- Cisco Community
- Technology and Support
- Security
- VPN
- VPN Connectivity
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 07:48 AM
We currently have a VPN setup for our users when they are on the road or working from home using Cisco AnyConnect. We have the VPN setup on our ASA 5508 Firewall.
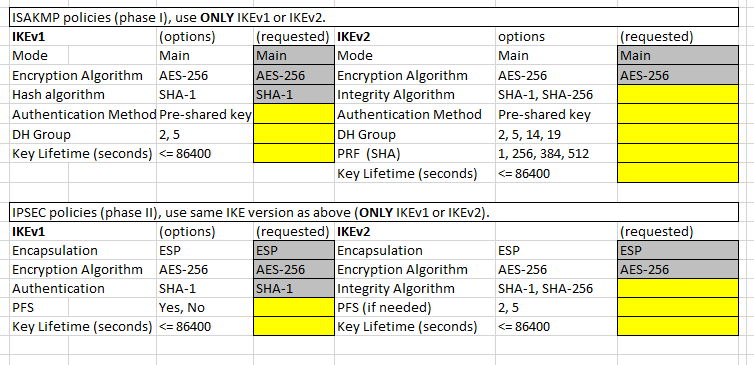
I now have a client that we send data to that needs us to setup a VPN for the connection. I was wondering if there was anyone out there that would be able to help me create the VPN (IKEv1 or IKEv2) and fill out this VPN questionnaire. Thank you in advance!!
Solved! Go to Solution.
- Labels:
-
IPSEC
-
Remote Access
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2020 06:29 AM
Yes, you don't need configure any certificate information.
Obviously that pre-shared keys needs to be the same key used by the peer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2020 06:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2020 06:38 AM
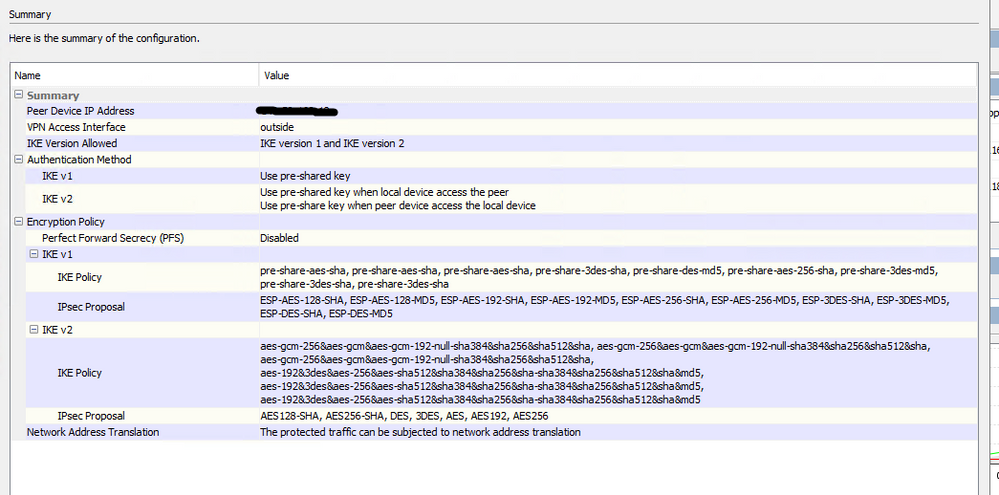
Ok, well you've selected all ciphers for IKEv1 and IKEv2, so it's bound to match one of them!!!
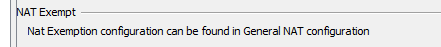
Did you create a NAT exemption rule to ensure traffic from your local network to the remote networks (those 2 ip addresses) are not natted?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2020 06:42 AM
No, I did not create NAT exemption rule. What should that look like?
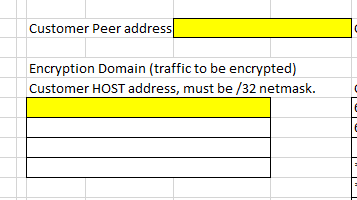
Also, They are wanting our IP address, which I believe is our Public IP. And then our HOST address, not sure what this is?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2020 06:58 AM
Correct, the public IP address.
The host address is the private IP address(es) of the computers accessing the peer network, which would be your internal/inside networks. It looks like they want each individual IP address (which is what a /32 represents). So for example if you have 5 computers accessing their VPN, you will define 5 host ip addresses in a network object. Your configuration needs to match exactly what they've configured.
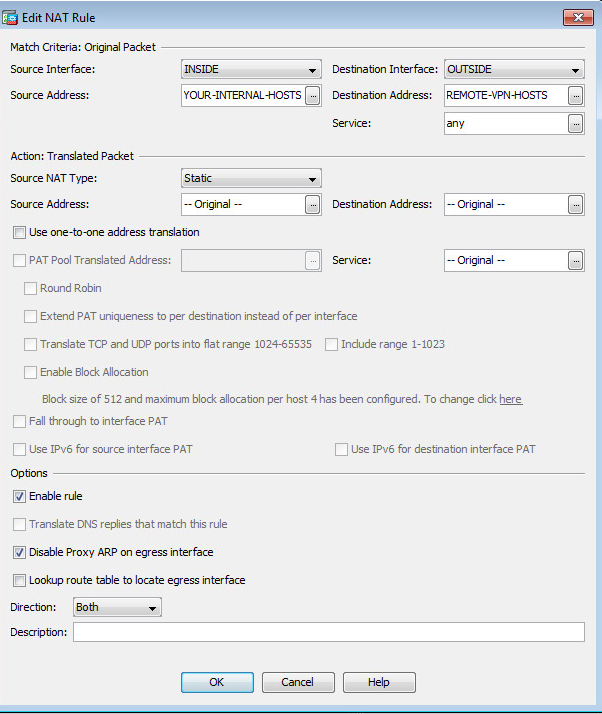
NAT Exemption rule would look something like this:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2020 07:10 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2020 07:17 AM - edited 10-14-2020 07:21 AM
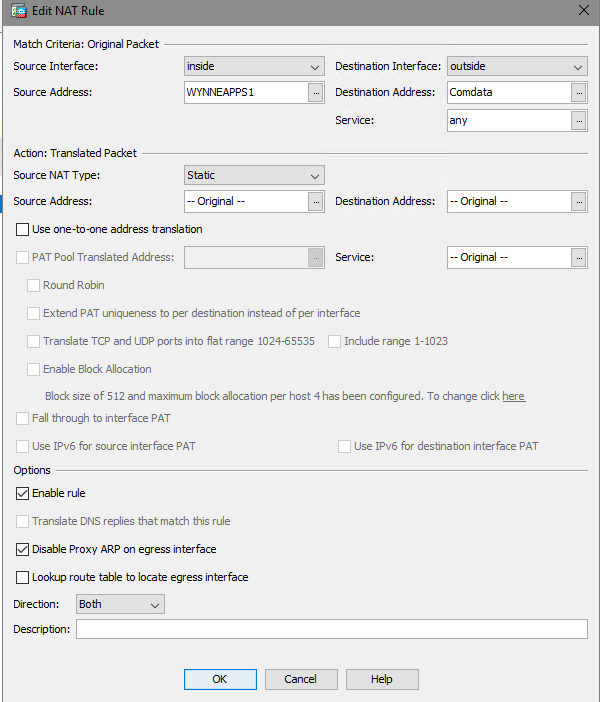
Ok, looks ok. So as long as "wynneapps1" represents the host(s) on your internal network and "Comdata" represents the hosts on the remote network, then this traffic would not be natted.
You'll need to ensure you are using those objects in the configuration of the VPN, these host objects should mirror the peers configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2020 07:23 AM
Okay, thanks for all your help! I will send the info over to them so they can test. I'll let you know how it goes or if I have any additional questions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2020 07:33 AM
So now that I have the VPN all configured on my Firewall, how do I test the VPN connection is working? I was thinking just ping the IP addresses, is that correct? Or is there another way to test the VPN connection?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2020 07:38 AM
Yes, run a ping from WYNNEAPP1 to Comdata IP address
If the ping doesn't work, from the CLI run "show crypto ipsec sa" and provide the output for review.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2020 07:43 AM
I was unable to ping 2 of the IP addresses.
Here is the output from the CLI "show crypto ipsec sa"
There are no ipsec sas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2020 07:50 AM
Ok, I assume there is no output from "show crypto ikev2 sa" either?
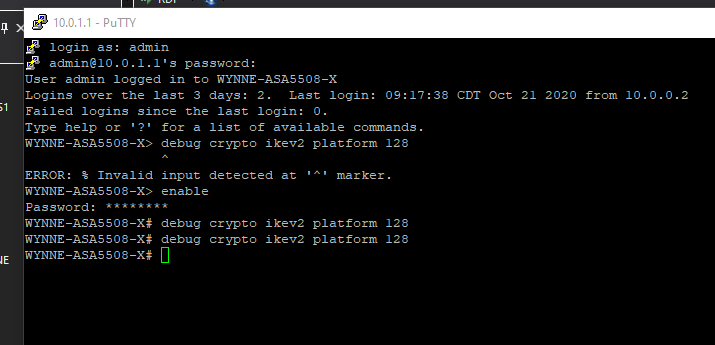
Can you turn on debugs "debug crypto ikev2 platform 128", "debug crypto ikev2 protocol 128" and provide the output for review please.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2020 07:55 AM
Yes same thing on "show crypto ikev2 sa": There are no IKEv2 SAs
Not getting anything on debug
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2020 08:00 AM
Sorry, I wasn't clear. After you entered those 2 debug commands, run the ping again. This will hopefully generate traffic and attempt to establish a VPN tunnel, this should provide a load of debug messages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2020 08:04 AM
I ran those 2 commands again and then tried to ping. Where will I find the debug messages?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: