- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- AP (bridge mode) not joining WLC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2016 09:03 AM - edited 07-05-2021 06:16 AM
Hello,
i'm having issues configuring one of my APs in Bridge mode.
After switching the mode to "Bridge" the AP cannot join the WLC anymore. (added the MAC of the AP to the AP Authorization List)
But to start out, here a Little Setup of what i'm trying to do:
WLC-----|Switch|------|AP| - - - (~10meters) - - - - |AP|-------|Switch|
I am testing with an "AIR-CAP2702I-E-K9" at the Moment for testing puroses ( I will use an "AIR-CAP1532E-E-K9" later on).
Before i can Switch the AP mode in my wlc to Bridge (or Flex/Bridge) i have to set the RF Channel Assignment and the TX Power Level Assignment manually. After this i can Switch the AP to Bridge but in the process of rebooting we cannot join the WLC anymore.
Quick HW specs:
AP: AIR-CAP2702I-E-K9 | SW-Version: 8.0.120.0
WLC: AIR-CT5508-K9 | SW-Version: 8.0.120.0
Error on AP:
IOS Software, C2700 Software (AP3G2-K9W8-M), Version 15.3(3)JA4, RELEASE SOFTWARE (fc1)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2015 by Cisco Systems, Inc.
Compiled Wed 01-Jul-15 18:19 by prod_rel_team
*Mar 1 00:00:35.847: %SNMP-5-COLDSTART: SNMP agent on host AP843d.c64e.1d48 is undergoing a cold start
*Dec 19 07:44:33.031: Warning: Failed to run startup script
*Dec 19 07:44:34.123: %LINEPROTO-5-UPDOWN: Line protocol on Interface BVI1, changed state to up
*Dec 19 07:44:34.735: [m102x_set_lanport_config] Cannot enable AUX port while POE, connect AC or Inj source
*Dec 19 07:44:35.151: %LINK-6-UPDOWN: Interface Dot11Radio0, changed state to up
*Dec 19 07:44:35.151: %LINK-5-CHANGED: Interface GigabitEthernet1, changed state to administratively down
*Dec 19 07:44:35.167: Starting Ethernet promiscuous modelwapp_crypto_init: MIC Present and Parsed Successfully
*Dec 19 07:44:35.307: %SSH-5-ENABLED: SSH 2.0 has been enabled
*Dec 19 07:44:35.307: %LINK-6-UPDOWN: Interface Dot11Radio1, changed state to up
*Dec 19 07:44:36.359: %LINEPROTO-5-UPDOWN: Line protocol on Interface Dot11Radio0, changed state to down
*Dec 19 07:44:36.359: %LINEPROTO-5-UPDOWN: Line protocol on Interface Dot11Radio1, changed state to down
*Dec 19 07:44:45.227: %LINK-6-UPDOWN: Interface BVI1, changed state to down
*Dec 19 07:44:46.307: %LINEPROTO-5-UPDOWN: Line protocol on Interface BVI1, changed state to down
flash:/mesh_start_cfg.txt: No such file or directoryThe filesystem containing the variables may not be initialized yet.
*Dec 19 07:44:48.079: %SOAP_FIPS-2-SELF_TEST_HW_SUCCESS: HW crypto FIPS self test passed (2-16)
*Dec 19 07:44:48.079: DPAA Initialization Complete
*Dec 19 07:44:48.079: %SYS-3-HARIKARI: Process DPAA INIT top-level routine exited
*Dec 19 07:44:48.079: No Mesh startup file found
*Dec 19 07:44:49.079: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0, changed state to up
*Dec 19 07:44:51.083: %LINK-6-UPDOWN: Interface BVI1, changed state to up
*Dec 19 07:44:51.515: Currently running a Release Image
*Dec 19 07:44:51.935: Using SHA-2 signed certificate for image signing validation.
*Dec 19 07:44:52.223: %LINEPROTO-5-UPDOWN: Line protocol on Interface BVI1, changed state to up
*Dec 19 07:44:58.247: APAVC: Succeeded to activate all the STILE protocols.
*Dec 19 07:44:58.247: APAVC: Registering with CFT
*Dec 19 07:44:58.247: APAVC: CFT registration of delete callback succeeded
*Dec 19 07:44:58.247: APAVC: Reattaching Original Buffer pool for system use
*Dec 19 07:44:58.247: Pool-ReAtach: paks 42878 radio42270
*Dec 19 07:45:05.743: %SYS-6-LOGGINGHOST_STARTSTOP: Logging to host 255.255.255.255 port 0 CLI Request Triggered
*Dec 19 07:45:05.747: %LINK-5-CHANGED: Interface Dot11Radio0, changed state to reset
*Dec 19 07:45:05.747: %LINK-5-CHANGED: Interface Dot11Radio1, changed state to reset
*Dec 19 07:45:11.727: %CDP_PD-4-POWER_OK: 15.4 W power - NEGOTIATED inline power source
*Dec 19 07:45:12.827: %LINK-6-UPDOWN: Interface Dot11Radio0, changed state to up
*Dec 19 07:45:13.827: %LINEPROTO-5-UPDOWN: Line protocol on Interface Dot11Radio0, changed state to up
*Dec 19 07:45:14.087: %LINK-6-UPDOWN: Interface Dot11Radio1, changed state to up
*Dec 19 07:45:14.739: %MESH-6-ADJACENCY_STATE_MACHINE_STARTED: Mesh adjacency state machine started
*Dec 19 07:45:15.087: %LINEPROTO-5-UPDOWN: Line protocol on Interface Dot11Radio1, changed state to up
Not in Bound state.
*Dec 19 07:45:49.359: %MESH-6-CAPWAP_RESTART: Mesh Capwap re-started
*Dec 19 07:45:52.371: %LWAPP-3-LWAPP_INTERFACE_GOT_IP_ADDRESS: Interface BVI1 obtained IP from DHCP...
*Dec 19 07:45:52.371: %MESH-6-CAPWAP_RESTART: Mesh Capwap re-started
*Dec 19 07:45:52.431: %DHCP-6-ADDRESS_ASSIGN: Interface BVI1 assigned DHCP address 10.14.50.103, mask 255.255.254.0, hostname AP843d.c64e.1d48
*Dec 19 07:45:52.431: %LWAPP-3-LWAPP_INTERFACE_GOT_IP_ADDRESS: Interface BVI1 obtained IP from DHCP...
*Dec 19 07:45:52.431: %MESH-6-CAPWAP_RESTART: Mesh Capwap re-started
*Dec 19 07:45:57.511: [m102x_set_lanport_config] Cannot enable AUX port while POE, connect AC or Inj source
*Dec 19 07:45:57.511: %LWAPP-4-CLIENTEVENTLOG: Not sending change state post as the radio admin is down, lrad state = 5
Translating "CISCO-CAPWAP-CONTROLLER.xyz"...domain server (10.14.42.71) [OK]
*Dec 19 07:45:57.515: %LINK-5-CHANGED: Interface Dot11Radio0, changed state to administratively down
*Dec 19 07:45:58.515: %LINK-6-UPDOWN: Interface Dot11Radio1, changed state to down
*Dec 19 07:45:58.515: %LINEPROTO-5-UPDOWN: Line protocol on Interface Dot11Radio0, changed state to down
*Dec 19 07:45:58.523: %LINK-5-CHANGED: Interface Dot11Radio1, changed state to reset
*Dec 19 07:45:59.515: %LINEPROTO-5-UPDOWN: Line protocol on Interface Dot11Radio1, changed state to down
*Dec 19 07:45:59.555: %LINK-6-UPDOWN: Interface Dot11Radio1, changed state to up
*Dec 19 07:46:00.555: %LINEPROTO-5-UPDOWN: Line protocol on Interface Dot11Radio1, changed state to up
*Dec 19 07:46:08.539: AP has SHA2 MIC certificate - Using SHA2 MIC certificate for DTLS.
*Dec 27 13:53:54.000: %CAPWAP-5-DTLSREQSEND: DTLS connection request sent peer_ip: 10.14.44.100 peer_port: 5246
*Dec 27 13:53:54.523: %CAPWAP-5-DTLSREQSUCC: DTLS connection created sucessfully peer_ip: 10.14.44.100 peer_port: 5246
*Dec 27 13:53:54.523: %CAPWAP-5-SENDJOIN: sending Join Request to 10.14.44.100
*Dec 27 13:53:57.199: %LWAPP-4-CLIENTEVENTLOG: Not sending change state post as the radio admin is down, lrad state = 6
*Dec 27 13:53:57.199: %CDP_PD-4-POWER_OK: Full power - NEGOTIATED inline power source
*Dec 27 13:53:59.523: %CAPWAP-5-SENDJOIN: sending Join Request to 10.14.44.100
*Dec 27 13:53:59.523: %DTLS-5-ALERT: Received WARNING : Close notify alert from 10.14.44.100
*Dec 27 13:53:59.523: %DTLS-5-SEND_ALERT: Send FATAL : Close notify Alert to 10.14.44.100:5246
*Dec 27 13:54:09.523: AP has SHA2 MIC certificate - Using SHA2 MIC certificate for DTLS.
*Dec 27 13:54:10.000: %CAPWAP-5-DTLSREQSEND: DTLS connection request sent peer_ip: 10.14.44.100 peer_port: 5246
*Dec 27 13:54:10.527: %CAPWAP-5-DTLSREQSUCC: DTLS connection created sucessfully peer_ip: 10.14.44.100 peer_port: 5246
*Dec 27 13:54:10.527: %CAPWAP-5-SENDJOIN: sending Join Request to 10.14.44.100
*Dec 27 13:54:15.527: %CAPWAP-5-SENDJOIN: sending Join Request to 10.14.44.100
*Dec 27 13:54:15.527: %DTLS-5-ALERT: Received WARNING : Close notify alert from 10.14.44.100
*Dec 27 13:54:15.527: %DTLS-5-SEND_ALERT: Send FATAL : Close notify Alert to 10.14.44.100:5246
*Dec 27 13:54:25.527: AP has SHA2 MIC certificate - Using SHA2 MIC certificate for DTLS.
The WLC accepts MIC & SSC & LSC Certificate
The AP works fine when he's in "local" mode.
I have tried to find the issue for a while now but it seems i'm a bit stuck, havent had that much expirience with wireless Networks yet.
Maybe someone of you guys can guide me in the right direction.
Thanks a lot!
Solved! Go to Solution.
- Labels:
-
Wireless LAN Controller
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2016 08:16 AM
So from your output, MESH is only supported with one country code domain defined on the controller. You will not be able to get bridge mode to work with more than one country code as this is one of the requirements.
-Scott
*** Please rate helpful posts ***
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2016 09:36 AM
I have ran indoor AP's as mesh in the past and this is what I did...
Make sure the antennas are connected if using E AP's
AP that will be the MAP is powered up via AC power
AP that will be the MAP & RAP connected via wired and joined to the controller
MAP & RAP Ethernet MAC address added to the Mac filter
RAP was connected to a trunk port with native vlan define on the MAP management
RAP power and channel defined
BGN was defined on the MAP/RAP
Change the AP that will be your RAP to bridge and when the MESH tab is present after the AP reboots, set that to Root AP
Change the AP that will be your MAP to bridge and when the MESH tab is present after the AP reboots, set that to Mesh AP
Remove the Ethernet connection on the MAP
Wait for a few and the MAP should join the RAP
-Scott
*** Please rate helpful posts ***
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2016 01:03 AM
Hello Scott,
I have ran indoor AP's as mesh in the past and this is what I did...
Make sure the antennas are connected if using E AP's
I tried today with an "AIR-AP1572EAC-E-K9" with an "AIR-ANT-2513P4M-N" connected.
AP that will be the MAP & RAP connected via wired and joined to the Controller
As Long as the AP is in local it joins the Controller normally
MAP & RAP Ethernet MAC address added to the Mac filter
I have added the MAC Adress of the AP to the "AP Authorization List" with "MIC Certificate Type" and the Base Radio MAC to the MAC filtering (screen shot)
RAP was connected to a trunk port with native vlan define on the MAP Management
I tried both, putting the port in the Management Vlan directly or via trunk and define the native vlan. (if the AP is in local mode it works fine in both, as expected)
RAP power and channel defined
Did this aswell (screenshot)
BGN was defined on the MAP/RAP
Haven't done anything here yet
All the other Points you mentioned i cant do since when i change the AP mode to Bridge it is unable to join the Controller again, as seen above with my LOG posted.
LOG joining the WLC when in local mode
*Mar 1 00:13:15.359: AP has SHA2 MIC certificate - Using SHA2 MIC certificate for DTLS.
*Dec 28 08:59:46.000: %CAPWAP-5-DTLSREQSEND: DTLS connection request sent peer_ip: 10.14.44.100 peer_port: 5246
*Dec 28 08:59:46.527: %CAPWAP-5-DTLSREQSUCC: DTLS connection created sucessfully peer_ip: 10.14.44.100 peer_port: 5246
*Dec 28 08:59:46.527: %CAPWAP-5-SENDJOIN: sending Join Request to 10.14.44.100
*Dec 28 08:59:51.527: %CAPWAP-5-SENDJOIN: sending Join Request to 10.14.44.100
*Dec 28 08:59:51.999: %LINK-6-UPDOWN: Interface Dot11Radio0, changed state to down
*Dec 28 08:59:52.043: %LINK-5-CHANGED: Interface Dot11Radio0, changed state to reset
*Dec 28 08:59:52.087: %CAPWAP-5-JOINEDCONTROLLER: AP has joined controller wlc123
*Dec 28 08:59:52.163: %LINK-6-UPDOWN: Interface Dot11Radio0, changed state to up
*Dec 28 08:59:52.787: %WIDS-6-ENABLED: IDS Signature is loaded and enabled
Thanks for your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2016 09:00 AM
You are using the base Ethernet MAC address not the radio MAC address correct?
-Scott
*** Please rate helpful posts ***
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2016 09:04 AM
You should be able to plug the AP Ethernet back in and then uncheck the AP Authorization List so that you can get the AP to join again and setup the BGN and any other settings.
-Scott
*** Please rate helpful posts ***
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2016 12:42 AM
Hello Scott,
I tried both, but I dont think this is my Problem at the moment.
AP MAC 00:a6:ca:e3:40:20
Base Radio MAC 00:a6:ca:be:7f:a0
The Problem i have is while i have the AP connected via Ethernet that it cannot join the WLC when in Bridge mode and i dont know how to work around that, or am i doing something completly wrong ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2016 02:58 AM
Take a look at the logs ad see if you see a AAA failure with a MAC address. Make sure that is in the Mac filter. If it is, then it must be another issue and you would have to go into the AP flash and delete the MESH config file and reboot the AP. You can also factory default the AP, but make sure you still remove the MESH file in flash.
-Scott
*** Please rate helpful posts ***
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2016 05:54 AM
Hello Scott,
i deleted the "mesh_port_cfg.txt"
from the AP Flash, but in bridge mode it is still thesame as above, resetting to factory Setting doesnt help aswell.
The Point is it join the AP successfully in local mode only in bride mode ist doesnt manage to join. I will see if i get any more Details for the WLC and see what he is doing in the joning process
Thank for your help!
----
edit
*spamApTask3: Dec 29 14:38:51.355: 00:a6:ca:be:7f:a0 ApModel: AIR-AP1572EAC-E-K9
spamApTask7: Dec 29 14:38:59.111: Unknown AP type. Using Controller Version!!!
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCID: called to evaluate <cscoDefaultIdCert>
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCID: comparing to row 4, ID cert >bsnSslWebauthCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCID: comparing to row 3, ID cert >bsnSslWebadminCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCID: comparing to row 2, ID cert >cscoDefaultIdCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCertFromCID: called to get cert for CID 16b26244
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCertFromCID: comparing to row 4, certname >bsnSslWebauthCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCertFromCID: comparing to row 3, certname >bsnSslWebadminCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCertFromCID: comparing to row 2, certname >cscoDefaultIdCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCID: called to evaluate <cscoDefaultIdCert>
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCID: comparing to row 4, ID cert >bsnSslWebauthCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCID: comparing to row 3, ID cert >bsnSslWebadminCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetCID: comparing to row 2, ID cert >cscoDefaultIdCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetSshPrivateKeyFromCID: called to get key for CID 16b26244
*spamApTask3: Dec 29 14:39:01.355: sshpmGetSshPrivateKeyFromCID: comparing to row 0, certname >bsnOldDefaultIdCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetSshPrivateKeyFromCID: comparing to row 1, certname >bsnDefaultIdCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetSshPrivateKeyFromCID: comparing to row 2, certname >cscoDefaultIdCert<
*spamApTask3: Dec 29 14:39:01.355: sshpmGetSshPrivateKeyFromCID: match in row 2
*spamApTask3: Dec 29 14:39:01.687: sshpmGetIssuerHandles: locking ca cert table
*spamApTask3: Dec 29 14:39:01.687: sshpmGetIssuerHandles: calling x509_alloc() for user cert
*spamApTask3: Dec 29 14:39:01.687: sshpmGetIssuerHandles: calling x509_decode()
*spamApTask3: Dec 29 14:39:01.691: sshpmGetIssuerHandles: <subject> C=US, ST=California, L=San Jose, O=Cisco Systems, CN=C1570-00a6cae34020, MAILTO=support@cisco.com
*spamApTask3: Dec 29 14:39:01.691: sshpmGetIssuerHandles: <issuer> O=Cisco, CN=Cisco Manufacturing CA SHA2
*spamApTask3: Dec 29 14:39:01.692: sshpmGetIssuerHandles: Mac Address in subject is 00:a6:ca:e3:40:20
*spamApTask3: Dec 29 14:39:01.692: sshpmGetIssuerHandles: Cert Name in subject is C1570-00a6cae34020
*spamApTask3: Dec 29 14:39:01.692: sshpmGetIssuerHandles: Extracted cert issuer from subject name.
*spamApTask3: Dec 29 14:39:01.692: sshpmGetIssuerHandles: Cert is issued by Cisco Systems.
*spamApTask3: Dec 29 14:39:01.692: sshpmGetCID: called to evaluate <cscoDefaultMfgCaCert>
*spamApTask3: Dec 29 14:39:01.692: sshpmGetCID: comparing to row 7, CA cert >cscoMfgSha2CaCert<
*spamApTask3: Dec 29 14:39:01.692: sshpmGetCID: comparing to row 6, CA cert >cscoRootSha2CaCert<
*spamApTask3: Dec 29 14:39:01.692: sshpmGetCID: comparing to row 5, CA cert >cscoDefaultMfgCaCert<
*spamApTask3: Dec 29 14:39:01.692: sshpmGetCertFromCID: called to get cert for CID 26ec3be3
*spamApTask3: Dec 29 14:39:01.692: sshpmGetCertFromCID: comparing to row 7, certname >cscoMfgSha2CaCert<
*spamApTask3: Dec 29 14:39:01.692: sshpmGetCertFromCID: comparing to row 6, certname >cscoRootSha2CaCert<
*spamApTask3: Dec 29 14:39:01.692: sshpmGetCertFromCID: comparing to row 5, certname >cscoDefaultMfgCaCert<
*spamApTask3: Dec 29 14:39:01.692: ssphmUserCertVerify: calling x509_decode()
*spamApTask3: Dec 29 14:39:01.702: ssphmUserCertVerify: failed to verify AP cert >cscoDefaultMfgCaCert<
*spamApTask3: Dec 29 14:39:01.702: sshpmGetCID: called to evaluate <cscoMfgSha2CaCert>
*spamApTask3: Dec 29 14:39:01.702: sshpmGetCID: comparing to row 7, CA cert >cscoMfgSha2CaCert<
*spamApTask3: Dec 29 14:39:01.702: sshpmGetCertFromCID: called to get cert for CID 29f09c0d
*spamApTask3: Dec 29 14:39:01.702: sshpmGetCertFromCID: comparing to row 7, certname >cscoMfgSha2CaCert<
*spamApTask3: Dec 29 14:39:01.702: ssphmUserCertVerify: calling x509_decode()
*spamApTask3: Dec 29 14:39:01.741: ssphmUserCertVerify: user cert verfied using >cscoMfgSha2CaCert<
*spamApTask3: Dec 29 14:39:01.741: sshpmGetIssuerHandles: ValidityString (current): 2016/12/29/13:39:01
*spamApTask3: Dec 29 14:39:01.741: sshpmGetIssuerHandles: ValidityString (NotBefore): 2016/08/04/07:32:49
*spamApTask3: Dec 29 14:39:01.741: sshpmGetIssuerHandles: ValidityString (NotAfter): 2026/08/04/07:42:49
*spamApTask3: Dec 29 14:39:01.741: sshpmGetIssuerHandles: Signature Algorithm is rsa-pkcs1-sha256
*spamApTask3: Dec 29 14:39:01.741: sshpmGetIssuerHandles: getting cisco ID cert handle...
*spamApTask3: Dec 29 14:39:01.741: sshpmGetCID: called to evaluate <cscoDefaultIdCert>
*spamApTask3: Dec 29 14:39:01.741: sshpmGetCID: comparing to row 4, ID cert >bsnSslWebauthCert<
*spamApTask3: Dec 29 14:39:01.741: sshpmGetCID: comparing to row 3, ID cert >bsnSslWebadminCert<
*spamApTask3: Dec 29 14:39:01.741: sshpmGetCID: comparing to row 2, ID cert >cscoDefaultIdCert<
*spamApTask3: Dec 29 14:39:01.749: sshpmFreePublicKeyHandle: called with 0x2c2bbf64
*spamApTask3: Dec 29 14:39:01.749: sshpmFreePublicKeyHandle: freeing public key
*spamApTask3: Dec 29 14:39:06.883: 00:a6:ca:be:7f:a0 Bridge AP can not join MultiCountry Controller: Bridge mode AP 10.14.50.104:13315 cannot be supported on Multi Country Controll
*spamApTask3: Dec 29 14:39:06.892: 00:a6:ca:be:7f:a0 State machine handler: Failed to process msg type = 3 state = 0 from 10.14.50.104:13315
*spamApTask3: Dec 29 14:39:06.892: 00:13:5f:ec:6c:00 Failed to parse CAPWAP packet from 10.14.50.104:13315
*spamApTask3: Dec 29 14:39:06.893: Unable to find deleted AP 00:a6:ca:be:7f:a0
*spamApTask3: Dec 29 14:39:06.893: 00:13:5f:ec:6c:00 Discarding non-ClientHello Handshake OR DTLS encrypted packet from 10.14.50.104:13315)since DTLS session is not established
(Cisco Controller) >show country channels
Configured Country............................. Multiple Countries:AT,HK
KEY: * = Channel is legal in this country and may be configured manually.
A = Channel is the Auto-RF default in this country.
. = Channel is not legal in this country.
C = Channel has been configured for use by Auto-RF.
x = Channel is available to be configured for use by Auto-RF.
(-,-) = (indoor, outdoor) regulatory domain allowed by this country.
-----------------:+-+-+-+-+-+-+-+-+-+-+-+-+-+-
802.11bg :
Channels : 1 1 1 1 1
: 1 2 3 4 5 6 7 8 9 0 1 2 3 4
-----------------:+-+-+-+-+-+-+-+-+-+-+-+-+-+-
AT (-E ,-E ): A * * * * A * * * * A * * .
HK (-AE ,-NA ): A * * * * A * * * * A * * .
Auto-RF : C x x x x C x x x x C x x .
-----------------:+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-
802.11a : 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
Channels : 3 3 3 4 4 4 4 4 5 5 6 6 0 0 0 1 1 2 2 2 3 3 4 4 5 5 6 6 6 7
: 4 6 8 0 2 4 6 8 2 6 0 4 0 4 8 2 6 0 4 8 2 6 0 9 3 7 1 5 9 3
-----------------:+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-
--More-- or (q)uit
AT (-E ,-E ): . A . A . A . A A A A A * * * * * * * * * * * . . . . . . .
HK (-NS ,-N ): . A . A . A . A A A A A * * * * * * * * * * * A A A A * . .
Auto-RF : . C . C . C . C C C C C x x x x x x x x x x x x x x x x . .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2016 08:16 AM
So from your output, MESH is only supported with one country code domain defined on the controller. You will not be able to get bridge mode to work with more than one country code as this is one of the requirements.
-Scott
*** Please rate helpful posts ***
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2017 02:48 AM
Mesh and Multi Country is only supported on 8.1 or higher.
I upted my WLC and now it works.
Ps. updating on 8.3 broke my Guest Web authentication so i will try 8.1 / 8.2 later and see if i get both to work on one of those versions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2017 08:12 AM
v8.2.130.0 is pretty stable for us. You can try v8.2.141.0.
-Scott
*** Please rate helpful posts ***
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2018 07:03 AM
You must do some steps:
1] Make enable " Admin Status" because sometimes it is disabled.
2]Change AP mode into Local.
And click on Apply Button. after rebooting, problem fix.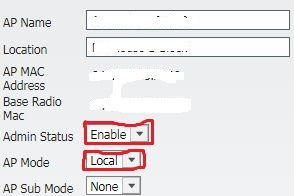
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:


