- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- Generating pcap wireshark readables files from WLC (and others)'s debugs' packets dumps
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-04-2010 08:06 AM - edited 11-18-2020 02:51 AM
Introduction
If you're going verbose into debugs, you may have noticed that you see sometimes packets dumps, such when you enable debug crypto isakmp 255 on ASA, or debug aaa packet enable on a WLC, but these dumps are not very friendly to analyze. We'll see here how to convert these dumps to pcap files to read them in wireshark.
I will use as example a WLC debug output, but it can of course be adapted to other debugs/dumps.
Collecting logs
I guess this part is not the most hardest, just turn on the log function of your terminal. I provide here an example with putty (free powerful terminal emulator). I will use debug client + debug dot1x all on a WLC while connecting to a WPA2 SSID with 802.1x authentication (PEAP) so that we can get some dumps on the debugs of the WLC:
(w-5508-1) >debug aaa packet enable

(See attached putty.log file)
Clearing the output
As you can see, there's lot of informations that are not useful:
(w-5508-1) >debug aaa packet enable
*aaaQueueReader: Nov 04 14:47:58.950: 00000000: 01 8c 00 a2 5a 4c 14 85 58 c9 dc 53 4b 09 84 a1 ....ZL..X..SK...
*aaaQueueReader: Nov 04 14:47:58.950: 00000010: ad b1 d8 71 01 09 62 61 73 74 69 65 6e 1f 0e 30 ...q..bastien..0
We need only the part that is in red.
To clear it, I use egrep and sed, which are unix utilities freely available on windows:
http://gnuwin32.sourceforge.net/packages/grep.htm
http://gnuwin32.sourceforge.net/packages/sed.htm
I use the following command to strip unuseful information:
C:\Program Files (x86)\GnuWin32\bin>egrep [0123456789abcdef]{8}: c:\tmp\putty.log
| sed.exe -r "s/(.*)([0123456789abcdef]{8}: ([0123456789abcdef]{2} ){1,16}.*)/\2/g" > c:\tmp\putty_dump.txt
Although regular expressions and use of the egrep and sed tools are not in the scope of this document, I will explain a little regular expressions I use. You can obviously use any other tool you want, the final goal being clearing debugs output.
- The grep command egrep [0123456789abcdef]{8}: c:\tmp\putty.log match the lines from the debug output files which contains a suit of eight characters in the set 0123456789abcdef, followed by ':' which correspond to the start of the dump in the line (example 00000000:).
- The sed command "s/(.*)([0123456789abcdef]{8}: ([0123456789abcdef]{2} ){1,16}.*)/\2/g" match two distinct parts in the selected lines, which are the starting of the line : ((.*)), and the starting of the dump, the hex character sequence (between 1 and 16 sequence of 2 hex digits), plus the rest of the line. Then we replace the whole line by only the second matched pattern, which basically strips off the date and message code part.
- The > c:\tmp\putty_dump.txt part redirect the cleared output in a separate file
Output looks like this
00000000: 01 8c 00 a2 5a 4c 14 85 58 c9 dc 53 4b 09 84 a1 ....ZL..X..SK...
00000010: ad b1 d8 71 01 09 62 61 73 74 69 65 6e 1f 0e 30 ...q..bastien..0
00000020: 30 30 63 66 31 36 33 30 35 30 38 1e 14 30 30 31 00cf1630508..001
(See attached putty_dump.txt file)
Converting dump to pcap
wireshark comes with a tool called text2pcap which can convert dumps to pcap files.
You can find help about the tool here:
http://www.wireshark.org/docs/man-pages/text2pcap.html
As I know the dumps are radius packets, I will add a dummy UDP header with radius ports as source/destination, which will also add dumb IP Header.
Here the command I used:
c:\Program Files\Wireshark>text2pcap.exe -u 1645,1645 c:\tmp\putty_dump.txt c:\tmp\putty_trace.cap
Input from: c:\tmp\putty_dump.txt
Output to: c:\tmp\putty_trace.cap
Generate dummy Ethernet header: Protocol: 0x800
Generate dummy IP header: Protocol: 17
Generate dummy UDP header: Source port: 1645. Dest port: 1645
Wrote packet of 51 bytes at 0
Wrote packet of 5 bytes at 51
Wrote packet of 51 bytes at 56
//.. output truncated
Wrote packet of 155 bytes at 6906
Wrote packet of 99 bytes at 7061
Read 85 potential packets, wrote 85 packets
There can be some packets that are erroneous, due to incorrect matching of the the regular expressions, or error in the putty output, but we should normally get all the valid debug outputs converted as packets (see attached putty_trace.cap file)
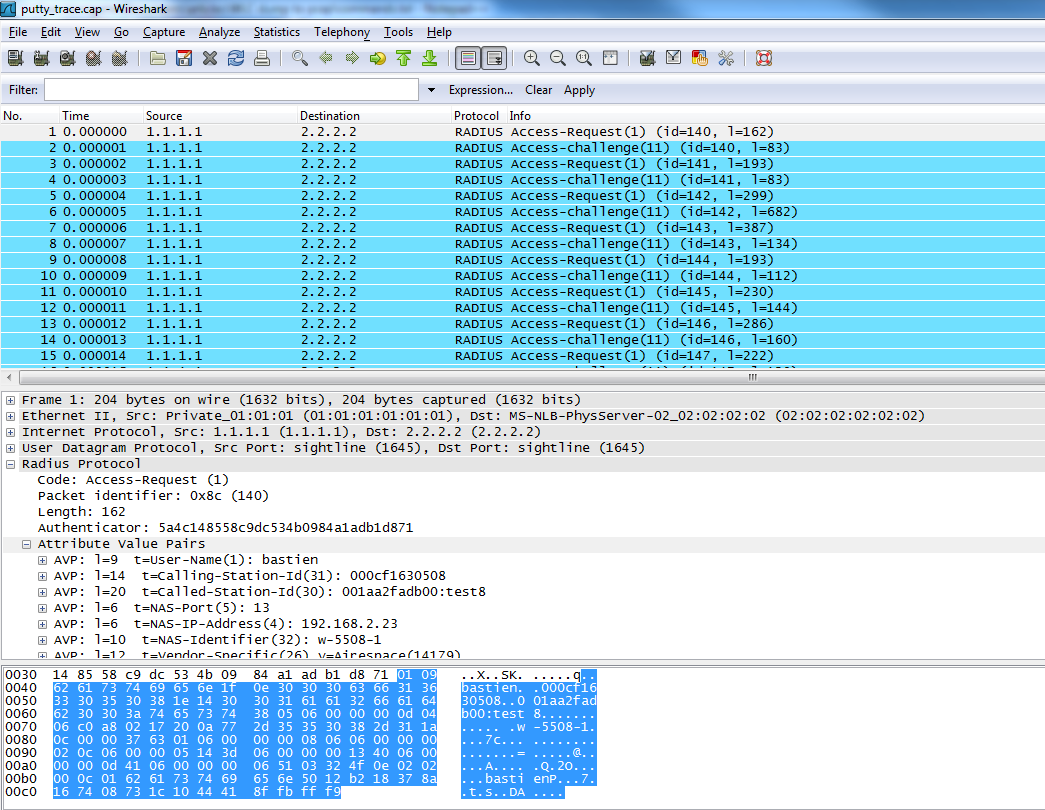
Script to automate all tasks (generate radius packets)
here is a batch script to extract dumps from debugs and convert them to pcap.
If you are converting packets that are not radius, you should modify the ports in the text2pcap command (here 1645).
Usage: debug2pcap.bat debugfile
@Echo off
rem modify this vars
set sed="C:\Program Files (x86)\GnuWin32\bin\sed.exe"
set egrep="C:\Program Files (x86)\GnuWin32\bin\egrep.exe"
set text2pcap="C:\Program Files\Wireshark\text2pcap.exe"
echo ===============================================
echo extracting packet
echo from: %1
echo to: %1.dmp and %1.pcap
echo ===============================================
echo.
echo Extracting dump ...
%egrep% [0123456789abcdef]{8}: %1 | sed.exe -r "s/(.*)([0123456789abcdef]{8}: ([0123456789abcdef]{2} ){1,16}.*)/\2/g" > %1.dmp
echo Ok!
echo.
echo.
echo Converting
echo.
%text2pcap% -u 1645,1645 %1.dmp %1.pcap
echo.
echo.
echo.
echo Done!
echo.
Conclusion
We've seen the process to convert packet dumps from a WLC debugs into a pcap file which can be read with tool such as wireshark. Although the example use some WLC's debugs output, as long as you extract the packet dumps you can convert it to pcap files using the text2pcap utility, but you moght adapt the regular expressions which are given here, or use any other tool of your convenience.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Cool - Thx for share it
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: