- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Rogue containment - no deauth packets sent by monitor mode AP (4800 series AP & 5520 WLC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Rogue containment - no deauth packets sent by monitor mode AP (4800 series AP & 5520 WLC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2019 05:27 AM - edited 07-05-2021 10:51 AM
Currently we are testing rogue detection/containment functionality on 5520 WLC on a small area (around 20 square meters), with a couple 2800 series APs in local mode and one 4800 series AP in monitor mode.
Detection and classification of rogue APs works correctly, within a couple of minutes. On the other hand rogue containment (both manual and automatic) don't seem to work. I captured packets on Wifi channel 1 on which my rogue AP is broadcasting and during containment not a single deauth package was found. To check if I was capturing them correctly I attacked my own rogue AP using aireplay-ng which generated deauth packets and that worked perfectly (packets seen in Wireshark and clients were unable to connect to the AP).
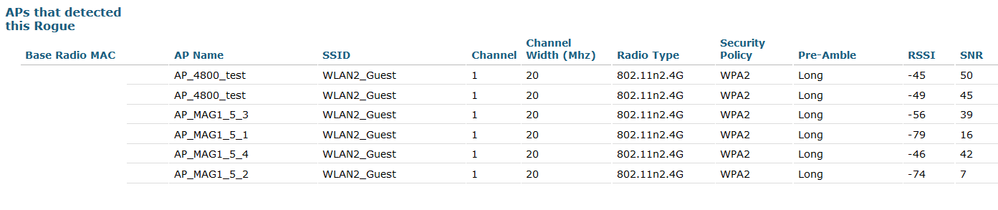
Further info, my test rogue AP in this case was a phone (Huawei P20) which was configured to broadcast SSID identical to managed SSID in WLC. All distances between rogue AP, local mode APs and monitor mode AP are within 5 meters in open space without much interference. Below are the APs that see particular rogue AP. Even when selecting maximum number of APs (4) to contain, always just the 4800 does the containment on it's two radios. Furthermore, under "containment type" column in below view, after containment is initiated it says "Discourage", I was unable to find which containment types exist and what exactly they do.
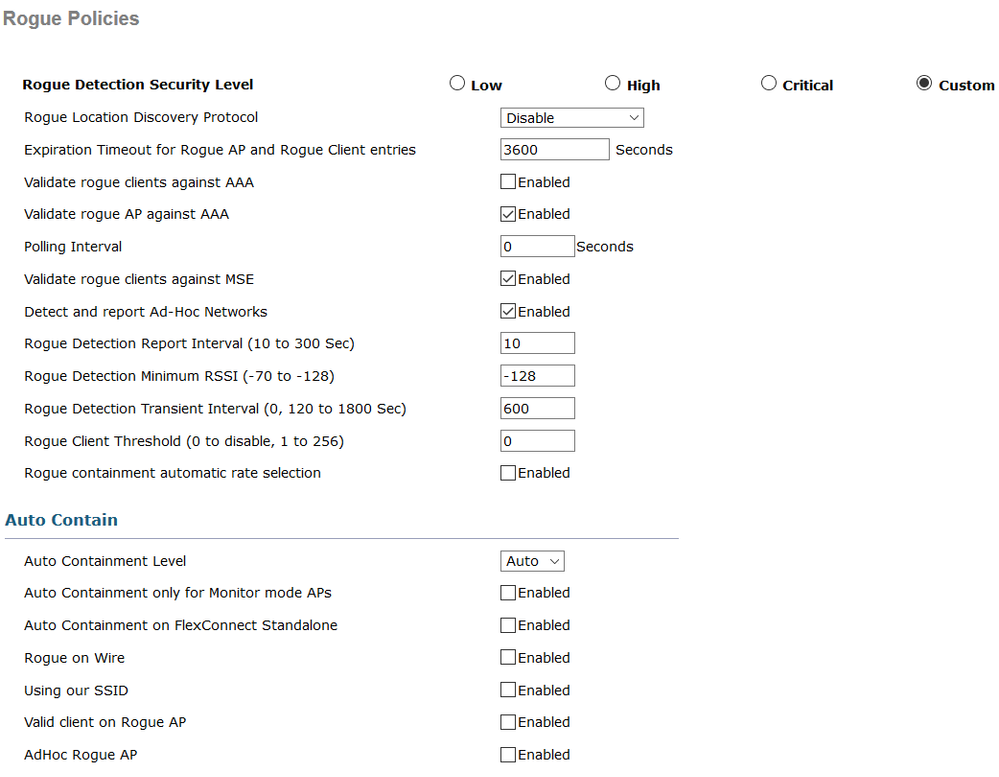
Below is what we configured regarding Rogue detection in general, autocontainment was tested too and it fails in the same way as manual containment.
Questions:
1. I tried putting one 2800 series in monitor mode, removed the other monitor mode AP and start containment. WLC notified me that no APs are available to contain the rogue AP, are 2800 series AP unable of sending deauth packets?
2. How many APs in general should I need to contain and AP with 2-3 clients?
I feel like I'm missing something, although I was following configuration guide for rogue detection, and it seemed pretty straightforward.
- Labels:
-
Wireless LAN Controller
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2019 06:38 AM
In most countries this is illegal today.
I actually don't know if Cisco still allows sending of deauth packets or not, but you might want to try to enable some of the options under Auto Contain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2019 01:21 AM
I tried to enable auto contain for the same SSID as their enterprise SSID, and it also didn't work. Preferred solution was possibility of manual containment, and it would only be used for SSIDs which they use (they are quite specific and there is no reason somebody else should use the exact same SSID unless they have malicious intents).
If Cisco doesn't allow sending deauth packets, I think containment shouldn't be an advertised feature anymore. Even documents from this year mention possibility of configuring containment and it should work by sending deauth packets. Is this something we should open a TAC case for?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2019 02:09 AM
It sounds like it should send deauth packets.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: