- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: ISE BYOD - WLC NSP ACL not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE BYOD - WLC NSP ACL not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 02:45 AM - edited 07-05-2021 10:13 AM
Hi all,
I'm setting up a new BYOD setup.
I can login with my Andriod device successfully using my AD Credentials
I can register my device successfully after logging in
Then once I run the Cisco Setup Utility error following occurs: “Unable to detect Server. Please ensure your network access device is configured to redirect enroll.cisco.com to ISE"
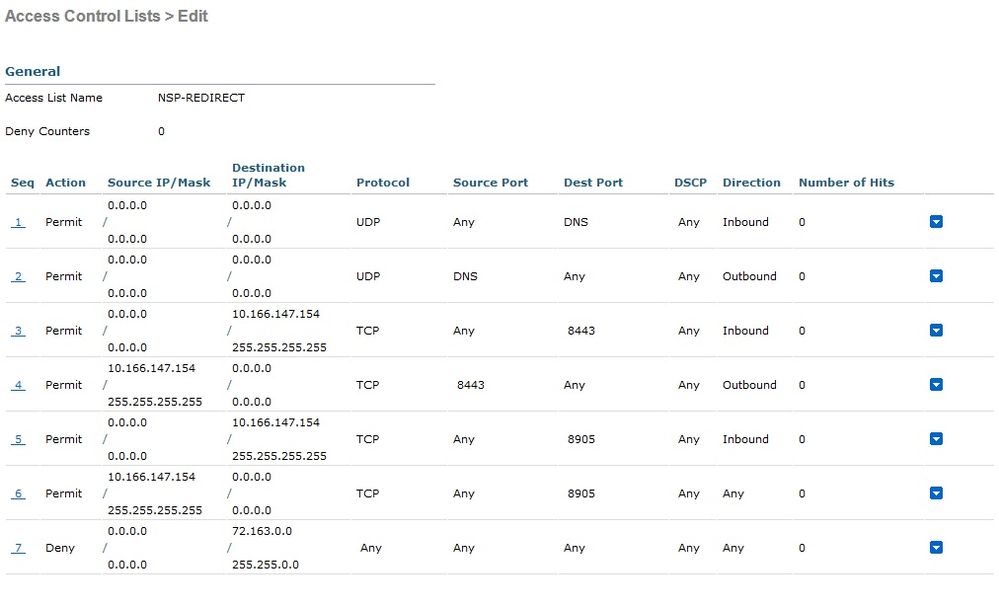
I instantly thought maybe the Andriod WLC ACL was incorrect, there maybe another issue I'm seeing, there are no hits against the ACL whatsoever. Below is my Andriod spw.log and attached a snapshot of WLC ACL
2019.04.08 09:30:31 INFO:About to apply random number generator fix, if necessary.
2019.04.08 09:30:31 INFO:Done applying random number generator fix.
2019.04.08 09:30:32 INFO:verion :9 SDK Level : 28
2019.04.08 09:30:32 INFO:State :START
2019.04.08 09:30:32 INFO:Starting Discovery
2019.04.08 09:30:32 INFO:Starting ISEDiscoveryAsynchTask
2019.04.08 09:30:32 INFO:DHCP Stringipaddr 10.66.108.238 gateway 10.66.108.7 netmask 255.255.255.0 dns1 8.8.8.8 dns2 8.8.4.4 DHCP server 1.1.1.1 lease 86400 seconds
2019.04.08 09:30:32 INFO:DHCP ipaddress10.66.108.238
2019.04.08 09:30:32 INFO:DHCP gateway10.66.108.7
2019.04.08 09:30:34 ERROR:DiscoverAsynchTask
2019.04.08 09:30:34 ERROR:java.net.SocketTimeoutException: failed to connect to /10.66.108.7 (port 80) from /10.66.108.238 (port 58284) after 2000ms
2019.04.08 09:30:34 ERROR:failed to connect to /10.66.108.7 (port 80) from /10.66.108.238 (port 58284) after 2000ms
2019.04.08 09:30:37 ERROR:DiscoverAsynchTask
2019.04.08 09:30:37 ERROR:java.net.SocketTimeoutException: failed to connect to enroll.cisco.com/72.163.1.80 (port 80) from /10.66.108.238 (port 55834) after 2000ms
2019.04.08 09:30:37 ERROR:failed to connect to enroll.cisco.com/72.163.1.80 (port 80) from /10.66.108.238 (port 55834) after 2000ms
2019.04.08 09:30:37 ERROR:Unable to discover ISE Server
2019.04.08 09:30:37 INFO:Internal system error.
My Authorisation profile for NSP-ANDRIOD is "Web Redirection" > Native Supplicant Provisioning>NSP-REDIRECT>Value = My BYOD Portal
Access Type = ACCESS_ACCEPT
cisco-av-pair = url-redirect-acl=NSP-REDIRECT
cisco-av-pair = url-redirect=https://ip:port/portal/gateway?sessionId=SessionIdValue&portal=0dfaf972-4bbb-11e9-9828-005056bc7ab1&action=nsp
Authorisation NSP Rule:
CONDITIONS = External groups EQUALS Provisioning Groups= AD
PROFILES = NSP-ANDRIOD
- Labels:
-
Wireless LAN Controller
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 02:54 AM - edited 04-08-2019 05:19 AM
I notice there's failed connection in my Andriod spw.logs to 10.66.108.7
10.66.108.7 this is the Firewall gateway which is the Default Router for the DHCP Scope (Firewall)
The answer I think is here https://www.linickx.com/cisco-ise-andriod-network-setup-assistant-unable-to-detect-server
even if I deny this rule in the WLC ACL "NSP-ANDROID" this doesn't explain why there are Zero hits against this ACL?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 06:28 AM
1.1.1.1 is today a valid public IP address and shouldn't be used internally. Google devices tend to ignore "uncommon" replies from that IP address, they expect a CloudFlare device answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 08:00 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 08:33 AM
2019.04.08 09:30:32 INFO:DHCP Stringipaddr 10.66.108.238 gateway 10.66.108.7 netmask 255.255.255.0 dns1 8.8.8.8 dns2 8.8.4.4 DHCP server 1.1.1.1 lease 86400 seconds
You probably have configured the WLC Virtual-Interface IP Address to 1.1.1.1 (was once recommended by Cisco, many years ago).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2019 12:41 AM
I've read some notes after your post about this issue, I have changed this is an RFC 1918 but non routable a random address 192.168.44.1 used same for both Anchor Controllers part of the same Mobility Group and I get the same result. Not sure if it's required to have a routable address, I wouldn't think so?
2019.04.09 08:26:02 INFO:About to apply random number generator fix, if necessary.
2019.04.09 08:26:02 INFO:Done applying random number generator fix.
2019.04.09 08:26:03 INFO:verion :9 SDK Level : 28
2019.04.09 08:26:03 INFO:State :START
2019.04.09 08:26:03 INFO:Starting Discovery
2019.04.09 08:26:03 INFO:Starting ISEDiscoveryAsynchTask
2019.04.09 08:26:03 INFO:DHCP Stringipaddr 10.66.108.249 gateway 10.66.108.7 netmask 255.255.255.0 dns1 8.8.8.8 dns2 8.8.4.4 DHCP server 192.168.44.1 lease 86400 seconds
2019.04.09 08:26:03 INFO:DHCP ipaddress10.66.108.249
2019.04.09 08:26:03 INFO:DHCP gateway10.66.108.7
2019.04.09 08:26:05 ERROR:DiscoverAsynchTask
2019.04.09 08:26:05 ERROR:java.net.SocketTimeoutException: failed to connect to /10.66.108.7 (port 80) from /10.66.108.249 (port 41584) after 2000ms
2019.04.09 08:26:05 ERROR:failed to connect to /10.66.108.7 (port 80) from /10.66.108.249 (port 41584) after 2000ms
2019.04.09 08:26:07 ERROR:DiscoverAsynchTask
2019.04.09 08:26:07 ERROR:java.net.SocketTimeoutException: failed to connect to enroll.cisco.com/72.163.1.80 (port 80) from /10.66.108.249 (port 46420) after 2000ms
2019.04.09 08:26:07 ERROR:failed to connect to enroll.cisco.com/72.163.1.80 (port 80) from /10.66.108.249 (port 46420) after 2000ms
2019.04.09 08:26:07 ERROR:Unable to discover ISE Server
2019.04.09 08:26:07 INFO:Internal system error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2019 02:45 AM
2019.04.09 08:26:05 ERROR:java.net.SocketTimeoutException: failed to connect to /10.66.108.7 (port 80) from /10.66.108.249 (port 41584) after 2000ms
It looks like the Gateway IP Address is not reachable by the client. It looks like some ACL/policy is blocking that. Did you permit the access of the guest portal in the default policy?
Also because your DNS servers are outside of the subnet, do you allow the access from the client (before authentication) to the DNS servers?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2019 04:40 AM - edited 04-09-2019 04:51 AM
10.66.108.7 is the default gateway of the WLC Guest Interface (10.66.108.7 is my Firewall interface)
Why would my device be trying to connect to my Firewall interface on port 80? I'm confused here. or is this when the NSA app sends a http://DFG/auth/discovery to Redirect to ISE?
I have created Dual SSID BYOD setup both SSID's are using the Guest Interface so I don't have to create additional VLAN's and interfaces in my Wireless infrastructure.
(For the WLC ACL for Guest Authorization profile, DNS was after ISE authentication I've changed this around to before)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2019 12:39 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2019 05:42 AM
I spoke to an ISE TAC Engineer yesterday and we added some Authorisation rules but this hasn't fixed the problem. It's the Authorization proifle for Andriod and Apple that don't seem to be working as when each user attempts to use the NSA the ISE logs for the session show cisco av-pair = nil so I guess for some reason the redirect is not working because of the error I'm getting in my Andriod's spw.log. I'm hoping for another Webex later on today. TAC person did check my WLC ACL's and Authorization profiles thoroughly so not sure what the issue is here. I'll let you know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2019 05:17 AM
ACL was incorrect on the Foreign Controller that's why there were Zero hits on the Anchor Redirect ACL, once applied (both identical) things started working.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: