- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Using FlexVPN with RADIUS based keyring verification
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2018 03:25 AM - edited 03-12-2019 05:09 AM
Hello Gents,
searching about a discription and reference to use for my FlexVPN (with virt. Tunnle and BGP) keyring verification by RADIUS. User and/or Group authorization (AAA) part of the profile definition is clear for me. What not clear for me. How can the Keyring per peer requested to radius and get psk for particular peer.
How the router config need to look and the Radius as well.
Thanks
Greeting
Olaf
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2018 06:26 AM
- Create a Network Device Group e.g. FlexVPN-Router
- Define the FlexVPN Hub as a Network Access Device add to the group FlexVPN-Router
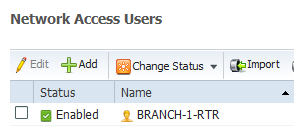
- Create User account on RADIUS server
- Create Authorization Profile
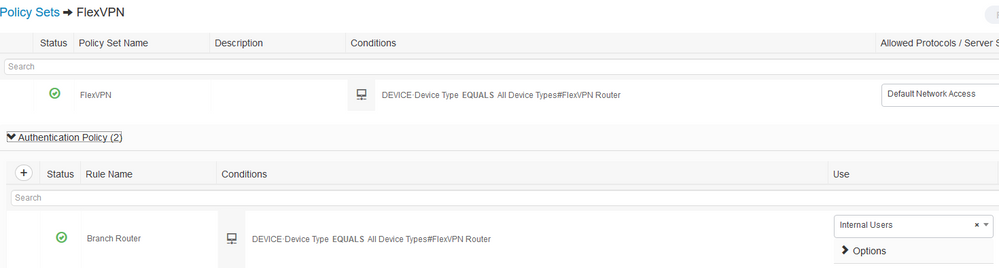
- Create Policy Set (use Network Device Group as condition to match Policy Set)
- Define Authentication Rule
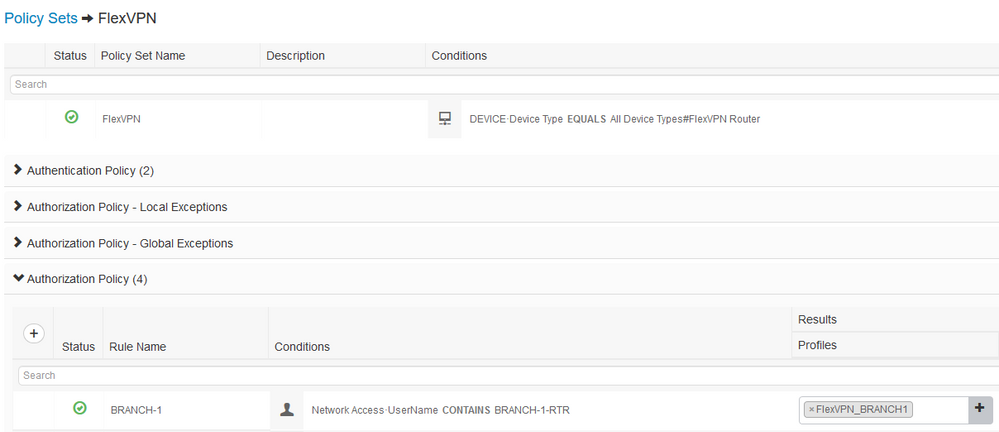
- Create Authorization Rule - reference the Authorization Profile previously created
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2018 05:00 AM
i misse dthe following:
Command exist under ikev2 profile as,
“keyring <aaa list name>”
Second of course aaa authentication command is necessary
Has someone experience with that setup and can share with me.
Important for he how the Radius configuration looks and how does it work combined with user/group authorization
Thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2018 02:14 PM - edited 03-29-2018 02:15 PM
Hi,
I'd never used radius for PSK authentication before, but was intrigued. I've spent sometime in my lab and got it working. In my lab the Hub authenticates itself to the spokes using a certificate but the spokes are authenticated using PSK which is via the radius server (ISE).
SPOKE
crypto ikev2 keyring KEYRING
peer ALL
address 0.0.0.0 0.0.0.0
pre-shared-key local Cisco1234
!
crypto ikev2 profile IKEV2_PROFILE
match identity remote fqdn domain lab.net
match certificate CERT_MAP
identity local fqdn BRANCH-1-RTR.lab.net
authentication local pre-share
authentication remote rsa-sig
keyring local KEYRING
pki trustpoint VPN_TP
dpd 10 2 on-demand
HUB
aaa new-model
aaa authorization network FLEX group ISE
aaa accounting network FLEX start-stop group ISE
!
crypto ikev2 name-mangler PSK
fqdn hostname
!
crypto ikev2 profile IKEV2_PROFILE
match identity remote fqdn domain lab.net
identity local dn
authentication remote pre-share
authentication local rsa-sig
keyring aaa FLEX name-mangler PSK password Cisco1234
pki trustpoint VPN_TP
aaa authorization user psk list FLEX name-mangler PSK password Cisco1234
aaa accounting psk FLEX
virtual-template 1 mode auto
The name-mangler extracts the hostname in this instance BRANCH-1-RTR, this is sent in the radius packet and needs to be defined on ISE as a User Account with a password specified as Cisco1234 - this password is specified in the ikev2 profile above, the default password if not defined is cisco btw.
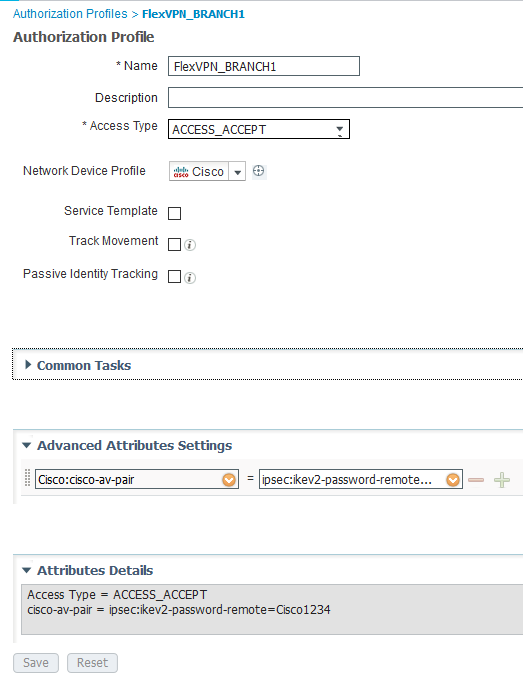
I then created an Authorization Profile with the following attribute - cisco-av-pair = ipsec:ikev2-password-remote=Cisco1234
The Authorization Policy rule matches on Calling Station ID (could match on the username previously defined) of the spoke router and returns the result of the Authorization Profile previously defined.
You create User accounts, Authorization Profile and Authorization Policy rules per spoke.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2018 05:51 AM
Hello RJI,
that sound good to me. And good to know that you have already tested. The password in the keyring authentication. I willst test it shorty when thje PoC is ready.
keyring aaa FLEX name-mangler PSK password Cisco1234
is only for the radius request. And the same for authorisation
aaa authorization user psk list FLEX name-mangler PSK password Cisco1234
So we know we have ones the IKEv2 negotiation authentication in the first phase (psw and ip or hostname). in the scond we have the user and or the group authentication for network credentials.
About the RADIUS what RADIUS attribut you have used for the authetication . Only user login?
Greeting
Olaf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2018 06:25 AM
So the password specified is for all AAA actions (authentication and authorization), it basically matches the password specified on the RADIUS server for the user account that needs to be created, this user account name is extracted via the name-mangler.
Not sure I undertstand your question, but for authentication PSK attribute "cisco-av-pair = ipsec:ikev2-password-remote" was used, that was matched on a per user basis, you could match on per group as long as you can differentiate between them, but per user would be more secure (as long as PSK different).
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2018 07:24 AM
Hello, yes I am totally agree.
Can you please share your radius credentials to verify if we are on the same page.
Thanks
Olaf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2018 06:26 AM
- Create a Network Device Group e.g. FlexVPN-Router
- Define the FlexVPN Hub as a Network Access Device add to the group FlexVPN-Router
- Create User account on RADIUS server
- Create Authorization Profile
- Create Policy Set (use Network Device Group as condition to match Policy Set)
- Define Authentication Rule
- Create Authorization Rule - reference the Authorization Profile previously created
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2018 06:39 AM
Thnaks for your support.
have a nice day
Greeting
Olaf
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide