- Cisco Community
- Technology and Support
- Security
- VPN
- VPN Connectivity
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 07:48 AM
We currently have a VPN setup for our users when they are on the road or working from home using Cisco AnyConnect. We have the VPN setup on our ASA 5508 Firewall.
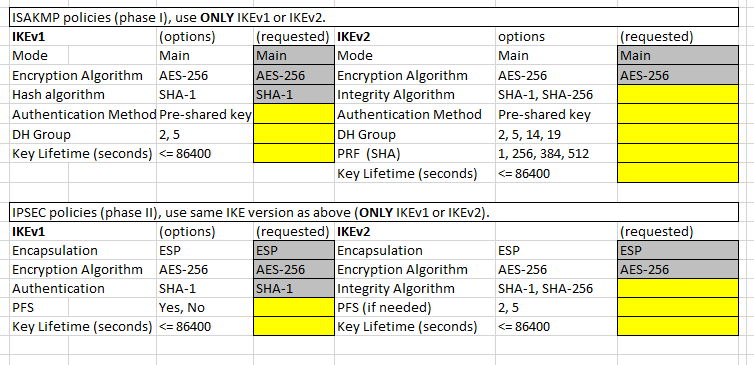
I now have a client that we send data to that needs us to setup a VPN for the connection. I was wondering if there was anyone out there that would be able to help me create the VPN (IKEv1 or IKEv2) and fill out this VPN questionnaire. Thank you in advance!!
Solved! Go to Solution.
- Labels:
-
IPSEC
-
Remote Access
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 06:57 AM
Result of the command: "show crypto ikev2 sa"
IKEv2 SAs:
Session-id:4, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
534010501 63.147.191.66/500 148.59.168.18/500 READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA96, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/25 sec
Child sa: local selector 10.0.0.3/0 - 10.0.0.3/65535
remote selector 66.20.45.233/0 - 66.20.45.233/65535
ESP spi in/out: 0x743c7f5e/0xbc1ef07f
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 07:00 AM
Awesome, that's a start, almost there. Run "show crypto ipsec sa" - if there is an output then the tunnel is up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 07:03 AM
Result of the command: "show crypto ipsec sa"
interface: outside
Crypto map tag: wynnemap, seq num: 1, local addr: 63.147.191.66
access-list outside_cryptomap extended permit ip host 10.0.0.3 host 66.20.45.233
local ident (addr/mask/prot/port): (10.0.0.3/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (66.20.45.233/255.255.255.255/0/0)
current_peer: 148.59.168.18
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 63.147.191.66/500, remote crypto endpt.: 148.59.168.18/500
path mtu 1500, ipsec overhead 78(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: BC1EF07F
current inbound spi : 743C7F5E
inbound esp sas:
spi: 0x743C7F5E (1950121822)
SA State: active
transform: esp-aes-256 esp-sha-256-hmac no compression
in use settings ={L2L, Tunnel, IKEv2, }
slot: 0, conn_id: 111308800, crypto-map: wynnemap
sa timing: remaining key lifetime (kB/sec): (4285440/28361)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0xBC1EF07F (3156144255)
SA State: active
transform: esp-aes-256 esp-sha-256-hmac no compression
in use settings ={L2L, Tunnel, IKEv2, }
slot: 0, conn_id: 111308800, crypto-map: wynnemap
sa timing: remaining key lifetime (kB/sec): (4239360/28361)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 07:20 AM
Well the IPSec SA has been formed, but no packets have been encrypted or decrypted.
Can you run the ping from WYNNEAPP1 please and then provide the output from "show crypto ipec sa"
Can you also provide the output from "show nat detail" please.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 07:24 AM
The pings worked successfully!!
Result of the command: "show crypto ipsec sa"
interface: outside
Crypto map tag: wynnemap, seq num: 1, local addr: 63.147.191.66
access-list outside_cryptomap extended permit ip host 10.0.0.3 host 66.20.45.233
local ident (addr/mask/prot/port): (10.0.0.3/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (66.20.45.233/255.255.255.255/0/0)
current_peer: 148.59.168.18
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 4, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 63.147.191.66/500, remote crypto endpt.: 148.59.168.18/500
path mtu 1500, ipsec overhead 78(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: BC1EF07F
current inbound spi : 743C7F5E
inbound esp sas:
spi: 0x743C7F5E (1950121822)
SA State: active
transform: esp-aes-256 esp-sha-256-hmac no compression
in use settings ={L2L, Tunnel, IKEv2, }
slot: 0, conn_id: 111308800, crypto-map: wynnemap
sa timing: remaining key lifetime (kB/sec): (4285439/27117)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x0000001F
outbound esp sas:
spi: 0xBC1EF07F (3156144255)
SA State: active
transform: esp-aes-256 esp-sha-256-hmac no compression
in use settings ={L2L, Tunnel, IKEv2, }
slot: 0, conn_id: 111308800, crypto-map: wynnemap
sa timing: remaining key lifetime (kB/sec): (4239359/27117)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: wynnemap, seq num: 1, local addr: 63.147.191.66
access-list outside_cryptomap extended permit ip host 10.0.0.3 host 66.20.45.234
local ident (addr/mask/prot/port): (10.0.0.3/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (66.20.45.234/255.255.255.255/0/0)
current_peer: 148.59.168.18
#pkts encaps: 3, #pkts encrypt: 3, #pkts digest: 3
#pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 3, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 63.147.191.66/500, remote crypto endpt.: 148.59.168.18/500
path mtu 1500, ipsec overhead 78(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 157B7E65
current inbound spi : 5CFCABB5
inbound esp sas:
spi: 0x5CFCABB5 (1560062901)
SA State: active
transform: esp-aes-256 esp-sha-256-hmac no compression
in use settings ={L2L, Tunnel, IKEv2, }
slot: 0, conn_id: 111308800, crypto-map: wynnemap
sa timing: remaining key lifetime (kB/sec): (4239359/28735)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x0000000F
outbound esp sas:
spi: 0x157B7E65 (360414821)
SA State: active
transform: esp-aes-256 esp-sha-256-hmac no compression
in use settings ={L2L, Tunnel, IKEv2, }
slot: 0, conn_id: 111308800, crypto-map: wynnemap
sa timing: remaining key lifetime (kB/sec): (4193279/28735)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Result of the command: "show nat detail"
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static WYNNEAPPS1 WYNNEAPPS1 destination static COMDATA COMDATA no-proxy-arp route-lookup
translate_hits = 15, untranslate_hits = 15
Source - Origin: 10.0.0.3/32, Translated: 10.0.0.3/32
Destination - Origin: 66.20.45.233/32, 66.20.45.234/32, Translated: 66.20.45.233/32, 66.20.45.234/32
2 (inside) to (outside) source static WYNNE-CORP WYNNE-CORP destination static IPPOOL IPPOOL no-proxy-arp route-lookup
translate_hits = 115199, untranslate_hits = 119284
Source - Origin: 10.0.0.0/24, 10.0.1.32/28, 10.0.1.0/29, 10.0.2.0/24, Translated: 10.0.0.0/24, 10.0.1.32/28, 10.0.1.0/29, 10.0.2.0/24
Destination - Origin: 192.168.100.0/24, Translated: 192.168.100.0/24
3 (any) to (outside) source dynamic IPPOOL interface
translate_hits = 1, untranslate_hits = 2
Source - Origin: 192.168.100.0/24, Translated: 63.147.191.66/29
Auto NAT Policies (Section 2)
1 (inside) to (outside) source static WYNNEAPPS1 63.147.191.67
translate_hits = 183269, untranslate_hits = 155167
Source - Origin: 10.0.0.3/32, Translated: 63.147.191.67/32
Manual NAT Policies (Section 3)
1 (inside) to (outside) source dynamic WYNNE-CORP interface
translate_hits = 2347387, untranslate_hits = 190197
Source - Origin: 10.0.0.0/24, 10.0.1.32/28, 10.0.1.0/29, 10.0.2.0/24, Translated: 63.147.191.66/29
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 07:28 AM
Yep, looks like ping is working to both comdata IP addresses and traffic is hitting the correct NAT exemption rule.
Looks like you should be good to go now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 07:37 AM
Thanks for all your help. Great learning for me. I appreciate it. I'll let you know if I have any further questions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 03:09 AM
Awesome and you are very welcome! Really glad we could help, it's been a bit a challenging one :). If you can mark the posts that you think they answered your queries please, that would help people to save reading the whole pages of this thread.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2020 03:34 PM
Good spot @Aref Alsouqi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2020 08:29 AM
It seems the VPN connection went down. However, I have not made any changes are even logged into ASDM since we had it working. Any ideas what could have changed it? Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2020 09:14 AM
The VPN will terminate if no traffic has been sent over the tunnel, however it should automatically establish again once traffic is sent.
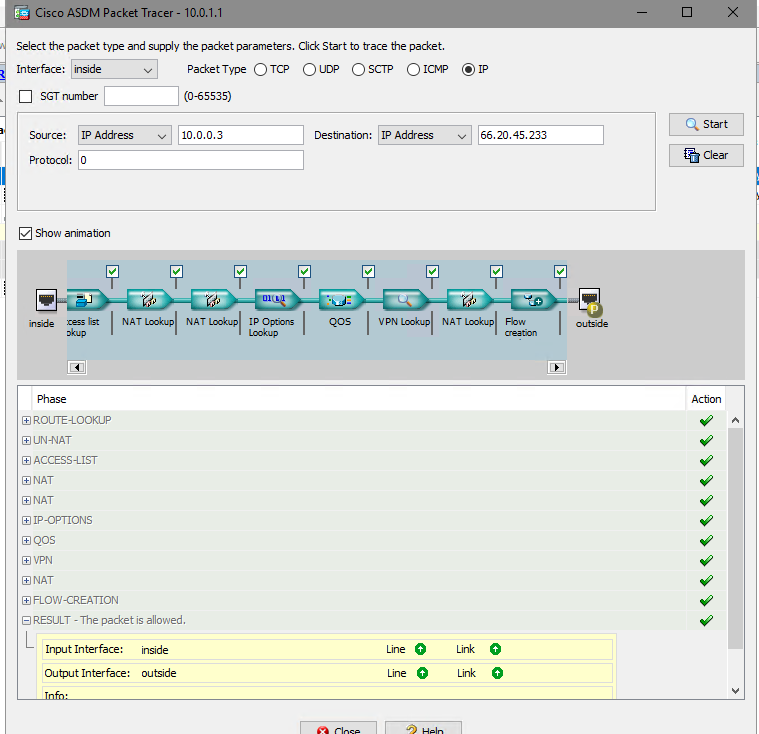
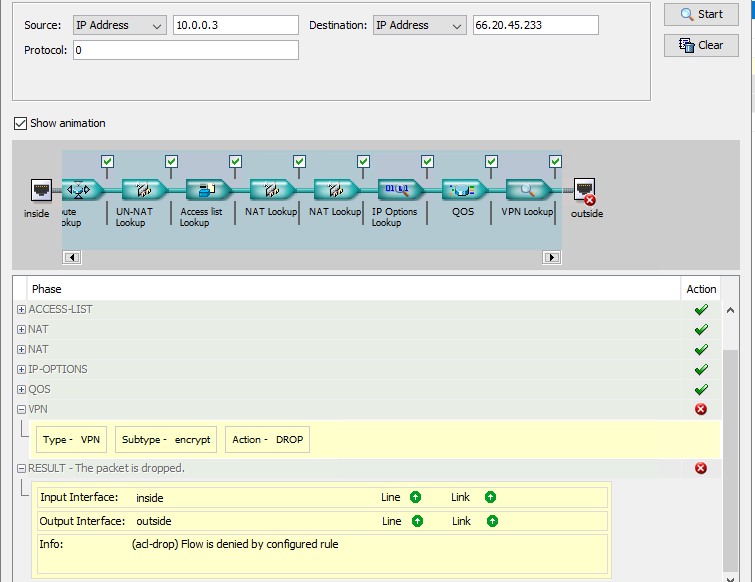
Can you run packet-tracer from the CLI and upload the output please.
Can you also run "show crypto ipsec sa" on the CLI and upload the output.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2020 09:22 AM
Looks like the VPN came back up. So if there is no traffic being passed the VPN will go down? How does it start back up?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2020 09:28 AM
Correct, the tunnel will drop if no traffic is sent over the tunnel and the timers expire.
It starts back up automatically once there is "interesting traffic" being sent over the tunnel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2020 03:33 PM
Also, please keep in mind that first time you run the packet-tracer, it might fail, I would always run it twice. Reason of this is because sometimes the tunnel might take some time before it is fully established so first packet would not go through.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2020 01:04 PM
Our VPN keeps going down and when I login to ASDM, it seems my settings got wiped out specifically just for this VPN and NAT rules. It had been working fine, so not sure how to troubleshoot this. Any ideas?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: