- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- Dynamic VLAN Assignment on autonomous AP using ACS 5
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-17-2011 08:50 AM - edited 11-18-2020 02:55 AM
- Introduction
- Topology
- Switch Configuration
- AP Configuration and Command Explanation
- ACS Configuration
- Verification
Introduction
In this Document we will see a sample configuration on how to use ACS 5 to assign a dynamic VLAN to a wireless user performing 802.1x authentication on an autonomous access-point, with only one SSID.
We will be using Active Directory authentication, and the VLAN will be assigned based upon the AD Usergroup the user belongs to.
The setup will have vlan 90 and 91, which are respectively 192.168.90.0/24 and 192.168.91.0/24.
I have two users in my active directory, bastien and bastien2, where bastien belongs to only domain users, and bastien2 belongs to corp2.
All users will be placed by default in the vlan 90, and we will define authorization rules to put all users from corp2 group in the vlan 91
The AP used is a AIR-AP1242AG-E-K9, version 12.4(21a)JA1.
Topology
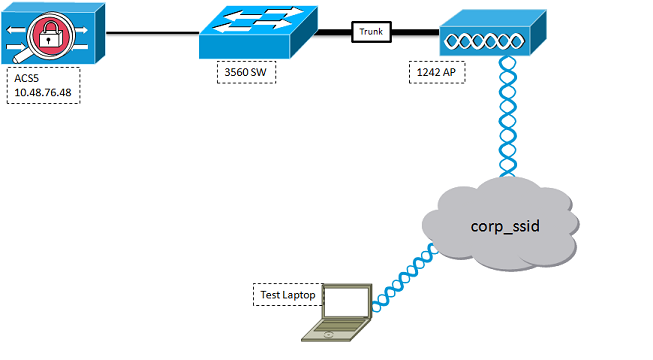
Switch Configuration
The switch configuration is pretty simple, and will not be covered in detail. The switch isa 3560 doing L3 Routing, and DHCP Server.
!
vlan 90
name MGT
!
vlan 91
name SSIDBastien1
!
interface FastEthernet0/7
desc Interface connected to the AP
switchport trunk encapsulation dot1q
switchport mode trunk
spanning-tree portfast
interface Vlan1
ip address 10.48.76.4 255.255.255.128
!
interface Vlan90
ip address 192.168.90.254 255.255.255.0
!
interface Vlan91
ip address 192.168.91.254 255.255.255.0
!
ip dhcp pool Bastien91
network 192.168.91.0 255.255.255.0
default-router 192.168.91.254
!
ip dhcp pool vlan90
network 192.168.90.0 255.255.255.0
default-router 192.168.90.1
!
AP Configuration and Command Explanation
Following is the needed configuration on the AP. Comments are inline.
! Activating AAA
aaa new-model
! Adding ACS Server in group RAD_EAP
aaa group server radius RAD_EAP
server 10.48.76.48 auth-port 1645 acct-port 1646
!
! Defining AAA list: Login is for auth, and authorization network
! is needed for dynamic vlan assignment
aaa authentication login EAP group RAD_EAP
aaa authorization network default group RAD_EAP
!
dot11 mbssid !not mandatory, depends if you have multiple SSIDs on your network
!Create the dot11 vlan: The dynamic VLAN needs to be defined on the AP
dot11 vlan-name vlan90 vlan 90
dot11 vlan-name vlan91 vlan 91
!
!Creating the SSID
dot11 ssid corp_ssid
vlan vlan90 !This is default VLAN
authentication open eap EAP
authentication network-eap EAP
authentication key-management wpa version 2
guest-mode !Guest mode or mbssid guest mode depends if you use mbssid or not
mbssid guest-mode
!
interface Dot11Radio0
no ip address
no ip route-cache
!
encryption vlan 90 mode ciphers aes-ccm ! We need to set encryption mode for all dynamic VLAN used
!
encryption vlan 91 mode ciphers aes-ccm ! We need to set encryption mode for all dynamic VLAN used
!
ssid corp_ssid ! Adding SSID to the dot110 interface
!
station-role root
!
interface Dot11Radio0.90 !subinterface for VLAN 90
encapsulation dot1Q 90
no ip route-cache
bridge-group 1
bridge-group 1 subscriber-loop-control
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
bridge-group 1 spanning-disabled
!
interface Dot11Radio0.91 !subinterface for VLAN 91
encapsulation dot1Q 91
no ip route-cache
bridge-group 91
bridge-group 91 subscriber-loop-control
bridge-group 91 block-unknown-source
no bridge-group 91 source-learning
no bridge-group 91 unicast-flooding
bridge-group 91 spanning-disabled
!
interface FastEthernet0
no ip address
no ip route-cache
duplex auto
speed auto
!
interface FastEthernet0.90 !subinterface for VLAN 90
encapsulation dot1Q 90
no ip route-cache
bridge-group 1
no bridge-group 1 source-learning
bridge-group 1 spanning-disabled
!
interface FastEthernet0.91 !subinterface for VLAN 91
encapsulation dot1Q 91
no ip route-cache
bridge-group 91
no bridge-group 91 source-learning
bridge-group 91 spanning-disabled
!
interface BVI1 ! BVI to manage the AP, and to use for radius communication
ip address 192.168.90.50 255.255.255.0
no ip route-cache
!
! Defining the ACS Server
radius-server host 10.48.76.48 auth-port 1645 acct-port 1646 key 7 1511021F0725
bridge 1 route ip
!
ACS Configuration
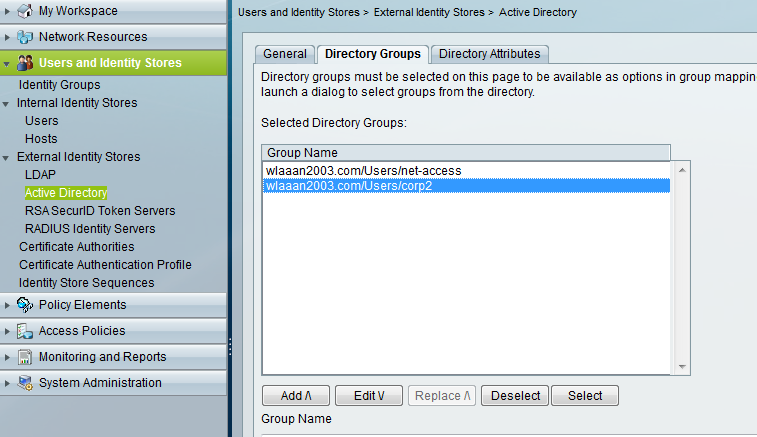
Step 1. Integration of ACS in the Domain, and choose the groups that will be using
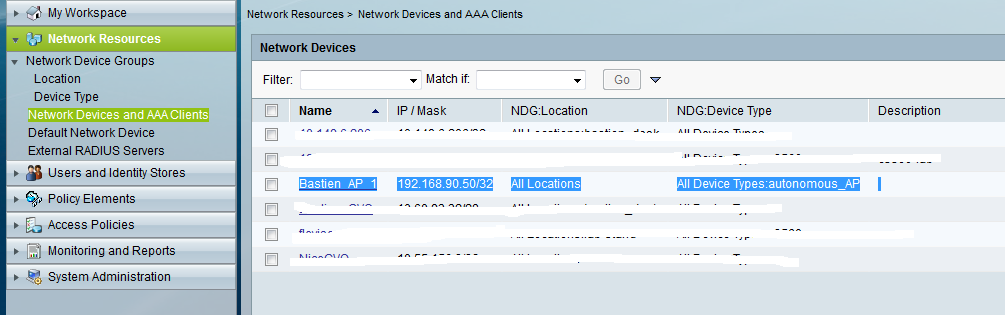
Step 2: Add the access-point as a network access-device, and define radius shared secret (which, obviously, has to be the same as the one defined in your AP configuraiton).
Note: In this case we have set the AP device type to autonomous_AP, as we will be using this criteria in the service selection (see below).
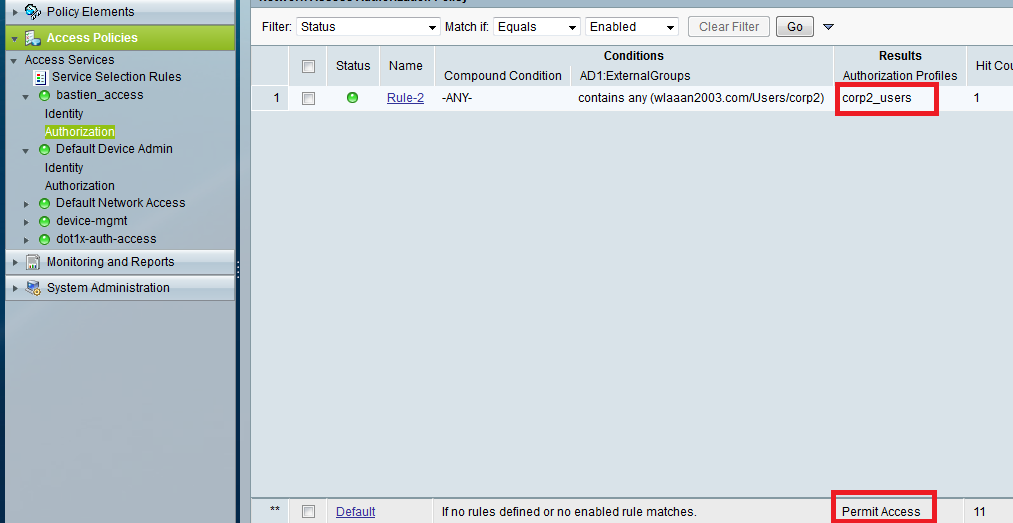
Step 3: After that, we need to create an authorization profile that will assign VLAN 91:

Step 4: Now, I have to create an access service with my AD as identity source, and with an authorization rules that will apply the profile I created in the previous step for all users belonging to the AD Group Corp2.
Note: To see the AD1:ExternalGroups condition field, you need to click on customize First.
Note2: Make sure that default rule is Permit Access, or any other authorization profile that will allow access.
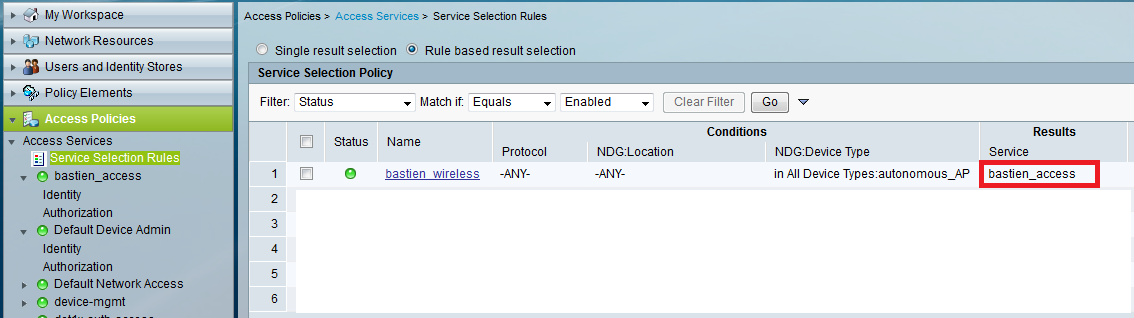
Step 5: The next and final step for ACS configuration is to direct all Radius request coming from my AP to my Access Service:
Verification
We can check that everything is fine using show dot11 assoc all: This is when I log with bastien:
ap#sh dot11 associations all-client
Address : 0011.95ca.e82d Name : NONE
IP Address : 192.168.90.61 Interface : Dot11Radio 0
Device : unknown Software Version : NONE
CCX Version : NONE Client MFP : Off
State : EAP-Assoc Parent : self
SSID : corp_ssid
VLAN : 90
Hops to Infra : 1 Association Id : 1
Clients Associated: 0 Repeaters associated: 0
Tunnel Address : 0.0.0.0
Key Mgmt type : WPAv2 Encryption : AES-CCMP
Current Rate : 54.0 Capability : WMM ShortHdr
Supported Rates : 1.0 2.0 5.5 11.0 6.0 9.0 12.0 18.0 24.0 36.0 48.0 54.0
Voice Rates : disabled Bandwidth : 20 MHz
Signal Strength : -63 dBm Connected for : 85 seconds
Signal to Noise : 35 dB Activity Timeout : 60 seconds
Power-save : Off Last Activity : 0 seconds ago
Apsd DE AC(s) : NONE
Packets Input : 833 Packets Output : 86
Bytes Input : 89150 Bytes Output : 13149
Duplicates Rcvd : 6 Data Retries : 9
Decrypt Failed : 0 RTS Retries : 0
MIC Failed : 0 MIC Missing : 0
Packets Redirected: 0 Redirect Filtered: 0
Session timeout : 0 seconds
Reauthenticate in : never
This is when I log with bastien2:
ap#sh dot11 associations all-client
Address : 0011.95ca.e82d Name : NONE
IP Address : 192.168.91.2 Interface : Dot11Radio 0
Device : unknown Software Version : NONE
CCX Version : NONE Client MFP : Off
State : EAP-Assoc Parent : self
SSID : corp_ssid
VLAN : 91
Hops to Infra : 1 Association Id : 1
Clients Associated: 0 Repeaters associated: 0
Tunnel Address : 0.0.0.0
Key Mgmt type : WPAv2 Encryption : AES-CCMP
Current Rate : 48.0 Capability : WMM ShortHdr
Supported Rates : 1.0 2.0 5.5 11.0 6.0 9.0 12.0 18.0 24.0 36.0 48.0 54.0
Voice Rates : disabled Bandwidth : 20 MHz
Signal Strength : -64 dBm Connected for : 33 seconds
Signal to Noise : 34 dB Activity Timeout : 60 seconds
Power-save : Off Last Activity : 1 seconds ago
Apsd DE AC(s) : NONE
Packets Input : 266 Packets Output : 53
Bytes Input : 32974 Bytes Output : 8475
Duplicates Rcvd : 0 Data Retries : 4
Decrypt Failed : 0 RTS Retries : 0
MIC Failed : 0 MIC Missing : 0
Packets Redirected: 0 Redirect Filtered: 0
Session timeout : 0 seconds
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Bastien,
Thanks a lot for documenting this behaviour with autonomous APs.
Do you know for which Autonomous APs dynamic vlan assignment is supported? We're trying to get this to work on the 870s (built-in AP) and 880s (built-in autonomous AP). I can't find a list with supported APs..
Best regards.
Stefan
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
Unfortunately, I don't have, nor I couldn't find such list. I believe this is more software than hardware dependent feature, so you can try to load a 12.2(21) on your built-in AP and test. If that doesn't work for you I may give it a try if I have some free time?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great doc my French friend. :-)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Stefan
Did you manage to get this working on a Cisco 880 series, I'm trying to do the same, the client gets authenticated as it shows on the logs on the Radius server, but it gets disconnected straight away so something isn't working as expected.
Steve
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Steve,
We only got it to work when both the original and radius-assigned vlan use the same wireless settings (encryption method and key management). We tried to assign some clients to a Preshared Key guest vlan using the corporate SSID. That we didn't get to work.
Also I'm not sure whether we tested with 880 specific. I am sure about the 1200s AP though.
Regard, Stefan
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: