- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Problem with GUI management of Air-1142-N
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Problem with GUI management of Air-1142-N
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2012 11:29 PM - edited 07-03-2021 10:18 PM
Dear All
When i am trying to make test between two of AP 1142-N as ((WGB & AP) scenario & (root bridge & non root bridge)scenario). but it's fail.
so i thougt the problem with IOS .. after delete old one and reupload another i have new problem..
the problem is the web interface managament of AP has been changed to (find the capture of screen below please) :
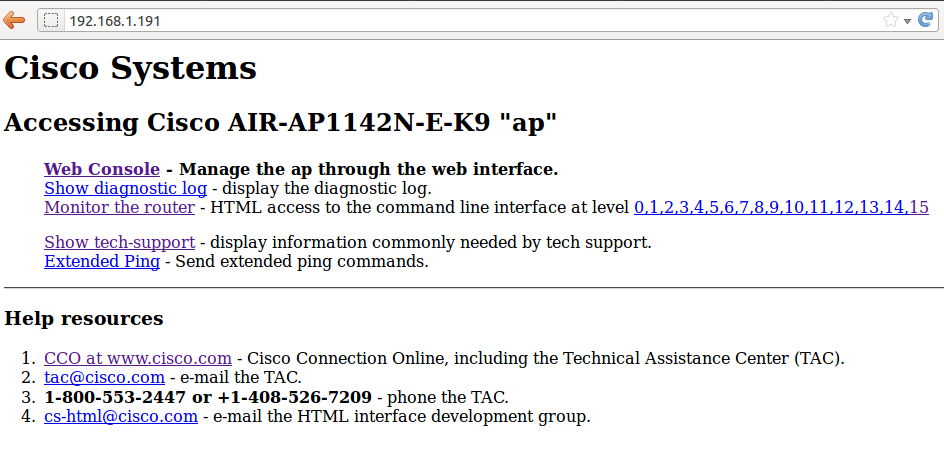
the old one was like :

my two question are :
1 - how to return the old web interface management of AP 1142?
2 - does the Ap 1142 work as WGB and root bridge in standalone mode ?
based on the link below from cisco .. i think this Ap 1142 does not work as WGB .. they said
based AP configured as WGB (1130, 1240, 1250, etc)
http://www.cisco.com/en/US/products/ps6087/products_tech_note09186a0080b90500.shtml
thanks alot
- Labels:
-
Aironet Access Points
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2012 03:37 AM
Salam Aref,
1142 should work as WGB. The link you provided says that it works with any IOS-based AP. and the letters "etc" at the end of your red-font quote explicitly include 1142 AP.
I am not sure why you are getting the new page. but what appears if you click on "Web Console" link that appears on the first pic you provided? will it open the original configuration page for you?
Please try.
HTH
Amjad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2012 04:39 AM
thank you amjad very much ... but "web console" does not work also :

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2012 07:01 AM
Well the 1140's will work at a WGB as I have tested that once before. Do you understand the configuration through the CLI and not the GUI. Is your ap at default settings or not? If you understand the CLI, you can verify that http or https server is enabled for GUI and that your username has privilege 15 to give you proper access. You can always just console into the ap and login and issues a write erase and start over.
Sent from Cisco Technical Support iPad App
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2012 11:13 PM
thank you very much Scott.
but still have problem after enabled https in the AP
by the way .. i have another AP ... it is work very well and i copied its configuration to which have problem...
but still have problem.... i don't know why?
see the running config below of AP which work very well :
!
version 12.4
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname ap
!
enable password 7 05080F1C2243
!
no aaa new-model
!
!
dot11 syslog
!
dot11 ssid Cisco
authentication open
guest-mode
infrastructure-ssid
!
!
!
username cisco privilege 15 password 7 121A0C041104
!
!
!
!
interface Dot11Radio0
no ip address
no ip route-cache
!
ssid Cisco
!
antenna gain 0
channel 2437
station-role root bridge
bridge-group 1
bridge-group 1 spanning-disabled
!
interface Dot11Radio1
no ip address
no ip route-cache
shutdown
antenna gain 0
no dfs band block
channel dfs
station-role root
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
bridge-group 1 spanning-disabled
!
interface GigabitEthernet0
ip address 192.168.1.192 255.255.255.0
no ip route-cache
duplex auto
speed auto
no keepalive
!
ip http server
ip http secure-server
ip http help-path http://www.cisco.com/warp/public/779/smbiz/prodconfig/help/eag
!
!
!
line con 0
line vty 0 4
password 7 13061E010803
login
!
end
see the running config below of AP which have problem :
!
version 12.4
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname ap
!
enable password 7 14141B180F0B
!
no aaa new-model
!
!
dot11 syslog
!
dot11 ssid Cisco
authentication open
guest-mode
infrastructure-ssid
!
!
crypto pki trustpoint TP-self-signed-64751520
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-64751520
revocation-check none
rsakeypair TP-self-signed-64751520
!
!
crypto pki certificate chain TP-self-signed-64751520
certificate self-signed 01
30820236 3082019F A0030201 02020101 300D0609 2A864886 F70D0101 04050030
2F312D30 2B060355 04031324 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 36343735 31353230 301E170D 30323033 30313035 31353536
5A170D32 30303130 31303030 3030305A 302F312D 302B0603 55040313 24494F53
2D53656C 662D5369 676E6564 2D436572 74696669 63617465 2D363437 35313532
3030819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281 8100B64C
2D9209B6 EFAFBD4F 5A307C40 0C89CB37 3EC3078A 11D4392C 5313B730 C605A2F8
25668E82 43185307 9C5D76EA D1D0D2A8 9607773E B2DF15D5 4B8746E5 D8838B12
BA00E374 A702A994 07D34CD3 851DD9AA 1CDC6444 D9891F55 6FBC95BC F016CC10
550BC998 64D99ED7 1100F6C6 6038A5E0 94464263 77D74662 00533C81 3CD10203
010001A3 62306030 0F060355 1D130101 FF040530 030101FF 300D0603 551D1104
06300482 02617030 1F060355 1D230418 30168014 5A4F78BF F2FE67AE 56C01056
211F2F4C BD7F21B1 301D0603 551D0E04 1604145A 4F78BFF2 FE67AE56 C0105621
1F2F4CBD 7F21B130 0D06092A 864886F7 0D010104 05000381 81004E87 C71B78CE
84D5C21E 5DB98F7E 220DB387 C98D31ED 6A16975C 6AF26ACA A7A566CE BDC24B15
EC9EDCE8 2EB831BD CBECEBEF 8BE2B031 802BC209 C59C8F25 97F2E93D FD20432C
0EE87A69 0B04F748 545FA550 2FC9E75C D14713E4 D26FE590 EEBE64E5 DD2DAA40
D8849204 5A5499A0 9B52D16B 42B19377 145FC5D8 EE378EC8 C818
quit
username cisco privilege 15 password 7 045802150C2E
!
!
!
!
interface Dot11Radio0
no ip address
no ip route-cache
!
ssid Cisco
!
antenna gain 0
channel 2437
station-role root bridge
bridge-group 1
bridge-group 1 spanning-disabled
!
interface Dot11Radio1
no ip address
no ip route-cache
shutdown
antenna gain 0
no dfs band block
channel dfs
station-role root
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
bridge-group 1 spanning-disabled
!
interface GigabitEthernet0
ip address 192.168.1.191 255.255.255.0
no ip route-cache
duplex auto
speed auto
no keepalive
!
ip http server
ip http secure-server
ip http help-path http://www.cisco.com/warp/public/779/smbiz/prodconfig/help/eag
!
!
!
line con 0
line vty 0 4
password 7 030752180500
login
!
end
thank you all ... hope someone help me to fix that problem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2012 11:31 PM
The only thing left that you can do is upload the code on the access point. That should fix it, but make sure it's biotin from that code. You can upload the latest firmware or one that is newer than the one you have. You can look at the flash and delete the old firmware once you have uploaded the new one.
Sent from Cisco Technical Support iPhone App
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2012 01:24 AM
I support Scott.
Having the 404 error means that the page can not be found on the specified destination. This could be due image problem where it was not extracted successfully.
You can install new iOS image and test. This should probably fix it.
Amjad
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


