- Cisco Community
- Technology and Support
- Security
- VPN
- VPN Tunnel between Cisco ISR and RV134W Routers
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN Tunnel between Cisco ISR and RV134W Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 01:08 AM
I am having an issue getting a tunnel properly working between the two routers. The router at the main office is an ISR 1921 and the remote location has RV134W. I have an IPSec Site-to-site VPN configured between the two, which is all up but not fully as I cannot ping any of the endpoints from either end. If I am at a remote location, I can ping the main router find and from the main location I can ping the remote router via their local IPs, but nothing else.
Any ideas?
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 01:33 AM
could you please share the output of these command from both routers.
show crypto isakmp sa
show crypto ipsec sa
one think i suggest to make sure you have correct routing in place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 01:41 AM
Please see the output below. Let me know if there is anything else you may need!
IPv4 Crypto ISAKMP SA
dst src state conn-id status
84.45.x.x 87.127.x.x QM_IDLE 1429 ACTIVE
IPv6 Crypto ISAKMP SA
interface: Dialer1
Crypto map tag: vpn, local addr 84.45.x.x
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.3.0/255.255.255.0/0/0)
current_peer 87.127.x.x port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 329, #pkts encrypt: 329, #pkts digest: 329
#pkts decaps: 501, #pkts decrypt: 501, #pkts verify: 501
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 84.45.x.x, remote crypto endpt.: 87.127.x.x
plaintext mtu 1438, path mtu 1492, ip mtu 1492, ip mtu idb Dialer1
current outbound spi: 0x73F508FA(1945438458)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x1C7823DF(477635551)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 3165, flow_id: Onboard VPN:1165, sibling_flags 80000040, crypto map: vpn
sa timing: remaining key lifetime (k/sec): (4299505/936)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x73F508FA(1945438458)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 3166, flow_id: Onboard VPN:1166, sibling_flags 80000040, crypto map: vpn
sa timing: remaining key lifetime (k/sec): (4299544/936)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.10.3.0/255.255.255.0/0/0)
current_peer 87.127.x.x port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 84.45.x.x remote crypto endpt.: 87.127.x.x
plaintext mtu 1438, path mtu 1492, ip mtu 1492, ip mtu idb Dialer1
current outbound spi: 0x6A394328(1782137640)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x8E6643C6(2389066694)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 3167, flow_id: Onboard VPN:1167, sibling_flags 80000040, crypto map: vpn
sa timing: remaining key lifetime (k/sec): (4234055/936)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x6A394328(1782137640)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 3168, flow_id: Onboard VPN:1168, sibling_flags 80000040, crypto map: vpn
sa timing: remaining key lifetime (k/sec): (4234055/936)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 01:48 AM
the output you showed is the main router or the branch router.
could you get the similar from the other side also.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 02:00 AM
That was the 1921 router at the main site.
I am attaching a screenshot from the other location:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 05:08 AM - edited 01-04-2019 05:08 AM
Considering the output of Show crypto Ipsec sa on the 2911 Router, It looks like you didnt configure the DH Group yet you configured Group 2 on the RV134W.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 05:18 AM
No, I did, here is the config from the 1921:
crypto isakmp policy 1 encr 3des hash md5 authentication pre-share group 2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 05:31 AM
Can we please have a look at the access rules (access-lists) and routing on both sides ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 05:48 AM
your access-list on both routers looks good.
could you please confirm what is the setup like. i believe, Branch router is connected to internet and on this router you have a vpn to you head office (main branch office). what routing protocols you have or you have a static route.
can you test and make sure the connectivity is there. from a client pc can you ping to its default router and so on the same other side.
can you share the config of both routers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 05:38 AM
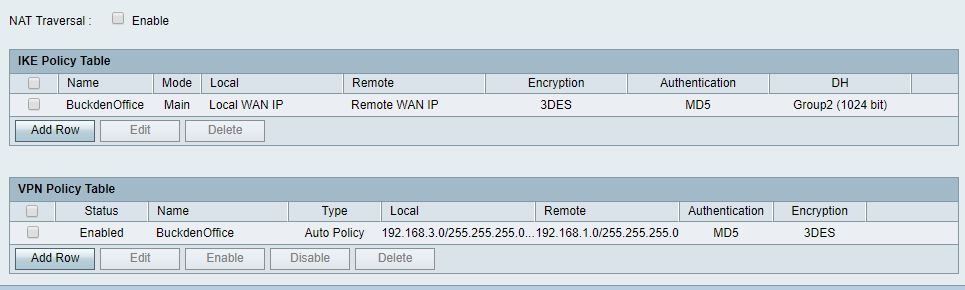
So for now I have removed the 10.10.3.0/24 subnet out of the equation, just to see if that makes a difference but it has not. See the screenshots from the Cisco RV134:
Here are the bits from the 1921 router:
Extended IP access list NAT
10 deny ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255 (19095 matches)
20 deny ip 192.168.1.0 0.0.0.255 10.10.3.0 0.0.0.255 (23 matches)
30 deny ip 10.10.1.0 0.0.0.255 10.10.3.0 0.0.0.255 (10 matches)
40 deny ip 10.10.1.0 0.0.0.255 192.168.3.0 0.0.0.255
90 permit ip any any (228233 matches)
Extended IP access list vpn-tunnel
10 permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255 (17007 matches)
Routing part
Gateway of last resort is 0.0.0.0 to network 0.0.0.0
S* 0.0.0.0/0 is directly connected, Dialer1
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.10.1.0/24 is directly connected, GigabitEthernet0/1.100
L 10.10.1.254/32 is directly connected, GigabitEthernet0/1.100
78.0.0.0/32 is subnetted, 1 subnets
C 78.33.x.x is directly connected, Dialer1
84.0.0.0/32 is subnetted, 1 subnets
C 84.45.x.x is directly connected, Dialer1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, GigabitEthernet0/1
L 192.168.1.254/32 is directly connected, GigabitEthernet0/1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 05:55 AM
The Routing on the the RV134W is a bit confusing, As per the result of the show crypto ipsec sa ... The Gateway at e RV134W should be 87.127.x.x but as per the routing on the RV134W is looks like it is 78.33.x.x and I am also seeing another route(ip route 78.33.x.x 255.255.255.255 87.127.X.X on RV134W ). It is a bit confusing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 06:03 AM
on the earlier post if you see in ipsec the peer ip addresses are
local crypto endpt.: 84.45.x.x, remote crypto endpt.: 87.127.x.x
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 05:59 AM - edited 01-04-2019 06:26 AM
let get to the process of elimination.
1. we can see the phase 1 on both side.
2. your access-list is correct.
3. confirm to us that PC-x can ping to the default gateway and same from router can ping the PC-x. (To be confirm by you).
4. if there is in between swtiches/SVI or router make sure the ip routing/route exist.
=====================================================================
I beleive this is a Main router. and here its config are what you showed us.
IPv4 Crypto ISAKMP SA
dst src state conn-id status
84.45.x.x 87.127.x.x QM_IDLE 1429 ACTIVE
IPv6 Crypto ISAKMP SA
interface: Dialer1
Crypto map tag: vpn, local addr 84.45.x.x
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.3.0/255.255.255.0/0/0)
current_peer 87.127.x.x port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 329, #pkts encrypt: 329, #pkts digest: 329
#pkts decaps: 501, #pkts decrypt: 501, #pkts verify: 501
here the traffic is encap and decap happening. but you never showed us what is the state of other side of the router.
can you give it a similar command show crypto ipsec sa and show crypto isakmp sa
Main router see the peer ip as 87.127.x.x
what does it other router show you?
if possible you can share the config on both router and hide sensitive information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 06:29 AM
So for now I have removed the 10.10.3.0/24 subnet out of the equation, just to see if that makes a difference but it has not. See the screenshots from the Cisco RV134:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 06:31 AM
Here are the bits from the 1921 router:
Extended IP access list NAT
10 deny ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255 (19095 matches)
20 deny ip 192.168.1.0 0.0.0.255 10.10.3.0 0.0.0.255 (23 matches)
30 deny ip 10.10.1.0 0.0.0.255 10.10.3.0 0.0.0.255 (10 matches)
40 deny ip 10.10.1.0 0.0.0.255 192.168.3.0 0.0.0.255
90 permit ip any any (228233 matches)
Extended IP access list vpn-tunnel
10 permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255 (17007 matches)
Routing part
Gateway of last resort is 0.0.0.0 to network 0.0.0.0
S* 0.0.0.0/0 is directly connected, Dialer1
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.10.1.0/24 is directly connected, GigabitEthernet0/1.100
L 10.10.1.254/32 is directly connected, GigabitEthernet0/1.100
78.0.0.0/32 is subnetted, 1 subnets
C 78.33.x.x is directly connected, Dialer1
84.0.0.0/32 is subnetted, 1 subnets
C 84.45.x.x is directly connected, Dialer1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, GigabitEthernet0/1
L 192.168.1.254/32 is directly connected, GigabitEthernet0/1
I can ping from both ends to the remote location's routers but endpoint cannot ping another endpoint.
So if I am on a remote computer on IP 192.168.3.107 I can then ping 192.168.1.254 (1921 router) but cannot ping 192.168.1.1. If I am on 192.168.1.1, I can ping 192.168.3.254 (rv134 router).
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: