- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Android BYOD Provisioing Error - TAC escalated to Cisco Business Units
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Android BYOD Provisioing Error - TAC escalated to Cisco Business Units
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2019 02:15 AM - edited 07-05-2021 10:15 AM
Hi Cisco community,
I've been working with a TAC Engineer for the last few days trying to sort my Android problem out (though I haven't tested Apple devices yet!)
I'm getting the same error explained in this document https://community.cisco.com/t5/security-documents/android-byod-provisioning-error-quot-certificate-generation/ta-p/3733734
Single SSID - Can login to BYOD successfully with Active Directory account
Redirects me to BYOD portal, click start
Register my Device successfully in Device Portal
Run my Cisco CNA Proceed and Trust Certificate
Network password is required, I enter my AD password same one as 1st step above
"Certificate generation failed"
I'm running VE ISE 2.4 Patch 7 and NSA 2.2.0.55
With the TAC engineer we went over and over again changed configs in WLC ALC's, Authorization profiles, Policy Sets, Generated a New Self Signed Certificate with another Certificate Portal.........basically Engineer went through in detail from what I could see.
For some reason after following this document, we never see counter hits against these rules in our Policy sets, we have added the rule at the top added a separate policy set to see if this would work, still no hits. Note EST Service is running.
The fact we cannot see any hits against these rules as suggested in this workaround doc means to me that we are missing something here.
Below are my Android SPW logs:
2019.04.15 20:43:01 INFO:EST Server =test.test.com
2019.04.15 20:43:01 INFO:EST Server port =8084
2019.04.15 20:43:01 INFO:ISEDownloadProfileAsynchTask.onPostExecute :PASSED
2019.04.15 20:43:04 INFO:Location Permission for the App is granted.
2019.04.15 20:43:13 INFO:Making SCEP call
2019.04.15 20:43:13 INFO:Generating RSA key with key size: 2048
2019.04.15 20:43:13 INFO:Going to call EST server with args: cn = ga2paen, un= ga2paen, sn= test.test.com, sp =8084, cur= P-384, ca_certs length = 4002
2019.04.15 20:43:13 INFO:Calling native logger init with : /storage/emulated/0/Download/estlog.txt
2019.04.15 20:43:13 INFO:SPW profile is having certificate parameters
2019.04.15 20:43:13 INFO:EnrollCert Native returned pem len = 16384
2019.04.15 20:43:13 ERROR:ISEEnrollmentAsynchTask
2019.04.15 20:43:13 ERROR:java.lang.NullPointerException: Attempt to invoke virtual method 'java.lang.String java.security.cert.X509Certificate.toString()' on a null object reference
2019.04.15 20:43:13 ERROR:Attempt to invoke virtual method 'java.lang.String java.security.cert.X509Certificate.toString()' on a null object reference
2019.04.15 20:43:13 INFO:Internal system error.
Here are my Android EST logs:
***EST [INFO][ossl_init_cert_store_from_raw:182]-->
Adding cert to store (/CN=Certificate Services Endpoint Sub CA - sv195978)
***EST [INFO][ossl_init_cert_store_from_raw:182]-->
Adding cert to store (/CN=Certificate Services Root CA - sv195978)
***EST [INFO][est_log_version:156]-->
libest 1.1.0 (API level 3)
***EST [INFO][est_log_version:160]-->
Compiled against CiscoSSL 1.0.1p.4.13
***EST [INFO][est_log_version:161]-->
Linking to CiscoSSL 1.0.1p.4.13
***EST [WARNING][est_client_set_auth:3439]-->
Not using client certificate for TLS session, HTTP basic or digest auth will be used.
***EST [INFO][cert_verify_cb:671]-->
entering: Cert passed up from OpenSSL. error = 26 (unsupported certificate purpose)
***EST [WARNING][cert_verify_cb:764]-->
Certificate verify failed (reason = 26) (unsupported certificate purpose)
***EST [ERROR][est_client_connect:2245]-->
Error connecting TLS context
***EST [WARNING][ossl_dump_ssl_errors:246]-->
OSSL error: 3386898888:error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed:s3_clnt.c:1285:
Any ideas? Thanks
- Labels:
-
Other Wireless Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2019 02:32 AM
Check this out https://www.youtube.com/watch?v=z0sRiffVdpg
Sathiyanarayanan Ravindran
Please rate the post and accept as solution, if my response satisfied your question:)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2019 03:10 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2019 05:15 AM
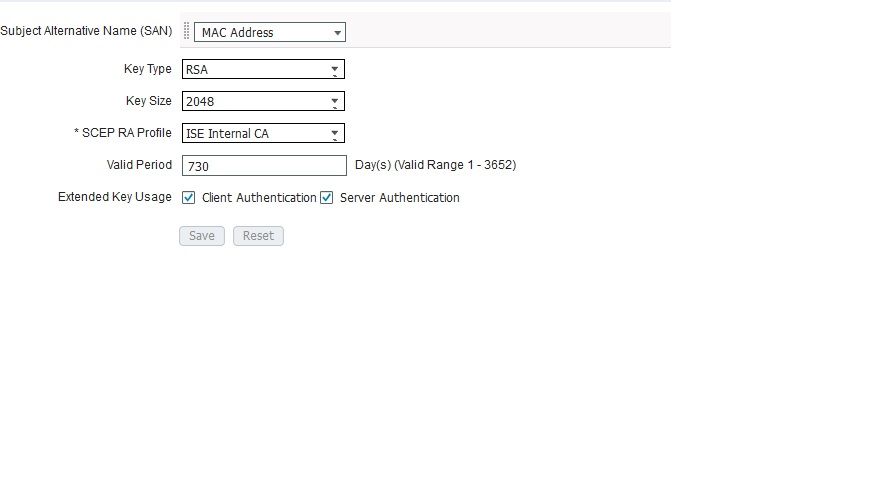
Or what is the "Enhanced Key Usage" in the certificate you have created for the ISE?
What is your test client exactly (make and model) and which software release is installed? It's well possible that it's just a client bug.
But who knows, maybe it's also an ISE bug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2019 05:30 AM
Hauwei P20 Pro Android 9 (have a colleagues phone who is running Android 7 with same result)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2019 06:06 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2019 07:46 AM - edited 04-16-2019 07:58 AM
I enabled Server Authentication under for my Certificate Template and deleted my session from ISE and Anchor WLC. No difference.
My DMZ ISE VM Server is using a Versign Certificate as Admin, EAP and Portal. I like using a Verisign Cert as these are always trusted in a device browser. This my confusion where does the certificate Template come into play with the user authentication process? I can't see this template been used without a Authorization rule in Policy sets if I'm correct? which I don't have.
Seems to me this problem is Cert related.
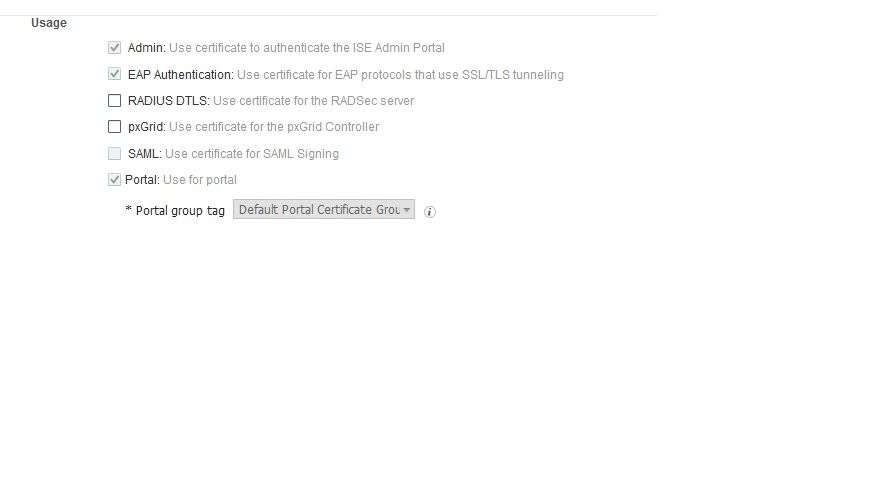
My system certificate:
Certificate template
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2019 11:41 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2019 04:24 AM - edited 04-18-2019 05:50 AM
Cisco TAC came back to me and said about a dozen customers are currently having the same issue.
To resolve generate new CSR and replace old Root CA, which I have now applied.
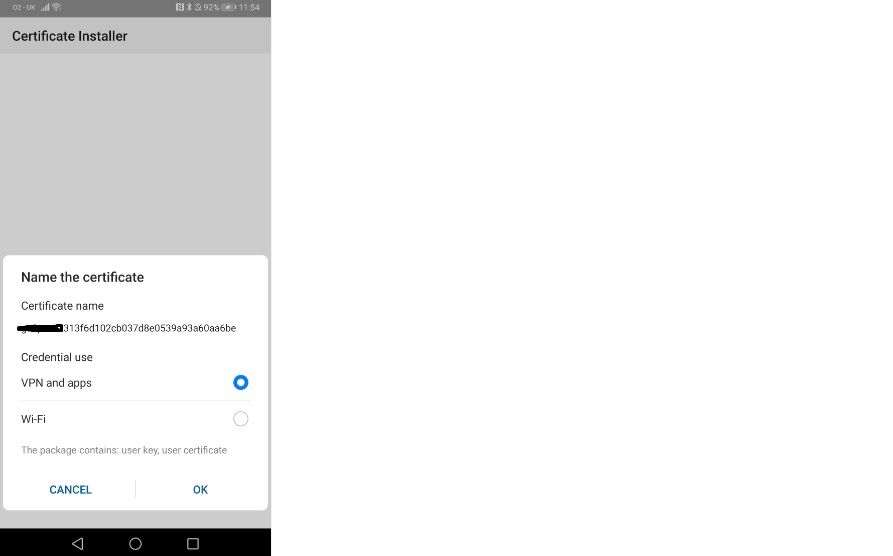
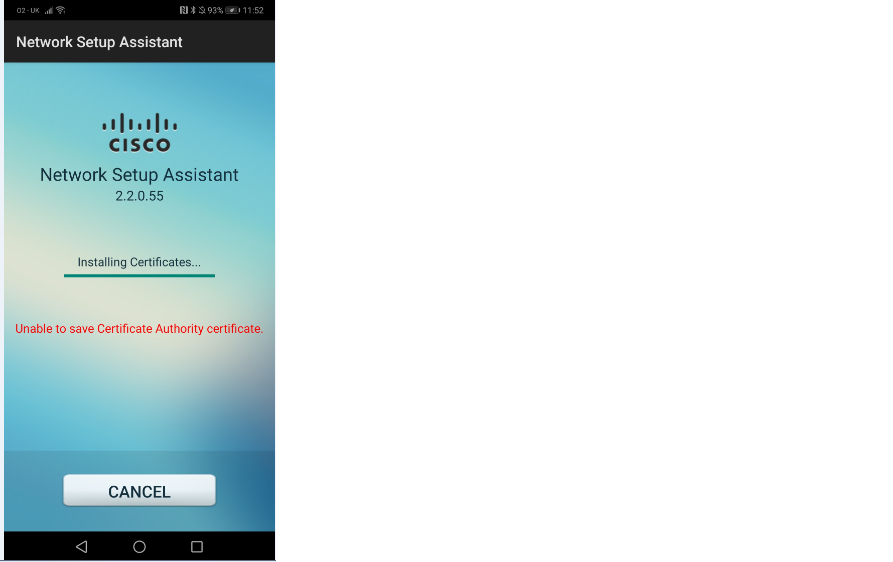
Tested getting a step further to success I hope! see below error I'm getting now with my Android device (I'm using a Verisign Cert for EAP and BYOD Portal Cert) see screenshots
SPW android log
2019.04.18 11:54:43 INFO:Subject name = C=BE,O=GlobalSign nv-sa,CN=GlobalSign Organization Validation CA - SHA256 - G2
2019.04.18 11:54:43 INFO:Issuer name = C=BE,O=GlobalSign nv-sa,OU=Root CA,CN=GlobalSign Root CA
2019.04.18 11:54:43 ERROR:ERROR: No Root CA downloaded from ISE server
2019.04.18 11:54:43 INFO:Internal system error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2023 01:17 AM
Did anyone managed to get this running? I have the same problem with ISE 3.2 Patch 2 and Android 13.
Any hints or tips are very welcome
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide