- Cisco Community
- Technology and Support
- Security
- VPN
- Re: VPN Connectivity
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 07:48 AM
We currently have a VPN setup for our users when they are on the road or working from home using Cisco AnyConnect. We have the VPN setup on our ASA 5508 Firewall.
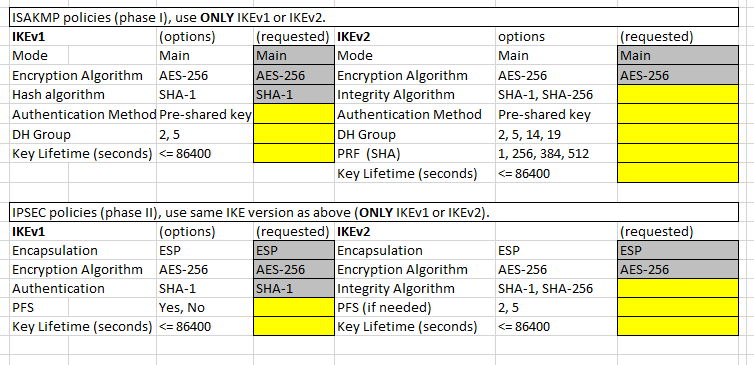
I now have a client that we send data to that needs us to setup a VPN for the connection. I was wondering if there was anyone out there that would be able to help me create the VPN (IKEv1 or IKEv2) and fill out this VPN questionnaire. Thank you in advance!!
Solved! Go to Solution.
- Labels:
-
IPSEC
-
Remote Access
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 10:34 AM
Okay, I ran the script successfully and see the changes in ASDM.
I tried to ping again to the two HOST addresses with no luck. I could successfully ping the PEER address, but I think that is just the public IP. Not sure why I am unable to ping HOSTs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 10:41 AM
You ran the ping from 10.0.0.3?
Did you renable the debug commands and was there any debug output in the SSH console?
Please provide the output of "show nat detail"
Run the command:- "packet-tracer input inside icmp 10.0.0.3 8 0 <comdata-ip>" from the CLI of the ASA, provide the output for review.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 10:33 AM
No, this rule applies only for traffic over the VPN to Comdata. No other traffic would match it and would match your existing rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 10:49 AM
I am running a continuous ping on my 10.0.0.3 machine but not seeing any output in Putty window, I ahve all logging enabled from earlier.
SHOW NAT DETAIL results:
WYNNE-ASA5508-X(config)# show nat detail
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static WYNNE-CORP WYNNE-CORP destination static IPPOOL IPPOOL no-proxy-arp route-lookup
translate_hits = 72672, untranslate_hits = 74474
Source - Origin: 10.0.0.0/24, 10.0.1.32/28, 10.0.1.0/29, 10.0.2.0/24, Translated: 10.0.0.0/24, 10.0.1.32/28, 10.0.1.0/29, 10.0.2.0/24
Destination - Origin: 192.168.100.0/24, Translated: 192.168.100.0/24
2 (any) to (outside) source dynamic IPPOOL interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.100.0/24, Translated: 63.147.191.66/29
3 (inside) to (outside) source static WYNNEAPPS1 WYNNEAPPS1 destination static COMDATA COMDATA no-proxy-arp
translate_hits = 15, untranslate_hits = 15
Source - Origin: 10.0.0.3/32, Translated: 10.0.0.3/32
Destination - Origin: 66.20.45.233/32, 66.20.45.234/32, Translated: 66.20.45.233/32, 66.20.45.234/32
Auto NAT Policies (Section 2)
1 (inside) to (outside) source static WYNNEAPPS1 63.147.191.67
translate_hits = 84297, untranslate_hits = 67654
Source - Origin: 10.0.0.3/32, Translated: 63.147.191.67/32
Manual NAT Policies (Section 3)
1 (inside) to (outside) source dynamic WYNNE-CORP interface
translate_hits = 1293622, untranslate_hits = 105166
Source - Origin: 10.0.0.0/24, 10.0.1.32/28, 10.0.1.0/29, 10.0.2.0/24, Translated: 63.147.191.66/29
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 10:52 AM
Result of the command: "packet-tracer input inside icmp 10.0.0.3 8 0 66.20.45.233"
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,outside) source static WYNNEAPPS1 WYNNEAPPS1 destination static COMDATA COMDATA no-proxy-arp
Additional Information:
NAT divert to egress interface outside
Untranslate 66.20.45.233/0 to 66.20.45.233/0
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group inside_access_in in interface inside
access-list inside_access_in extended permit ip any4 any4
Additional Information:
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,outside) source static WYNNEAPPS1 WYNNEAPPS1 destination static COMDATA COMDATA no-proxy-arp
Additional Information:
Static translate 10.0.0.3/0 to 10.0.0.3/0
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect icmp
service-policy global_policy global
Additional Information:
Phase: 8
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Phase: 9
Type: QOS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
service-policy global_policy global
Additional Information:
Phase: 10
Type: VPN
Subtype: encrypt
Result: DROP
Config:
Additional Information:
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 10:58 AM
The output of the NAT rules confirms traffic is translated and untranslated correctly
3 (inside) to (outside) source static WYNNEAPPS1 WYNNEAPPS1 destination static COMDATA COMDATA no-proxy-arp
translate_hits = 15, untranslate_hits = 15
Source - Origin: 10.0.0.3/32, Translated: 10.0.0.3/32
Destination - Origin: 66.20.45.233/32, 66.20.45.234/32, Translated: 66.xx.xx.233/32, 66.xx.xx.45.234/32
Check the commands "show crypto ikev2 sa" and "show crypto ipsec sa" from the CLI
Your configuration now looks ok from what I can tell, can you confirm with the other end if they troubleshoot with you?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 11:01 AM
Result of the command: "show crypto ikev2 sa"
There are no IKEv2 SAs
Result of the command: "show crypto ipsec sa"
There are no ipsec sas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 11:47 AM
So debugs are still enabled when you run the ping? And no output?
Does the peer see any traffic or the VPN attempt to establish?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 12:02 PM
This is from the peer that I am working with "I am not seeing any traffic at all the tunnel is not attempting to build even phase 1. "
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 01:27 PM
Not sure why I'm not getting any debug messages in Putty window. Do I need to turn on debugging somewhere else?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 01:52 PM - edited 10-22-2020 01:53 PM
You are connected to the ASA using SSH right? and not with a console cable?
If you have the logging enable, which I believe you do and you do not see anything in the logs, then it is possible that the VPN does not even activate. Which could mean your ACL is incorrect, is the source IP address of the WYNNEAPP server correct? Are the destination IP addresses correct?
Are you testing from the IP address (10.0.0.3) that is defined in the crypto ACL?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 01:56 PM
Yes, I am connected to the ASA using Putty SSH
I am using the correct IP for WYNNEAPPS1, which is 10.0.0.3. I have entered the two HOST addresses as Network Objects and also created a Network Group called COMDATA which includes the two HOST addresses. I did all this in ASDM.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2020 04:28 AM
If you try the packet-tracer command twice, does it still show VPN DROP at Phase 10? if so, might be that the remote peer is configured to be originate-only?, also, can you please try to disable and re-enable IKEv2 on the outside interface and try again?
no crypto ikev2 enable outside crypto ikev2 enable outside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2020 07:48 AM
I ran the Packet Tracer twice. Here are the results:
Result of the command: "packet-tracer input inside icmp 10.0.0.3 8 0 66.20.45.233"
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,outside) source static WYNNEAPPS1 WYNNEAPPS1 destination static COMDATA COMDATA no-proxy-arp
Additional Information:
NAT divert to egress interface outside
Untranslate 66.20.45.233/0 to 66.20.45.233/0
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group inside_access_in in interface inside
access-list inside_access_in extended permit ip any4 any4
Additional Information:
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,outside) source static WYNNEAPPS1 WYNNEAPPS1 destination static COMDATA COMDATA no-proxy-arp
Additional Information:
Static translate 10.0.0.3/0 to 10.0.0.3/0
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect icmp
service-policy global_policy global
Additional Information:
Phase: 8
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Phase: 9
Type: QOS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
service-policy global_policy global
Additional Information:
Phase: 10
Type: VPN
Subtype: encrypt
Result: DROP
Config:
Additional Information:
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
Result of the command: "packet-tracer input inside icmp 10.0.0.3 8 0 66.20.45.233"
Phase: 1
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,outside) source static WYNNEAPPS1 WYNNEAPPS1 destination static COMDATA COMDATA no-proxy-arp
Additional Information:
NAT divert to egress interface outside
Untranslate 66.20.45.233/0 to 66.20.45.233/0
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group inside_access_in in interface inside
access-list inside_access_in extended permit ip any4 any4
Additional Information:
Phase: 3
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,outside) source static WYNNEAPPS1 WYNNEAPPS1 destination static COMDATA COMDATA no-proxy-arp
Additional Information:
Static translate 10.0.0.3/0 to 10.0.0.3/0
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect icmp
service-policy global_policy global
Additional Information:
Phase: 7
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: QOS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
service-policy global_policy global
Additional Information:
Phase: 9
Type: VPN
Subtype: encrypt
Result: DROP
Config:
Additional Information:
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2020 09:46 AM
Can you confirm with the 3rd party that they've configured their crypto ACL to mirror yours? You are permitting traffic from 10.0.0.3 to their 2 ip addresses, they need the exact mirror opposite of what you've defined. Source from their 2 ip addresses to your IP address 10.0.0.3. If these are mismatched this usually causes issues in stopping a VPN establishing.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: