- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: Cisco Wireless MAB and 802.1X
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Wireless MAB and 802.1X
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2018 02:28 AM - edited 07-05-2021 09:05 AM
Hi All
Is there any way I could set up and SSID on Cisco WLC that will authenticate using both 802.1x dor AD users AND authenticate other devices via their MAC Address ?
My other option would be to create 2 SSID , one for 802.1X and AD users , another for Mac address authentication
This would be connecting to cisco ISE to authenticate users .
If any one has example polices for the ISE that would be great as I new to it and struggling with the condition, Authorisation and Authentication
Thanks
Craig
- Labels:
-
Wireless Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2018 02:45 AM
As i understood you want to do two factor athentication (802.1x and MAC auth)
If its correct then Yes you can do it.
Step1: Cretae a MAC address list in ISE in endpoint group.
Step2:
Authentication policy example:
8021xMAB : If Wireless_802.1X AND
Radius:Called-Station-ID ENDS WITH <ssid name> Allow Protocols : PEAP
AuthZ policy example:
AuthZPolicy8021xMAB if <Endpoint group of mac address>AND (Wireless_802.1X AND Radius:Called-Station-ID ENDS_WITH <ssid name> ) then Permit Access
Regards
Dont forget to rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2018 11:27 AM
It will send the mac address first so you have a few options:
1. Perform MAB and if it is valid do not perform 802.1x. (i.e a Printer)
2. Perform MAB and it if is NOT VALID, perform 802.1x. (i.e a domain computer)
3. You can do as Sandeep said to perform both MAB and 802.1x and force both to pass.
You need make sure that under your Authentication policy for Wireless-MAB you select the "Continue" option for "if the user does not exist". Otherwise you'll get an access-reject for the MAB and won't get to the 802.1x authentication.
Hope that helps.
CCIE #58023
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2018 07:52 AM
Thanks for that , I still cannot get it to bypass the AD group though
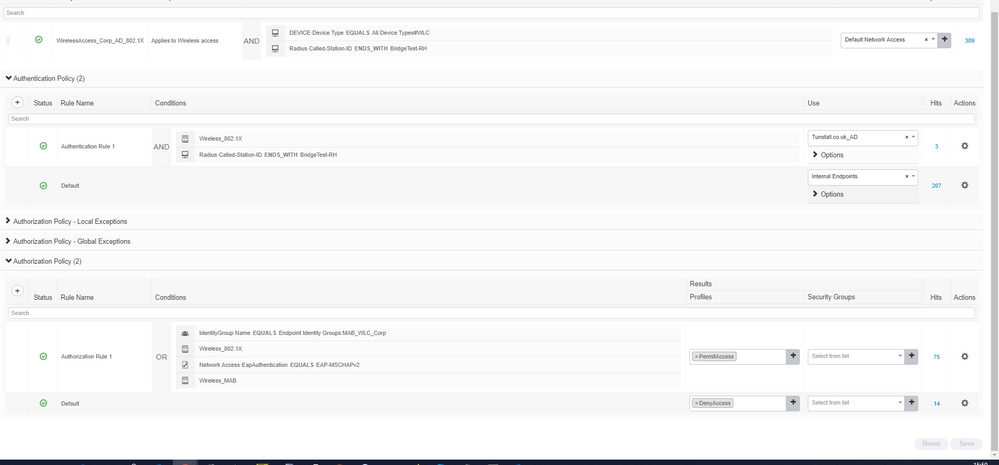
I am using ISE 2.3 with Cisco WLC . I am confused with the Condition- Authentication-Authorization and Also where I configure the MAC filter to send to ISE from the WLC . Please see below , It only looks at AD group then fails if it is not in the group . Please see below . Its probably something simple but the new policies on 2.3 are not intuitive
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2018 08:05 AM
Hi All
To add to this . I am trying to achieve the following
1. Authenticate clients using 802.1x and then within the AD group - this works
2. Those who do not belong to the AD group I then authenticate by their MAC address - cannot get to work
This is because some devices are not in the AD group .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2018 09:20 AM
And I can see two scenarios:
Option 1. If the users that are not within the AD group are valid users (the AD response will be that credentials are valid)
ISE RULE:
1. IF (AD-Identity-group IS NOT xyz AND endpoint-identity-group IS YourMacAddreses) THEN PermitAccess1
2. IF (AD-Identity-group IS xyz) THEN PermitAccess2
And create two rules in ISE:
Option 2: If the users are not valid AD Users (Unknown users), I believe it may work with the following rule but I haven't tested it.
ISE RULE:
1. IF (Network Access:AuthenticationStatus IS UnknownUser AND Network Access:EapTunnel IS PEAP) AND (endpoint-identity-group IS YourMacAddreses) THEN PermitAccess1
2. IF (AD-Identity-group IS xyz) THEN PermitAccess2
CCIE #58023
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2018 05:08 AM
Hi Jhosbell,
If I enable mac filtering I get the following on the WLC - Cannot enable MAC filtering and other Layer2 Security with Radius NAC.
Can you confirm what I need to configure on the WLC in order to allow the mac filtering , the ISE rules is also being bypassed
This seems more complex than I thought .
Thanks in advance
Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2018 09:08 AM
CCIE #58023
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2018 08:05 AM
Ok, I disabled Mac Auth and this seems to work ,
However , I cannot seem to get my policies to work, Can anyone give me an example please ?
Where 1 SSID can :
1. Use 802.1x and authenticate both AD users and Non AD users ( Mac address ) ?
If possible ( I know this is a big ask ) Include the SSID / WLAN config for WLC and ISE policy and Client config.
Currently I have
Client - WPA2 ENTERPRISE USING PEAP with user authentication
WLC - SSID = Layer 2 securtity WPA2 , auth key managment = 802.1x, Mac filtering and NAC state non ( in advanced)
ISE policy
Condition = Device = WLC , Radius called station-ID ends with *****
Authentication = Condition-WirelessMAB use Internal endpoint , Wirless 802.1x use AD
Authorisation = Condition . I have tried many of the above for comments for this but it seems to allow fall into default and DENYS
Thanks
Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 02:29 AM
Hi,
I had the same problem, and finally I fonund the solution NOW!!! :):
In your sitiatuon create 2 authentication rules:
1- 802.1x and use:AD
2-MAB and use: indentity endpoint
in authorization:
1 rule: Identity: AD and 802.1x
2 rule: Identity: Identity group endpoint and condition MAB
result both the same.
the first process, as you select the MAC filtering in the controller, are the rules with MAB, and later use the 802.1x.
if one of them fails. can't access!! :)
I hope you find the solution here!!
Samuel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2019 03:48 AM
Hi @samuel.cardenas (and @Kudetauk77 , @Jhosbell Verdesca De Aguiar , @Sandeep Choudhary )
This thread is a bit old now but I wanted to ask you what client device you used to perform the MAB test on your enterprise SSID? I have tried Android/iPhone/Windows10/Printer and each client is different. The printer won't associate to an 802.1X SSID, which is exactly the use case for MAB. So how does that work then? I cannot even see the SSID on that device - so I cannot stand a hope to perform MAB. The printer has no supplicant. Hence, it refuses to connect to an Enterprise WPA2 SSID.
Other devices like iPhone bring up the supplicant wizard straight away - they won't even associate to the SSID until you enter some creds or feed a cert - I can see the MAB request coming into ISE, and I force it to send Access-Accept back to WLC. But WLC is then stuck in 8021X_REQD. It doesn't work. Same story for Android and Windows.
I just want to know WHAT kind of a wireless client (that has no supplicant) can successfully associate to an enterprise SSID ? makes no sense to me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2019 11:33 AM
Hi Arne.
When you enable MAC Filtering and WPA2+802.1x at the WLC, BOTH have to succeed. Therefore your client needs to be 802.1x capable.
This is not MAB which means mac address bypass. (If the MAC is allowed, then bypass the 802.1x auth. If the MAC does not exist, then perform 802.1x auth).
This is MAC Filtering, which means ONLY the allowed MAC Address can move on to 802.1x authentication (or PSK or web-auth).
What you could do is, create a MAC filtering SSID with no L2 Auth and RADIUS or ISE NAC and if it is the printer then just send an access accept, if it is another device redirect to a web-page for authentication. This is basically CWA but bypassing the printer so it does not get redirected to the portal.
Starting on 8.3 I believe you can do CWA+PSK if you still want to have encryption for the traffic over the air, but the printer needs to be able to do WPA2+PSK.
Or create another SSID for the printers :(
Hope this helps.
CCIE #58023
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2019 01:58 PM
Great answer. Thanks. It concurs with my findings. MAB vs MAC filtering - subtle but important to understand the difference.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2022 12:28 PM
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: