Searching Policy with fvrf 0, local address 1.1.1.1
*Oct 31 03:49:10.619: IKEv2:Found Policy 'VPN'
*Oct 31 03:49:10.635: IKEv2:(SA ID = 1):Check for IPSEC rekey
*Oct 31 03:49:10.639: IKEv2:(SA ID = 1):Set IPSEC DH group
*Oct 31 03:49:10.639: IKEv2:(SA ID = 1):Checking for PFS configuration
*Oct 31 03:49:10.639: IKEv2:(SA ID = 1):PFS configured, DH group 2
*Oct 31 03:49:10.639: IKEv2:(SA ID = 1):[IKEv2 -> Crypto Engine] Computing DH public key, DH Group 2
*Oct 31 03:49:10.639: IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] DH key Computation PASSED
*Oct 31 03:49:10.639: IKEv2:(SA ID = 1):Request queued for computation of DH key
*Oct 31 03:49:10.639: IKEv2:(SA ID = 1):Generating CREATE_CHILD_SA exchange
*Oct 31 03:49:10.639: IKEv2:(SA ID = 1):ESP Proposal: 1, SPI size: 4 (IPSec negotiation),
Num. transforms: 4
R3#3DES SHA512 DH_GROUP_1024_MODP/Group 2 Don't use ESN
*Oct 31 03:49:10.639: IKEv2:(SA ID = 1):Building packet for encryption.
Payload contents:
SA N KE TSi TSr
*Oct 31 03:49:10.639: IKEv2:(SA ID = 1):Checking if request will fit in peer window
*Oct 31 03:49:10.639: IKEv2:(SA ID = 1):Sending Packet [To 2.2.2.2:500/From 1.1.1.1:500/VRF i0:f0]
Initiator SPI : 0DFB9D0B32B7BA3C - Responder SPI : E6A41CF831867435 Message id: 2
IKEv2 CREATE_CHILD_SA Exchange REQUEST
Payload contents:
ENCR
*Oct 31 03:49:10.659: IKEv2:(SA ID = 1):Received Packet [From 2.2.2.2:500/To 1.1.1.1:500/VRF i0:f0]
Initiator SPI : 0DFB9D0B32B7BA3C - Responder SPI : E6A41CF831867435 Message id: 2
IKEv2 CREATE_CHILD_SA Exchange RESPONSE
Payload contents:
NOTIFY(INVALID_KE_PAYLOAD)
*Oct 31 03:49:10.667: IKEv2:(SA ID = 1):Processing any notify-messages in child SA exchange
*Oct 31 03:49:10.667: IKEv2:(SA ID = 1):Processing invalid ke notification, we sent group 2, peer prefers gr
R3#oup 0
*Oct 31 03:49:10.667: IKEv2:(SA ID = 1):Unsupported DH group
*Oct 31 03:49:10.667: IKEv2:(SA ID = 1):
*Oct 31 03:49:10.671: IKEv2:(SA ID = 1):Error encountered while navigating State Machine
*Oct 31 03:49:10.671: IKEv2:(SA ID = 1):No Result Transition table avail for CHILD_I_PROC / EV_INV_KE with return code 0.0.0.11
seems like the output indicate that the DH group mismatch problem, but i didn't know where is going wrong.
Hope anyone can comment for it , Thanks.
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2019 02:50 AM
You are missing pfs on the ASA
ASA:
crypto map CMAP 1 match address TESTOUT
crypto map CMAP 1 set peer 1.1.1.1
crypto map CMAP 1 set ikev2 ipsec-proposal TEST1
crypto map CMAP interface HQ_OUTBOUND
R3:
crypto map CMAP-SITE 10 ipsec-isakmp
set peer 2.2.2.2
set transform-set SITE-TS
set pfs group2
set ikev2-profile SITE-PROFILE
match address SITE-SITE-CACL
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2019 09:22 PM
HI,
On R3 you have got 2 crypto map sequences for the same peer (2.2.2.2). Remove the second sequence and amend the ACL of the first entry to include both subnets.
e.g
no crypto map CMAP-SITE 20 ipsec-isakmp
ip access-list extended SITE-SITE-CACL
permit ip 192.168.30.0 0.0.0.255 192.168.10.0 0.0.0.255
permit ip 192.168.30.0 0.0.0.255 192.168.20.0 0.0.0.255
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2019 11:31 PM
The configuration I showed is the result of trial and error just trying to solve the issue but didn't.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2019 02:50 AM
You are missing pfs on the ASA
ASA:
crypto map CMAP 1 match address TESTOUT
crypto map CMAP 1 set peer 1.1.1.1
crypto map CMAP 1 set ikev2 ipsec-proposal TEST1
crypto map CMAP interface HQ_OUTBOUND
R3:
crypto map CMAP-SITE 10 ipsec-isakmp
set peer 2.2.2.2
set transform-set SITE-TS
set pfs group2
set ikev2-profile SITE-PROFILE
match address SITE-SITE-CACL
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2019 06:21 AM
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: